JWT (JSON Web Tokens) Are Better Than Session Cookies
In this article, we take a look at the JSON Web Tokens (JWT), what advantages they hold, and how they constitute an improvement over older authentication systems.
Join the DZone community and get the full member experience.
Join For FreeWhat Is a Token-Based Authentication System?
The token-based authentication systems allow users to enter their username and password in order to obtain a token which allows them to fetch a specific resource - without entering their username and password at each request. Once their token has been obtained, the user can use the token to access specific resources for a set time period.
JWT (pronounced 'jot') is a token based authentication system. It is a compact, URL-safe means of representing claims to be transferred between two parties. The claims in a JWT are encoded as a JSON object that is digitally signed using JSON Web Signature. The JWT is a self-contained token which has authentication information, expire time information, and other user defined claims digitally signed.
How We Used to Do Authentication
HTTP is a stateless protocol. That means it doesn't store any state from request to response. If you login for one request, you'll be forgotten and will need to login again to make another request. As you can imagine, this can get very annoying, very fast.
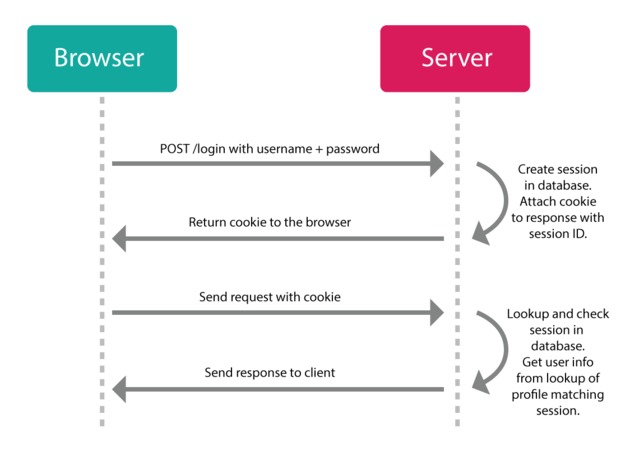
The old-school solution was to create what's called a "session." A session is implemented in two parts:
An object stored on the server that remembers if a user is still logged in, a reference to their profile, etc.
A cookie on the client-side that stores some kind of ID that can be referenced on the server against the session object's ID.
![Image title]()
This solution still works, but nowadays we have different requirements, i.e. hybrid application or single page application contacting multiple backends (split up into separate micro-service authetication servers, databases, image processing servers, etc). In these types of scenarios, the session cookie we get from one server won't correspond to another server.
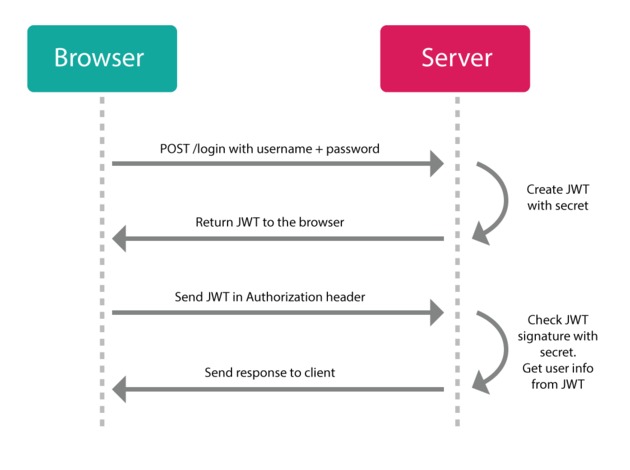
JWTs don't use sessions and have no problem with micro-service architectures. Instead of making a session and setting a cookie, the server will send you a JSON Web Token instead. Now you can use that token to do whatever you want to do with the server (that you have authorization to do).
Think of it like a hotel key: you register at the front-desk, and they give you one of those plastic electronic keys with which you can access your room, the pool, and the garage, but you can't open other people's rooms or go into the manager's office. And, like a hotel key, when your stay has ended, you're simply left with a useless piece of plastic (i.e., the token doesn't do anything anymore after it's expired).
Advantages of JWTs
No Session to Manage (stateless): The JWT is a self contained token which has authetication information, expire time information, and other user defined claims digitally signed.
Portable: A single token can be used with multiple backends.
No Cookies Required, So It's Very Mobile Friendly
Good Performance: It reduces the network round trip time.
Decoupled/Decentralized: The token can be generated anywhere. Authentication can happen on the resource server, or easily separated into its own server.
Opinions expressed by DZone contributors are their own.


Comments