Architecture Patterns: API Gateway
An API Gateway optimizes client-service interactions and enhances security, but needs careful design to avoid potential pitfalls. Proper use ensures scalability.
Join the DZone community and get the full member experience.
Join For FreeWhat Is an API Gateway?
An API Gateway is a tool that acts as an intermediary for requests from clients seeking resources from servers or microservices. It manages, routes, aggregates, and secures the API requests.
Like previous patterns we have explored, this is often described as a “microservices context” pattern, but this is not necessarily the case. It could be worth using in many “not microservices” cases and sometimes shouldn’t be used in microservices.
Let’s go deeper into the details.
Request Routing
This involves taking a client’s request and determining which service/services should handle it. It could have different aspects:
- Dynamic routing: API Gateways can dynamically route requests based on URL paths, HTTP methods, HTTP headers, etc. NB: This could be useful in the case of a multi-tenancy context. (See Architecture Patterns: Multi-tenancy with Keycloak, Angular, and Spring Boot)
- Service versioning: Allows multiple versions of a service to coexist; Clients can specify which version they want to interact with. NB: This is very useful in microservices, but also in SOA or any kind of exposed API that needs to allow different versions.
- Load distribution: Some gateways can distribute load to multiple instances of a service, often in conjunction with a load balancer.
API Composition
Combining multiple service requests into a single response to streamline client communication. This could be done with:
- Aggregation: For instance, a client might want details about a user and their orders. Instead of making separate calls, a single call is made, and the gateway fetches data from the user and order services, aggregating the results.
- Transformation: Transforming data from multiple services into a format expected by the client
NB: This part could also be achieved with another pattern called backend for the frontend (BFF). It could also be combined with the gateway depending on your needs. (See Backend For Frontend (BFF) Pattern)
Rate Limiting
Restricting the number of requests a user or service can make within a given time frame. This is very useful for protecting your API and can have several uses:
- Client-specific limits: Different clients can have different rate limits based on their roles, subscription levels, etc.
- Burst vs. sustained limits: Allow short bursts of traffic or limit requests over a more extended period
- Preventing system overload: Ensures that services aren’t overwhelmed with too many requests, leading to degradation or failures
Security
Ensuring that only authorized requests reach the services could also provide client-specific authentication.
- Authentication: Verifying the identity of clients using methods like JWT, OAuth tokens, API keys, etc.
- Authorization: Determining what an authenticated client is allowed to do
- Threat detection: Some gateways can identify and block potential security threats like DDoS attacks, SQL injections, etc. (Related to the previous point)
Caching
Caching is temporarily storing frequently used data to speed up subsequent requests. This depends on the caching strategy you are trying to achieve. It could also be done in BFF, maybe not at all.
- Response caching: Store service responses for common requests to avoid redundant processing.
- TTL (Time-To-Live): Ensuring cached data isn’t too old, defining how long it should be stored
- Cache invalidation: Mechanisms to remove outdated or incorrect data
Service Discovery
This refers to finding the network locations of service instances automatically.
- Dynamic location: In dynamic environments like Kubernetes, services might move around. The gateway keeps track of where they are, so the consumer doesn’t have to worry about it; it’s a way of decoupling the scalability effects from the client side.
- Health checks: If a service instance fails a health check, the gateway won’t route requests to it. It prevents consumers from requesting to reach a down service, which improves the quality of failure management and may also prevent some types of exploits.
- Integration with Service Discovery tools: Often integrated with tools like Consul, Eureka, or Kubernetes service discovery
Analytics and Monitoring
Analytics and monitoring relate to gathering data on API usage and system health. DevOps would be very interested in this feature, especially because it allows them to have a good view of the activity on a whole system, regardless of its complexity.
