The Role of DevSecOps in Securing Multi-Cloud Architectures
Discover how DevSecOps enhances security in multi-cloud ecosystems, enabling safe implementation and addressing key challenges with effective strategies.
Join the DZone community and get the full member experience.
Join For FreeIn this article, we will explore how DevSecOps transforms security in multi-cloud ecosystems. Starting with the DevSecOps phase, we will delve into how multi-cloud environments can be implemented effectively and safely. Additionally, we will examine the most significant challenges associated with their use and discuss strategies to counter them successfully.
If a company uses several cloud providers, each cloud has its specifics and challenges for IT operation and development teams while promoting code and movement flexibility. Securing such an environment is a challenging proposition since it requires a delicate maintaining flexibility of an organization and its ability to defend against new and constantly emerging threats.
In the past, security was addressed as an add-on approach, which resulted in major deficiencies and created new bottlenecks. DevSecOps changes this narrative by integrating security into the DevSecOps process flows as part of the processes. This redraws team structures and makes deployments quicker and more secure. This article will unfold how DevSecOps can help businesses unlock the full potential of the multiple cloud worlds safely and securely.
Embedding Security at Every Stage of the DevSecOps Lifecycle
DevSecOps is the implementation of security in every area of an organization’s software delivery pipeline. Security should be integrated into the pipeline to prevent and stop potential issues before they have a chance to harm the business or its applications. Key practices include the following:
1. Automated Security Scans
Integrating automated security scans into CI/CD pipelines (continuous integration and continuous deployment) ensures that vulnerabilities are covered in the process and do not get deployed. Several tools help in finding code vulnerabilities and misconfigured systems, like SonarQube, OWASP ZAP, and Snyk.
2. Secure Coding Practices
Security should be built into the application by ensuring developers write their code securely, to reduce vulnerabilities. Organizations can achieve this by organizing period training on secure coding standards. Also, using SAST (Static application security testing) tools in compliance with code checks.
3. Threat Modeling
As a result of threat risk analysis during the design phase of an organization, it becomes easy for an organization to foresee threats and seek ways of handling such threats. This involves looking at the potential risks and vulnerabilities. Also, emphasizing the protection of insecure zones as far as potentially dangerous incidents are concerned.
This flowchart illustrates security integration in the DevSecOps lifecycle:
Security Strategies for Multi-Cloud Data and Business Workloads
Data protection and workload management, when an organization is employing multiple clouds, is a complex architectural function. There are issues like a lack of continuity in security policies on different platforms and the rising area of attacks. The following strategies are key:
1. Encryption and Data Protection
This is not able to be manipulated by unauthorized persons, hence the need the data encryption and protection. In that case should encrypt data both at rest and while in transit to help protect data that has been stored or is in the process of being transferred. Additionally, the security of encryption keys should be achieved using HSM (hardware security modules) and key management services.
2. Identity and Access Management (IAM)
IAM policies are the key to protecting cloud service delivery. In that respect, they have access to resources within more than one cloud-providing platform. Best practices might be applying the concept of role-based access control (RBAC) an aspect that involves limited user access based on a user’s role. Also, implementing multi-factor authentication (MFA) is strict for important accounts.
3. Threat Intelligence and Monitoring
Particularly, real-time threat intelligence tools can help detect and effectively prevent cases of perceived threats. This can be achieved by considering that security information and event management (SIEM) solutions should be used for the centralised monitoring of organizations’ security. Exploiting the regularity detection tools helps in determining out-of-norm activities and is also effective for achieving this.
4. Policy Automation
The effectiveness of managing security policies in parallel in multiple cloud environments eliminates human errors. There is often the possibility to use Infrastructure as Code (IaC) tools like Terraform and AWS CloudFormation for the provisioning processes when defining presets in which production is not allowed.
