AI-Powered Defenses Against Clickjacking in Finance
Clickjacking is not a new online threat, but it continues to evolve and stay relevant. This article discusses AI-driven techniques for combating this attack.
Join the DZone community and get the full member experience.
Join For FreeClickjacking is a well-known cyber-attack that has been present in web-based platforms for almost two decades now. It refuses to go away, with a new attack vector surfacing pretty regularly. One of the primary reasons this attack has remained relevant is due to the fact that it provides an attractive option for hackers to steal people’s money.
With the evolution and rapid growth of digital banking platforms and self-serve money movement capabilities, it has become a playfield for the bad actors to exploit people’s innocence and make money through apparently harmless mouse clicks. At the beginning of this year, 2025, a new pattern of clickjacking called double-clickjacking [1] has surfaced, which underscores the fact that this vulnerability is going to appear in different forms in web platforms, and the battle to protect people’s assets will continue.
Background and Attack Techniques
Clickjacking was first discovered by Jeremiah Grossman and Robert Hansen in 2008. Normally, this attack is made by leveraging the iFrame HTML component. A malicious website may design an attractive webpage inviting users to enter some information and click a link or a button.
Behind the scenes, using iFrame, the malicious website sends information collected from the user to a legitimate website (assume your bank website). This will allow an active session in the bank on behalf of the user and then cause further damage such as account takeover or money transfer. The users are generally tricked into visiting the malicious website via phishing or social engineering strategy, such as sending a nicely crafted email having a link to the malicious website, creating lucrative money-making advertisements (win prize!) in social media platforms, and so on.
While this attack is now well known in the industry and there is general awareness among the young population, the elderly people with less technical awareness and who are dependent on digital platforms, especially for finance management, often fall victim to this attack.
The techniques to execute this attack have evolved over time in the last decade and a half. The technique described in the previous paragraph is generally called the classic technique of clickjacking. Similar other classic techniques are overlaying invisible buttons, images in legitimate websites, using transparent layer to hide malicious web content, etc.
As time evolved, various other types of attack patterns came up, such as Likejacking (trick user to like social media post without consent), Cookiejacking (trick user to steal browser cookie), Cursorjacking (user thinks clicking a certain UI element in a web page but actually clicks somewhere else), etc.
The modern techniques to make this attack are password manager attack and browserless clickjacking, to name a few [2]. Password manager attack exploits the autofill feature of input fields on a webpage. This attack tricks the password manager into filling in stored credentials in a malicious form, and through this technique, attackers collect users' credentials and then use them to log in across several services for financial gain.
Needless to say, financial platforms will be the first target of this attack as this provides the opportunity to get people’s banking credentials and steal money from their accounts. Browserless clickjacking demonstrates the perfect example of how the attack surface has changed. Instead of the traditional web browser where clickjacking is generally targeted, browserless clickjacking targets mobile devices as attack surfaces. It often targets the notification feature, taking advantage of the delay between a notification message and the appearance of the actual notification in the mobile device.
