DevSecOps With Open Source Tools
DevSecOps: Integrating speed and security seamlessly. Conducts static and dynamic checks with each code update. Streamline processes without sacrificing safety.
Join the DZone community and get the full member experience.
Join For FreeDevSecOps involves adding advanced security measures to the DevOps process, as security is crucial for any application or data in any organization. It not only enhances security but also maintains the same efficiency and flexibility as DevOps. DevSecOps continuously incorporates, develops, and updates the latest security techniques for effective and secure results. To demonstrate DevSecOps, we will utilize open-source tools, freely available for showcasing data security. However, implementing and integrating security into the pipeline process requires additional resources and time for regular integration and testing. By doing so, we can achieve quicker response times and prevent attacks in advance.
Introduction
DevSecOps, short for Development Security Operations, encompasses the procedures for securely transferring data and thwarting attacks such as data breaches and tampering. Its significance lies in transforming the development cycle into a more secure environment. Traditionally, DevSecOps serves as a nexus between operations, development, and integration. There is a significant need for data security in online platforms like Clouds and repositories such as Git, which are accessed by the public regardless of their identity. Therefore, implementing DevSecOps with open-source tools to secure data pulled or pushed onto repositories can offer substantial benefits, as fixing issues at the code level is often more robust and advantageous if executed correctly.
DevSecOps introduces a fresh approach to integrating security processes into development and operations, enabling the creation of a fast-paced process chain. Revisiting security poses a challenge in terms of time and obstacles within the era of continuous production cycles. The concept of DevSecOps emerged as a promising solution to this dilemma, ensuring security integration across the Development Operation workflow without disrupting the efficiency and pace of DevOps processes. This approach also empowers developers to grasp the importance of data security, facilitating the identification of vulnerabilities effectively.
Related Work
Embedding security within the CI/CD pipeline proves highly beneficial in identifying numerous bugs and data vulnerabilities and generating multiple reports on defects and faults discovered in the source code retrieved from the repository. This approach involves configuring various static and dynamic tools to check the code for defects directly within the pipeline, rather than dedicating a separate phase after code deployment for security checks, where programmers would need to rescan for faults and potentially redesign the code from scratch if significant issues arise.
Static code scanning occurs without executing the code, typically in a non-runtime environment, and examines the source code for code smells, flaws, and other surface-level bugs. Dynamic testing, on the other hand, involves security scanning by executing the code in a runtime environment after it has undergone static testing. This process detects any additional bugs and vulnerabilities post-deployment. Once both static and dynamic tests are completed, the results are displayed, indicating the total number of faults, and the same results are forwarded via email for further corrections.
Proposed Work
The figure below illustrates the proposed DevSecOps system for our project. In this system, our solution integrates the processes of development, testing, security analysis, and deployment. Users interact with the system through a user interface (UI) where they define the location of the source code in the Source Code Management (SCM) repository to be scanned for security issues.
Upon receiving this information, the solution automatically retrieves the source code from the SCM repository and initiates the security scan according to a predefined schedule. The project conducts both static and dynamic security analyses, generating corresponding security reports. These reports contain detailed information about identified security vulnerabilities.
