Container Security: The Art and Science of Safeguarding Cloud-Native Environments
Delve into a spectrum of crucial security patterns and anti-patterns to best navigate the ever-evolving and highly popular realm of containers.
Join the DZone community and get the full member experience.
Join For FreeIn the ever-evolving landscape of cloud-native computing, containers have emerged as the linchpin, enabling organizations to build, deploy, and scale applications with unprecedented agility. However, as the adoption of containers accelerates, so does the imperative for robust container security strategies. The interconnected realms of containers and the cloud have given rise to innovative security patterns designed to address the unique challenges posed by dynamic, distributed environments.
Explore the latest patterns, anti-patterns, and practices that are steering the course in an era where cloud-native architecture, including orchestration intricacies of Kubernetes that span across Amazon Elastic Kubernetes Service (EKS), Azure Kubernetes Service (AKS), Google Kubernetes Engine (GKE), including nuances of securing microservices.
Related: Amazon ETL Tools Compared.
What Is Container Security?
Container security is the practice of ensuring that container environments are protected against any threats. As with any security implementation within the software development lifecycle (SDLC), the practice of securing containers is a crucial step to take, as it not only protects against malicious actors but also allows containers to run smoothly in production. Learn how to incorporate CI/CD pipelines into your SDLC.
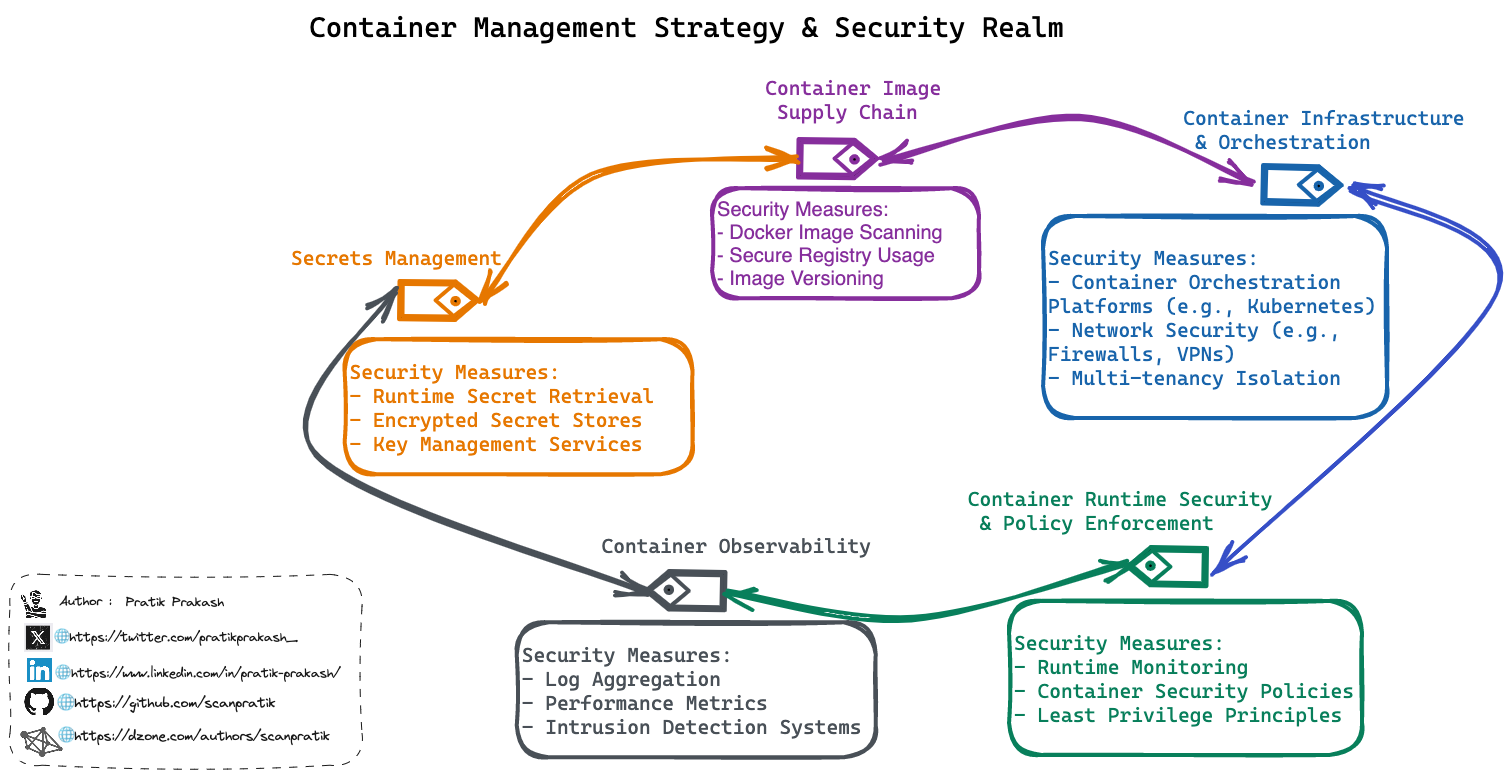
The process of securing containers is a continuous one and can be implemented on the infrastructure level, runtime, and the software supply chain, to name a few. As such, securing containers is not a one-size-fits-all approach. In future sections, we will discuss different container management strategies and how security comes into play. Review additional CI/CD design patterns.
