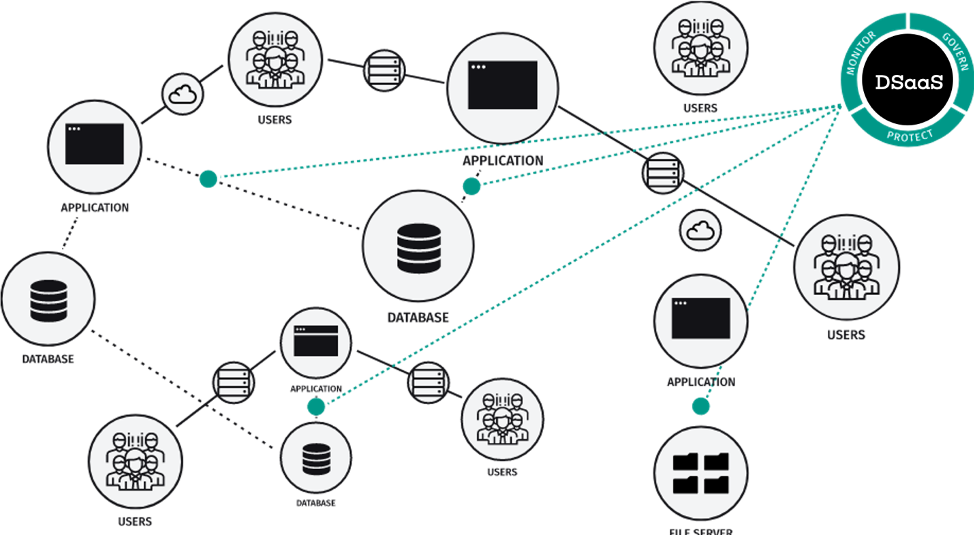
In order to understand how DSaaS can give your security and compliance teams what they need, you need a quick overview of the areas that are currently falling short, both in effectiveness and efficiency.
Implementing an adequate security, privacy, and compliance strategy is a time-consuming and challenging undertaking. It can take years to plan, deploy, integrate, and then optimize your strategy. By that time, new threats could have emerged, or cutting-edge technology that makes your current approach obsolete.
Security should be baked in from day one of development, freeing up time and money on the back-end. The traditional outlook of security being an “aftermarket” add-on to applications ends up costing organizations time and money, ultimately preventing them from getting technology out the door.
In order to understand how DSaaS can give your security and compliance teams what they need, you need a quick overview of the areas that are currently falling short, both in effectiveness and efficiency.
This is a preview of the Introduction to Data Security as a Service Refcard. To read the entire Refcard, please download the PDF from the link above.