Custom Authenticator for WSO2 Identity Server (WSO2IS) SSO Login
Need a custom authenticator for your WSO2 Identity Server SSO login? We've got you covered. Let's look at implementing a WSO2IS authenticator, and extend the basic authenticator.
Join the DZone community and get the full member experience.
Join For Freein sso login, you can plug different custom authenticators in to the wso2is. there are two major types. one is local authenticators and other one is federated authenticators. federated authenticators are needed when you need to provide browser based redirections to another idp. as an example salesforce, google, facebook idps. (more details from here ). in other cases, we can implement a local authenticator.
default authenticator of wso2is, is the basic authenticator and it is also a local authenticator which authenticates the end user with connected user store using provided username and password.
in this post, lets try to implement a local authenticator for wso2is by extending the basic authenticator.
lets take following two sample requirements.
1. users who are login using “openid connect” must be authenticated with user store and must be authorized. in authorization, user must be verified that user is assigned to the specific role called “openidconnectrole”
2. users who are from application (service provider) “soasecurity.org” must be authenticated with user store and must be authorized. in authorization, user must be verified that user contains a specific attribute. as an example, user contains a mail with domain “soasecurity.org”
step 1 . extend the basic authenticator and implement a new authenticator.
as we are only worry about authorization, authentication can be happened as in the basic authenticator level. we need to add authorization logic after the authentication. therefore we only need to extend an one method in the basic authenticator which is “processauthenticationresponse()”
also, we need to modify the authenticator name by extending “getfriendlyname() ” and “getname()” methods.
you can fine the extend authenticator source from here .
step 2 . create osgi bundle out of your extended authenticator. sample project can be found from here . you can build the project using maven3
step 3. deploy osgi bundle in wso2 identity server (or apim) by copying in to /repository/components/dropins directory.
step 4. you need to edit the /repository/deployment/server/webapps/authenticationendpoint/login.jsp page with your new authenticator name.
because currently it is set to “basicauthenticator”. you can modify it as following by adding check for “basiccustomauthenticator”
if(localauthenticatornames.contains("basicauthenticator") | localauthenticatornames.contains("basiccustomauthenticator")){
if(localauthenticatornames.size()>0 && (localauthenticatornames.contains("basicauthenticator") || } else if(localauthenticatornames.size()>0 && (localauthenticatornames.contains("basicauthenticator") || localauthenticatornames.contains("basiccustomauthenticator"))) {localauthenticatornames.contains("basiccustomauthenticator"))) {step 5 . (optional) if you need to make this as the default authenticator for all service providers, you can configure it using /repository/conf/identity/service-providers/default.xml file.
this file is configured to “basicauthenticator” by default...you can modify it to “basiccustomauthenticator” by changing following two properties.
<name>basicauthenticator</name>
<displayname>basicauth</displayname>in to
<name>basiccustomauthenticator</name>
<displayname>basiccustom</displayname>step 6. restart the server.
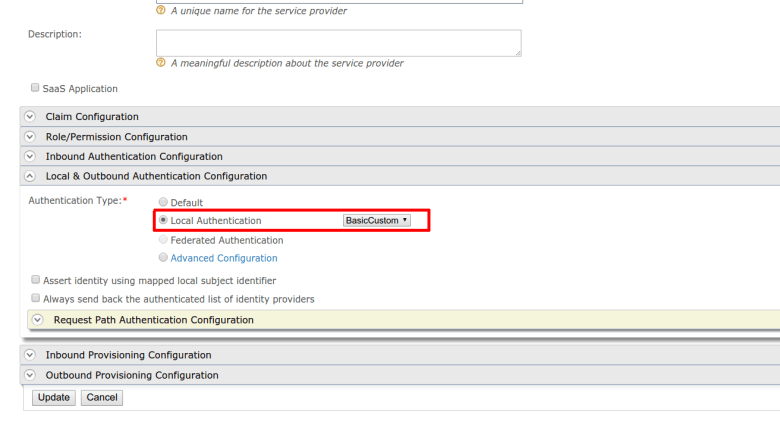
step 7 . you can login to management console and configure new authenticator for each service provider using “local & outbound authentication configuration”
step 8. try out.
you can debug the custom authenticator source by starting server in debug mode.
>sh wso2server.sh -debug 5005thanks for reading…!!!
Published at DZone with permission of Asela Pathberiya, DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments