Understanding and Mitigating IP Spoofing Attacks
The article discusses how IP Spoofing is executed by cyber criminals and what measures and steps we can take to prevent it.
Join the DZone community and get the full member experience.
Join For FreeSpoofing is a type of cyber-attack used by hackers to gain unauthorized access to a computer or a network, IP spoofing is the most common type of spoofing out of the other spoofing method. With IP Spoofing the attacker can hide the true source of the IP packets to make it difficult to know the origin of the attack. Once access to a network or a device/host is achieved, cybercriminals usually mine them for sensitive data, with computers they can turn into zombies and can be used to launch Denial-of-Service (DoS) attacks.
What Is IP Spoofing?
IP addresses are used for communication between devices on the internet. Cybercriminals use a false source IP address to hide and impersonate another system. Essentially making it harder for the destination system to detect. Such attacks come with the intent to steal sensitive data, infect your computer with malware or viruses, or even crash your server.
How IP Spoofing Works
So, let’s get deeper into how IP spoofing works. An IP address is a series of numbers that identifies your device on the internet and every device that connects to the internet has an IP address with its use they are able to exchange data., below is what an IP header packet looks like
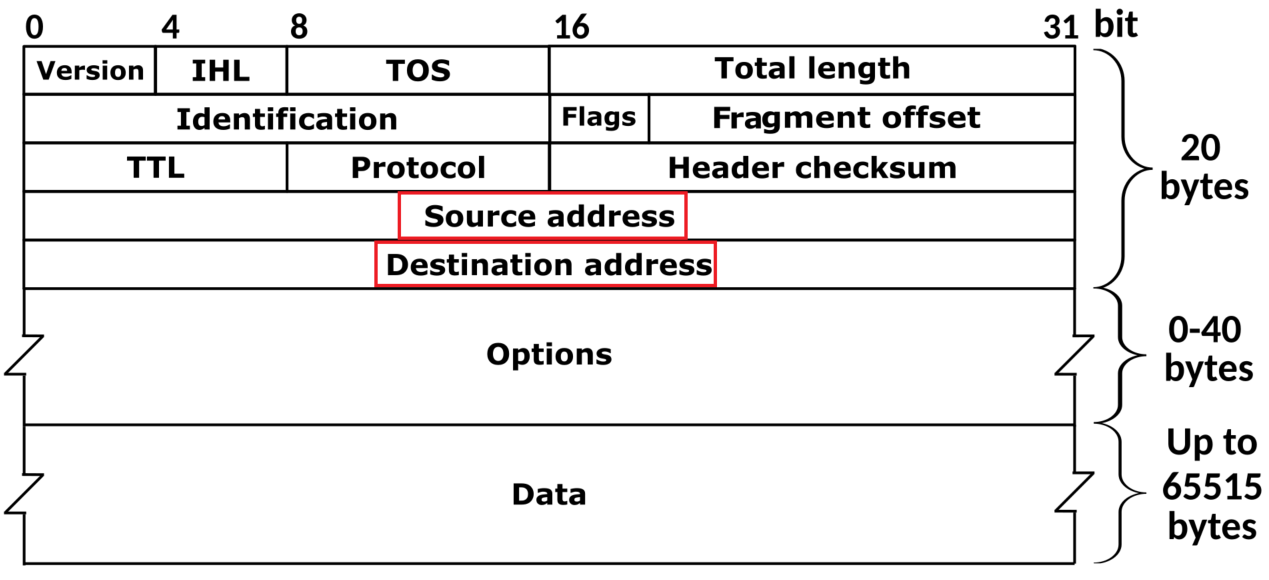
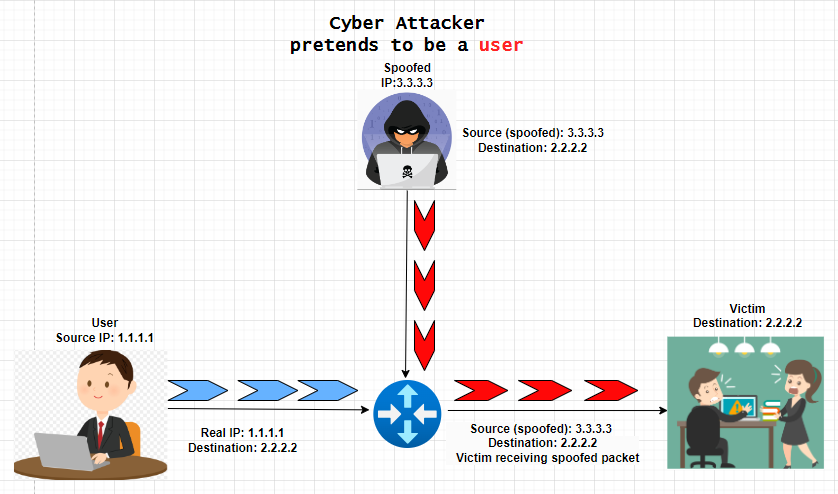
IP Spoofing takes advantage of the source by faking the source inside the packet similarly it's like putting a fake return address on an envelope in a mailbox. Most of the time when an IP packet travels to reach its destination it goes over multiple intermediate devices or routers which do not inspect the source address at all.