How to Build a Container Strategy With Security Forensics Embdedded
A container management strategy involves a structured plan to oversee the creation, deployment, orchestration, maintenance, and discarding of containers and containerized applications. It encompasses key elements to ensure efficiency, security, and scalability throughout the software development lifecycle based around containerization.
Let's first analyze the prevailing and emerging anti-patterns for container management and security. Then, we will try to correlate possible solutions or alternative recommendations corresponding to each anti-pattern along with optimization practices for fortifying container security strategies for today's and tomorrow's threats. Review more DevOps anti-pattern examples.
"Don't treat container security like a choose-your-own-adventure book; following every path might lead to a comedy of errors, not a happy ending!"
Container Security Best Practices
Weak Container Supply Chain Management
This anti-pattern overlooks container supply chain management visible in "Docker history," risking compromised security. Hastily using unofficial Docker images without vetting their origin or build process poses a significant threat. Ensuring robust container supply chain management is vital for upholding integrity and security within the container environment. Learn how to perform a docker container health check.
Anti-Pattern: Potential Compromise
Pushing malicious code into Docker images is straightforward, but detecting such code is challenging. Blindly using others' images or building new ones from these can risk security, even if they solve similar problems.
Pattern: Secure Practices
Instead of relying solely on others' images, inspect their Dockerfiles, emulate their approach, and customize them for your needs. Ensure FROM lines in the Dockerfile point to trusted images, preferably official ones or those you've crafted from scratch, despite the added effort, ensuring security over potential breach aftermaths.
Installing Non-Essential Executables Into a Container Image
Non-essential executables for container images encompass anything unnecessary for the container's core function or app interpreter. For production, omit tools like text editors. Java or Python apps may need specific executables, while Go apps can run directly from a minimal "scratch" base image.
Anti-Pattern: Excessive Size
Adding non-essential executables to a container amplifies vulnerability risks and enlarges image size. This surplus bulk slows pull times and increases network data transmission.
Pattern: Trim the Fat
Start with a minimal official or self-generated base image to curb potential threats. Assess your app's true executable necessities, avoiding unnecessary installations. Exercise caution while removing language-dependent executables to craft a lean, cost-effective container image.
Cloning an Entire Git Repo Into a Container Image
It could look something like :
RUN git clone https://github.org/somerepoAnti-Pattern: Unnecessary Complexity
- External dependency: Relying on non-local sources for Docker image files introduces risk, as these files may not be vetted beforehand.
- Git clutter: A
git clonebrings surplus files like the.git/directory, increasing image size. The.git/folder may contain sensitive information, and removing it is error-prone. - Network dependency: Depending on container engine networking to fetch remote files adds complexity, especially with corporate proxies, potentially causing build errors.
- Executable overhead: Including the Git executable in the image is unnecessary unless directly manipulating Git repositories.
Pattern: Streamlined Assembly
Instead of a direct git clone in the Dockerfile, clone to a sub-directory in the build context via a shell script. Then, selectively add needed files using the COPY directive, minimizing unnecessary components. Utilize a .dockerignore file to exclude undesired files from the Docker image.
Exception: Multi-Stage Build
For a multi-stage build, consider cloning the repository to a local folder and then copying it to the build-stage container. While git clone might be acceptable, this approach offers a more controlled and error-resistant alternative.
Building a Docker Container Image “On the Fly”
Anti-Pattern: Skipping Registry Deployment
Performing cloning, building, and running a Docker image without pushing it to an intermediary registry is an anti-pattern. This skips security screenings, lacks a backup, and introduces untested images to deployment. The main reason is that there are security and testing gaps:
- Backup and rollback: Skipping registry upload denies the benefits of having a backup, which is crucial for quick rollbacks in case of deployment failures.
- Vulnerability scanning: Neglecting registry uploads means missing out on vulnerability scanning, a key element in ensuring data and user safety.
- Untested images: Deploying unpushed images means deploying untested ones, a risky practice, particularly in a production environment.
DZone's previously covered how to use penetration tests within an organization.
