2-Way SSL with Java: The Keystore Strikes Back - Part 1
If you start off trying to get to grips with the in-built Java Secure Sockets Extension you're gonna be stunned by the complexity of it all.
Join the DZone community and get the full member experience.
Join For Freeyou'd think with how prevalent ssl/tls on the web that ssl with java is easy, well it's not. in addition to having to get to grips with understanding how private/public key, certificates work there's all the networking that goes on in java.
if you start off trying to get to grips with the in-built java secure sockets extension you're gonna be stunned by the complexity of it all.
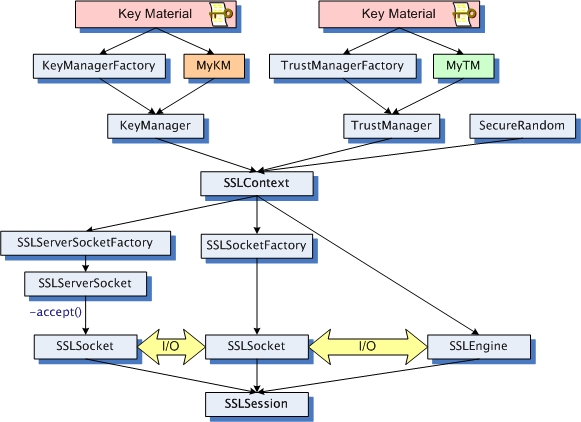 clear as mud eh? the jsse guide alone is 73 pages long - but i hate to say that its
really
a must read. print it out (double-sided to save some trees) grab a venti decaff or two and wrestle the information into your brain.
clear as mud eh? the jsse guide alone is 73 pages long - but i hate to say that its
really
a must read. print it out (double-sided to save some trees) grab a venti decaff or two and wrestle the information into your brain.
thankfully jakarta commons http client makes it relatively easy code-wise (side note: why the heck does http components v4.0 seem so much more complicated than v3.0? the v4 docs seems much less clear!). for example:
httpclient httpclient = new httpclient();getmethod httpget = new getmethod("https://www.bob.com/");try {httpclient.executemethod(httpget);system.out.println(httpget.getstatusline());}finally {httpget.releaseconnection();} in any event it's pretty straightforward code-wise with http client until you have to start to get to grips with three funky things - they are
1) the keystore
2) the truststore
3) keytool to access both
truststore
lets start off with a truststore. in a normal 1-way ssl situation, say on a browser, you need your bank's server to authenticate itself to assure you that you are hitting the real bank server and not some spoofed site. so in the 1-way ssl case the bank server sends your browser a certificate signed by a ca(certificate authority) then your browser compares that ca signature against an in-built list of cas. in a similar way your truststore is your secure store of trusted ca entries or self-signed certs provided from third parties you trust. so essentially the truststore contains the certificates you use to authenticate other servers / processes. every java install comes with it's own truststore located in $java_home/lib/security/cacerts
keystore
a keystore is, as you can imagine, is a secure store for keys used in the ssl protocol. essentially it's where you will put private keys and their associated certificates used to authenticate you as client to a server. typically in a normal web browser transaction you use 1-way ssl to authenticate the server then you use a login/password combo to authenticate you. well in b2b systems you can use 2-way ssl where client and server authenticate each other - and this is where the keystore is critical to authenticate your java program, the client, to the server.
typically for client authenticate you create either a self-signed or you purchase a ca signed cert. you store your private key and public cert in the keystore and provide your b2b partner with the self-signed cert - or in the case of a ca-signed cert typically your partner's truststore will trust that ca and you are good to go.
keytool
keytool is the command line tool to maintain these two beasts. and let's just say it's not easy to use keytool. it's like snowboarding - its good when you're used to it but getting started with keytool you're gonna spend a lot of time on your ass or face first! if you're just getting started with keystores and truststores i strongly recommend using portecle - an open source gui tool which makes keytool obsolete and should really ship with java someday.
then you have to tell java where they keystore and truststore are and the passwords to these stores. well you can do that with system properties e.g.
-djavax.net.ssl.keystore=keystore
-djavax.net.ssl.keystorepassword=password
-djavax.net.ssl.truststore=truststore
-djavax.net.ssl.truststorepassword=trustwordif standards are good, more is better right?
getting tired yet? well this is gonna put you over the edge . . . . when you get keys and certs from your b2b partners how many types of files do you think there are - two? three? four? let's list the ones i've had to deal with lately.
- pfx
- pem
- p12
- cer
- crt
- der
it's madness! if you want a good description overview of the file formats then this link is a good place to start. this is when openssl becomes your friend when you need to convert from different file formats into formats compatible with keytool - oh and good luck finding documentation on which file formats keytool takes!
in any event so far things are tough but not insurmountable - well so i thought until two b2b partners decided to provide me each with a key for my keystore to authenticate me. a key of the same type (rsa), signed by the same ca. then all hell broke loose - cos java don't support that without some major surgery . . . . and that's the topic of part ii.
from http://softarc.blogspot.com/2011/03/2-way-ssl-with-java-keystore-strikes.html
Opinions expressed by DZone contributors are their own.

Comments