Comparative Table of Security Tools
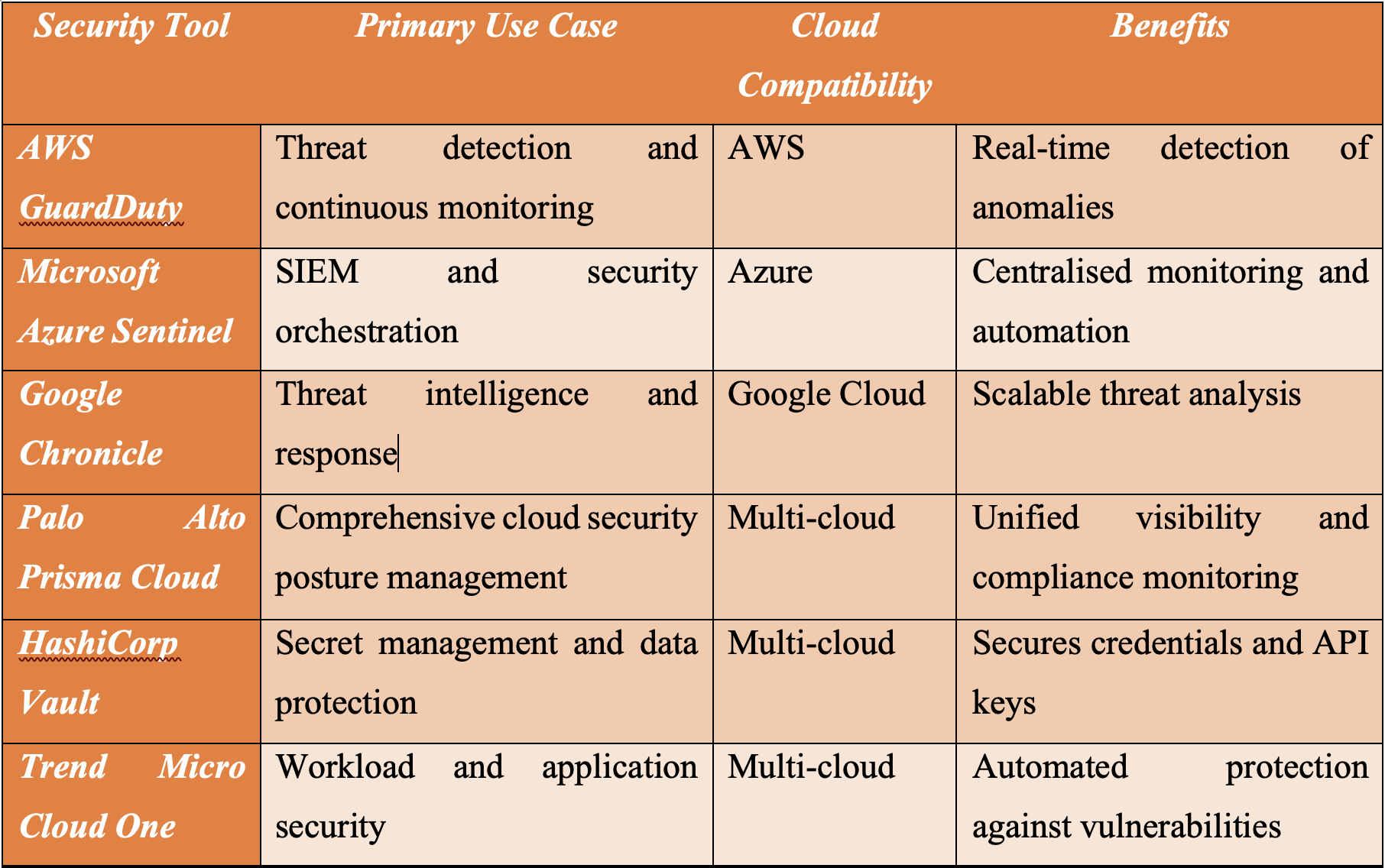
Real-World Examples of DevSecOps Adoption
Many organizations have effectively adopted DevSecOps to improve the security of multi-cloud environments.
1. Financial Sector: Protecting Customer Data
The largest financial service providers have integrated DevSecOps to safeguard their workloads in AWS, Azure, and Google Cloud. By integrating automated compliance checks and continuous monitoring tools, the organization can achieve improvement in security incidents by 40%.
Additionally, to ensure that they comply with strict rules for managing personal information like that envisaged under GDPR or the rules governing PCI DSS compliance.
2. Healthcare Industry: Regulatory Compliance
An example of applying DevSecOps was provided by a healthcare provider, which integrated the regulation of regulatory requirements while using multiple cloud solutions for data processing. Key measures included the use of compliance technologies to help reduce audit requirements. Also, HIPAA-compliant encryption of patient data for secure storage is effective.
3. E-commerce: Accelerating Threat Response
The e-commerce company used real-time monitoring tools and threat intelligence for the protection of its multi-cloud environment. This resulted in an optimised solution that realised a 60% decrease in incident response time. The issue of strong security measures as a way of improving customer trust.
Conclusion
In particular, multi-cloud solutions are gaining popularity. DevSecOps enables organizations, developers, operations, and security to work practically to enable security. By embedding security at every stage of the DevSecOps lifecycle, adopting best practices, and learning from real-world success stories, businesses can naturally reduce risk occurrences, protect sources, and work for compliance.
DevSecOps is a new culture that supports the integration of all teams. As much as organizations adopt this approach, they can achieve the full benefits of multi-cloud and ensure security.
Opinions expressed by DZone contributors are their own.

Comments