Asymmetric JCE Cryptography API Using RSA Algorithm in Mule 4
See how to encrypt and decrypt stream, byte[], or string using the Asymmetric JCE Cryptography module in Mule 4 taking an API as the reference implementation.
Join the DZone community and get the full member experience.
Join For FreeThis article provides how to encrypt and decrypt stream, byte[], or string using the Asymmetric JCE Cryptography module in Mule 4 taking an API as the reference implementation.
What Is Asymmetric JCE Cryptography?
The Java Cryptography Extension (JCE) provides a framework and implementations for encryption, key generation and key agreement, and Message Authentication Code (MAC) algorithms. Types of encryptions supported are symmetric, asymmetric, block, and stream ciphers.
Asymmetric encryption is a strong encryption technique which uses a key pair. The key pair consists of a public key and a private key. Data or message encrypted using the private key can only be decrypted using the public key and vice versa.
Asymmetric key encryption can be implemented in a number of algorithms. Some of the common algorithms are RSA, DSA and Elliptic Curve. The most commonly used asymmetric key algorithm is RSA.
MuleSoft Cryptography Strategies
MuleSoft provides various encryption/decryption strategies to encrypt your messages.
Encryption strategy |
Description |
JCE encrypter |
Encrypts stream, byte[], or string. |
XML encrypter |
Encrypts string; encrypts individual fields using xpath expressions. |
PGP encrypter |
Encrypts stream, byte[], or string; applies tighter security (relative to JCE and XML); increases processing load (relative to JCE and XML). |
About This API
Key Benefits and Problem Statement
Security has always been the most important aspect when developing integration solutions, especially in the banking and finance domain. In many APIs, sensitive information is sent over the channel in raw format, which is prone to threats like a man in the middle of an attack. While sending data securely over the channel to third parties, it is very important that data is always encrypted so it becomes unreadable for unauthorized entities.
Solution
A proposed solution is a reusable API with a POST and a GET method using Asymmetric JCE Cryptography with RSA algorithm. The POST method accepts the sensitive information, encrypts the data and signs it with private key and stores it in an object store. The GET method is used to fetch the data every time the sensitive information is used in an application from object store in an unreadable format, validates the data and decrypts using a public key.
API Overview
- Create a Keystore using Keytool
- Add a cryptography connector in Anypoint Studio
- Project overview of jce-asymmetry-api
- Encryption of sensitive data using private key and storing in Object Store
- Signing and storing in Object Store
- Validation of sensitive data against the signed data retrieved from Object Store
- Decryption of unreadable data using public key for authorized entities
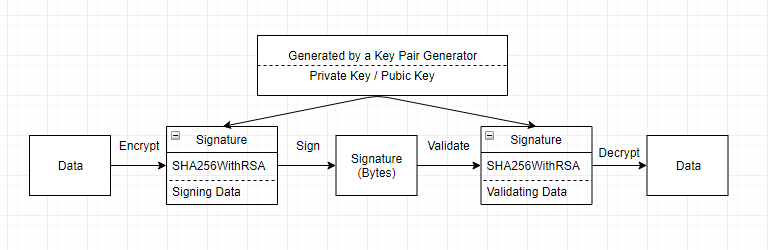
Step 1: Create a Keystore Using Keytool
Create a Temp folder and execute the following command.
C:\Temp>keytool -genkey -keyalg RSA -alias sampleAlias -keystore cryptokeystore.jks -storepass password123 -keypass password123The principal information necessary to configure JCE Encrypter using keystore are
- Name of the keystore: cryptokeystore.jks
- Password of the keystore: password123
- Name of the key: crypto
- Password of the key: password123
- Name of the alias: sampleAlias
Step 2: Add a Cryptography Connector in Anypoint Studio
** Installing encryption/cryptography connector in studio from anypoint enterprise security update site is currently unavailable for Mule 4.
Hence, download the dependency from exchange.
Else add the dependency in pom.
<dependency>
<groupId>com.mulesoft.modules</groupId>
<artifactId>mule-cryptography-module</artifactId>
<version>1.0.0</version>
<classifier>mule-plugin</classifier>
</dependency>Step 3: Project Overview of jce-asymmetry-api
- Current application developed in studio 7.1.3 and deployed in Mule runtime version 4.1.4.
- Create a API specification (RAML) in design center.
#%RAML 1.0
title: jce-asymmetry
description: This API enable global encryption and decryption of data while storing and retrieving from object store
/jce-asymmetry:
post:
description: Method used to store sensitive data with data key
queryParameters:
datakey:
responses:
201:
body:
application/json:
example: {response: Data Posted Successfully!}
/{datakey}:
description: Retrieve data from store using data key
get:
responses:
200:
body:
application/json:
example: {response: Data fetched sucessfully!}3. Mule application structure specifying the API definition file.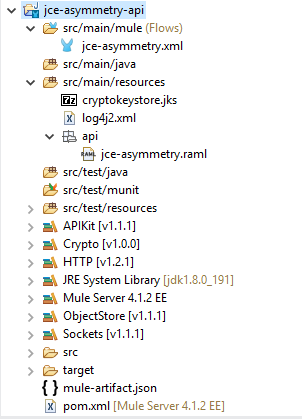
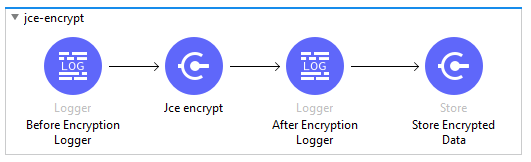
Step 4: JCE Asymmetry Cryptography — Encryption
- Encryption of sensitive data using private key and storing in Object Store.
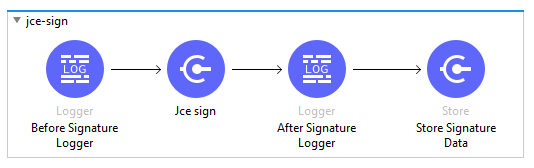
Step 5: JCE Asymmetry Cryptography — Signature
- Signing and storing in Object Store.
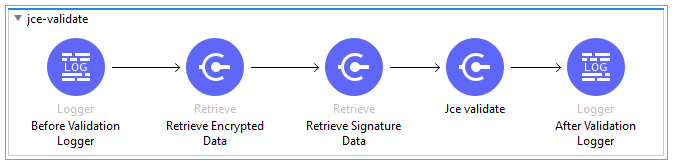
Step 6: JCE Asymmetry Cryptography — Validation
- Validation of sensitive data against the signed data retrieved from Object Store.
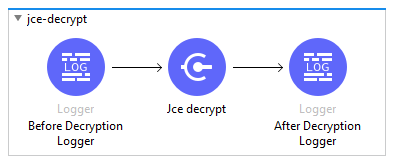
Step 7: JCE Asymmetry Cryptography — Decryption
- Decryption of unreadable data using public key for authorized entities
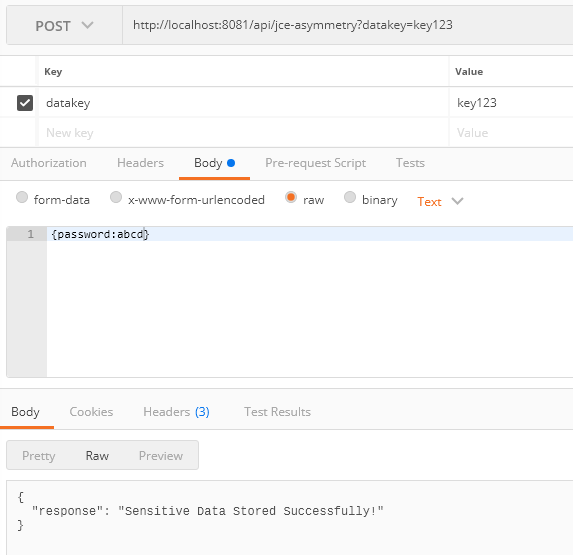
Testing the API
- Create sample mule application and use the POST method in a HTTP Request call to store sensitive data using unique object store key.
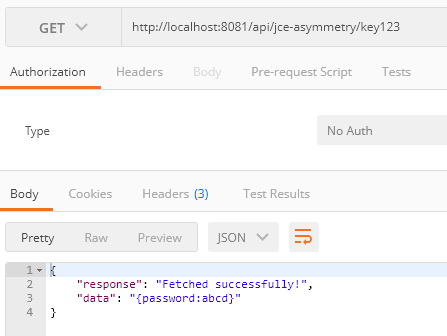
- Use the GET method in an application to retrieve the sensitive data using the same object store key.
- A glimpse of the log file for the above implementation.
**********************************************************************
* Application: jce-asymmetry-api *
* OS encoding: windows-1252, Mule encoding: UTF-8 *
* *
**********************************************************************
INFO 2018-12-13 12:17:57,674 [[MuleRuntime].cpuLight.05: [jce-asymmetry-api].post:\jce-asymmetry:jce-asymmetry-config.CPU_LITE @7fa378] 0-047263d1-fea3-11e8-b138-80a5899fd9bforg.mule.runtime.core.internal.processor.LoggerMessageProcessor: before encrypting: {password:abcd}
INFO 2018-12-13 12:17:58,191 [[MuleRuntime].cpuLight.05: [jce-asymmetry-api].post:\jce-asymmetry:jce-asymmetry-config.CPU_LITE @7fa378] 0-047263d1-fea3-11e8-b138-80a5899fd9bforg.mule.runtime.core.internal.processor.LoggerMessageProcessor: after encrypt: ?A/????????L('?4?eka}3?Q2??J-1?M??6r?B??c??pz*L?k??%????