As mentioned at the beginning of this article, in January 2025, a new type of clickjacking attack named double-clickjacking has been reported, which bypasses the proven prevention strategy of clickjacking. This attack technique has been reported by security researcher Paulos Yibelo. This attack doesn’t leverage traditional iFrame in a browser, instead it leverages user interaction and timing.
In this attack, the user visits a malicious website that asks the user to enter something like CAPTCHA, which typically requires a double-click event. After the first click, the parent window in the browser is changed to a legitimate website the attacker plans to exploit. The victim doesn’t notice that and makes the second click, which apparently happens on the legitimate website, potentially exposing sensitive information about the victim to the attacker. In this case, as the URL of the parent window is changed in the browser, it evades the traditional HTTP header-based security solutions. Figure-1 demonstrates the sequence of events in a double-clickjacking attack.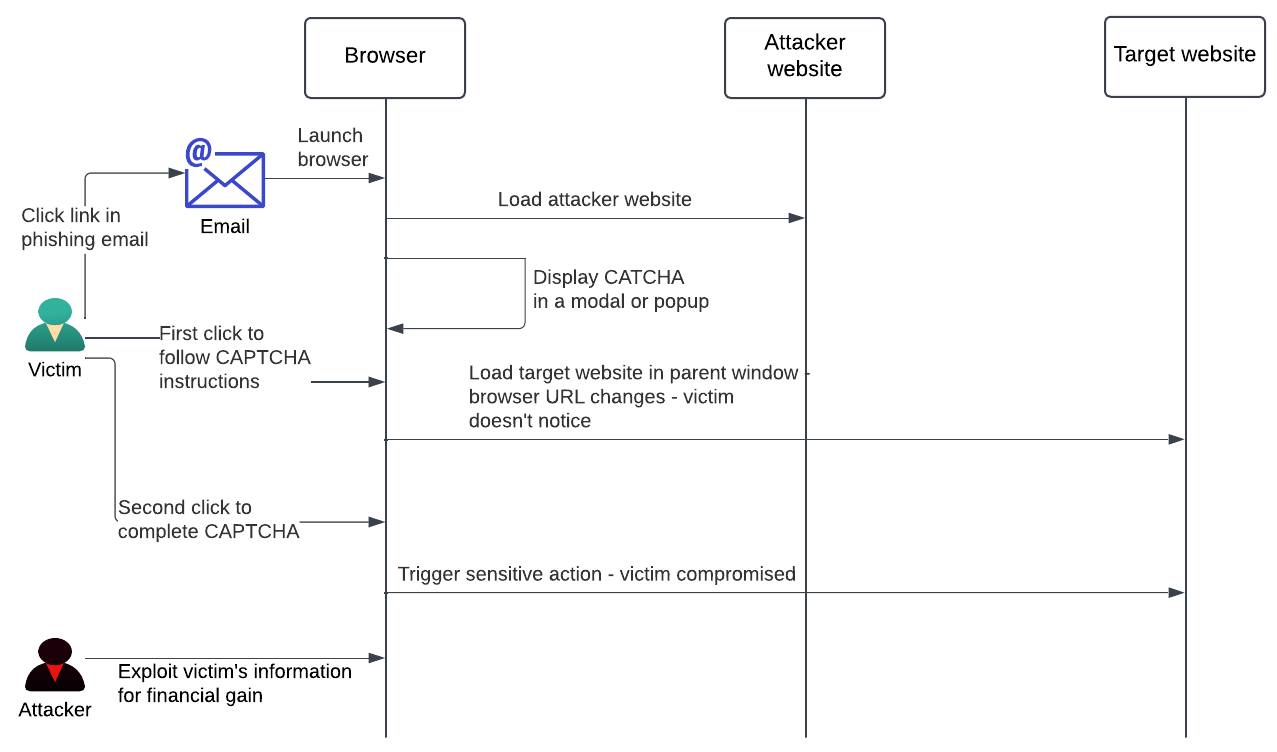
Figure 1: Double-Clickjacking Attack
Clickjacking Implication in Finance Sector
- The most common threat of clickjacking is trick a user to make unauthorized financial transactions causing direct financial loss via credit card purchase or draining money from bank account. In addition to that unauthorized cryptocurrency transactions could be catastrophic where funds can get stolen from digital wallets.
- Identity theft is another critical damage that this attack can cause to victims. In this case, personally identity information is stolen via clickjacking and attacker later uses that information to target various financial accounts of the victim or sell information in dark web for further financial exploitation.
- Operational disruption is another major threat of clickjacking. By distributing malware in infrastructure, this attack may bring down an application, causing operational disruption and leading to financial damage to an organization. The mode of attack could be manifold, such as injecting ransomware payloads in web portals or spreading botnet malware.
Regardless of the methodology of the attack or the amount of financial damage, organizations face reputational damage, leading to a loss of customer trust. A real-world example of a clickjacking threat was reported in PayPal in 2022 [3]. The vulnerability could allow an attacker to steal money from a victim's PayPal account or leverage the same exploit to add money to the attacker’s PayPal account.
Current Prevention Approaches
A decade ago, when industry was still learning about this vulnerability, penetration testing of applications were reporting this as a major issue, it was found that 97% of bank and financial institutions don’t have clickjacking protection in their website [4]. Since then, organizations have taken steps to mitigate this issue.
The core prevention techniques for clickjacking attacks are HTTP headers to be set on the server side of web applications to either completely block a website from being iFramed or selectively allow iFrame by trusted websites.
X Frame Header and Content Security Policy Frame Ancestor directives are used together to control iFrame-ing of a website to prevent clickjacking attack.
- If we do not want our websites to be iFramed at all then following is the setting of the HTTP headers that needs to be set on the server side.
JavaScript
Content-Security-Policy: frame-ancestors 'none' X-Frame-Options: DENY - If we want our websites to be iFramed only within subdomains under the same domain, then we need to use the following settings.
JavaScript
Content-Security-Policy: frame-ancestors 'self' X-Frame-Options: SAMEORIGIN - Finally, if we want to allow our website to be whitelisted only within certain partners (e.g. in case of B2B model) website, then the partner websites need to be whitelisted under frame ancestor directive.
JavaScript
Content-Security-Policy: frame-ancestors https://partner-website.com X-Frame-Options: DENY
Apart from X Frame Options and Content Security Policy, the SameSite attribute value of a cookie helps prevent clickjacking and other web vulnerabilities. Setting the SameSite attribute as Lax or Strict blocks access to the cookie if a malicious website attempts to iFrame the legitimate website.
