Cybersecurity in the Cloud: Integrating Continuous Security Testing Within DevSecOps
AI assisted cyberattacks against cloud infrastructure is a fast growing threat. Integrating CST within DevSecOps serves as a crucial weapon for organizations.
Join the DZone community and get the full member experience.
Join For FreeCloud computing has revolutionized software organizations' operations, offering unprecedented scalability, flexibility, and cost-efficiency in managing digital resources. This transformative technology enables businesses to rapidly deploy and scale services, adapt to changing market demands, and reduce operational costs. However, the transition to cloud infrastructure is challenging. The inherently dynamic nature of cloud environments and the escalating sophistication of cyber threats have made traditional security measures insufficient. In this rapidly evolving landscape, proactive and preventative strategies have become paramount to safeguard sensitive data and maintain operational integrity.
Against this backdrop, integrating security practices within the development and operational workflows—DevSecOps—has emerged as a critical approach to fortifying cloud environments. At the heart of this paradigm shift is Continuous Security Testing (CST), a practice designed to embed security seamlessly into the fabric of cloud computing. CST facilitates the early detection and remediation of vulnerabilities and ensures that security considerations keep pace with rapid deployment cycles, thus enabling a more resilient and agile response to potential threats.
By weaving security into every phase of the development process, from initial design to deployment and maintenance, CST embodies the proactive stance necessary in today's cyber landscape. This approach minimizes the attack surface and aligns with cloud services' dynamic and on-demand nature, ensuring that security evolves in lockstep with technological advancements and emerging threats. As organizations navigate the complexities of cloud adoption, embracing Continuous Security Testing within a DevSecOps framework offers a comprehensive and adaptive strategy to confront the multifaceted cyber challenges of the digital age.
Most respondents (96%) of a recent software security survey believe their company would benefit from DevSecOps' central idea of automating security and compliance activities.
This article describes the details of how CST can strengthen your cloud security and how you can integrate it into your cloud architecture.
Key Concepts of Continuous Security Testing
Continuous Security Testing (CST) helps identify and address security vulnerabilities in your application development lifecycle. Using automation tools, it analyzes your complete security structure and discovers and resolves the vulnerabilities.
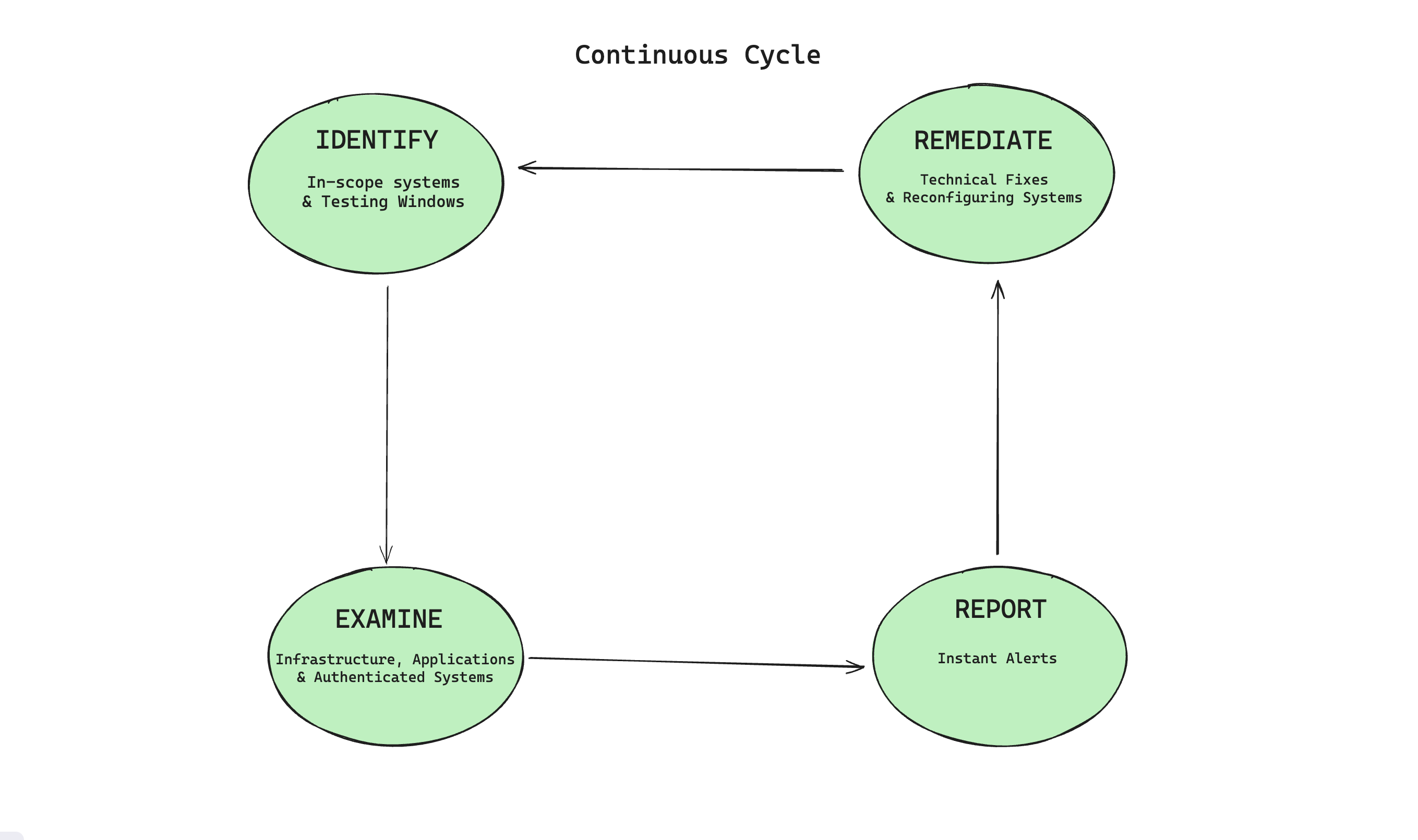
The following are the fundamental principles behind it:
- Shift-left approach: CST promotes early adoption of safety measures by bringing security testing and mitigation to the start of the software development lifecycle. This method reduces the possibility of vulnerabilities in later phases by assisting in the early detection and resolution of security issues.
- Automated security testing: Critical to CST is automation, which allows for consistent and quick evaluation of security measures, scanning for vulnerabilities, and code analysis. Automation ensures consistent and rapid security evaluation.
- Continuous monitoring and feedback: As part of CST, safety incidents and feedback chains are monitored in real-time, allowing security vulnerabilities to be identified and fixed quickly.
