Simplify Your Compliance With Google Cloud Assured Workloads
Google Cloud Assured Workloads lets you create compliant environments, monitor for violations, and audit against major compliance frameworks.
Join the DZone community and get the full member experience.
Join For FreeTo navigate the complex world of cloud compliance, Google Cloud provides a tool, Google Cloud Assured Workloads, that helps organizations create a secure and compliant environment to run their workloads in Google Cloud. It helps organizations enforce strict data residency controls that restrict the resources to run only in specific Google Cloud Regions.
Assured Workloads Monitoring and Auditing helps organizations identify compliance policy violations in the Google Cloud environment. Additionally, Assured Support gives organizations control over their support experience. Organizations can decide who can access their data and restrict support personnel’s data access based on their location.
Assured Workloads offers a comprehensive set of controls for your Google Cloud environment:
- Regional controls. Enforce data residency and personnel controls.
- Sovereign controls. Enforce data sovereignty requirements by expanding regional controls with external key management or using a hardware security module with key access justifications.
- Regulated controls. Enforce specific regulatory regimes like CJIS, FedRAMP Moderate, FedRAMP High, Healthcare and Life Science Controls, Healthcare and Life Science Controls with US Support, Impact Level 2 (IL2), Impact Level 4 (IL4), Impact Level 5 (IL5), ITAR, Canada Regulatory Frameworks.
To create and manage Assured Workloads folders, ensure that the principal has the "Access Transparency Admin" and "Assured Workloads Administrator" IAM roles.
-
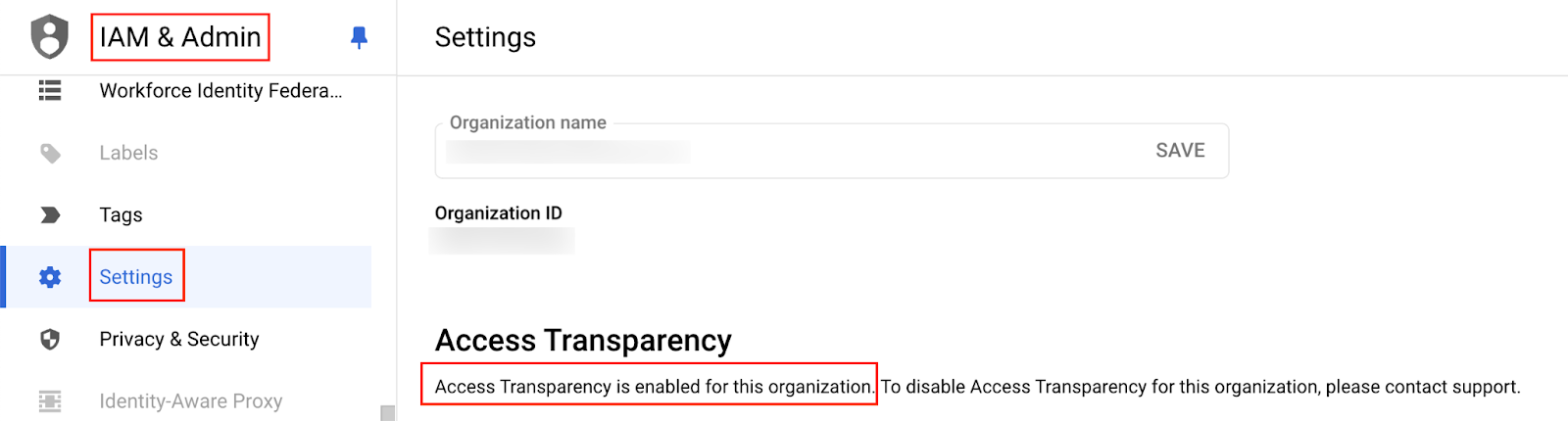
In the Google Cloud console, navigate to "IAM & Admin" → "Settings." Click the "Enable Access Transparency for Organization" button. You should see a confirmation message indicating that "Access Transparency" is enabled.
-
Even though it's not mandatory for creating Assured Workloads folders, it's recommended to enable "Google Cloud Support." To receive assistance from Google Cloud Support, we’ll need an Enhanced or Premium Support subscription.
Create Assured Workloads Folder
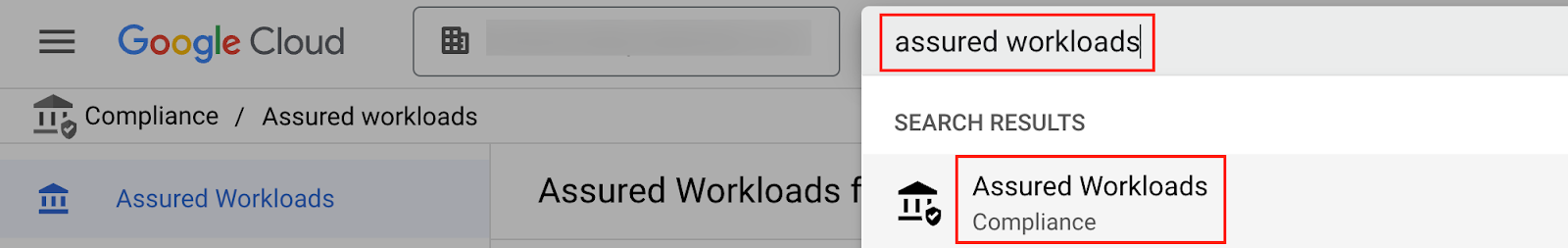
The Assured Workloads folder is the folder you create in Assured Workloads where you can store your Google Cloud projects that need to adhere to specific compliance requirements. Search for "Assured Workloads" in the Google Cloud Console and select "Assured Workloads."
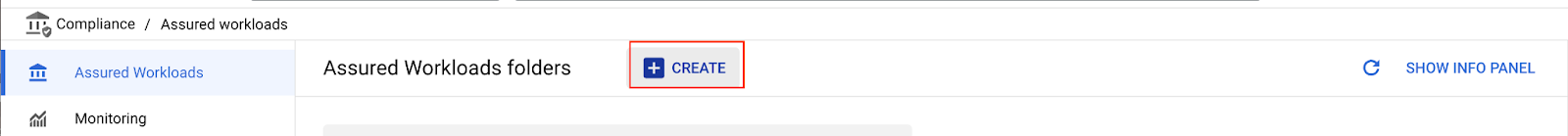
Click on "Create" to create the Assured Workloads folder.
Specify the folder name as "dzone-tutorial," and select the organization where you want the Assured Workloads folder to be created and the location as the parent organization or another folder where you want the Assured Workloads folder to be created. Click on "Next."
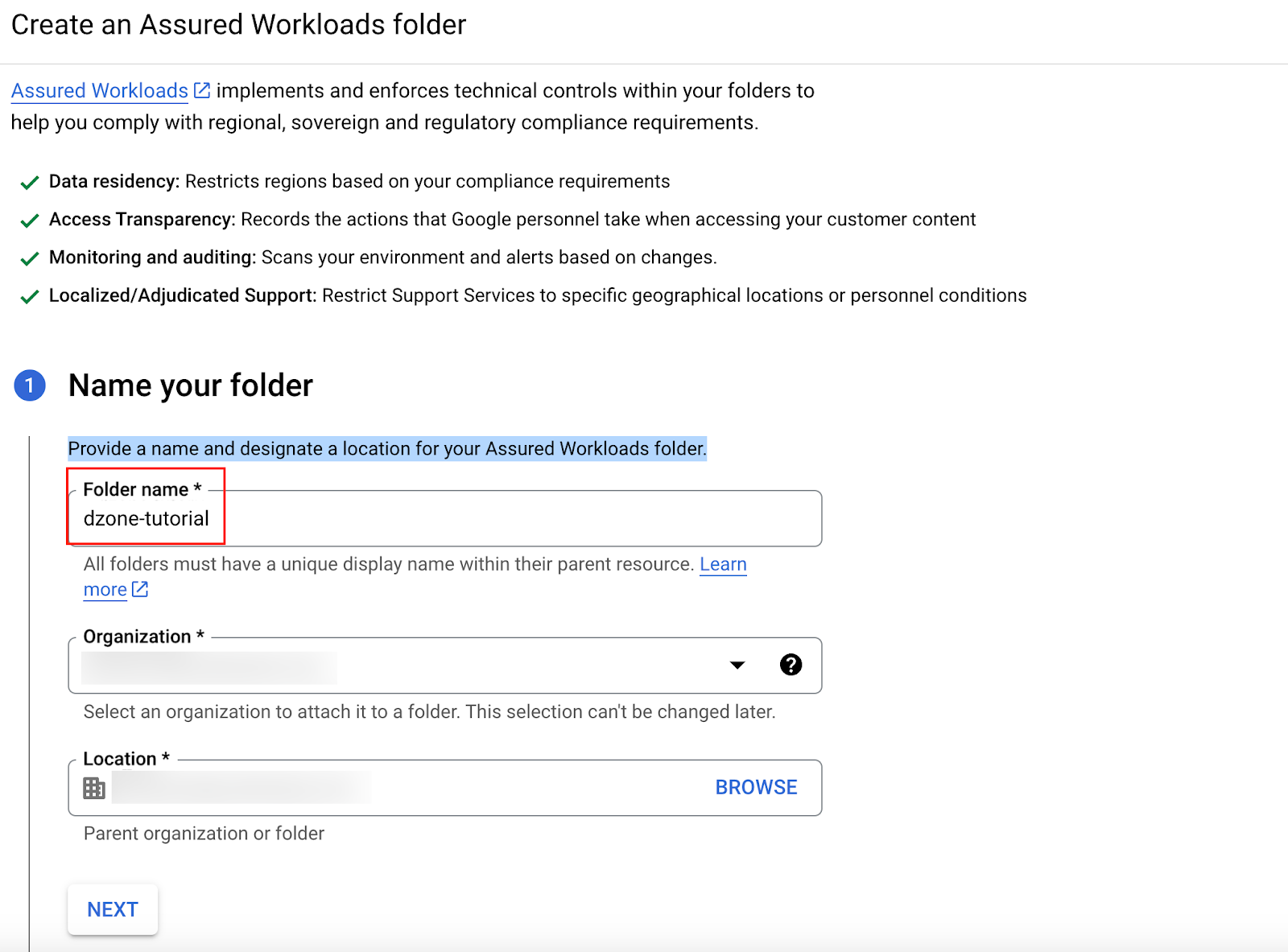
We can select either the Regional, Sovereign, or Regulatory controls for our folder. In this tutorial, as we will create a folder that is compliant with the Fedramp Moderate Controls, we will select "Regulatory Controls" → "Fedramp Moderate."
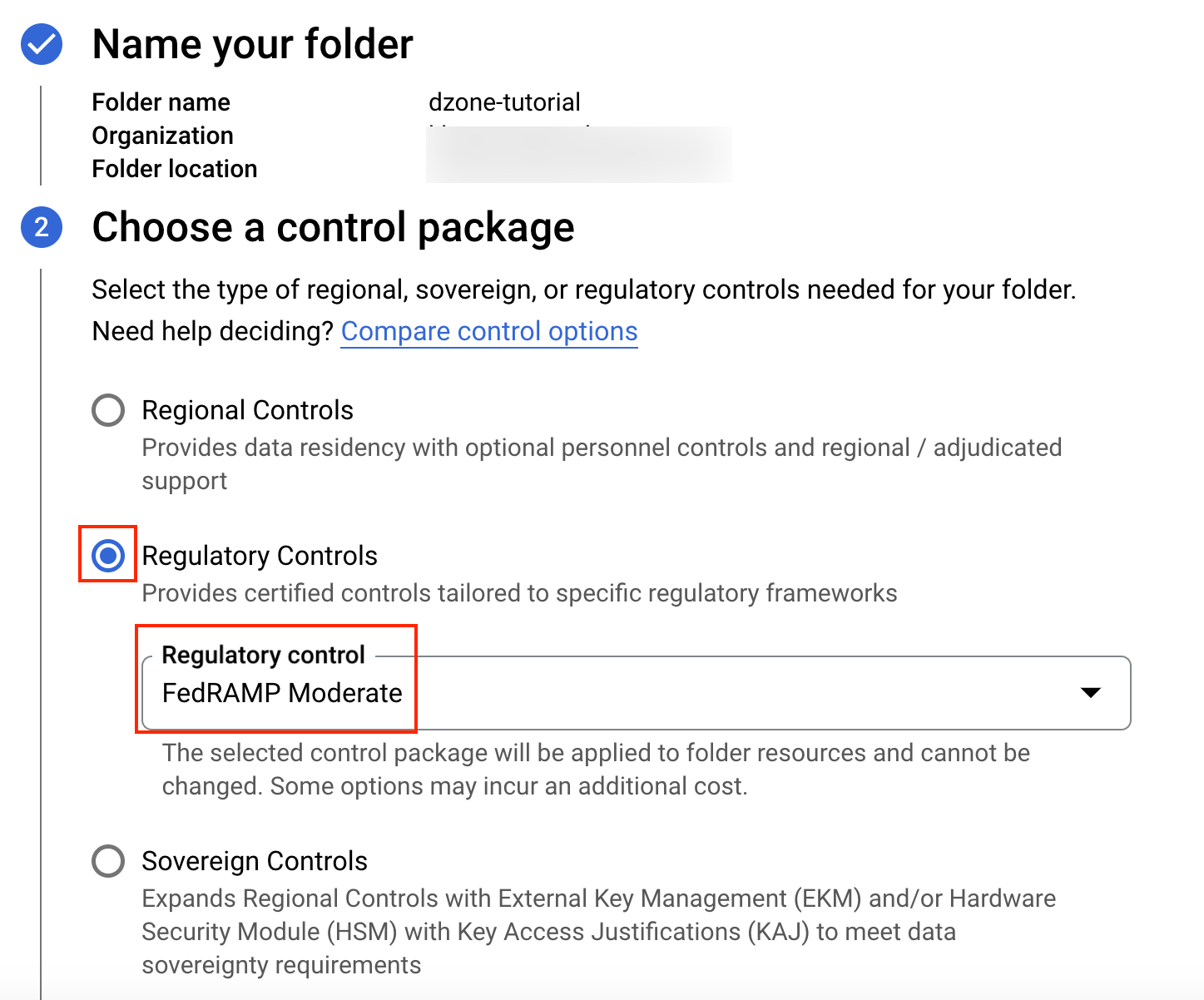
Assured Workloads can restrict the geographic locations where we can create the resources within our folder. We can select the "us-central1" cloud region or any other cloud region that aligns with the organizational policies. Click on "Next."

If you would like to use your own encryption keys, we can optionally create our own key management project and key ring within our Assured Workloads folder to store your Customer Managed Encryption Keys. In this tutorial, we will not be using Customer Managed Encryption Keys; we will click on "Next."