Set-Cookie: CookieName=CookieValue; SameSite=Strict;
OR
Set-Cookie: CookieName=CookieValue; SameSite=Lax;Client-side protections are also available, such as a frame-bursting script to prevent a page from being loaded in an iFrame, modern Intersection Observer JavaScript API, or browser extensions(NoScript, NoClickjack, etc.). However, it is always recommended to use a server-side HTTP header-based solution, as client-side protection can be evaded by an attacker.
AI Powered Detection Techniques
The solution options discussed in the above section are all prevention techniques. There has been several impactful research studies in which techniques to detect clickjacking threats in malicious websites have been proven using AI and machine learning. Using AI-based techniques to detect clickjacking or other similar web vulnerabilities is at an early stage of adoption in the industry.
Extreme Learning Machine (ELM) Technique
ELM is a fast, single-hidden-layer feedforward neural network (SLFN) that has been used by researchers [5] to detect malicious URLs in a webpage vulnerable to a clickjacking attack. The technique uses a URL extraction method from a webpage and feeds the URLs to the ELM algorithm, and ELM predicts the vulnerable URLs among the list of URLs it was fed.
Support Vector Model (SVM) can be used to perform the same as ELM as well, but SVM requires more training dataset compared to ELM according to the research.
Convolutional Neural Network (CNN)
Likewise, CNN is another technique that researchers have proven to be an effective technique to detect malicious content in webpage that may cause clickjacking attack [6]. CNN is powerful as it can operate on unstructured data. Researchers have used image processing and feature extraction technique to identify vulnerable visual element in user interface of a webpage to detect clickjacking potential.
User Behavior Analytics (UBA)
User behavior analytics, coupled with machine learning, is another technique researchers have vouched for to detect cyber-attacks like clickjacking [7]. It uses deep learning methodology, and the solution is broken into two parts. In part one, as part of model training, user behavior is captured as a sequence of ordered events and fed to the deep learning model. The second part is to utilize the learning and flag user behavior in web platform as regular or irregular to identify cyber threats like clickjacking.
Anti-Phishing Using Machine Learning (APuML)
This technique targets detection of attacks using clickjacking in mobile devices [8]. It uses random forest as the algorithm and claims 93.85% accuracy in detecting malicious content in web application. This technique extracts all static and site popularity feature from a given URL and create a feature set. Then random forest is applied to the feature set to obtain the vulnerability result.
PhishCatcher Google Chrome Extension
This is a client-side defense mechanism using advanced machine learning algorithms [9]. Researchers developed a Chrome extension, PhishCatcher, that uses a random forest algorithm under the hood to determine if a login page is compromised. This approach has a downside, though, as it requires user to install the extension in their browser, which they might be reluctant to do, and therefore, it is challenging for mass scale adoption.
Challenges of AI-Powered Solution Implementation
The AI-powered solutions provided above are detection techniques. No AI-driven solution is available at this moment to prevent the issue from happening. Implementing AI-based detection techniques in applications has several challenges.
- Preparing comprehensive dataset to cover various clickjacking techniques as part of the data collection and labelling is a complex effort due to the evolving nature of attack techniques by the perpetrators.
- The dynamic nature of modern web applications makes it hard to extract features for AI models.
- Implementing real-time detection in webpages using AI could impact performance or responsiveness of webpages, impacting user experience.
- At the same time AI based solution implementation for prevention is significantly costlier compared to the existing server-side HTTP header-based protection. Although it can be argued that the cost for implementation and maintenance gets offset due to the financial and reputational protection it provides to an organization.
Conclusion
The battle to exploit financial systems with creative attack techniques and build more powerful and robust solutions to prevent exploitation will continue. Therefore, though clickjacking was reported more than a decade ago, it continues to stay relevant like most of the other cyber-attacks due to new attack surfaces and techniques. This attack has evolved from basic UI manipulation to serious cybersecurity risk in web platforms particularly targeting the finance domain. It is currently ranked 4th as an Insecure Design under the OWASP list of vulnerabilities [10].
The combination of AI-driven detection techniques to alert users upfront and the traditional HTTP header-driven prevention technique is the appropriate hybrid approach going forward to protect people and their assets in finance and other domains.
References
- Double Clickjacking
- Password Manager and Browserless Clickjacking Attack
- PayPal Clickjacking
- Lack of protection in early 2010
- Extreme Learning Machine (ELM)
- Convolutional Neural Network (CNN)
- User Behavior Analytics (UBA)
- Anti Phishing using Machine Learning (APuML)
- PhishCatcher Extension
- OWASP Top 10
Opinions expressed by DZone contributors are their own.

Comments