Integrating Continuous Security Testing Into the Cloud
Let's explore the phases involved in integrating CST into cloud environments.
Laying the Foundation for Continuous Security Testing in the Cloud
To successfully integrate Continuous Security Testing (CST), you must prepare your cloud environment first. Use a manual tool like OWASP or an automated security testing process to perform a thorough security audit and ensure your cloud environments are well-protected to lay a robust groundwork for CST.
Before diving into integrating Continuous Security Testing (CST) within your cloud infrastructure, it's crucial to lay a solid foundation by meticulously preparing your cloud environment. This preparatory step involves conducting a comprehensive security audit to identify vulnerabilities and ensure your cloud architecture is fortified against threats. Leveraging tools such as the Open Web Application Security Project (OWASP) for manual evaluations or employing sophisticated automated security testing processes can significantly aid this endeavor.
Conduct a detailed inventory of all assets and resources within your cloud architecture to assess your cloud environment's security posture. This includes everything from data storage solutions and archives to virtual machines and network configurations. By understanding the full scope of your cloud environment, you can better identify potential vulnerabilities and areas of risk.
Next, systematically evaluate these components for security weaknesses, ensuring no stone is left unturned. This evaluation should encompass your cloud infrastructure's internal and external aspects, scrutinizing access controls, data encryption methods, and the security protocols of interconnected services and applications. Identifying and addressing these vulnerabilities at this stage sets a robust groundwork for the seamless integration of Continuous Security Testing, enhancing your cloud environment's resilience to cyber threats and ensuring a secure, uninterrupted operation of cloud-based services.
By undertaking these critical preparatory steps, you position your organization to leverage CST effectively as a dynamic, ongoing practice that detects emerging threats in real-time and integrates security seamlessly into every phase of your cloud computing operations.
Establishing Effective Security Testing Criteria
The cornerstone of implementing Continuous Security Testing (CST) within cloud ecosystems is meticulously defining the security testing requirements. This pivotal step involves identifying a holistic suite of testing methodologies encompassing your security landscape, ensuring thorough coverage and protection against potential vulnerabilities.
A multifaceted approach to security testing is essential for a robust defense strategy. This encompasses a variety of criteria, such as:
- Vulnerability scanning: Systematic examination of your cloud environment to identify and classify security loopholes.
- Penetration testing: Simulated cyber attacks against your system to evaluate the effectiveness of security measures.
- Compliance inspections: Assessments to ensure that cloud operations adhere to industry standards and regulatory requirements.
- Source code analysis: Examination of application source code to detect security flaws or vulnerabilities.
- Configuration analysis: Evaluation of system configurations to identify security weaknesses stemming from misconfigurations or outdated settings.