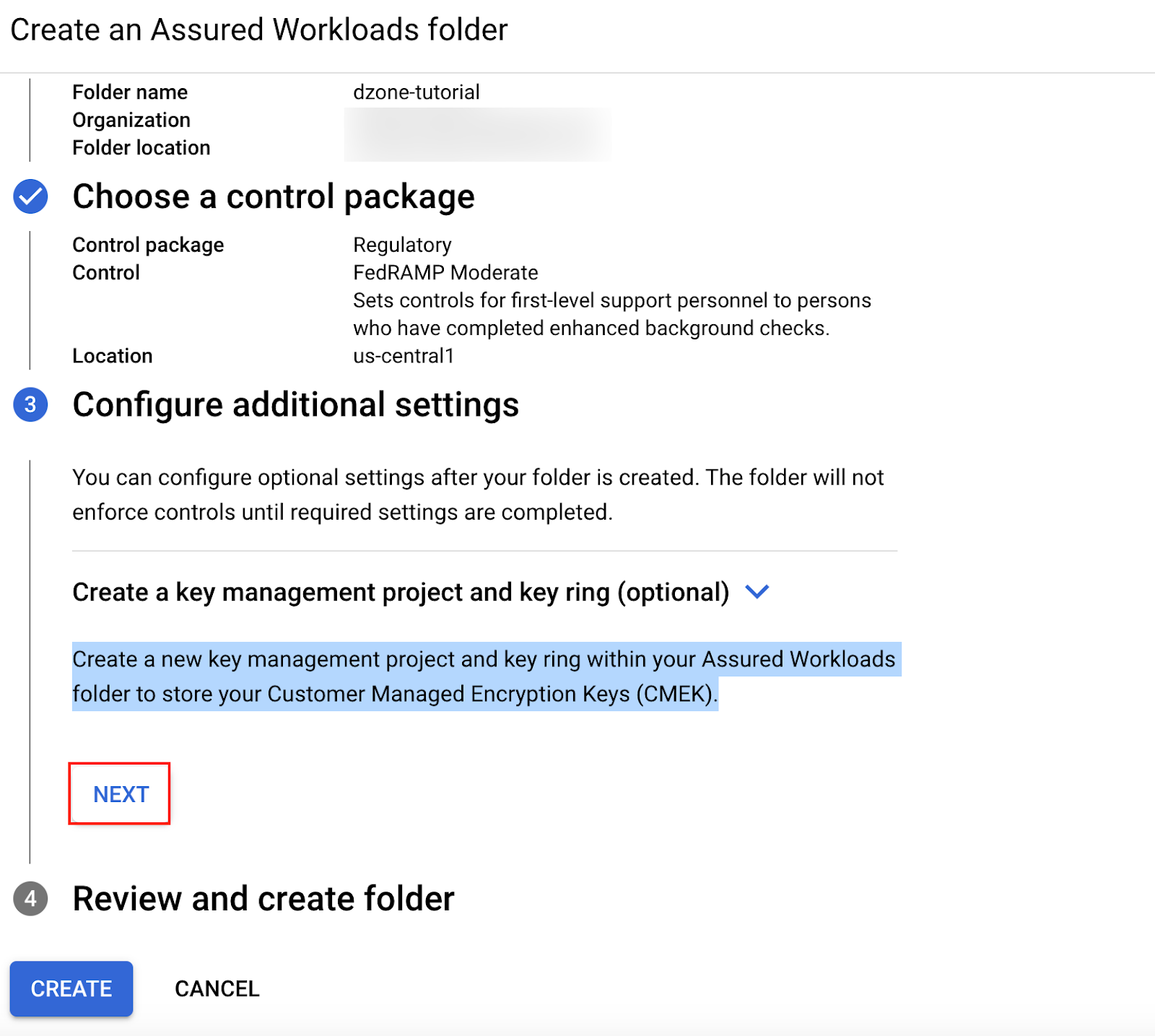
Click on "Create" to create the Assured Workloads folder.
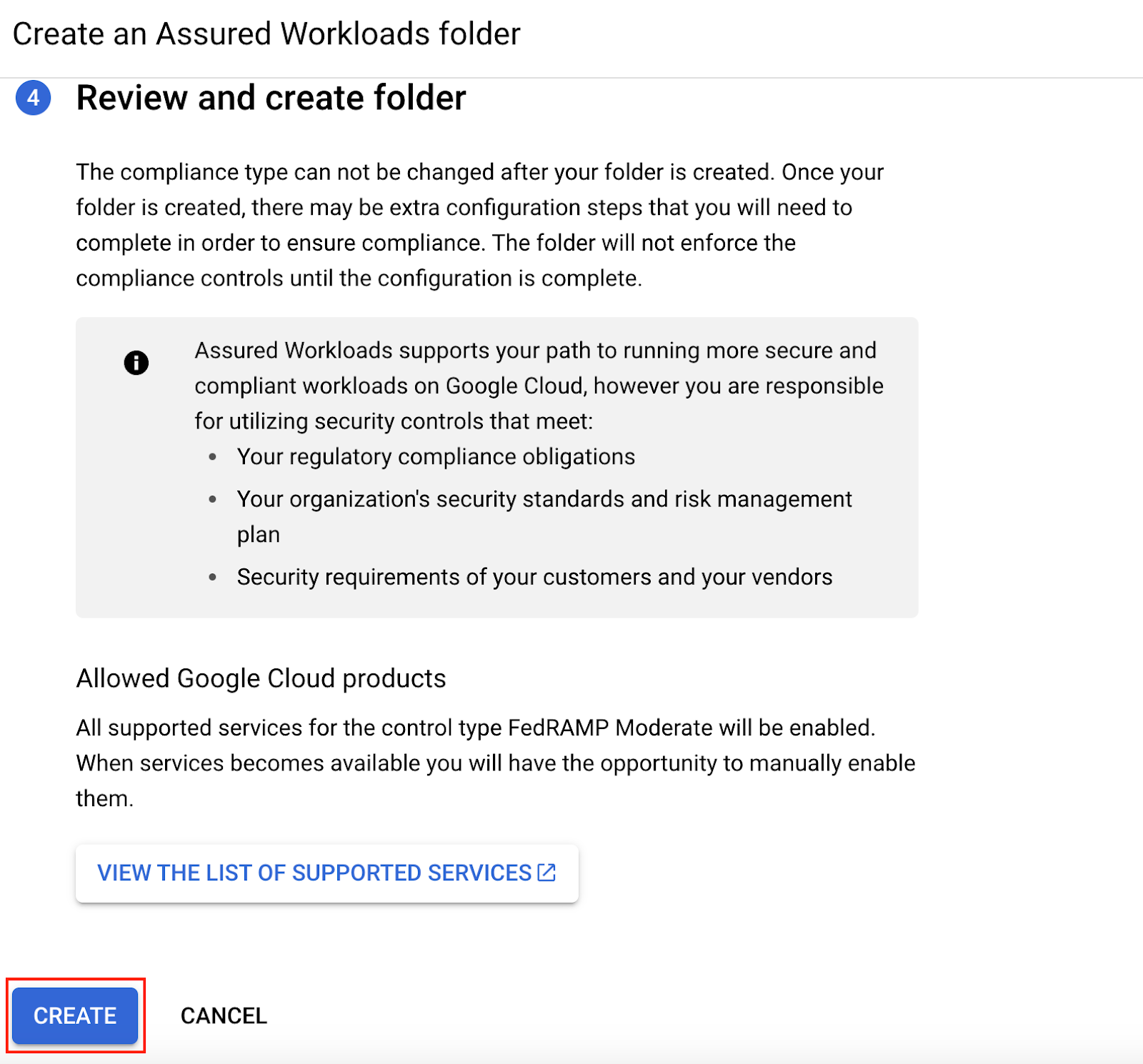
The dzone-tutorial Assured Workloads folder has been created.
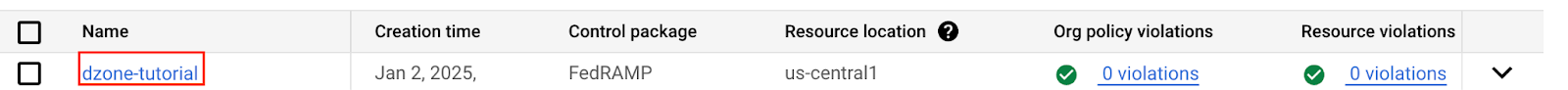
Assured Workloads Monitoring
Assured Workloads Monitoring provides ongoing security and compliance assurance for our Google Cloud environment. Assured Workloads Monitoring regularly scans our Google Cloud environment, compares it to our organization's compliance posture, and sends notifications to the Administrator if any policy violations are detected. This proactive approach helps us maintain a secure and compliant Google Cloud Environment.
In the below example, as an Assured Workloads Administrator, we can notice any unresolved organization compliance policy violations.
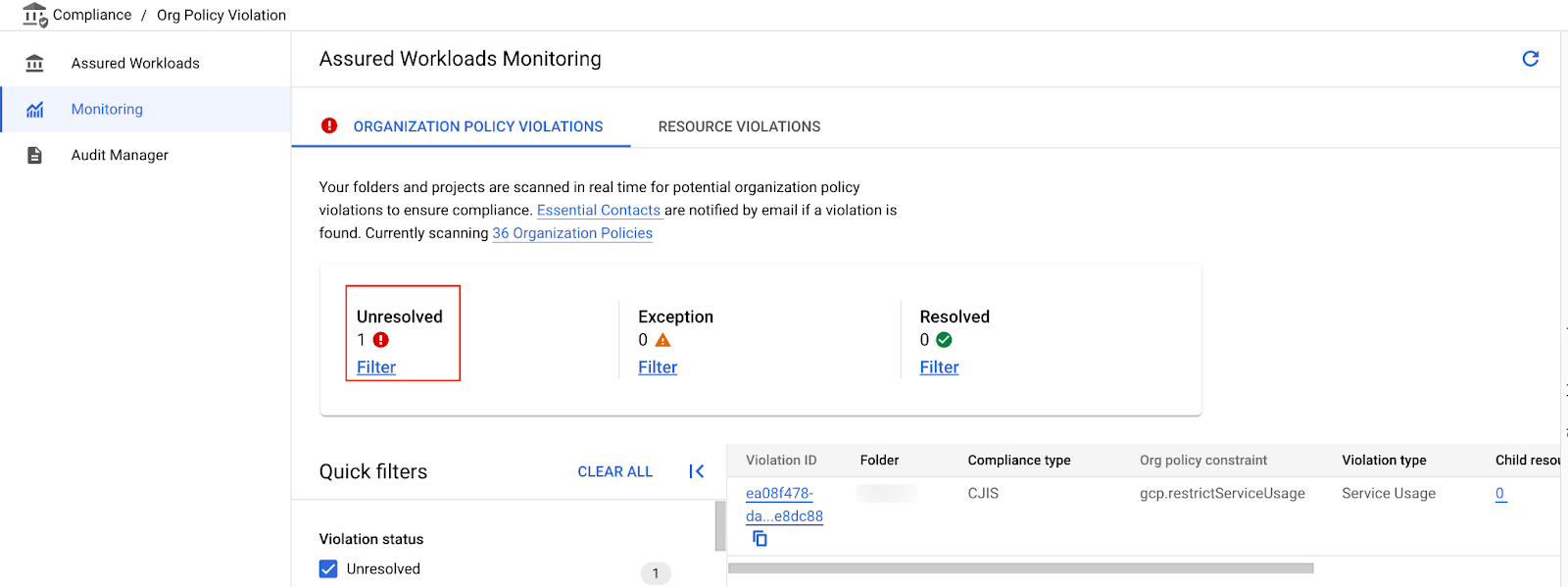
Assured Workloads Administrator can identify the resource violations if the Cloud resources are running in a non-compliant region or unsupported Google Cloud Service is used in the Assured Workloads folder, or when a Google Cloud resource is created without the Customer Managed Encryption for a service that requires Customer Managed Encryption.
Assured Workloads Audit Manager
Assured Workloads Audit Manager enables organizations to audit their Google Cloud resources against major compliance frameworks, including NIST 800-53, SOC2, PCI DSS, ISO, and Google's AI controls. Audit Manager helps Organizations identify policy violations for specific compliance controls across the compliance frameworks.
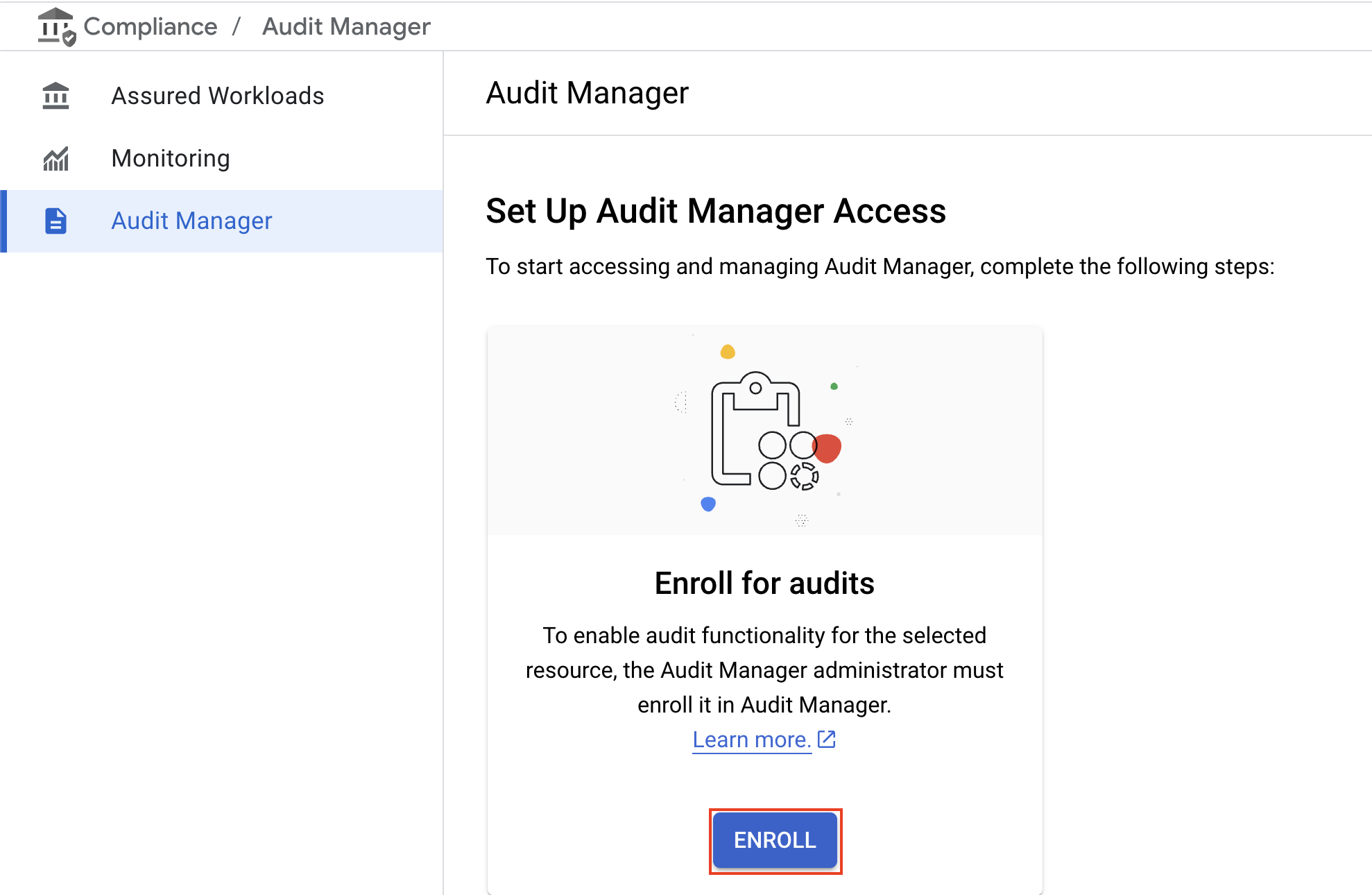
To set up Audit Manager, navigate to "Assured Workloads" → "Audit Manager." Click on "Enroll" to enable the audit functionality.
Click on "Create Bucket," to create a bucket where evidence could be saved.
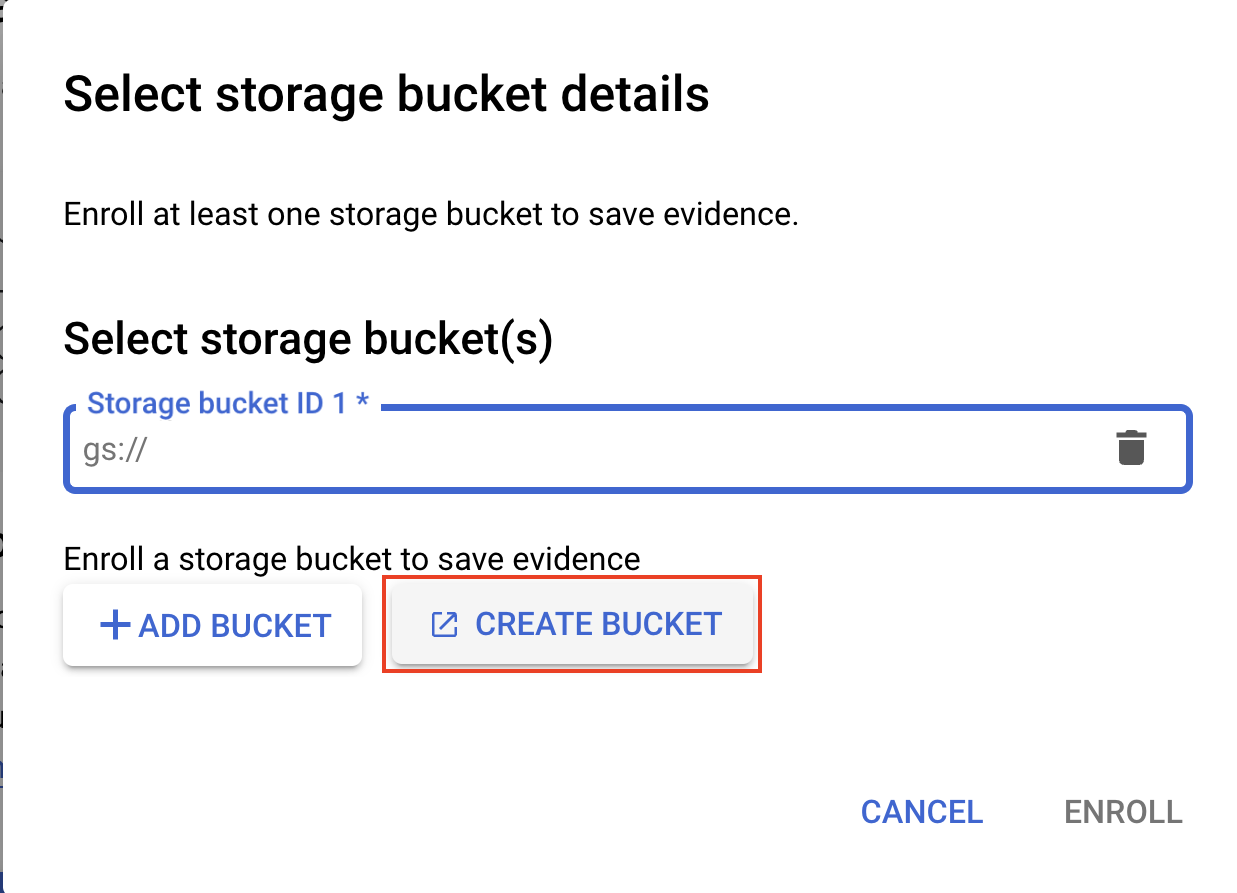
Specify the name of the bucket; it has to be a unique name. Click on "Continue."
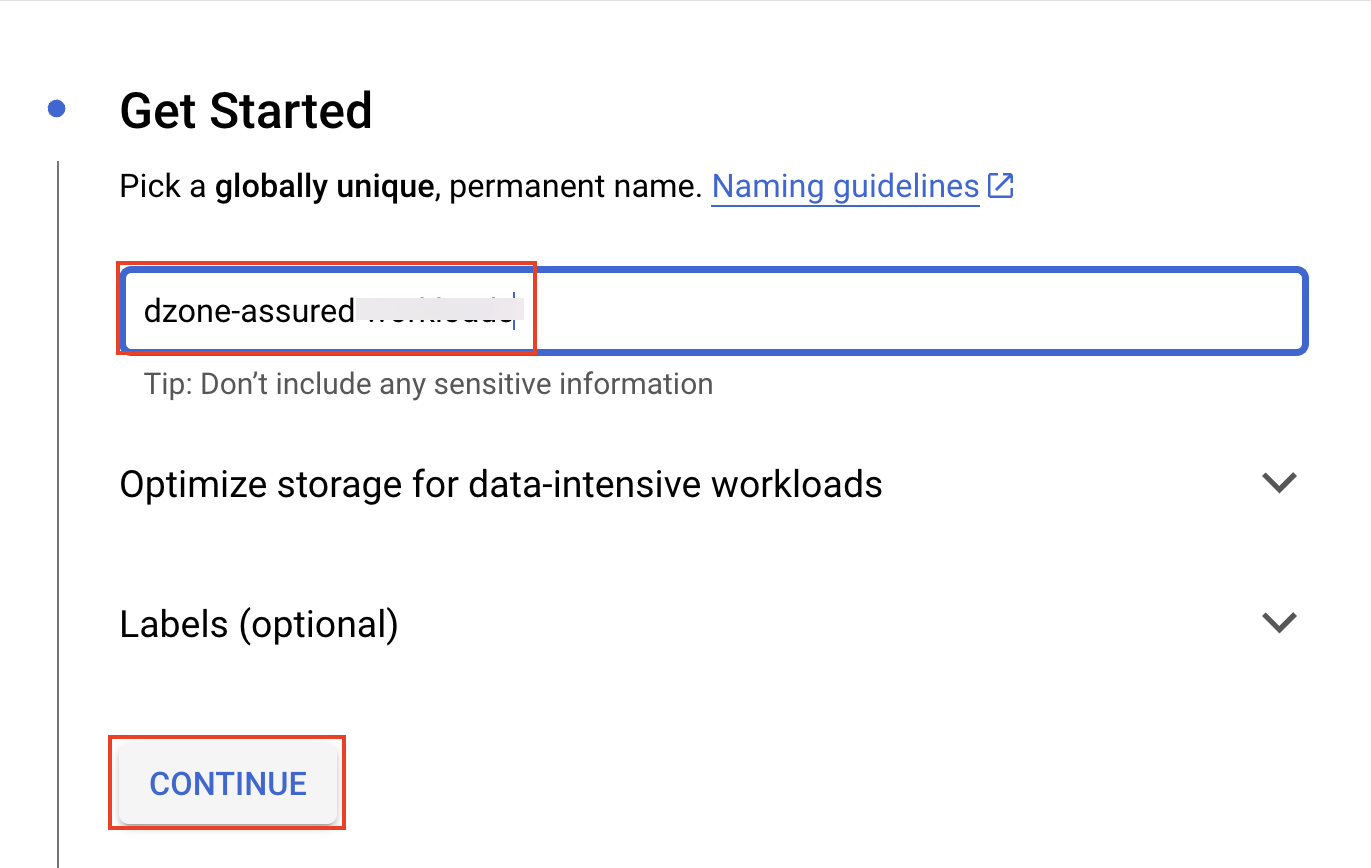
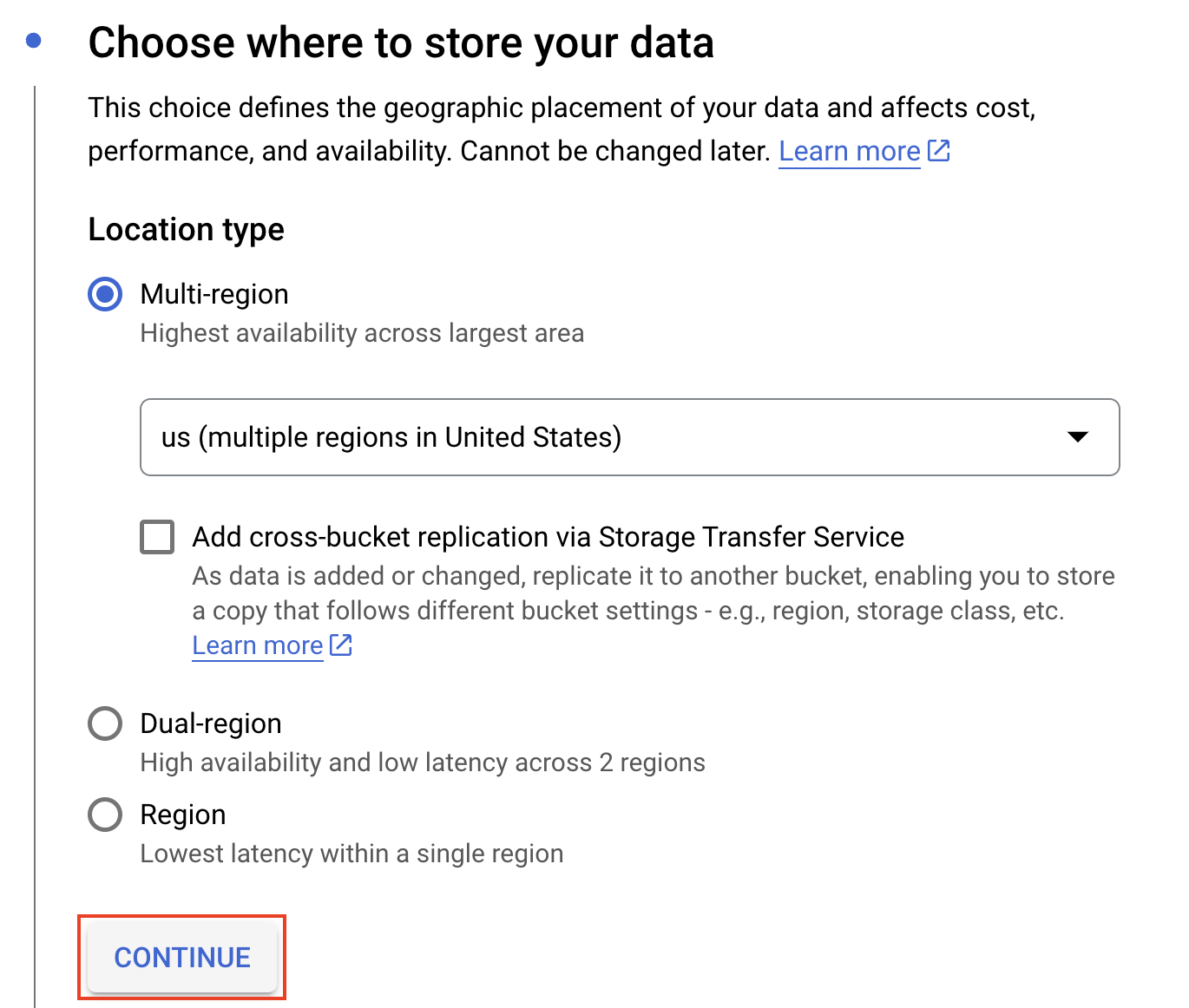