In the below example, you can see that the cyber attacker has successfully changed the source IP of the packet from 1.1.1.1 to 3.3.3.3 (changed IP).
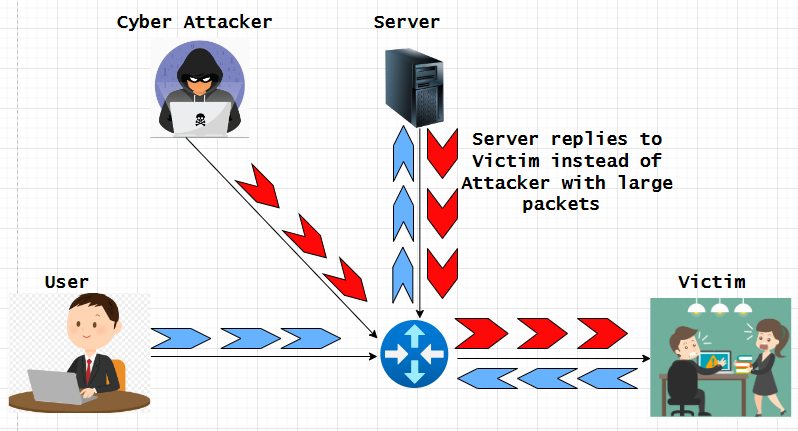
Now, let's say that someone wants to disrupt and completely disconnect their internet service, they can send packets with a fake source address to that victim with so many packets that the victim has no resources to process legitimate packets. An attacker can use many different fake source addresses across many packets and often it's not feasible to trace back the attacker to its origin to block the attack at the victim it gets even worse when an attacker can commandeer intermediate nodes to amplify an attack by triggering that node to send the victim very large packets which takes more resources to process as seen in the image below.
Types of IP Spoofing
The below three are the most common types of IP Spoofing
1. Distributed Denial of Service (DDoS) Attacks
A Distributed Denial of Service (DDoS) attack is the most common cyber attack which uses a spoofing method, essentially the targeted host, service, or network is flooded with Internet traffic.
Key Characteristics of DDoS Attacks
- Volume-based attacks: The idea is to saturate the bandwidth of the target host. Some of the ways are to perform ICMP floods, UDP floods, and other spoofed packet floods. The attack is measured in bits per second (bps).
- Protocol attacks: These attacks work on exploiting weaknesses in network protocols. For example, in TCP it would use SYN floods. Fragment packet attacks are another example where packets are fragmented and reassembled to evade security controls and launch attacks. Ping of death and Smurf DDoS are some of the others. These attacks are measured in packets per second (pps).
- Application layer attacks: These target specific applications or services, making the attack look like legitimate traffic. Examples include HTTP floods, GET/POST floods, and Slowloris. These attacks are measured in requests per second (rps).
