In this section, we explore how to use RASP to solve common security problems.
Preventing Exploits
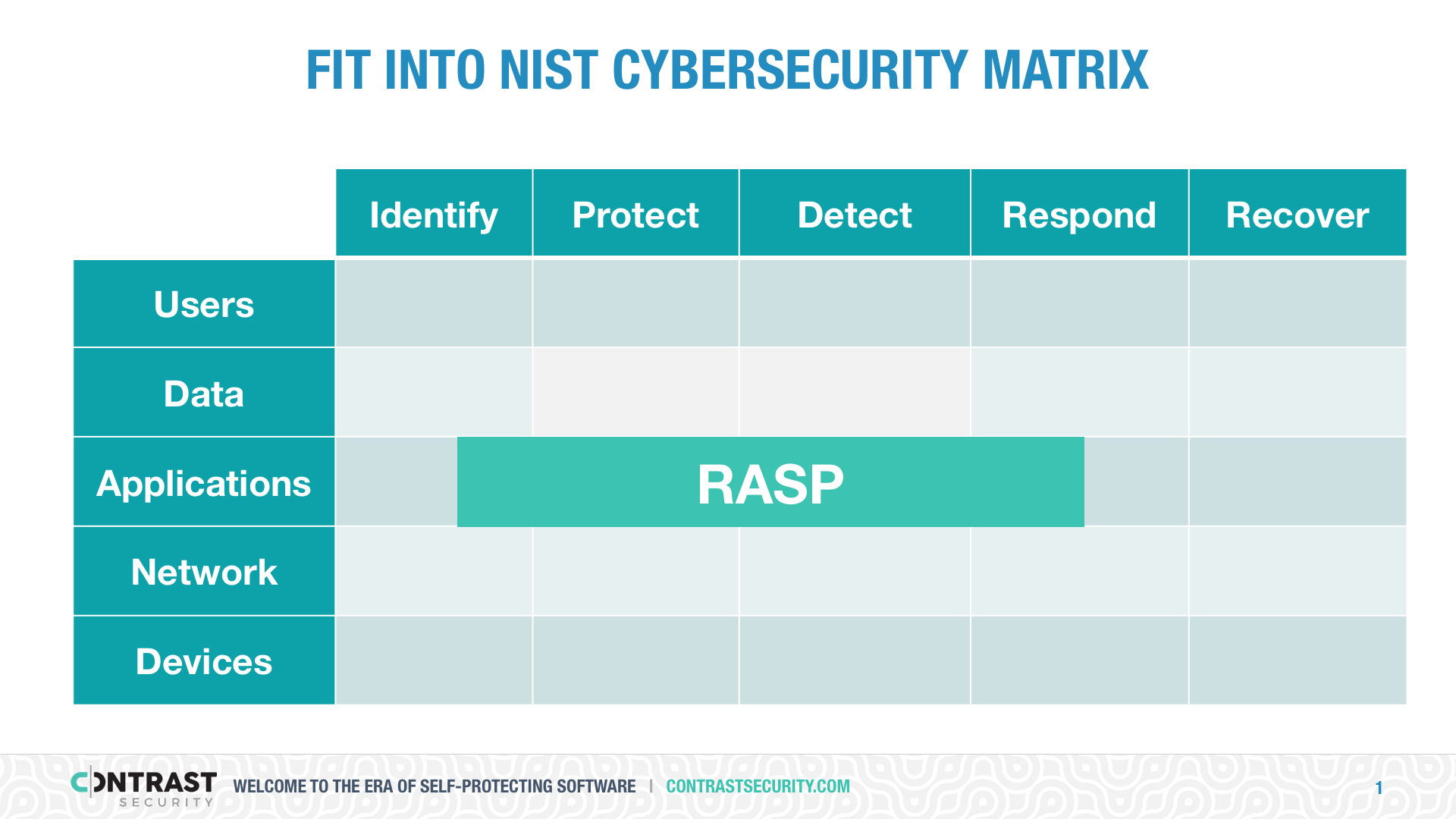
In general, RASP can deal with attacks on vulnerabilities in the software itself, not container, operating system, or network attacks. Every product is different, but RASP can protect typically protect against attacks like:
- Cross-site scripting
- Path traversal
- Command injection
- SQL injection
- NoSQL injection
- HTTP method tampering
- Expression language injection
- Untrusted deserialization
- XML external entities
- OGNL injection
- Cross-site request forgery
- Server-side request forgery
- Regex DOS
- Padding Oracle
RASP does not typically work on network layer attacks such as:
- Distributed denial of service (DDOS)
- Insecure SSL configuration
Using RASP to Protect New Custom Code
In a world of high-speed software development, performing full software verification of all new code before it is deployed is often impossible. RASP can provide strong protection in the gap between deployment and completing security testing. Having RASP in place can provide the extra protection that will allow you to deploy safely at high speed without security bottlenecks.
Using RASP to Reduce Application Vulnerability Backlog
Whether you have one application or tens of thousands, everyone has vulnerabilities in their codebase. Working through this backlog could take many years of development. RASP shouldn’t be used as an excuse to give up on writing secure code, but it can provide significant protection during the “window of exposure” before vulnerabilities are remediated.
Using RASP to Protect APIs
APIs are difficult to protect for two reasons. First, from a protocol standpoint, they are far more complex than simple web sites. APIs are often HTTP with a JSON, XML, binary, or other payload. APIs might also use a non-HTTP protocol such as WebSocket. The second reason is that API data and control flows within software are often far more complex than simple websites. Most APIs use a software framework with features like automatic payload parsing and object mapping. Many use annotations to route data to the appropriate methods.
Web API attacks are generally similar to normal web application attacks (including various types of injection, XML, and JSON parser flaws), and RASP is ideal for solving these challenges because it works at the application layer, after protocol and data format issues have been resolved. This approach allows APIs to be protected against attacks, just like full web applications.
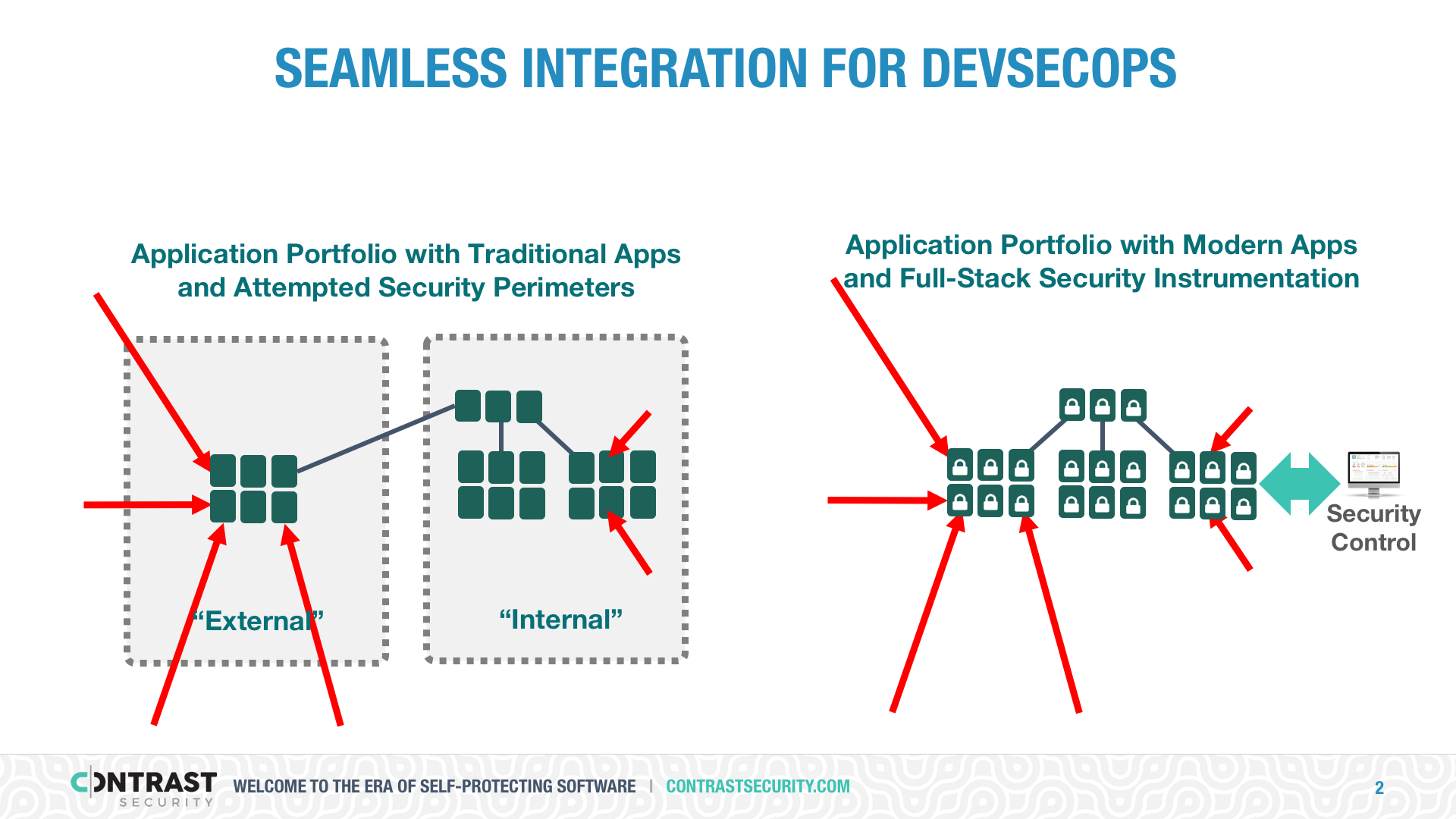
Using RASP to Protect “Internal” Applications
