Considering Tor-like Techniques to Protect Your Users
The Tor project lets users opt-out of the kind tracking and surveillance that happens invisibly and without informed consent.
Join the DZone community and get the full member experience.
Join For FreeTor stands for The Onion Router, an open network that by design makes it difficult (but not impossible) for an user and her activities to be identified.
Why is this important?
The past five years have brought unprecedented clarity to the problem of mass surveillance. The revelations of those few years — WikiLeaks, HBGary Federal , Cablegate, the NSA leaks, to name only the most well-known — have demonstrated that, bit by bit, the expectation of privacy no longer holds true online. Vast dragnets have eroded the capability of the average user to defend themselves against a now-"standard" level of surveillance that reaches directly into the homes, workplaces, and devices of everyday users. (Clearly, WhatsApp has concerns that align to those Tor responds to.)
There are two competing beliefs that rise in reaction to that observation. The first asserts that for the average user, the kind of surveillance invoked isn't likely to be targetted toward them, and that it shouldn't be considered a problem "if you aren't doing anything wrong." The second says that the capacities that governments, and even more crucially, private supranational entities, have developed to hide their own activites whilst being able to pry into that of the citizenry, is, in and of itself, an offense to the integrity of all.
What does this mean for developers?
Users are your primary constituents. They deserve far more from the applications and platforms being developed than they're currently getting.
Put simply, developers should now consider actively obfuscating surveillance and tracking (and, possibly, stand against the kind of programmatic advertising that edges up to the same):
1. No network or system should be constructed in an attempt to characterize the user, or through inaction, allow the user to become characterized.
Tor
Tor defeats a) traffic analysis by third parties and b) prevents sites from learning defining but unvolunteered characteristics of the user.
Tor's network works to pick up where encryption leaves off. While encryption can make data unretrievable, this isn't enough. For any piece of encrypted data, there's also routing instructions contained in a header. By analogy, this is the same as knowing the itinerary of a person. And for a clever attacker or analyst, the origin point of your connection, services used, timing, and size of packets might well be enough to infer, albeit by correlation, identifying traits or behaviors.
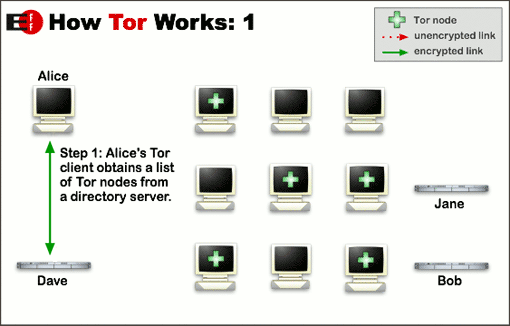 | 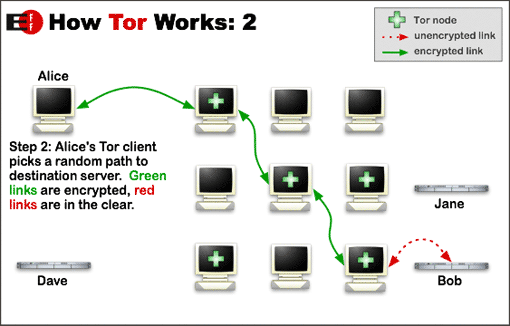 | 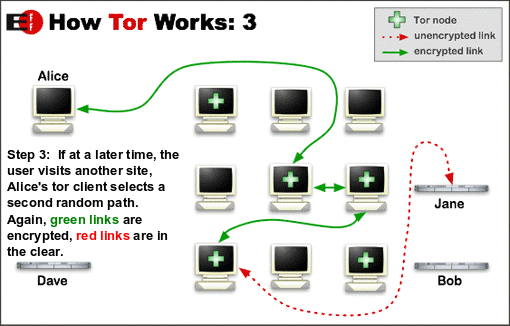 |
Tor obfuscates the route that data takes by creating a parallel network for it to traverse. Alongside encryption (and even better, coupled with VPN), Tor offers a shot at the kind of privacy that one expects offline, should expect online, and between the lines.
That network is run by volunteers and is only as good as those who support it. Developer support for standards that safeguard a user's intent — which nearly never includes a handshake with the NSA—is essential to the promotion of an Internet, or more broadly, a digital life bereft of the panopticon.
More Resources
The Electronic Frontiers Foundation tracks the trackers and arms the disarmed.
PrivacyTools.io contains significant resources, including examples of enterprise-grade projects that protect privacy.
Opinions expressed by DZone contributors are their own.

Comments