- Container security analysis: Analysis focused on the security of containerized applications, including their deployment, management, and orchestration.
Organizations can proactively identify and rectify security vulnerabilities within their cloud architecture by selecting the appropriate mix of these testing criteria. This proactive stance enhances the overall security posture and embeds a culture of continuous improvement and vigilance across the cloud computing landscape. Adopting a comprehensive and systematic approach to security testing ensures that your cloud environment remains resilient against evolving cyber threats, safeguarding your critical assets and data effectively.
Choosing the Right Security Testing Tools for Automation
The transition to automated security testing tools is critical for achieving faster and more accurate security assessments, significantly reducing the manual effort, workforce involvement, and resources dedicated to routine tasks. A diverse range of tools exists to support this need, including Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and safety measures for Infrastructure as Code (IaC) etc.
These technologies are easy to integrate into Continuous Integration/Continuous Deployment (CI/CD) pipelines and improve security by finding and fixing vulnerabilities before development.
More than half of DevOps teams conduct SAST scans, 44% conduct DAST scans, and almost 50% inspect containers and dependencies as part of their security measures. However, when choosing the right tool for automation, consider features like ease of use, the ability to get updated with the vulnerability, and ROI vs. the cost of the tool.
When choosing the right automation tools, evaluating them based on several critical factors beyond their primary functionalities is vital. The ease of integration into existing workflows, their capacity for timely updates in response to new vulnerabilities, and the balance between their cost and the return on investment they offer are crucial considerations. These factors ensure that the selected tools enhance security measures and align with the organization's overall security strategy and resource allocation, facilitating a more secure and efficient development lifecycle.
Continuous Monitoring and Improvement
The bedrock of maintaining an up-to-date and secure cloud infrastructure lies in the practices of continuous monitoring and iterative improvement throughout the entirety of its lifecycle. Integrate your cloud log with Security Information and Event Management (SIEM) capabilities to get centralized security intelligence and initiate continuous monitoring and improvement. Similarly, ELK Stack (Elasticsearch, Logstash, Kibana) is another tool that can help you visualize, collect, and analyze your log data.
Regularly monitoring your security landscape and adapting based on the insights gleaned from testing and monitoring outputs are essential. Such a proactive approach not only aids in preemptively identifying and mitigating potential threats but also ensures that your security framework remains robust and adaptive to the ever-evolving cyber threat landscape.
Strategic Risk Management and Mitigation Efforts
Effective security management requires a strategic approach to evaluating and mitigating vulnerabilities, guided by their criticality, exploitability, and potential repercussions for the organization. Utilizing threat modeling techniques enables a targeted allocation of resources, focusing on areas of highest risk to reduce exposure and avert potential security incidents.
Following identifying critical vulnerabilities, devising and executing a comprehensive risk mitigation strategy is imperative. This strategy should encompass a range of solutions tailored to diminish the identified risks, including the deployment of software patches and updates, the establishment of enhanced security protocols, the integration of additional safeguarding measures, or even the strategic overhaul of existing systems and processes. Organizations can fortify their defenses by prioritizing and systematically addressing vulnerabilities based on severity and impact, ensuring a more secure and resilient operational environment.
Benefits of Continuous Security Testing in the Cloud
There are numerous benefits of using continuous security testing in cloud environments.
- Early vulnerability detection: Using CST, you can identify security issues early on and address them before they pose a risk.
- Enhanced security quality: To better defend your cloud infrastructure against cyberattacks, security testing gives it an additional layer of protection.
- Enhanced innovation and agility: CST enables faster release cycles by identifying risks early on, allowing you to take proactive measures to counter them.
- Enhanced team collaboration: CST promotes collaboration between different teams to cultivate a culture of collective accountability for security.
- Compliance with industry standards: By routinely assessing its security controls and procedures, you can lessen the possibility of fines and penalties for noncompliance with corporate policies and legal requirements.
Conclusion
In the rapidly evolving landscape of cloud computing, Continuous Security Testing (CST) emerges as a cornerstone for safeguarding cloud environments against pervasive cyber threats. By weaving security seamlessly into the development fabric through automation and vigilant monitoring, CST empowers organizations to detect and neutralize vulnerabilities preemptively.
The adoption of CST transcends mere risk management; it fosters an environment where security, innovation, and collaboration converge, propelling businesses forward. This synergistic approach elevates organizations' security posture and instills a culture of continuous improvement and adaptability. As businesses navigate the complexities of the digital age, implementing CST positions them to confidently address the dynamic nature of cyber threats, ensuring resilience and securing their future in the cloud.
Opinions expressed by DZone contributors are their own.

Comments