As the “perimeter” crumbles, the difference between “internal” and “external” applications disappears. “Internal” applications are generally only intended for employee and partner use, while “external” applications are for public access. However, internal web applications and APIs are increasingly exposed to the same threat-facing external applications. Often, the applications only intended for employees include more sensitive data and have more powerful capabilities than their public-facing brothers and sisters. Because RASP is software and can be easily and widely deployed, it’s now possible to protect all applications and APIs in your portfolio.
Using RASP to Protect Backend Interfaces
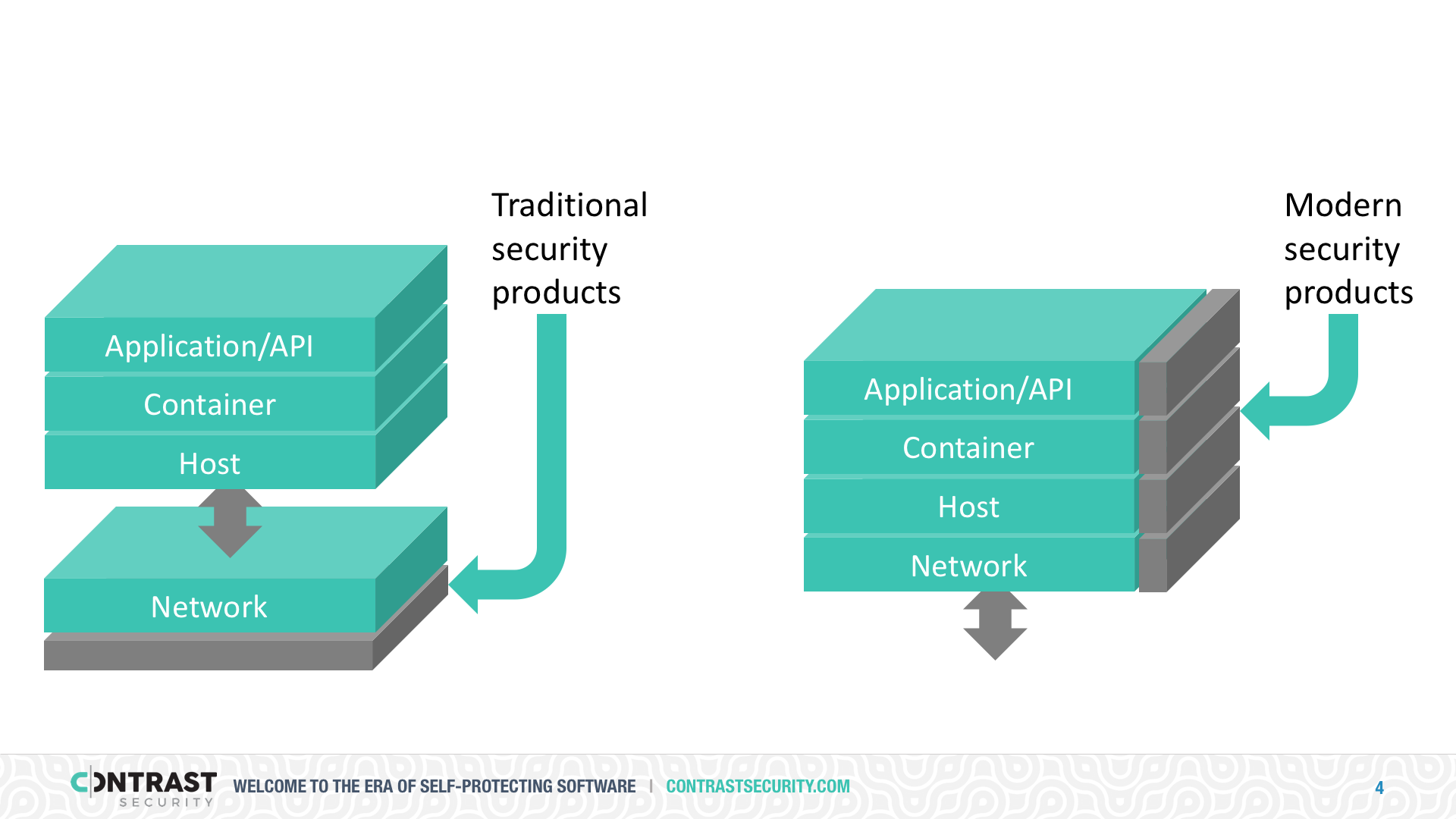
RASP is not limited to frontend interfaces or HTTP. RASP can protect the entire attack surface, including all kinds of attacker-controlled data sources. For example, RASP can protect against databases, message queues, socket connections, file shares, mainframes, ftp sites, and other sources that you can’t fully trust. You could try to use a perimeter approach, but no such devices exist. And even if they did, imagine the complexity of interrupting all backend connections coming from an application or API. RASP is protocol-independent, so it can protect all front and back doors at once.
Using RASP to Protect Open Source
While open-source vulnerabilities often seem like a flood, the situation is usually considerably worse than it appears. There are millions of open-source libraries in existence, and only a handful of security experts testing them. RASP can protect open-source against both newly disclosed vulnerabilities (CVEs) and latent vulnerabilities that are still undiscovered. In either case, if the vulnerability is of a known class, like SQL injection or cross-site scripting (XSS), RASP prevents it from being exploited. So, your open source is protected regardless of whether or not the vulnerability has been disclosed. In this way, RASP keeps the “window of exposure” to an absolute minimum.
Using RASP to Protect against Novel Vulnerability Classes
No security solution can claim to protect against types of vulnerability that haven’t been discovered yet. Historically, new classes of vulnerability have emerged at a rate of about one or two a year. And there are also occasionally specific vulnerabilities that only apply to a single library or component. Because it takes so long for organizations to learn about these new issues, the window of exposure for these novel vulnerabilities is often months or more despite attacks starting within days. However, RASP provides the infrastructure to deploy protection quickly and effectively, regardless of what measures are required. The new defense might come in the form of a new sensor, rule, or capability, or a virtual patch. RASP allows these updates to be made across an entire application portfolio within hours. The alternative is to scan for problems, wait for software updates, replace libraries, recode applications, retest, and redeploy all affected applications.
Threat Intelligence
Most organizations are completely blind when it comes to application threat intelligence. They do not know who is attacking them, what attack vectors are being attempted, which applications are being targeted, and which parts of the attack surface are affected. If an organization does have information, it is almost always buried in a mountain of false positives.