Furthermore, the system allows for the storage of these reports as structured data files. Subsequently, the reports can be seamlessly integrated with an issue-tracking system, facilitating efficient management and resolution of identified security issues.
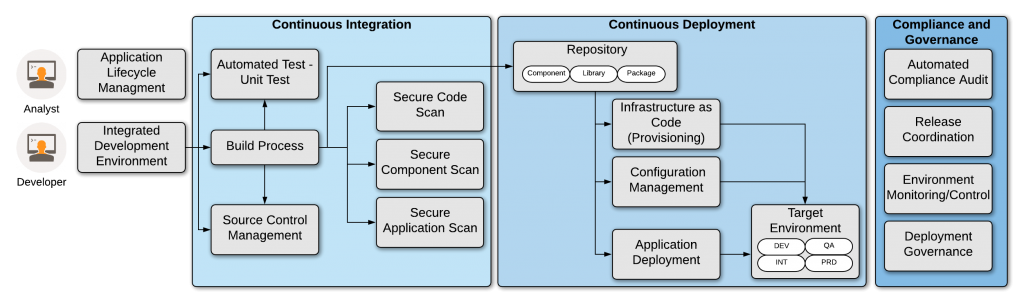
Figure 1: DevSecOps automated pipeline reference architecture
Implementation
>
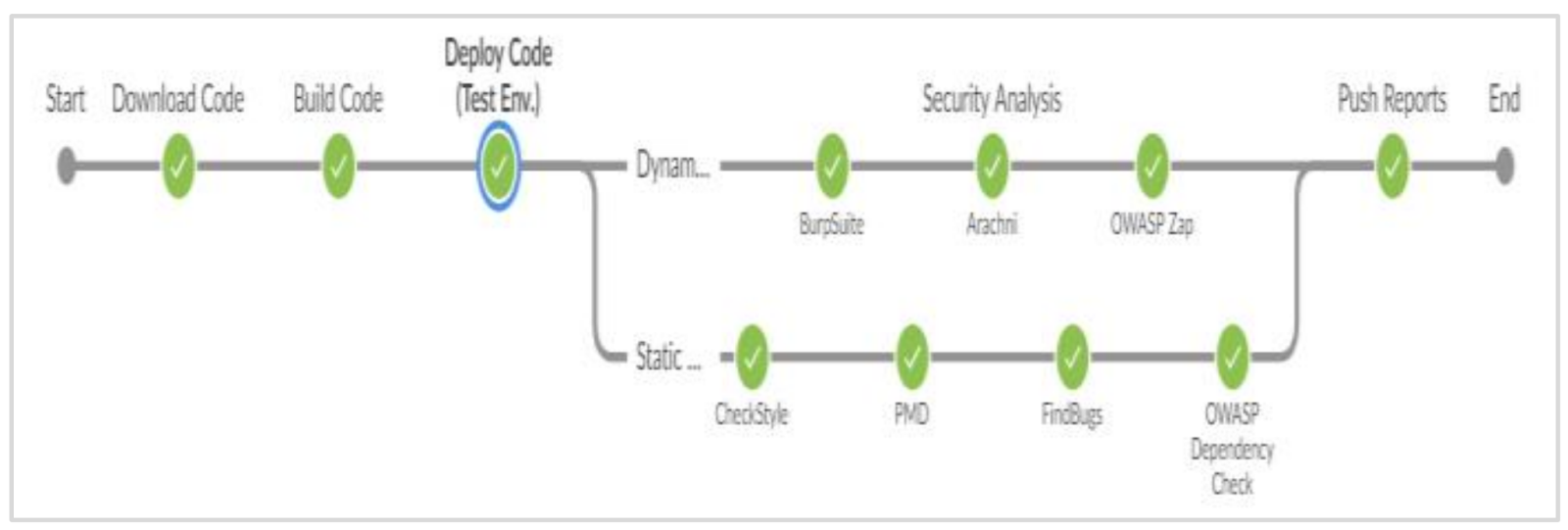
The pipeline graph above illustrates the various steps involved in the journey of the source code towards its final deployment. Jenkins, a continuous integration server, plays a pivotal role in this process. It begins by checking out the source code from a source code repository, typically supporting various source code management systems, with Git being one of the most widely used.
Jenkins downloads the code or module onto the local system, where programmers can upload or load the block or module of code they've developed into a common repository, where it is committed and stored. This additional code undergoes unit testing and can be further utilized by other colleagues for code enhancement.
Utilizing Git with Jenkins allows developers to consistently commit code changes to GitHub repositories. This fosters frequent code commits within organizations, enhancing collaboration and software quality through the continuous integration process.
Software Configuration Management and Build Engineers maintain all software repositories, ensuring that incremental changes are synchronized across different code branches. They manage all software build infrastructure for the continuous integration of code changes, as well as the lab infrastructure.
During the build stage, the code is compiled. For languages like Java, tools such as Maven can be integrated into Jenkins. In this phase, necessary libraries or dependencies are downloaded from the internet to support the proper functioning of the code.
Moving on to the testing phase, various types of testing are performed, including unit testing, where each chunk or unit of source code is tested for bugs. If any bugs are detected, the programmer is promptly notified, and reports are emailed.
Jenkins employs plugins for static security testing, including Checkstyle, PMD, and FindBugs. Checkstyle verifies the syntax of the code, PMD identifies unused objects, methods, and variables, while FindBugs categorizes bugs found in the code into four categories: scariest, scary, troubling, and of concern, respectively.
For dynamic security testing, Jenkins utilizes plugins such as the OWASP dependency check. This plugin checks for unknown dependencies present along with those downloaded during the build stage, and identifies publicly disclosed open-source vulnerabilities, highlighting any unknown dependencies for further investigation.
The release stage involves further corrections and error rechecking of the code block, where programmers address any issues before pushing the fixed code onto the production line of the pipeline for deployment.
Conclusion
DevSecOps effectively merges the seemingly conflicting objectives of "speed of delivery" and "secure code" into a single streamlined and automated process. It emerged as a blessing, ensuring the integration of security measures without disrupting the pace of DevOps-driven IT processes
In this approach, static and dynamic security checks are conducted for every version or addition of the source code. The test results from these security checks are then forwarded to the issue tracking system for thorough monitoring and analysis of potential threats. This system promptly informs programmers about any identified security vulnerabilities.
Thus, this project validates the building blocks of software development without impeding the process or compromising on security. It ensures that code is both delivered efficiently and remains secure throughout its lifecycle.
Published at DZone with permission of Yusuf Tezcan. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments