Cloud Key Management Services Use Cases
This article will compare the primary security key management services solution use cases among the Azure key vault, AWS KMS, Google CKMS, and other Cloud key management solutions.
Join the DZone community and get the full member experience.
Join For FreeToday, the cloud environment has been chosen by many business solutions as the major hosting environment for their applications. They can either choose Software-as-a-service (SaaS), Platform-as-a-service (PaaS), or Infrastructure-as-a-service (IaaS) different solution types to build up solutions to meet business requirements. However, storing business data in the Cloud environment will have a great challenge in exposing business data to the public. As the concerns data security issues, every Cloud platform vendor provides a different solution for data security. Understanding the similarity and differences in those solutions will help the business clients choose the proper solution for the business applications.
This article will discuss the primary solution use cases and major differences in secret key management among the Microsoft Azure, Amazon AWS, and Google Cloud Platform for managing secret keys, certificates, and data encryptions. Although a platform could provide a similar solution or indirect solution for a specific use case, it will still be compared as a difference as long as it is not a commonly used use case.
Azure Security Key Vault Service
Microsoft Azure cloud platform provides a centralized solution key vault for protecting application sensitive information, managing the secrets, security keys, and certificates for Azure web Apps, function applications, and cold storage. It can be used as a PaaS solution, integrated with other Azure cloud services, and supports both software keys and hardware keys.
Azure Security Keys are created in the resource Group with key vault name, region, pricing tier (standard and premium), and a set of access policies. Vault keys can be accessed from multiple methods, such as Rest API, Ney SDK, Java SDK, Node.js, Python, Azure CLI, PowerShell, etc.
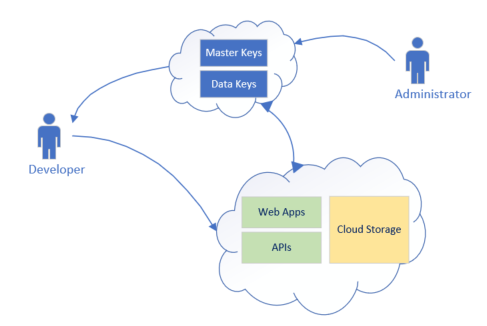
Azure key vault provided two service tiers, standard and premium and can be used in the following major use cases:
- Use Azure key vault to manage the VM and disk storage via the VM keys
- Use Azure key vault to manage backend Azure SQL, Logical Apps, and Web Apps, monitoring and logging via the Secrets and certificates
- Identity translation or brokering service across other cloud platforms, such as AWS, Google cloud platform, etc.
AWS Key Management Service
AWS Key Management System (KMS) is a regional key system. Multi-region keys can be used in multiple regions, like disaster recovery or global apps operating.
AWS key management service includes both client-side encryption and server-side encryption. It is managed inside the AWS Amazon Elastic Compute Cloud (EC2). KMS enables customers to provision and use encryption keys to protect data, and also enables the customer to create, use, and manage encryption keys.
For example, in KMS, the user can use a data key to encrypt a file or store data. An encrypted data key is stored inside the encrypted data file and is encrypted by the KMS crypto model. During the decryption process, the data key will be decrypted first, and then it will be used to decryption the data file.
AWS KMS uses master keys to generate data keys which will be used to encrypt and decrypt the data file. The master key is encrypted with AES 256 encryption algorithm with a provided password. AWS also manages the encryption/decryption activities and audit events managed in the AWS cloud trail.
Compared with Azure Key Vault, the common use case in AWS Key Management Service (KMS) is using symmetric keys. That means the same key is used for data encryption and decryption (with a 256 AES algorithm). It is the primary way of encryption and decryption a data file, and keys can also be used for signature and signing.
Azure vault is an asymmetric keys mechanism with public keys and private keys. The private key is used for decryption or signatures, and the public key is used for encryptions or verifications. The public key is given to everybody to do encryption. It does not help with decryption
Because of the difference between the symmetric or asymmetric key method, the major use cases in AWS are different from the Azure key vault use cases:
- In AWS, the system generates a fresh data key, and the AWS KMS will encrypt that fresh data key with a master key, and protect it inside the KMS. AWS will send the user back both clear version and encrypted version keys via the TLS. The client can use the encrypted version key for later decryption, or the clear version key for encryption.
- In Azure Vault, the client will generate his/her own keys, encrypt the data file with the public key provided by the Azure key vault, and decrypt the data file with the private key.
Google Cloud Key Management Service
Google Cloud Key Management Service (CKMS) is a centralized cloud service for managing encryption keys for encrypting cloud data files for other Google services such as API tokens, data files, storage, or Web Apps. It uses AES 256 encryption algorithm to protect data files.
Google Cloud KMS supports both asymmetric keys and symmetric keys. It is integrated with other Google-provided services, for example, Cloud Identity and Access Management, storage management, and content management. Like Azure vault, Google CKMS has integrated with cloud monitoring and logging, Hardware Security Model, etc.
Major use cases:
- Use Google Cloud KMS to manage access to the content, disk storage, and Web Apps APIs.
- Use asymmetric keys (public keys and private keys), or symmetric keys (master keys and data keys) to manage the data file encryption and decryption
- Use encrypted data in BigQuery via APIs in Google-provided services
Other Cloud Key Management Services
There are some other cloud key management services, such as Spring Cloud Vault which provides a central place with an external client-side configuration to manage external security secrets. Spring Cloud Vault is an open structure framework for managing security secrets, which can be used to protect external services, such as Could database (MySQL, PostgreSQL, MongoDB, etc.)
IBM Security Guardium Key Lifecycle Manager is also a centralized, transparent encryption key management service which is used for key life-cycle management, such as key creation, storage, self-encrypting, interoperation, and API access. It is one integrated service in the IBM Security Guardium suites.
Oracle Cloud provides Oracle Cloud Infrastructure (OCI) Vault, again, a centralized place to manage the use of keys and secrets across OCI services as well as Oracle Identity and Access Management (IAM) services. It supports both symmetric and asymmetric keys with AES 256 encryption algorithm.
In a Summary
Although Azure key vault, AWS Key Management service, and Google Cloud key management service provide almost similar security, key management, encryption, and decryption service to protect the cloud data file, storage, content, certificates, hardware, access, etc., they still have some difference in major use cases, system access and development, and cost models. Here is a summary discussion of the major difference between those platforms:
From the Development Point of View
Azure Key Vault support the local development environment with native APIs, it is much easier to set up on the developer’s local machine. AWS KMS needs to generate the keys from the key management console and set development with encryption SDK. Google CKS needs google cloud services APIs for the development
From the Deployment Point of View
Azure Key Vault and google CKMS supports on-premises development and deployment remotely. Azure key vault can be used as a broker agent for identity translation across other cloud platforms.
From the Key Encryption/Decryption Perspective
Azure key vault is majorly used as an Asymmetric key system (public and private keys). AWS KMS uses symmetric keys( master and data keys), and Google CKMS uses both.
From the Key Management and Data Retention Perspective
In the Azure key vault, the key will be destroyed after the retention period elapses. AWS KMS will destroy keys after they are deleted in 7-30 days. Google CKMS won’t delete the keys.
Conclusion
As you are aware, in the cloud environment, the different platform provides similar security key management services for data file encryption and decryption. The difference between them is very subtle. Choosing which system will be used in your solution should be considered in a broad picture of the strategic roadmap plan of your organization.
However, just for key management and data file encryption, IT developers and architects will consider the symmetric or asymmetry key structure, the convenience of using native environment development, the convenience of access service across cloud Platforms, and the cost model, etc.
Thanks for the reading and hopeful you found this article helpful.
Opinions expressed by DZone contributors are their own.

Comments