Java Web Application Security - Part V: Penetrating with Zed Attack Proxy
Join the DZone community and get the full member experience.
Join For Freeweb application security is an important part of developing applications. as developers, i think we often forget this, or simply ignore it. in my career, i've learned a lot about web application security. however, i only recently learned and became familiar with the rapidly growing "appsec" industry.
i found a disconnect between what appsec consultants were selling and what i was developing. it seemed like appsec consultants were selling me fear, mostly because i thought my apps were secure. so i set out on a mission to learn more about web application security and penetration testing to see if my apps really were secure. this article is part of that mission, as are the previous articles i've written in this series.
- java web application security - part i: java ee 6 login demo
- java web application security - part ii: spring security login demo
- java web application security - part iii: apache shiro login demo
- java web application security - part iv: programmatic login apis
when i first decided i wanted to do a talk on webapp security, i knew it would be more interesting if i showed the audience how to hack and fix an application. that's why i wrote it into my original proposal :
webapp security: develop. penetrate. protect. relax.
in this session, you'll learn how to implement authentication in your
java web applications using spring security, apache shiro and good ol'
java ee container managed authentication. you'll also learn how to
secure your rest api with oauth and lock it down with ssl.
after learning how to develop authentication, i'll introduce you to
owasp, the owasp top 10, its testing guide and its code review guide.
from there, i'll discuss using webgoat to verify your app is secure and
commercial tools like webapp firewalls and accelerators.
at the time, i hadn't done much webapp pentesting . you can tell this from the fact that i mentioned webgoat as the pentesting tool. from webgoat's project page :
webgoat is a deliberately insecure j2ee web application maintained by owasp designed to teach web application security lessons. in each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the webgoat application. for example, in one of the lessons the user must use sql injection to steal fake credit card numbers. the application is a realistic teaching environment, providing users with hints and code to further explain the lesson.
what i really meant to say and use was zed attack proxy , also known as owasp zap. zap is a java desktop application that you setup as a proxy for your browser, then use to find vulnerabilities in your application. this article explains how you can use zap to pentest a web applications and fix its vulnerabilities.
the application i'll be using in this article is the ajax login application i've been using throughout this series. i think it's great that projects like damn vulnerable web app and webgoat exist, but i wanted to test one that i think is secure, rather than one i know is not secure. in this particular example, i'll be testing the spring security implementation, since that's the framework i most often use in my open source projects.
zed attack proxy tutorial
- download and run the application
- install and configure zap
- perform a scan
- fix vulnerabilities
- summary
download and run the application
to begin,
download the application
and expand it on your hard drive. this app is the completed version of the ajax login application referenced in
java web application security - part ii: spring security login demo
. you'll need java 6 and maven installed to run the app. run it using
mvn jetty:run
and open
http://localhost:8080
in your browser. you'll see it's a simple crud application for users and you need to login to do anything.
install and configure zap
the
zed attack proxy
(zap) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications.
download
the latest version (i used 1.3.0) and install it on your system. after
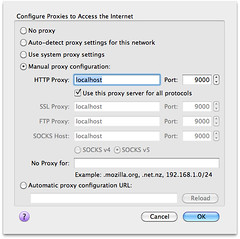
installing, launch the app and change the proxy port to 9000 (tools >
options > local proxy). next, configure your browser to proxy
requests through port 9000 and allow localhost requests to be proxied. i
used firefox 4 (preferences > advanced > network > connection
settings). when finished, your proxy settings should look like the
following screenshot:
another option (instead of removing localhost) is to add an entry to your hosts file with your production domain name. this is what i've done for this demo.
127.0.0.1 demo.raibledesigns.com
i've also configured apache to proxy requests to jetty with the following mod_proxy settings in my httpd.conf:
<ifmodule mod_proxy.c>
proxyrequests off
proxypreservehost off
<virtualhost *:80>
proxypass / http://localhost:8080/
</virtualhost>
<virtualhost *:443>
sslengine on
sslproxyengine on
sslcertificatefile "/etc/apache2/ssl.key/server.crt"
sslcertificatekeyfile "/etc/apache2/ssl.key/server.key"
proxypass / https://localhost:8443/
</virtualhost>
</ifmodule>
perform a scan
now you need to give zap some data to work with. using firefox, i
navigated to http://demo.raibledesigns.com and browsed around a bit,
listing users, added a new one and deleted an existing one. after doing
this, i noticed a number of flags in the zap ui under sites. i then
right-clicked on each site (one for http and one for https) and selected
attack > active scan site. you should be able to do this from the
"active scan" tab at the bottom of zap, but
there's a bug when the urls are the same
.
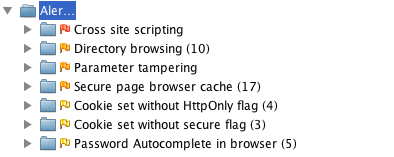
after doing this, i received a number of alerts, ranging from high
(cross-site scripting) to low (password autocomplete). the screenshot
below shows the various issues.
now let's take a look at how to fix them.
fix vulnerabilities
one of the things not mentioned by the scan, but #1 in
seven security (mis)configurations in java web.xml files
,
is custom error pages not configured. custom error pages are configured
in this app, but error.jsp contains the following code:
<% if (exception != null) { %>
<% exception.printstacktrace(new java.io.printwriter(out)); %>
<% } else { %>
please check your log files for further information.
