Infrastructure as Code presents an incredible opportunity to embed consistent and scalable cloud security coverage. IaC security refers to addressing cloud configuration issues in IaC rather than deployed cloud resources. Because IaC does not represent infrastructure itself, IaC security is a means to an end. It ensures that IaC is configured in such a way that it will provision secure resources. IaC security is a proactive approach to cloud security which, historically, has addressed configured cloud resources in runtime. If IaC is in use, this reactive approach introduces risk and redundancy where cloud security issues are concerned.
Cloud security issues, commonly referred to as misconfigurations, are often related to securing access to critical services and customer data. Each cloud and resource type has its own set of security best practices, commonly referred to as policies, and corresponding compliance benchmarks, and IaC is a programmatic way to identify violations against those policies. Organizations may also enforce their own policies unique to their infrastructure and business requirements.
How IaC Security Works
Much like static analysis of application code, the most basic form of IaC security is being able to scan IaC to identify misconfigurations. Scanning IaC involves checking templates, files, modules, and their variables against known policies. Policy violations occur when proper settings are either missing variables or the values are incorrectly set.
Because each cloud and resource type has its own security standards, there are hundreds — and sometimes thousands — of policies that may be relevant to your stack. Relying on developers to keep track of those policies is impossible, which is why automation is the best way to gain total coverage across cloud environments. By automating IaC scans, organizations save time and provide coverage not possible through manual work alone. There are a few open-source tools such as Open Policy Agent (OPA) and Bridgecrew’s Checkov that enable anyone to scan IaC files or directories against known policies.
Here's an example of leveraging Checkov to scan Terraform against a few policies. Once you’ve scanned your file or folder, you’ll see output such as this:
IaC security is incredibly valuable in that it puts the same flexibility and repeatability that IaC uses to provision resources into securing it. Code is inherently extendable — and applying the same methodology into cloud security is the best way to secure it consistently.
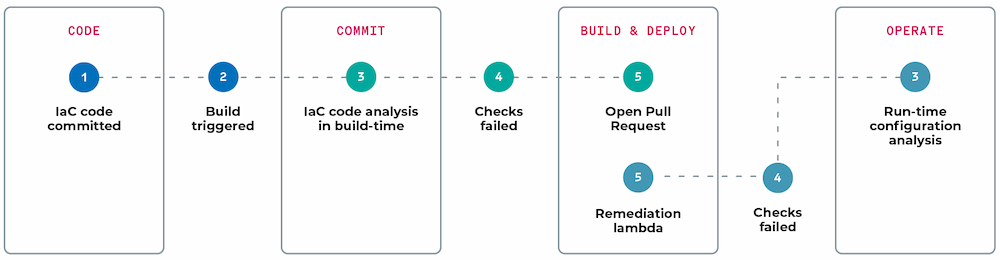
How you scan your IaC matters almost as much as when you scan it. On the one hand, the earlier misconfigurations are identified — for instance, in a developer’s IDE or via a pre-commit hook — the faster and cheaper it is to fix. Relying on individual contributors is a great way to exchange quick feedback, but a more collaborative approach is needed for comprehensive coverage. A common approach to getting collaborative and consistent IaC security feedback is to integrate it into a version control system (VCS) such as GitHub or GitLab. This way, when code is committed or pull/merge requests are created, scans are automatically kicked off and misconfigurations are surfaced right then and there. Giving timely feedback to developers — regardless of the stage or tool — is key to embracing IaC security.
Additionally, because IaC is more abstracted the further away it is from its runtime state, adding periodic checkpoints in the development lifecycle is best practice. Whether you’re surfacing IaC security feedback to your pull-request checks or a failing step in your CI/CD pipeline, IaC works best when it’s automated as part of everyday code reviews.
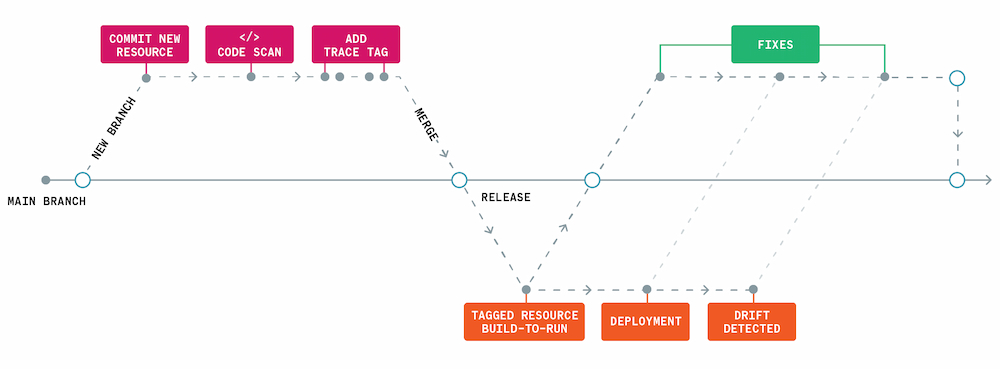
IaC is unique in that it creates a level of abstraction on top of reality — how cloud resources operate and are configured once they are released and running. That’s why any IaC security and monitoring strategy should be accompanied by runtime protection. To be alerted if and when changes are made to resources outside of the IaC template, creating cloud configuration drift, you have to have traceability between the code and cloud resources. This can be done by tagging resources in code with unique values using tools, such as open-source Yor, that get persisted to runtime. Trace tags — along with runtime monitoring — give you complete coverage and the ability to detect drift.
Figure 2: Infrastructure coverage from commit to post-release
Finding the right tooling to automate the identification of IaC issues is imperative and enforcing security policies continuously is just as important. The easiest way to make IaC security feedback actionable is to deliver fixes in a common language — code. Implementing IaC security not only equips developers with real solutions to their problems but helps set policies to govern infrastructure in the future.
Why Is IaC Security Important?
As IaC adoption soars and infrastructure innovation speeds up, it’s becoming more important to understand the security risks and complexities involved with IaC. Because infrastructure best practices are constantly evolving, a set-it-and-forget-it approach won’t work. Obtaining updated and modern coverage is the best approach when it comes to IaC security.
IaC is designed to make cloud provisioning simpler, faster, and predictable. But in order for teams to recognize those benefits, the same philosophy must be applied to how they approach cloud security. IaC security is the answer to cloud security in IaC-forward environments. It is the only way to get consistent, scalable, and immutable security.
If security is not applied at the IaC layer, misconfigurations are inevitable. And when clouds are orchestrated by inherently misconfigured code, they’ll continue to be orchestrated and configured incorrectly in production. This causes a deluge of errors that security teams have to triage, prioritize, and assign to the right engineering teams. By the time misconfigurations make their way back to the teams responsible, they have likely already moved on from that code. This context switching takes much more time than if the issue was addressed at its inception.
The gap between security and engineering teams is also a breeding ground for risk. Between the time a misconfiguration is released, identified by traditional cloud security posture management (CSPM) tools, and fixed, a bad actor may have gained privileged access to proprietary code or sensitive data.
Enabling developers to address security issues across the development lifecycle increases consistency and allows you to take a more holistic approach to security. Security automation also reduces the risk of human errors, improving accuracy and reducing the risk and cost of breaches, if secured properly.