LinkedIn Security Vulnerability: A Lesson for Security Engineers
A new LinkedIn vulnerability shows how even a small loophole from the engineering team can expose job seekers to phishing attacks.
Join the DZone community and get the full member experience.
Join For FreeSecurity-related controversies are not new for LinkedIn. Here's the latest one, which was discovered by a cybersecurity firm, Cyphere, in Aug 2021. As per the company's report, anyone can post jobs on behalf of any company they want, without the consent or knowledge of the original company!
This means hackers can post jobs impersonating a reputed company and invite the job applications, receiving thousands of CVs on the fake email address, or redirect candidates to a malicious or phishing website!
Here's how it works.
- First of all, you need to create a company page on LinkedIn. It's free for all. (This can be any random company's page and not necessarily the one for which you want to post a job).
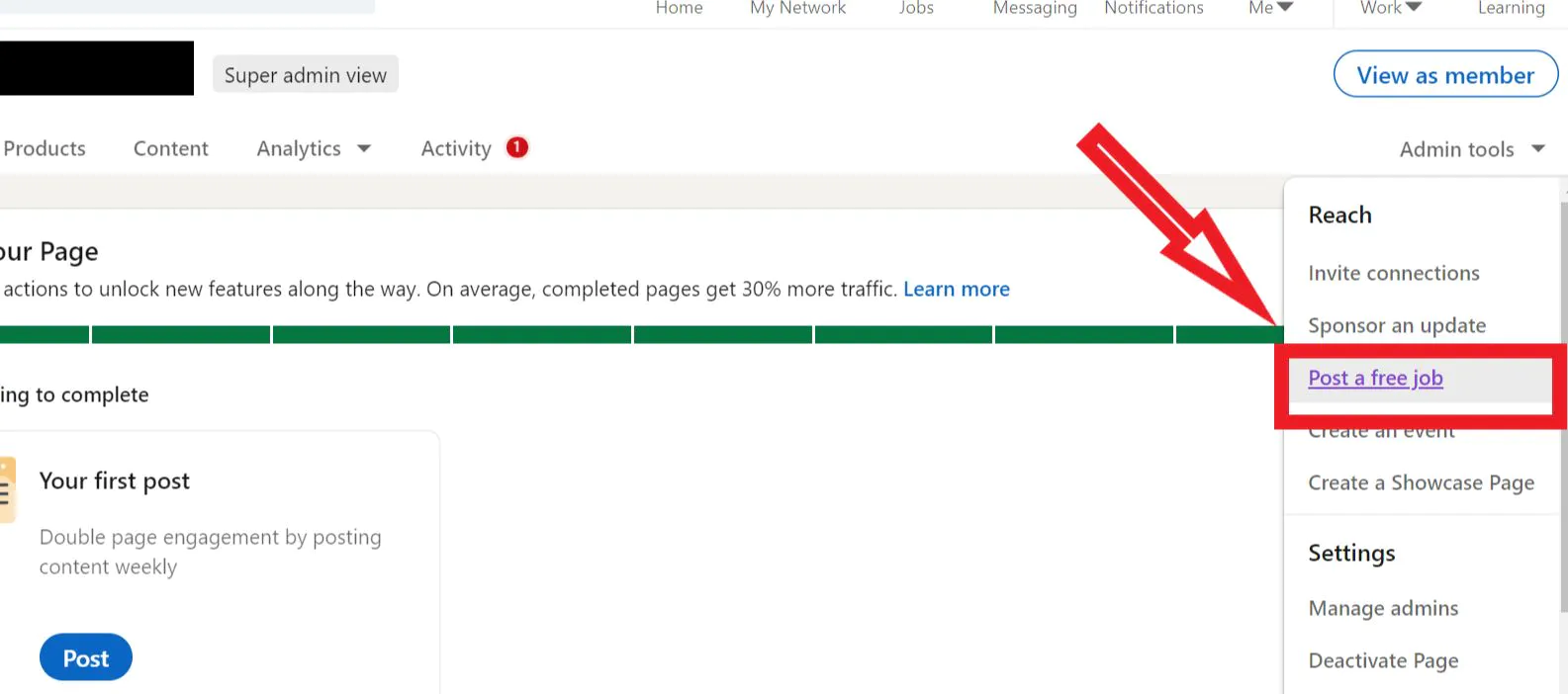
- Then, click on Admin Tools and select Post a free job, as shown in the screenshot below.