<% } %>
stack traces can be really useful to an attacker, so it's important to start by removing the above code from src/main/webapp/error.jsp .
the rest of the issues have to do with xss, autocomplete, and cookies. let's start with the easy ones. fixing autocomplete is easy enough; simply changed the html in login.jsp and userform.jsp to have autocomplete="off" as part of the <form> tag.
then modify web.xml so http-only and secure cookies are used. while you're at it, add session-timeout and tracking-mode as recommended by the aforementioned web.xml misconfigurations article.
<session-config>
<session-timeout>15</session-timeout>
<cookie-config>
<http-only>true</http-only>
<secure>true</secure>
</cookie-config>
<tracking-mode>cookie</tracking-mode>
</session-config>
next, modify spring security's remember me configuration so it uses secure cookies. to do this, add use-secure-cookies="true" to the <remember-me> element in security.xml .
<remember-me user-service-ref="userservice" key="e37f4b31-0c45-11dd-bd0b-0800200c9a66"
use-secure-cookie="true"/>
unfortunately, spring security doesn't support httponly cookies , but will in a future release.
the next issue to solve is disabling directory browsing. you can do this by copying jetty's webdefault.xml (from the org.eclipse.jetty:jetty-webapp jar) into src/test/resources and changing its "dirallowed" <init-param> to false:
<servlet>
<servlet-name>default</servlet-name>
<servlet-class>org.mortbay.jetty.servlet.defaultservlet</servlet-class>
<init-param>
<param-name>acceptranges</param-name>
<param-value>true</param-value>
</init-param>
<init-param>
<param-name>dirallowed</param-name>
<param-value>false</param-value>
</init-param>
<init-param>
you'll also need to modify the plugin's configuration to point to this file by adding it to the <webappconfig> section in pom.xml.
<configuration>
<webappconfig>
<contextpath>/</contextpath>
<defaultsdescriptor>src/test/resources/webdefault.xml</defaultsdescriptor>
</webappconfig>
of course, if you're running in production you'll want to configure this in your server's settings rather than in your pom.xml file.
next, i set out to fix secure page browser cache issues . i had the following settings in my sitemesh decorator:
<meta http-equiv="cache-control" content="no-store"/> <meta http-equiv="pragma" content="no-cache"/>
however, according to zap, the first meta tag should have "no-cache" instead of "no-store", so i changed it to "no-cache".
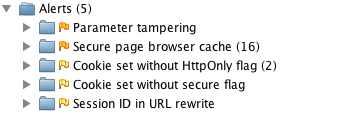
after making all these changes, i created a new zap session and ran an active scan on both sites again. below are the results:
i believe the first issue (parameter tampering) is because i show the error page when a duplicate user exists. to fix this, i changed userformcontroller so it catches a userexistsexception and sends the user back to the form.
try {
usermanager.saveuser(user);
} catch (userexistsexception uex) {
result.adderror(new objecterror("user", uex.getmessage()));
return "userform";
}
however, this still doesn't seem to cause the alert to go away. this is likely because i'm not filtering/escaping html when it's first submitted. i believe the best solution for this would be to use something like owasp's esapi to filter parameter values. however, i was unable to find integration with spring mvc's data binding, so i decided not to try and fix this vulnerability.
finally, i tried to disable jsessionid in urls using suggestions from stack overflow . the previous setting in web.xml (<tracking-mode>cookie</tracking-mode>) should do this, but it doesn't seem to work with jetty 8. the other issues (secure page browser cache, httponly cookies and secure cookies), i was unable to solve. the last two are issues caused by spring security as far as i can tell.
summary
in this article, i've shown you how to pentest a web application using
firefox and owasp's zed attack proxy (zap). i found zap to be a nice
tool for figuring out vulnerabilities, but it'd be nice if it had a
"retest" feature to see if you fixed an issue for a particular url. it
does have a "resend" feature, but running it didn't seem to clear alerts
after i'd fixed them.
the issues i wasn't able to solve seemed to be mostly related to frameworks (e.g. spring security and httponly cookies) or servers (jetty not using cookies for tracking). my suspicion is the jetty issues are because it doesn't support servlet 3 as well as it advertises. i believe this is fair; i am using a milestone release after all. i tried scanning http://demo.raibledesigns.com/ajax-login (which runs on tomcat 7 at contegix ) and confirmed that no jsessionid exists.
hopefully this article has helped you understand how to figure out security vulnerabilities in your web applications. i believe zap will continue to get more popular as developers become aware of it. if you feel ambitious and want to try and solve all of the issues in my ajax login application, feel free to fork it on github .
if you're interested in talking more about webapp security, please leave a comment, meet me at jazoon later this week or let's talk in july at über conf .from http://raibledesigns.com/rd/entry/java_web_application_security_part4
Opinions expressed by DZone contributors are their own.

Comments