Based on the organizational policy, select the location of the bucket. In this example, you can select the location type of the bucket as "Multi-region." Click on "Continue."
Click on "Continue" and click on "Create."
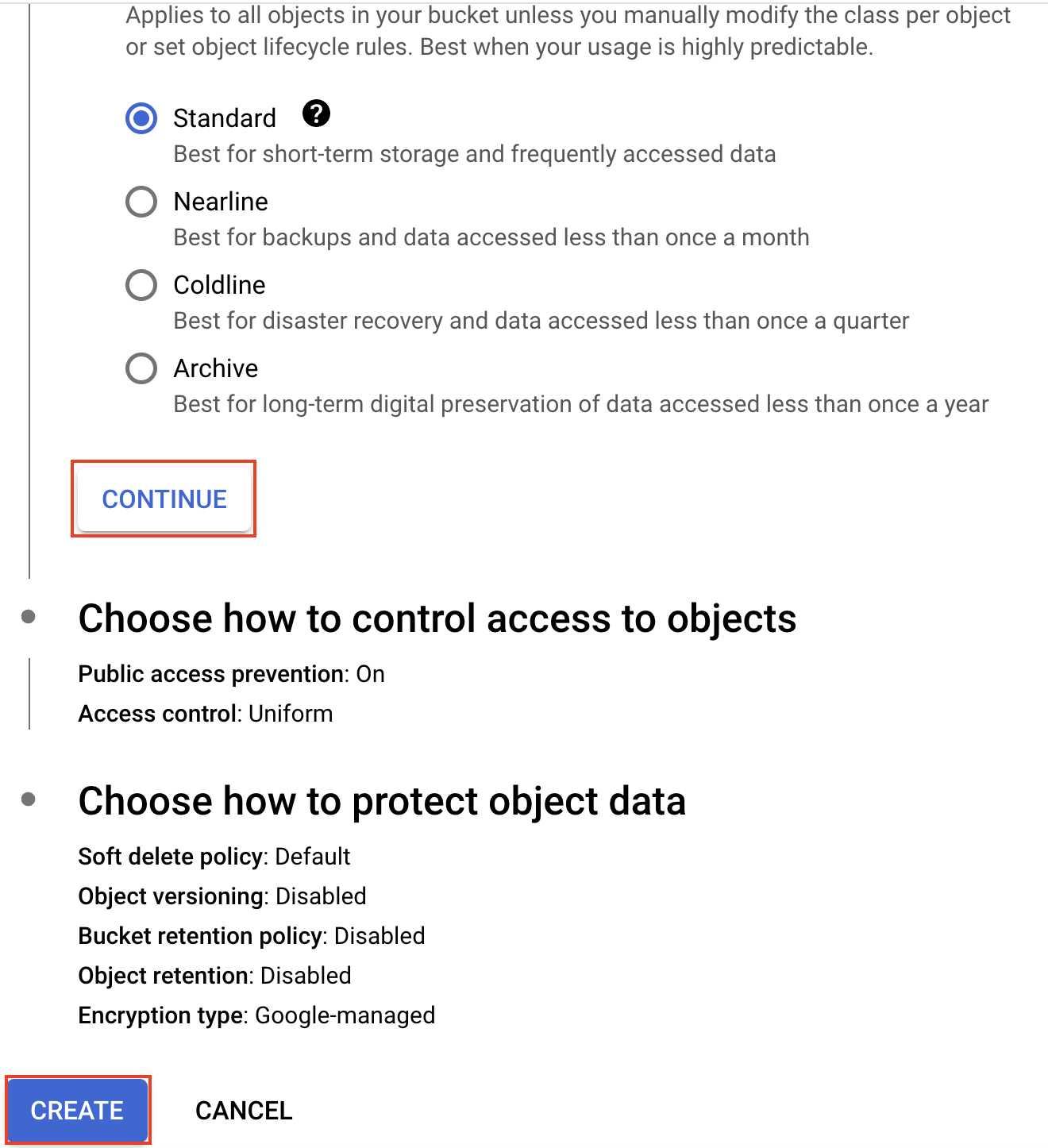
Click on "Confirm" to prevent public access to the bucket.