2. Masking Botnet Devices
IP Spoofing can be used to access computers by masking botnets. A botnet once it gains access to a PC is used by the perpetrator to control from a single source. The PCs that are affected by the botnet carry out malicious attacks on attackers' behalf.
3. Man-In-The-Middle Attacks
Man-in-the-middle attack is used to alter packets and transmit them without the original sender or receiver knowing. If attackers spoof an IP address and obtain access to personal accounts, they can follow any aspect of the communication. Once access is achieved, personal information can be easily stolen, perpetrators can direct users to fake websites, and more. Over time hackers collect a wealth of confidential information they can use or sell — which means a man-in-the-middle attack can be more valuable and lucrative than the others.
How To Detect IP Spoofing
Network monitoring tools can be used to analyze traffic at endpoints. Although it's difficult for end users to detect IP spoofing attacks, the change of source IP is done in the Network layer i.e. Layer 3 of the Open System Interconnection communications model. Since the modification is done at a packet level it doesn't leave a sign of alterations. Usually, spoofed connection requests can appear genuine from the outside. Let's discuss the ways you can mitigate such attacks:
- Packet filtering: It is used to analyze packets to check for any inconsistencies between the packet's IP address and the IP address detailed on the access control list (ACLs), it is used to detect tampered packets.
- Ingress filtering: Check incoming packets to assess whether the source IP header matches a permitted source address. If it fails the check, the packet is dropped.
- Egress filtering: Outbound packets are verified for their source addresses which don't match with the ones of the organization's network. This prevents internal users from initiating IP spoofing attacks
How To Protect Against IP Spoofing
With the way IP Spoofing works, it conceals the attacker's identity as it is hard to trace back to its original source. However, we can take some anti-spoofing steps to lower the risks of such attacks.
- Constantly scanning networks for irregular activities
- Packet filtering mechanisms to detect source IPs divergent from the organization's registered network
- Authenticating all IP addresses and deploying a network attack-prevention tool
- Enabling Reserve Path Forwarding on Routers/Firewalls to verify that traffic is to be blocked on an interface if it is sourced from forged IP addresses.
Example of a Spoofing Attack
GitHub Spoofing Attack (2019)
In July 2019, a sophisticated phishing campaign targeted GitHub users, the objective was to steal their login credentials and two-factor authentication (2FA) codes. The intrusion involved spoofing methods where the attackers pretended as GitHub and other well-known entities to gain the trust of users to give up sensitive information.
Attack Details
- Phishing emails: Emails were sent by the attackers that presented themselves to be from GitHub. The message in the email was to notify the user about suspicious login attempts, account security problems, or required updates making a situation of high importance for the security of their account urging users to click on a link to secure their accounts.
- Spoofed websites: The URL links took the users to websites that mirrored GitHub's login page. Now when the users entered their credentials, the attackers captured this information.
- Credential harvesting: Once the user entered their credentials and the 2FA codes on the spoofed websites, attackers were able to gather this information. This enabled the attackers to gain unauthorized access to the user's GitHub accounts.
- Exploitation: Access to GitHub accounts, will potentially lead up to a lot of exploitation.
- Alter or delete code repositories
- Access private repositories containing sensitive information.
- Use the compromised accounts to launch further attacks within the network or organization
Conclusion
IP Spoofing remains a prevalent and dangerous type of cyberattack that allows perpetrators to gain unauthorized access to networks and systems by concealing their true identity. Altering the source IP address and tracing it back to the origin of the attack is significantly difficult. As discussed in the GitHub spoofing attack, various tactics were used and they were effective in deceiving users to give you their sensitive info, leading to credential theft, unauthorized access, and further exploitation.
To mitigate such attacks we need to employ a comprehensive network monitoring system, tools such as packet filtering, and ingress and egress filtering. Also, advanced techniques like enabling Reverse Path Forwarding on routers and firewalls will help verify the source of the IP packet.
A proactive approach is a must to protect networks and users from IP spoofing attacks which would reduce the risk and impact of such attacks and help to safeguard sensitive data.
Opinions expressed by DZone contributors are their own.

Comments