AWS Web Application and DDoS Resiliency
Let me start by explaining the term "DDoS" and then we will get into how AWS helps in creating resiliency against these kinds of attacks.
Join the DZone community and get the full member experience.
Join For FreeLet me start by explaining the term "DDoS" and then we will get into how AWS helps in creating resiliency against these kinds of attacks.
DDoS
DDoS stands for ‘Distributed Denial of Service’ attack in which an attacker attempts to disrupt the online services by overwhelming the target with huge network traffic. It is achieved by exploiting multiple machines using malware and then using them for crafting a surge in network requests on the actual target machine which causes the bandwidth to choke, resulting in a service breakdown. Sometimes DDoS attacks are also used to hide some severe types of incursions where the attacker uses them for producing distractions.
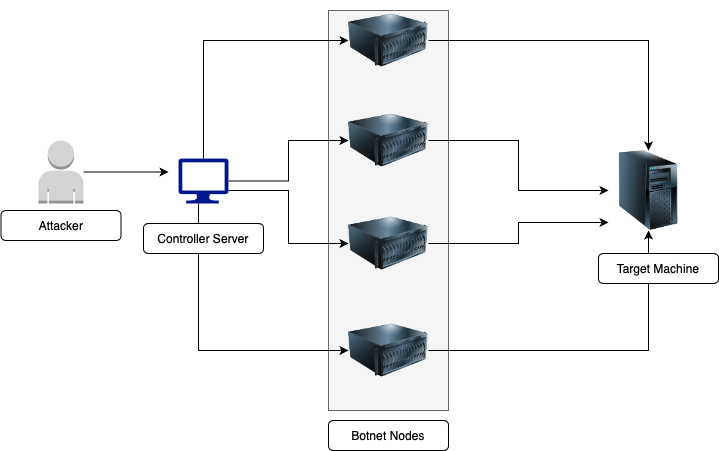
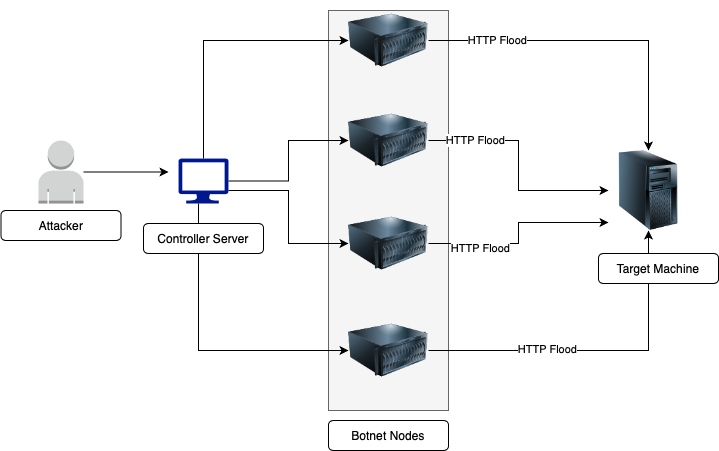
Malicious nodes behave as Botnet Nodes. These are compromised by malware through which the attacker gets their remote access.
Open Systems Interconnection (OSI) Model and Threats
Below is a depiction of a DDoS attack over the layers of an OSI model and the shared responsibility model offered by AWS services. This will be followed by some of the common DDoS attack types.
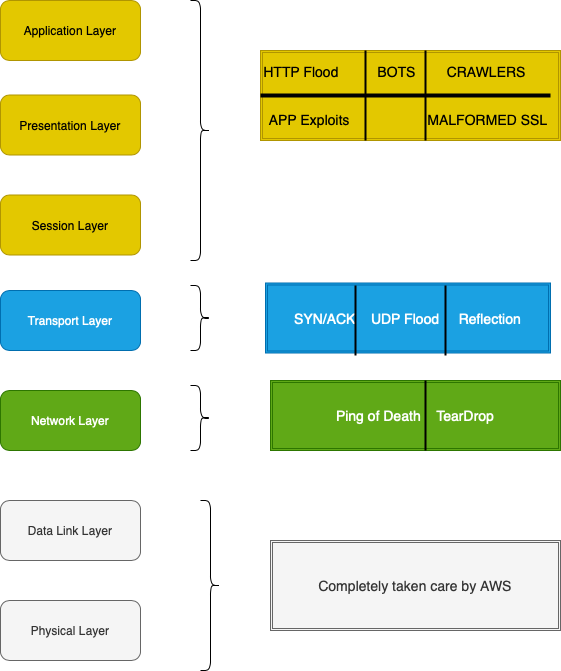
DDoS Attack Types
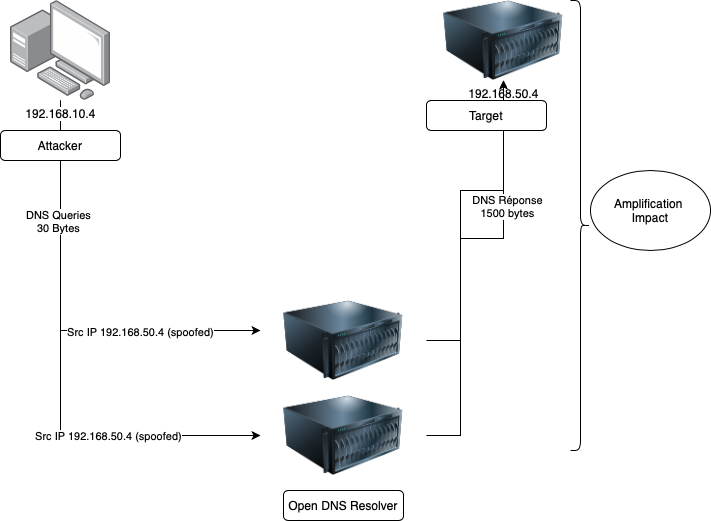
Reflection Attack
There are tools that are readily available for crafting such attacks. These tools majorly use User Datagram Protocol (UDP) protocols to send requests for some information. Though in some cases Transmission Control Protocol (TCP) is also used
In this kind of attack, the Bad Actor spoof the target’s IP address and starts sending the requests to the vulnerable services. The server responds back with the information to the spoofed IP (Target Machine), instead of the machine generating these requests. For further amplifying the impact of these attacks, the attacker identifies vulnerable services where the response payload is considerably larger than the original requests. This is also called an amplification reflection attack.
The severity of the attack can be measured through BAF (Bandwidth Amplification Factor). It is the ratio of the length of UDP payload response (amplified) in bytes versus the length of UDP payload request in bytes.
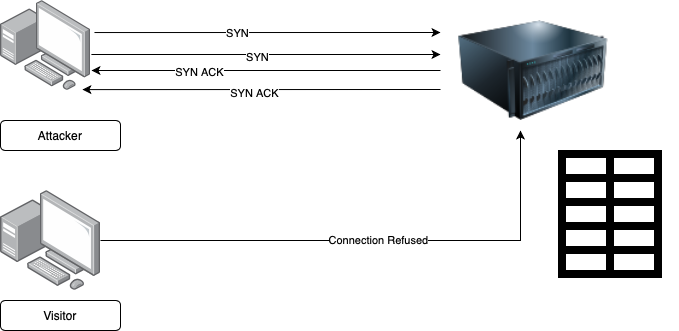
SYN Flood
SYN Flood attack exploits the 3-way-TCP-handshake. Let’s first understand the 3-way-TCP-handshake mechanism.
- The client initiates the connection with the SYN (Synchronize) packet to the server.
- The server responds back with SYN-ACK to the client on successfully receiving the SYN packet and starts waiting for the ACK packet from the client.
- The client responds with an ACK packet to form the connection.
Attackers exploit this mechanism by not sending the ACK packets back to the server but by continuing to send SYN packets. It causes the consumption of the connection state tables, present in many of the network components like load balancers, firewall, and IPS, etc. Once the tables are exhausted, they avoid receiving the new SYN packet or new connection requests from any source. SYN floods are often called half-open attacks.
Further, to avoid being detected, attackers use networks like Tor or spoofed/forged IPs.
Application Layer DDoS Attacks
Application layer DDoS attacks are designed to target the specific vulnerabilities of the application. The main intention of the attacker is to make the service unavailable to the intended and legitimate users. These attacks are volumetric attacks where an extremely large number of requests per second are sent to the application to make the server non-responsive resulting in the application not being able to deliver content to the legitimate user. Examples of these attacks are HTTP flooding, cache busting, and exploiting of XML-RPC.
HTTP Flooding
HTTP flooding is a layer 7 attack, it works on the same principle where the malicious actor tries to exhaust all the server resources by bombarding the requests on specific functionality of the application. Once all the resources are drenched and the server starts dropping the normal traffic, additional requests from actual users start contributing to denial-of-service attacks.
To further complicate things, the attacker uses botnets for producing these requests. It becomes a little tricky to identify which requests are legitimate and which are not.
Cache Busting Attack
This is more of an HTTP flood, where the malicious actor uses variations in query string so that it can bypass CDN cache (content delivery network) and CDN must contact the origin server for the response.
AWS Services Introduction
Let us now see some of the AWS services and how they can be tied together to form a DDoS resiliency.
Route 53
Amazon Route 53 is a cloud Domain Name System (DNS) web service provided by AWS. AWS hosts it at numerous edge locations. It is a kind of two-edged sword, which helps in minimizing the latency as well as in creating a scalable and distributed DNS structure that can imbibe a large amount of DNS requests. Further, each edge location is supported by multiple Internet connections to increase the fault tolerance.
Route 53 also supports below two approaches for increasing the availability:
- Shuffle sharding
- Anycast striping
Shuffle sharding is an approach to minimize the blast radius of the attack. Conceptually AWS creates virtual shards by randomly picking (based on hash algorithm) physical shards. Each customer is assigned with one virtual shard which is using some combination of physical shards under the hood.
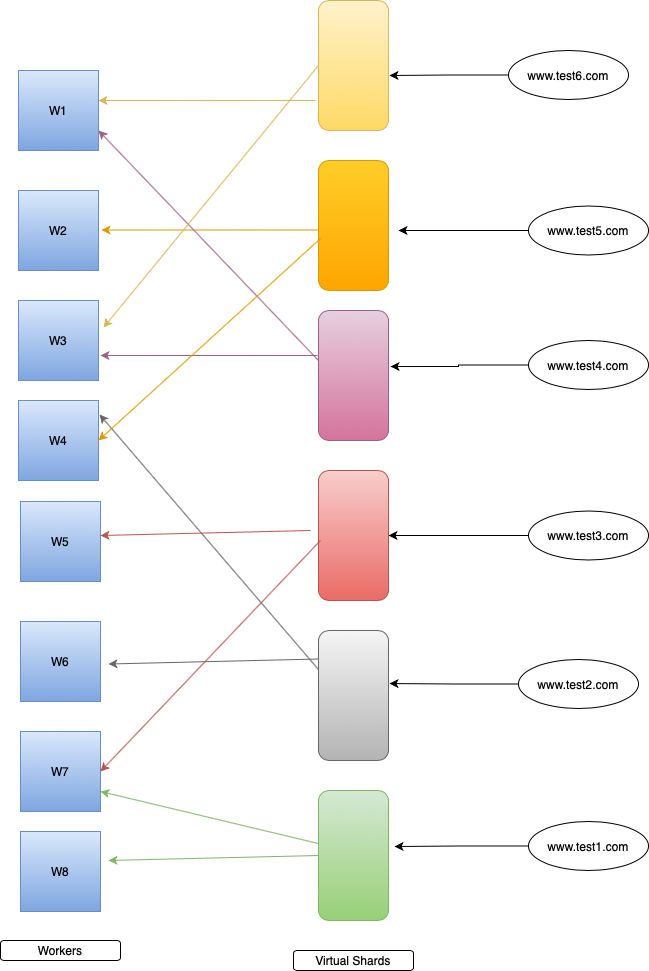
** This is only for understanding purposes. Consider worker nodes as nameservers.
The benefit of the approach is isolation or reduction in the attack surface area. To understand its modus operandi, please refer to the above diagram, suppose domain “www.test1.com” is under DDoS attack (Green virtual shard). Only nodes W7 and W8 are highly impacted as they are supporting green shards, the rest of the worker nodes have no impact. So attack entities are isolated. Though W7 is serving both test1 and test2, the impact is limited to test1 only as all the requests of test2 are still getting fulfilled by the W4 node, this way AWS reduced the impact only on test1.
Anycast is a routing technology(algorithm) that helps end user’s DNS queries get answered from the optimal Route 53 location given your network conditions. You can think it as a service where multiple servers are serving behind a single IP address. As a result, users get high availability and improved performance with Route 53.
Other than this, Route 53 supports creating Disaster Recovery policies across regions and health checks for the underlying infrastructure.
AWS WAF
AWS web application firewall helps in mitigating many vulnerabilities including OWASP Top 10. You can define multiple custom security rules and each rule consists of multiple conditions and actions to block attacks. It also helps in mitigating DDOS attacks by inspecting inline traffic.
It can be integrated with the following AWS resources
- Application load Balancer (ALB)
- Elastic Load Balancer (ELB)
- Cloudfront (CDN)
- API Gateways
- AWS app sync
WAF along with s3 and Lambda parser supports the creation of rules for rate-limiting the requests and block/blacklist the IPs which are going above the threshold for a certain time.
Traffic can be restricted based on geographies using Geo match conditions.
AWS WAF also supports custom responses so that instead of sending HTTP errors like “403” and “404”, you can send a custom response so that the attacker would not change his approach or strategy.
AWS Shield
AWS Shield is a managed DDoS protection service that safeguards applications running on AWS against external threats, such as bots and DDoS attacks. AWS Shield comes in two variants - Standard and Advanced. AWS Shield Advanced offers a lot more power and protection than the Standard version.
AWS Standard is free and enabled by default. It is well suited for most common L3 and L4 DDoS attacks. This protection is applied automatically and transparently on the below services.
- Application load Balancer (ALB)
- Elastic Load Balancer (ELB)
- Cloudfront (CDN)
- Route 53 (DNS)
Advance Shield is more of a paid service and helps in the protection of Layer 7 attacks, Shield Advance can be used for additional detection and mitigation against large and sophisticated DDoS attacks, with near real-time visibility into attacks. It comes with real-time monitoring along with real-time reporting and attack diagnostic.
It can be integrated with the following services:
- Amazon Elastic Compute Cloud (EC2)
- Elastic Load Balancing (ELB)
- Amazon CloudFront
- AWS Global Accelerator
- Amazon Route 53
For supporting the applications which are not hosted in the AWS, you can utilize the combination of AWS shield and AWS Cloudfront which virtually supports any origin.
If you have a Business support plan or Enterprise support plan and you are using AWS Shield Advanced, you can engage with AWS Shield Response Team (SRT), which can assist you in taking down the issue. You can further increase this collaboration for help and custom mitigation techniques during attacks. To contact the DRT, Enterprise, or Business Support levels will be required.
Shield Advanced promotes your network ACL to the AWS border from near the Ec2 instance, this expands the attack absorbing capacity from tens of GBPS to multi-terabyte. In 2020, AWS claimed that its AWS shield service mitigated a 2.3Tbps DDoS attack, the largest-ever publicly disclosed number.
ELB Autoscaling
The simplest approach on any cloud platform to absorb the DDoS attacks is by horizontal scaling. A single EC2 instance can be completely saturated with the deluge of requests as there is an upper bandwidth cap associated with Ec2 instances based on their instance types. ALB/ELB provides a mechanism to add more numbers of EC2 instances horizontally and distributing the traffic among them during the attack, which will help in absorbing huge traffic and increase the resiliency.
Moreover, ELB/ALB comes with protection against many L3/L4 attacks which helps in curbing many DDoS attacks and it can automatically scale to absorb additional traffic.
ELB provides a health check mechanism that helps in detecting and replacing unhealthy instances. If any of the servers are overwhelmed by the attack and become either non-responsive or experiencing a large delay in generating a response, ELB will automatically remove it and procure a new instance. Users can configure aggressive cool-down time periods or step scaling policies if the application is critical or experiencing frequent attacks.
ELB also has a security group that can be used to reduce the surface attack area by restricting the traffic only from the required IP set.
Amazon Cloudfront
AWS hosts Cloudfront is a distributed network of edge locations throughout the world, which makes it highly scalable and optimized. This can be used for absorbing DDoS attacks on static as well as dynamic applications. Cloudfront also supports geographic restrictions to help block attacks originating from specific countries and can be integrated with other services like WAF and Shield to further add the protection.
AWS DDoS Resilient Architecture
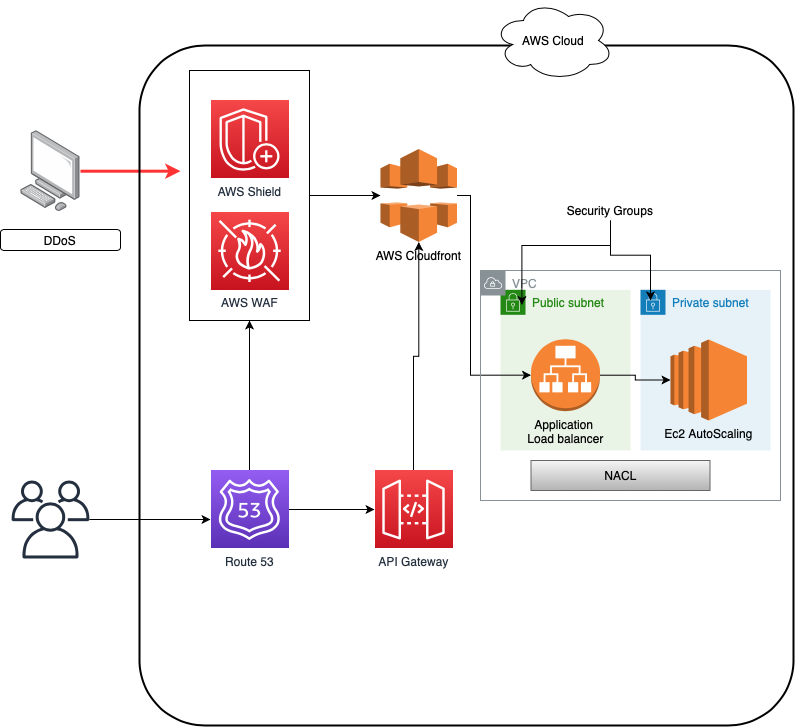
Users can use a combination of these AWS services to make their infrastructure resilient against DDoS attacks. I have included one such architecture diagram for reference.
Opinions expressed by DZone contributors are their own.

Comments