Using RASP to Create Visibility
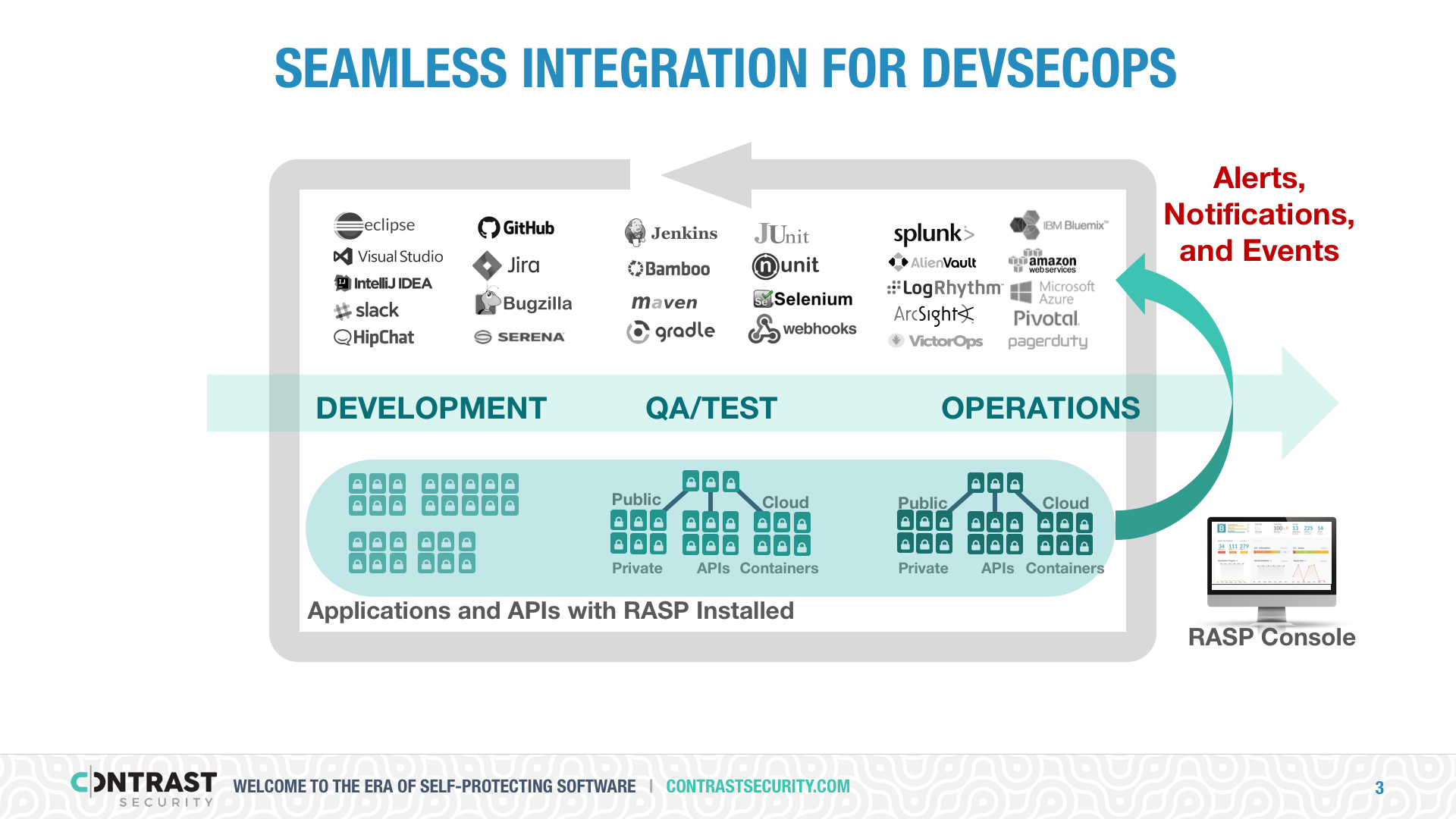
RASP is excellent at identifying application layer attacks and creating visibility. RASP continuously provides information about who is attacking you, what techniques they are using, and which of your applications are being targeted. In addition to full HTTP request details, RASP provides application details including the exact line(s) of code associated with a vulnerability, exact backend connection details (like SQL query), transaction information, and currently logged-in user.
Collecting threat and attack information is just half the problem. The other half is making it useful to all the employees that need the information through the tools they are already using. Some RASP solutions simply send their data into a SIEM, which will require custom reports to make sense of the data. In some cases, a SIEM plugin is provided to help interpret the data. Other RASP providers also provide an integrated console/dashboard.
Enhancing Logs With Security Telemetry
Most applications do not perform sufficient security logging. Logs are full of exceptions and debug information but aren’t complete enough to identify attacks or diagnose their impact. Some RASP implementations can enhance security logging without requiring changing software or redeploying. Essentially, RASP weaves enhanced security logging into the application as it loads, without requiring code changes or redeploying. With more complete security logs, your SIEM can be more effective at identifying attacks and breaches. This can create much better visibility around what is occurring in the application layer for the SOC.
RASP Is Not For Vulnerability Discovery
Discovering vulnerabilities is not a use case for RASP. Some organizations have tried to claim that if you use dynamic scanning (DAST) and RASP together, they form an effective vulnerability detection solution — even suggesting that the combination constitutes IAST. This is nonsense. At best, this might help confirm some of the vulnerabilities that the DAST tool identifies. But it has all the problems and limited coverage of a DAST scanner, and RASP does very little to improve coverage or accuracy. If you’re interested in vulnerability analysis, interactive application security testing (IAST) is very compatible with RASP, and some vendors are offering integrated IAST/RASP agents.