- Logging: Capturing data about every request and response
- Metrics: Tracking key metrics like request rate, response times, error rates (classified by HTTP code), etc.
- Visualization: Integration with tools like Grafana or Kibana to visualize the data
- Alerting: Notifying system operators if something goes wrong or metrics breach a threshold
This could be a representation:
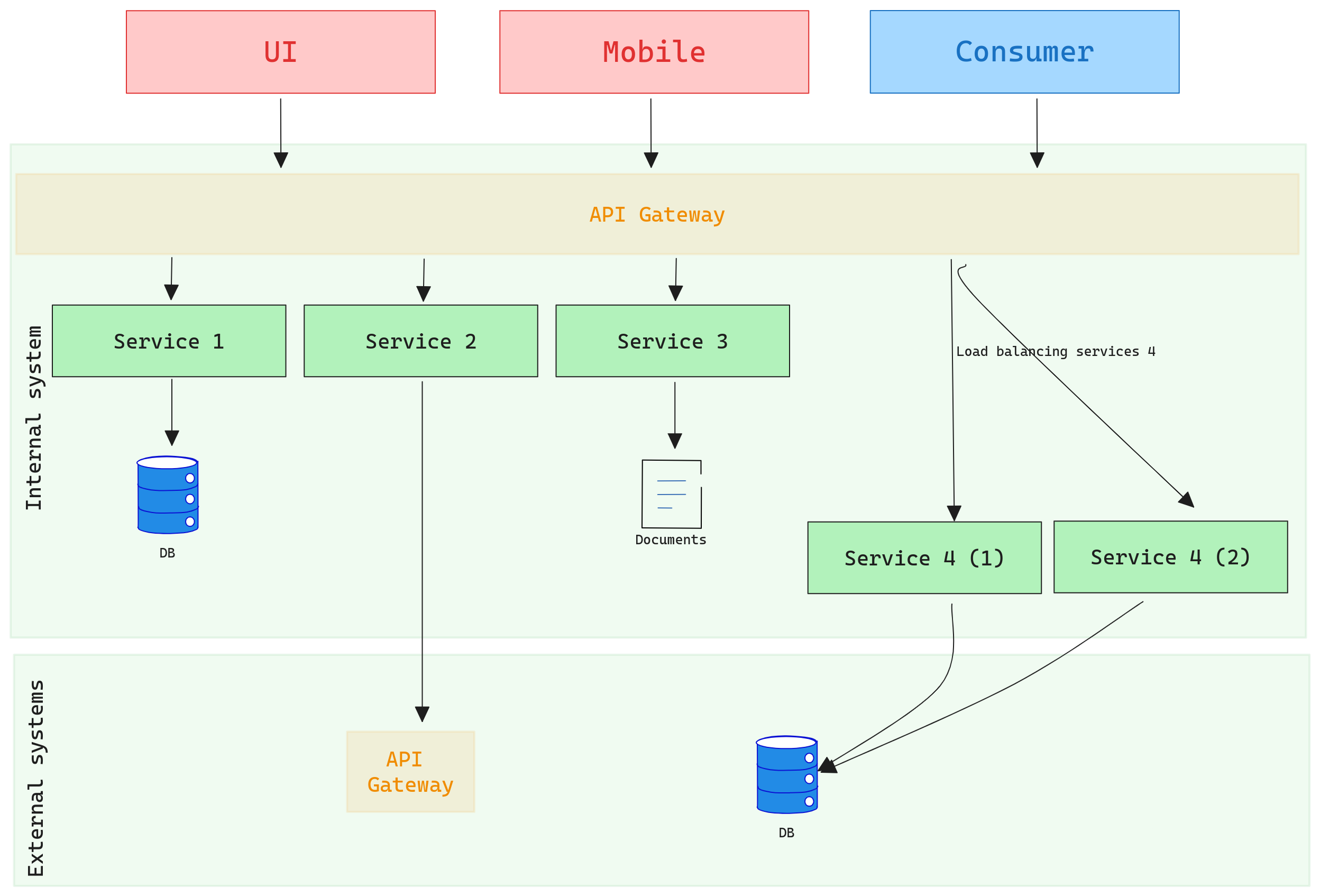
Benefits and Trade-Offs
Benefits
Simplified Client
By having a unified access point, clients can communicate without knowing the intricacies of the backend services. This simplifies client development and maintains a consistent experience, as they don’t need to handle the varied endpoints and protocols directly.
Centralized Management
A major advantage of the API Gateway is that common functionalities such as rate limiting or security checks are handled in a single place. This reduces redundant code and ensures a consistent application of rules and policies.
Cross-Cutting Concerns
Concerns that apply to multiple services, like logging or monitoring, can be handled at the gateway level. This ensures uniformity and reduces the overhead of implementing these features in every single service.
Optimized Requests and Responses
Based on the client’s needs (e.g., mobile vs web vs desktop), the API Gateway can modify requests and responses. This ensures clients receive data in the most optimal format, reducing unnecessary payload and enhancing speed.
Increased Security
By centralizing authentication and authorization mechanisms, the gateway provides a consistent and robust security barrier. It also can encrypt traffic, providing an added layer of data protection.
Stability
Features like circuit breaking prevent overloading a service, ensuring smooth system operation. The gateway can quickly reroute or pause requests if a service becomes unresponsive, maintaining overall system health.
Trade-Offs
Single Point of Failure (SPOF)
Without appropriate high availability and failover strategies, the API Gateway can become a system’s Achilles heel. If it goes down, all access to the backend services may be cut off. This then became a very strategic and sensitive point for the production environment, but not only that, when working on the gateway in a given environment, all the services that depend on that access are affected, so it has to be considered in both the production and development aspects.
Complexity
Introducing an API Gateway adds another component to manage and operate. This can increase deployment complexity and necessitate additional configuration and maintenance. I would agree with Elon Musk that “the best part is no part" - this could be true for aerospace development as well as software engineering.
Latency
As all requests and responses pass through the gateway, there’s potential for added latency, especially if extensive processing or transformation is involved. The same as the previous point, usually more components on the transaction path imply more time.
Scaling Issues
High traffic can stress the API Gateway. Proper scaling strategies, both vertical and horizontal, are essential to ensure the gateway can handle peak loads without degrading performance. (Linked to SPOF point)
Potential Inefficiencies
Without careful design, the gateway can introduce inefficiencies, such as redundant API calls or unnecessary data transformations. Proper optimization and continuous monitoring are crucial.
Conclusion
The API Gateway, like many architectural patterns, offers a robust suite of functionalities that cater to an array of needs in modern software systems. By providing a unified entry point for client requests, it streamlines, secures, and optimizes interactions between clients and services, especially in microservices-based systems. However, as with any tool or pattern, it comes with its unique set of challenges. The potential for increased latency, the need for special scaling considerations, and the risk of introducing a single point of failure underscores the importance of careful planning, design, and continuous monitoring. When employed judiciously, and with a thorough understanding of both its benefits and trade-offs, an API Gateway can prove invaluable in achieving scalable, secure, and efficient system interactions. As always, architects and developers must weigh the pros and cons to determine the fit of the API Gateway within their specific context, ensuring they harness its power while mitigating potential pitfalls.
Published at DZone with permission of Pier-Jean MALANDRINO. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments