A Beginner’s Guide to Understanding Encryption Vs Decryption
Although encryption and decryption fall under one umbrella of cryptography, both are different from each other. In this blog, we will talk about what is what.
Join the DZone community and get the full member experience.
Join For FreeA computer system must promise or at least assure privacy and confidentiality when it transmits sensitive or personal data. A simple system, unless equipped with the proper technology, cannot stop any unauthorized access to cyber criminals. And in this computer era, data tampering needs no introduction as it is not something unheard of. So if you want to prevent or altogether stop the mishap, one of the best ways is to alter the data as it will prevent unauthorized access.
The technique employed to alter the data is known as cryptography, and this process takes place in two phases- encryption and decryption of information. So if you want to find out what encryption vs. decryption is all about, keep reading:
Before differentiating between encryption and decryption, it is best to understand the terms individually to understand how each technology works. Let us first try to understand the meaning of encryption in cryptography:
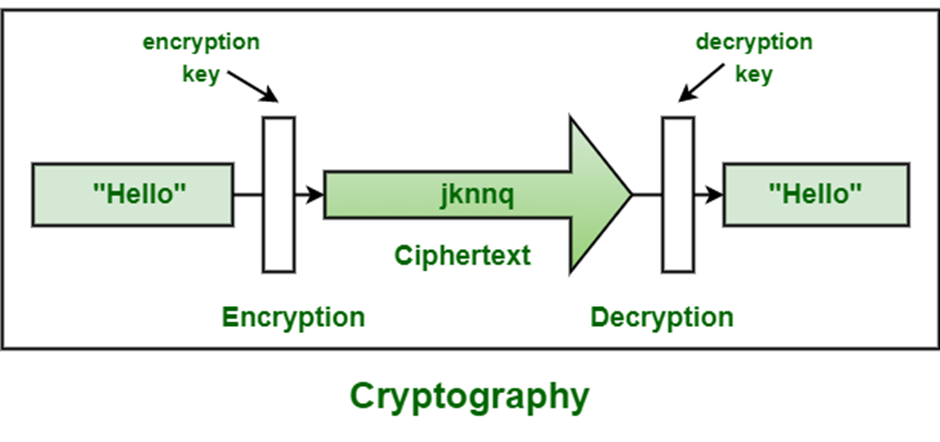
What Is Meant By Encryption?
Encryption is the process of converting original information or data into an unreadable form. The new form of information is completely distinct and different from the initial information, thus, preventing hackers from reading the data, thanks to the use of the encryption algorithm. Typically done with the help of key algorithms, the data is encrypted to make it completely safe from any stealing or mishandling. Often, big names encrypt their data, so their business stays hidden from their contemporaries.
During the carrying out of data transmission, the data that requires security is called the plaintext. In contrast, the data that is formed as a result of the encryption algorithm using a specific key is called ciphertext. The latter is not shielded as it goes through the transmission medium. In the entire process, the encryption algorithm helps input the encryption key and plain text and comes up with a ciphertext.
In conventional (symmetric)encryption techniques, the encryption and decryption keys stay the same and are concealed. Typically, the conventional encryption methods are broadly categorized into two parts- character-level encryption and Bit-level Encryption.
We will talk about it briefly:
Character-level Encryption
In this method, the encryption process takes place at the character level. For character-level encryption, substitutional and transposition are the two most common strategies.
Bit-level Encryption
This method encompasses the division of data, like text, graphics, audio, video, etc., into blocks of bits first and then subjected to modification by different methods such as permutation, rotation, exclusive, encoding/ decoding, and so on.
Now that we know the conventional encryption methods, let us talk about the common encryption tools. Here, we will discuss two widely used tools- LastPass and BitLocker.
LastPass
LastPass is one of the most widely used and popular password manager tools available. While it offers the free feature, you can still secure all your personal data and credentials. With this tool at your convenience, you no longer have to memorize or write down passwords somewhere safe. Apart from this, the tools offer a convenient and innate interface, providing the best password security. Users can also employ a two-factor authentication system for enhanced security if possible.
BitLocker
Though a wide range of tools available locally encrypts all the data, BitLocker has been one of the favorites among users. This full-disk encryption tool is built into Windows 10, the most recent Windows operating system. It has the ability to encrypt data on drives with the help of AES (128 and 256-bit) encryption. People have started targeting it as it is a technology built into Microsoft.
This was all about encryption. Now that you know a thing or two about encryption, let us get into another step forward in understanding decrypt vs encrypt, i.e., decryption. Let us decode decryption!
What Does Decryption Mean?
The process of converting an encrypted or encoded message or data into readable form, understood by a computer or human, is called decryption. It is achieved either by unencrypting the message or applying keys to decoding the original information.
In this method, a mathematical process called a decryption algorithm is used for generating the original message text or information as a result of any ciphertext and decryption key. In simple words, one can define decryption as the reverse of an encryption algorithm.
Based on the kind of cryptosystems used, the keys for encryption and decryption could be similar and dissimilar.
Decryption can be accomplished manually, automatically, or with the application of the best decryption software, unique keys, passwords, or codes. They help convert unreadable or unintelligible data into original user data, text files, images, email messages, and directories that users can read and interpret. Decryption can be explained with this simple example:
Suppose 2 x = y; then the establishment of the function key is done, and the users can map all the possible values of x and y. This is what happens during decryption. The example we have used can easily be solved with the help of 'brute-force' methods.
Let us take another example to understand this process:
When a vendor gets an email from their client with all their requirements for a specific project, now, when the vendor opens the email, all the details are in plain text. However, their system decrypts the data upon receiving the email (which is in ciphertext). While traveling over the internet, the ciphertext was unreadable, thereby protecting the two parties' confidential information.
So now you have an idea of what encryption and decryption do and what the whole topic of encryption vs decryption is all about. Next, you must know why these two technologies form an integral component of the computer system.
Why Do We Need Encryption and Decryption?
While encryption and decryption(cryptography systems) do not fully guarantee your security, rest assured that you can still use the technologies to safeguard your privacy and identity. With a well-planned and implemented cryptography system in place, you can protect your data efficiently.
The system works best when automated or set as default and should not be limited to being a feature that the user turns on when they feel it is worth protecting.
If you are still unsure how they help protect your data, we have you covered! Below, we have listed the top four applications of the technology:
Top 4 Applications of Encryption and Decryption
Let us take a look at some of the daily life applications of encryption and decryption:
1. Validation or Digital Signature
Authentication, or the method of proving and verifying information, demands the working of encrypting and decrypting confidential information. A particular digital signature is done based on a document and the signer’s key, and it, therefore, requires encryption and decryption to maintain security.
2. Timestamping
Timestamping is something that is done with the help of encryption and decryption. The process helps confirm that an electronic document or communication was delivered promptly.
3. Electronic Money
When it comes to electronic money, all the transactions are carried out electronically by transferring funds between two concerned parties. All these transactions are encrypted and decrypted with the help of cryptography systems so that sensitive user data can be safeguarded.
4. Encryption and Decryption in Email
Typically, emails are encrypted so that no one outside of a particular email conversation gets access to the contents of the emails. Only the receiver with a private key can decrypt and access the message's information.
All these activities mentioned above take place every day, speaking volumes about the importance of an efficient cryptography system.
Though the working of both processes sounds similar, they are not. Now, we will finally break it to you about encryption vs decryption and how both do the same things(protect confidential data) and yet are quite different.
Encryption vs Decryption
There are numerous parameters if you want to understand the similarities and differences between decryption and encryption. We have listed the top three parameters on which both the technologies differ:
1. Process
Often, machines automatically encrypt(by using a secret key) all the data when a user sends it. Upon receiving, the machine again automatically converts the data to its initial form with the same key algorithm. However, decryption sometimes demands additional steps, such as a confirmation to convert the data back from the unreadable form of figures.
2. Location
The conversion location occurs where a user sends or receives data. Encryption happens at the machine that sends information, whereas decryption takes place at the recipient's location. The encrypted data stays unreadable over the network during the transmission process between the sender and receiver.
3. Algorithm
When a system encrypts data, it uses an algorithm with a key to creating an algorithm that is impossible to hack. The systems use similar algorithms and keys to encrypt and decrypt. However, decryption, it uses a key that is just specific to decoding the text or applies the algorithm in reverse.
There you have it! While we have covered some major differences between the two, there is a better way to wrap things up! We have made a table to help you understand how to differentiate between encryption and decryption based on multiple parameters.
Here you go:
Technology |
Encryption |
Decryption
|
Process |
The process of converting original information or data into an unreadable form is called encryption. |
The process of converting unreadable information or data into its original form is called decryption.
|
Location |
The process of encryption takes place at the sender's end. |
The process of decryption takes place at the receiver's end. |
Primary Function |
The primary function of the process is converting the plain text into cipher text. |
The primary function of the process is converting the cipher text into plain text. |
Technique |
In this process, the system can encrypt any message or data with either a secret key or a public key. |
In this process, the receiver, upon receiving the cipher text or information, converts it into plain or readable text.
|
Functionality |
The encryption process involves the sender sending the data or information to the receiver after encrypting it. |
The decryption process involves the receiver first receiving the information and then converting it into plain text. |
Algorithm |
The system uses the same algorithm with the same key for the encryption-decryption process. |
The system uses only a single algorithm for encryption-decryption with a pair of keys, where one is used for encryption and the other for decryption. |
Application areas |
It maintains integrity, provides security to data always, protects privacy, and data across a wide range of devices, etc. |
It provides techniques such as encryption techniques that can safeguard data and communication, cryptographic techniques such as digital signature, MAC and digital signatures against cybercrimes and forgeries. |
Uses |
This technology is useful for modern data security like safeguarding sensitive electronic data such as credentials and emails. |
This technology has found its usefulness in army communications, time stamping electronic commerce, chip-based card payments, digital currencies, etc. |
Types |
Types of encryption- symmetric and asymmetric encryption. |
Types of cryptography- symmetric key cryptography and asymmetric key cryptography. |
Example |
An employee sending important documents to his/her/their manager in a secret code that only the manager understands.
|
The manager receives the essential documents from his/her employee and decodes the secret code into an understandable form. |
We hope the table gave a clear picture of what all encryption vs decryption is all about.
To Conclude
Both decrypt and encrypt processes come under a cryptology system that is a combination of cryptography and cryptanalysis. While cryptography encompasses ways to ensure security with the application of encoding messages to make them unreadable, cryptanalysis means decoding messages where the unreadable form is converted back to its original form. Both technologies together work to protect data from cybercriminals or any potential threats.
Opinions expressed by DZone contributors are their own.

Comments