(??mG?R ?????4e??5?=1.????!?h'???*
^?v?c?
?aS?s?w?
???~??*???qK?n??/4L
????f?y?)}j?`S?D?h???7?b?l? ????V?j?
?&}w?*?luqUz?g?~pU?L?"GV#?/???oO?
qby??#$y??rU?6?
??"?[
INFO 2018-12-13 12:17:58,388 [[MuleRuntime].cpuLight.05: [jce-asymmetry-api].post:\jce-asymmetry:jce-asymmetry-config.CPU_LITE @7fa378] 0-047263d1-fea3-11e8-b138-80a5899fd9bforg.mule.runtime.core.internal.processor.LoggerMessageProcessor: before sign: ?A/????????L('?4?eka}3?Q2??J-1?M??6r?B??c??pz*L?k??%????
(??mG?R ?????4e??5?=1.????!?h'???*
^?v?c?
?aS?s?w?
???~??*???qK?n??/4L
????f?y?)}j?`S?D?h???7?b?l? ????V?j?
?&}w?*?luqUz?g?~pU?L?"GV#?/???oO?
qby??#$y??rU?6?
??"?[
INFO 2018-12-13 12:17:58,513 [[MuleRuntime].cpuLight.05: [jce-asymmetry-api].post:\jce-asymmetry:jce-asymmetry-config.CPU_LITE @7fa378] 0-047263d1-fea3-11e8-b138-80a5899fd9bforg.mule.runtime.core.internal.processor.LoggerMessageProcessor: after sign: duLCTboEQjdepSA4KjbUAhuwdrKvNWgMsLQvwwc1WD8NpTmi7ZIVqzGZRx9Sye4ziLZoouHe58ePakJnOM/ql1HXF0FkXTvKYD/OmrzLX2nuLowk/2bWh+xY47cwcvctSCfN3BpIUwMqbFq1dAC+/c96DuZZAK0a+CNx8Z58Dykvh1Tz35KVS6YbI2JdYHVG2a8O4Bsd21L8krQ43v4Rhygo8xuNouPOHSeZrKZdfPl5M9iKk3/tLFphYBftYMvA7q/Xmnt/K07z95mTnc6cTVLxqVlUwD+ketBgmp4at0ZycWG3Mt1/A3sjrls9y/0Mj39Pwgw8HFBf40TAztdzLA==
INFO 2018-12-13 12:18:06,757 [[MuleRuntime].cpuLight.01: [jce-asymmetry-api].get:\jce-asymmetry\(datakey):jce-asymmetry-config.CPU_LITE @f45d68] 0-0b1833e0-fea3-11e8-b138-80a5899fd9bforg.mule.runtime.core.internal.processor.LoggerMessageProcessor: Before validating
INFO 2018-12-13 12:18:06,807 [[MuleRuntime].cpuLight.01: [jce-asymmetry-api].get:\jce-asymmetry\(datakey):jce-asymmetry-config.CPU_LITE @f45d68] 0-0b1833e0-fea3-11e8-b138-80a5899fd9bforg.mule.runtime.core.internal.processor.LoggerMessageProcessor: After validating
INFO 2018-12-13 12:18:06,876 [[MuleRuntime].cpuLight.01: [jce-asymmetry-api].get:\jce-asymmetry\(datakey):jce-asymmetry-config.CPU_LITE @f45d68] 0-0b1833e0-fea3-11e8-b138-80a5899fd9bforg.mule.runtime.core.internal.processor.LoggerMessageProcessor: Before decryption: ?A/????????L('?4?eka}3?Q2??J-1?M??6r?B??c??pz*L?k??%????
(??mG?R ?????4e??5?=1.????!?h'???*
^?v?c?
?aS?s?w?
???~??*???qK?n??/4L
????f?y?)}j?`S?D?h???7?b?l? ????V?j?
?&}w?*?luqUz?g?~pU?L?"GV#?/???oO?
qby??#$y??rU?6?
??"?[
INFO 2018-12-13 12:18:06,986 [[MuleRuntime].cpuLight.01: [jce-asymmetry-api].get:\jce-asymmetry\(datakey):jce-asymmetry-config.CPU_LITE @f45d68] 0-0b1833e0-fea3-11e8-b138-80a5899fd9bforg.mule.runtime.core.internal.processor.LoggerMessageProcessor: Decrypted data is: {password:abcd}Note: The complete source code is available in GitHub.
Summary
Asymmetric encryption using RSA algorithm is a relatively new technique and is preferred over symmetric encryption even though asymmetric encryption takes relatively more time than the symmetric encryption. Symmetric encryption uses a single key that needs to be shared among the people who need to receive the message while asymmetrical encryption uses a pair of public key and a private key to encrypt and decrypt messages when communicating. Make use of this reusable API to securely send data over a channel to third parties.
Opinions expressed by DZone contributors are their own.

Comments