Navigate back to the Assured Workloads Audit Manager and specify the bucket we recently created. Click on "Enroll."
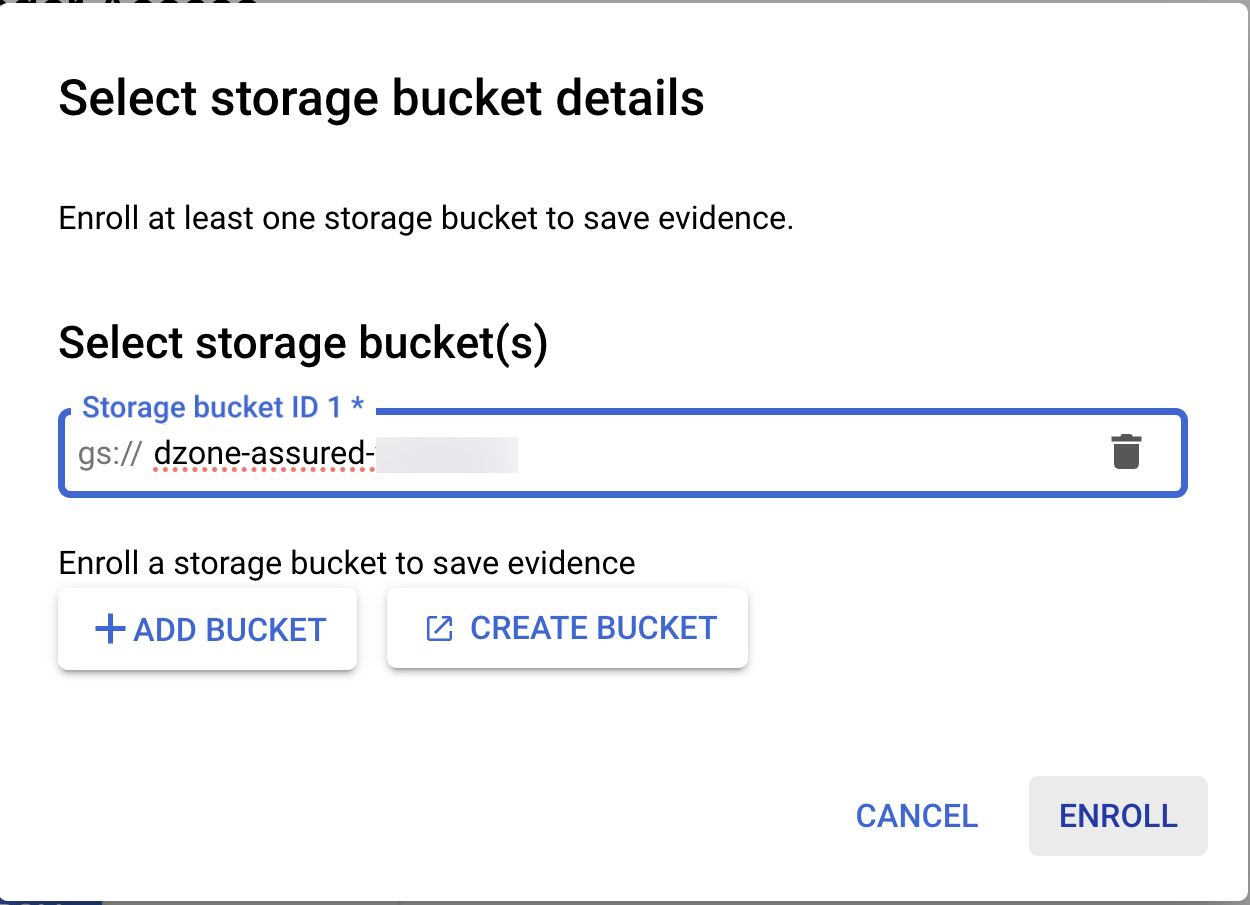
You should see the success message saying, "The resource is successfully enrolled."
You have successfully enrolled for audits using Audit Manager.
Click on "Run Audit."
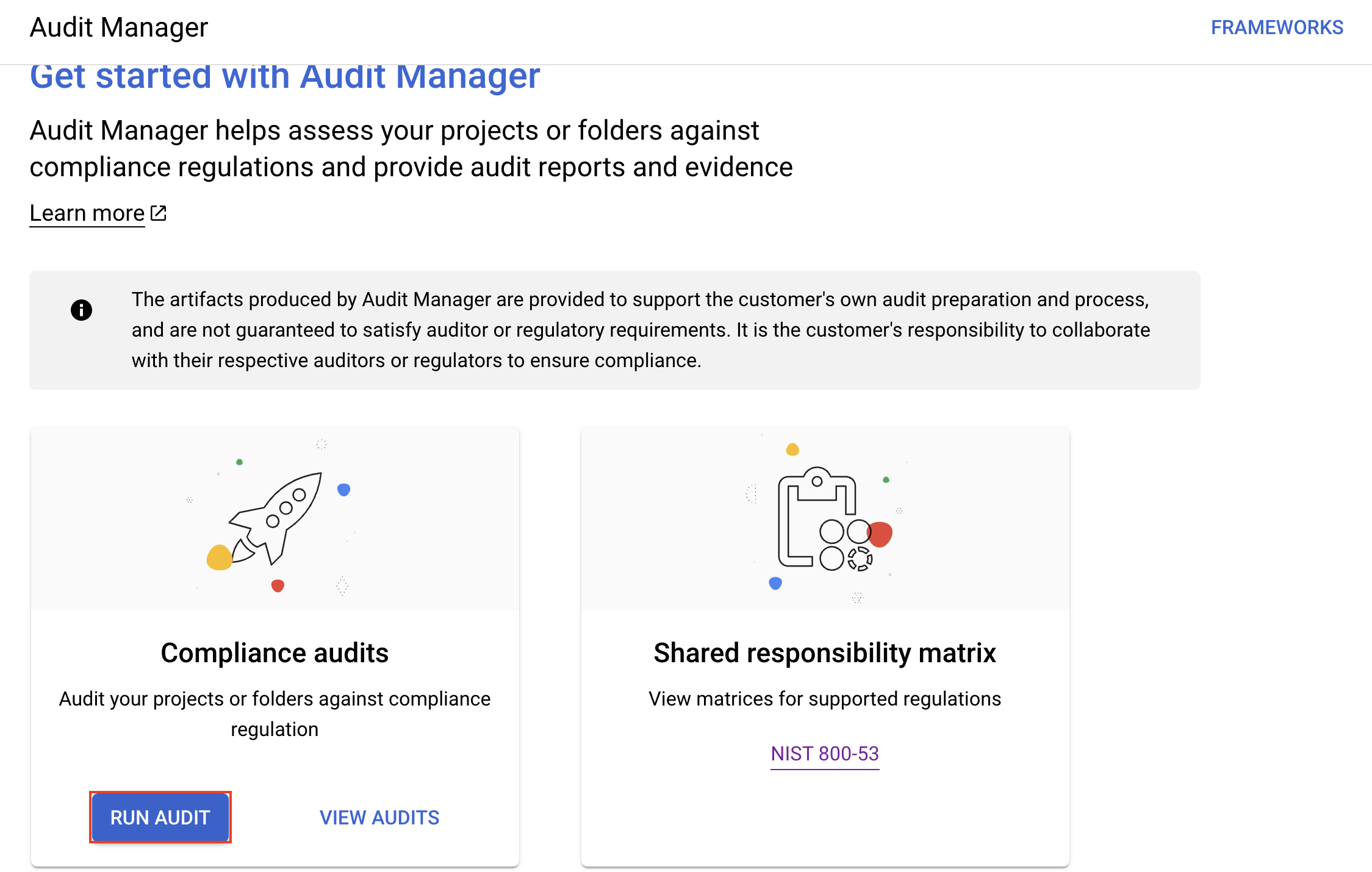
You can run the Audit for Compliance Frameworks like CIS Controls v8, CIS GCP Foundation Benchmark 2.0, Cloud Controls Matrix 4.0, ISO 27001 2022, NIST 800-53 r4, NIST CSF v1, PCI DSS 4.0, Google Recommended AI Controls, SOC2 2017. We can select SOC2 2017. Select the location as "us-central1" and click on "Next."