![Post a free job in the Admin Tools]()
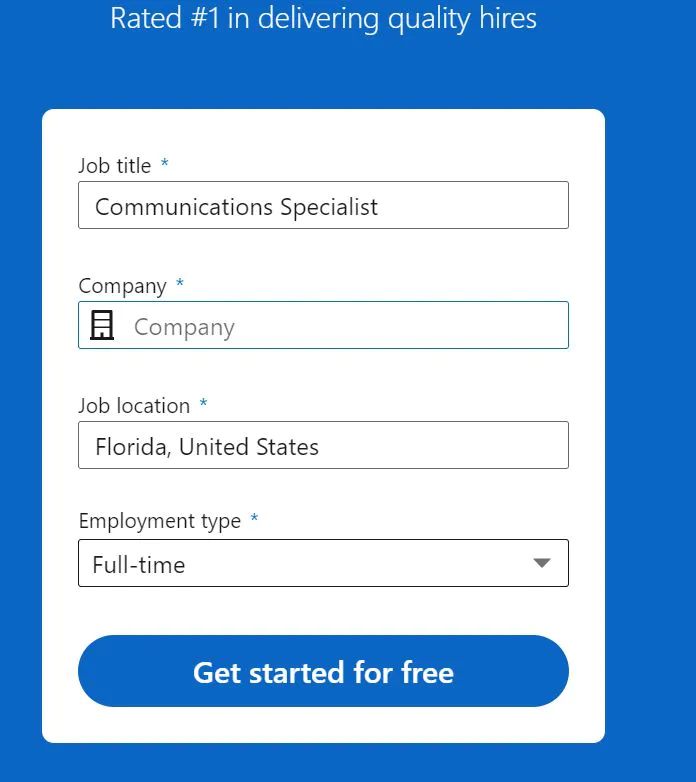
- You will be redirected to a job posting page, where you can select any company you want to post a job on behalf of! LinkedIn doesn't authenticate whether you are the legit representative of that company.
![Setting Up A Job Posting]()
![Dropdown For Selecting Company]()
- Yes, there are exceptions here. If you try to post jobs on behalf of a handful of big companies like Google, Facebook, Microsoft, Apple, Amazon, etc., you will be shown an error message like below.

Once the job is posted, even the original company's super admin can't do anything about it!
LinkedIn's Response
Cyphere reached to BleepingComputer to reconfirm their claims. After verifying the claims to be credible, BleepingComputer contacted LinkedIn for their comments.
Here's the vague reply they received from LinkedIn:
"Posting fake content, misinformation and fraudulent jobs are clear violations of our terms of service. Before jobs are posted, we use automated and manual defenses to detect and address fake accounts or suspected fraud."
However, the shreds of evidence Cyphere's researchers found prove contradictory. LinkedIn didn't do anything further to tackle the issue. That means, the vulnerability still exists and can be exploited by anyone having a LinkedIn account.
How Can This LinkedIn Vulnerability Be Exploited by Hackers?
So, here's the point where the matter takes a dangerous turn.
LinkedIn gives two options to the job posters. They can either receive the CVs via emails or redirect applicants to a third-party website, which ideally should be the company's career page. Hackers can exploit this vulnerability in three ways.
Note: We don't have any information on whether anyone has exploited this vulnerability yet or are there any victims for the same. But it is just a matter of time before hackers learn about this weakness and misuse it in the following ways:
1. Data Theft
Scammers can easily collect applicants' personally identifiable information (PII) such as name, email address, phone number, employment history, and even physical address from the resume. They can sell this data on the darknet, or misuse it for identity theft-related crimes.
2. Phishing Attacks
The con artists pretend to be representatives of a legit company and ask candidates further sensitive information such as bank account numbers to credit the salary, or SSN, and other confidential information for tax purposes. They can also run common employment-related scams such as asking applicants to transfer money for conducting a background check, processing the application, or receiving the training.
3. Malware Delivery
Attackers can send malware-laden files in the email attachments and label them as job description, terms, and conditions, employment contract, interview schedule, etc. They can also redirect candidates to a malicious or spammy site that automatically downloads malware to the victim's device. In the worst-case scenario, hackers can make a cybersquatting site that looks exactly like the original site with a similar domain name, and trick applicants to share their credentials and other confidential documents.
What Can We Do About It?
LinkedIn has 722+ million members in more than 200 countries around the globe, and people extensively use it for finding talents and job opportunities. It is a large pool of targets. By now, you must have an idea that anyone can post a job on behalf of any company and invite applications without the original company's knowledge. This can significantly affect a business's goodwill and create trust issues for potential candidates.
Unfortunately, you can't do anything much about it — the ball is in LinkedIn's court. But if you are a security engineer, threat hunter, pentester, or security consultant, you can take a lesson from here. How a small bug and negligence can expose millions of people to massive phishing attacks. If you have a similar job posting website or even an interactive site where users can generate their own content, you can double-check and confirm whether your own site doesn't have the same vulnerability. Do a thorough software validation, whitelisting along with code sanitization.
Until LinkedIn recognizes the danger and patches the issues, all you can do is to ask your human resource department to keep a keen eye on all the jobs posted in your company's name. If they recognize any job which is not posted by your company, immediately contact LinkedIn support to report a complaint. You can also report the fake job by following the steps mentioned in this guide.
Published at DZone with permission of Medha Mehta. See the original article here.
Opinions expressed by DZone contributors are their own.


Comments