Pattern: Registry Best Practices
Build and uniquely version images in a dedicated environment, pushing them to a container registry. Let the registry scan for vulnerabilities and ensure thorough testing before deployment. Utilize deployment automation for seamless image retrieval and execution.
Running as Root in the Container
Anti-Pattern: Defaulting to Root User
Many new container users inadvertently run containers with root as the default user, a practice necessitated by container engines during image creation. This can lead to the following security risks:
- Root user vulnerabilities: Running a Linux-based container as root exposes the system to potential takeovers and breaches, allowing bad actors access inside the network and potentially the container host system.
- Container breakout risk: A compromised container could lead to a breakout, granting unauthorized root access to the container host system.
Pattern: User Privilege Management
Instead of defaulting to root, use the USER directive in the Dockerfile to specify a non-root user. Prior to this, ensure the user is created in the image and possesses adequate permissions for required commands, including running the application. This practice reduces security vulnerabilities associated with root user privileges.
Running Multiple Services in One Container
Anti-Pattern: Co-Locating Multiple Tiers
This anti-pattern involves running multiple tiers of an application, such as APIs and databases, within the same container, contradicting the minimalist essence of container design. The complexity and deviation from the design cause the following challenges:
- Minimalism violation: Containers are meant to be minimalistic instances, focusing on the essentials for running a specific application tier. Co-locating services in a single container introduces unnecessary complexity.
- Exit code management: Containers are designed to exit when the primary executable ends, relaying the exit code to the launching shell. Running multiple services in one container requires manual management of unexpected exceptions and errors, deviating from container engine handling.
Pattern: Service Isolation
Adopt the principle of one container per task, ensuring each container hosts a single service. Establish a local virtualized container network (e.g., docker network create) for intra-container communication, enabling seamless interaction without compromising the minimalist design of individual containers.
Embedding Secrets in an Image
Anti-Pattern: Storing Secrets in Container Images
This anti-pattern involves storing sensitive information, such as local development secrets, within container images, often overlooked in various parts like ENV directives in Dockerfiles. This causes the following security compromises:
- Easy to forget: Numerous locations within container images, like
ENVdirectives, provide hiding spots for storing information, leading to inadvertent negligence and forgetfulness. - Accidental copy of secrets: Inadequate precautions might result in copying local files containing secrets, such as
.envfiles, into the container image.
Pattern: Secure Retrieval at Runtime
Dockerignorebest practices: Implement a.dockerignorefile encompassing local files housing development secrets to prevent inadvertent inclusion in the container image. This file should also be part of.gitignore.- Dockerfile security practices: Avoid placing secrets in Dockerfiles. For secure handling during build or testing phases, explore secure alternatives to passing secrets via
--build-arg, leveraging Docker's BuildKit for enhanced security. - Runtime secret retrieval: Retrieve secrets at runtime from secure stores like HashiCorp Vault, cloud-based services (e.g., AWS KMS), or Docker's built-in secrets functionality, which requires a docker-swarm setup for utilization.
Failing to Update Packages When Building Images
Anti-Pattern: Static Base Image Packages
This anti-pattern stems from a former best practice where container image providers discouraged updating packages within base images. However, the current best practice emphasizes updating installed packages every time a new image is built. The main reason for this is outdated packages, which causes lagging updates. Base images may not always contain the latest versions of installed packages due to periodic or scheduled image builds, leaving systems vulnerable to outdated packages, including security vulnerabilities.
Pattern: Continuous Package Updates
To address this, regularly update installed packages using the distribution's package manager within the Dockerfile. Incorporate this process early in the build, potentially within the initial RUN directive, ensuring that each new image build includes updated packages for enhanced security and stability.
When striving to devise a foolproof solution, a frequent misstep is to undervalue the resourcefulness of total novices.
Building Container Security Into Development Pipelines Creates a Dynamic Landscape
In navigating the ever-evolving realm of containers, which are at an all-time high in popularity and directly proportional to the quantum of security threats, we've delved into a spectrum of crucial patterns and anti-patterns. From fortifying container images by mastering the intricacies of supply chain management to embracing the necessity of runtime secrets retrieval, each pattern serves as a cornerstone in the architecture of robust container security.
Unraveling the complexities of co-locating services and avoiding the pitfalls of outdated packages, we've highlighted the significance of adaptability and continuous improvement. As we champion the ethos of one-container-per-task and the secure retrieval of secrets, we acknowledge that container security is not a static destination but an ongoing journey. By comprehending and implementing these patterns, we fortify our containers against potential breaches, ensuring a resilient and proactive defense in an ever-shifting digital landscape.
Opinions expressed by DZone contributors are their own.

Comments