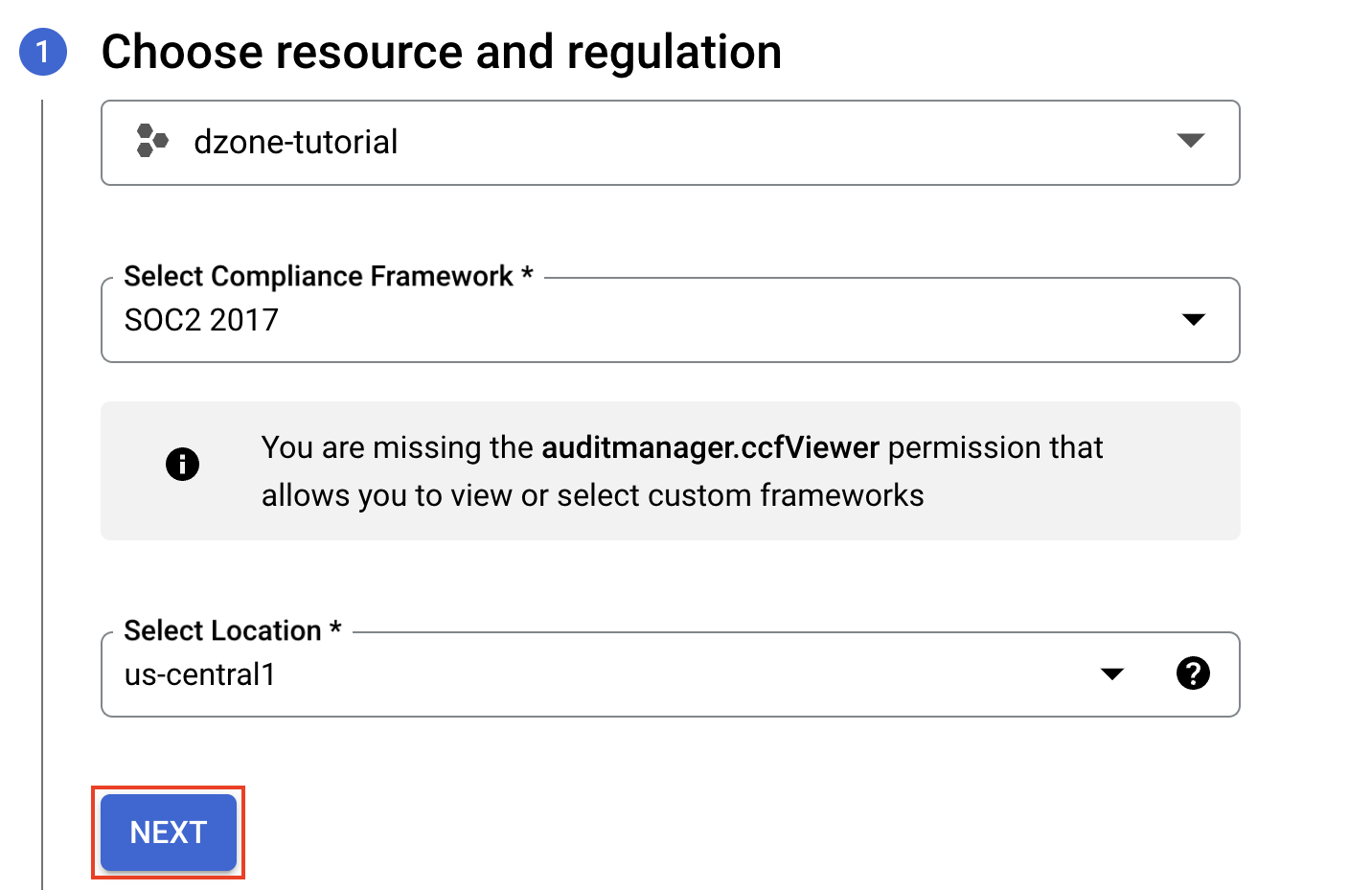
Select the "Storage Bucket Location" and click on "Run Audit."
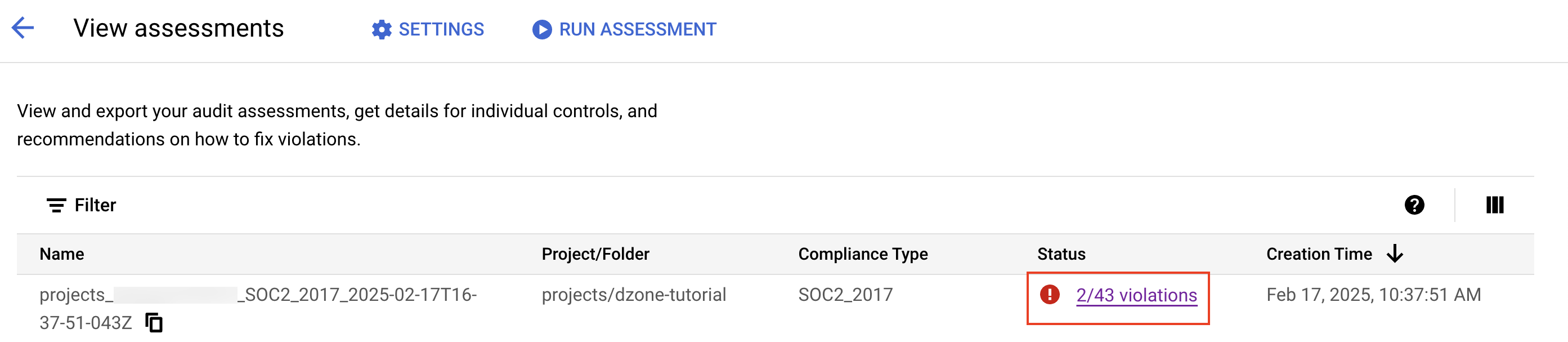
You will see all the policy violations identified for the compliance framework on which we ran the audit.
Summary
Google Cloud Assured Workloads empowers organizations to take control of their cloud compliance. This blog walks you through how to establish secure, regulated environments by creating Assured Workloads folders tailored to meet specific compliance requirements.
You have successfully learned how to enforce data residency and sovereignty controls, ensuring your data stays where it should. The blog highlighted the ongoing assurance provided by Assured Workloads Monitoring, which proactively flags any policy violations.
Finally, we reviewed how Audit Manager simplifies compliance audits against major frameworks, offering evidence of your adherence to compliance controls. Essentially, this guide equips you with the tools to build and maintain a compliant Google Cloud environment.
Opinions expressed by DZone contributors are their own.

Comments