MuleSoft Salesforce Connector: OAuth 2.0 JWT Bearer
Here's how to set up OAuth 2.0 JWT Bearer for simple Mulesoft Salesforce integration.
Join the DZone community and get the full member experience.
Join For FreeIn the first part of the MuleSoft Salesforce Connector blog series, we showed how integration to Salesforce made easy by MuleSoft Salesforce connector. In the process, we learned how to install/setup salesforce connector and created a simple flow which authorizes the connection using basic authentication.
Now we're going to create a salesforce connection with authorization OAuth 2.0 JWT Bearer.
The OAuth 2.0 JWT bearer token flow is similar to a refresh token flow within OAuth. access_token is issued based on prior approval of the application, also the client doesn’t need to have or store consumer_secret, because it uses an uploaded certificate as the signing secret.
First, we need to gather all the required parameters of OAuth 2.0 JWT Bearer Configuration listed below:
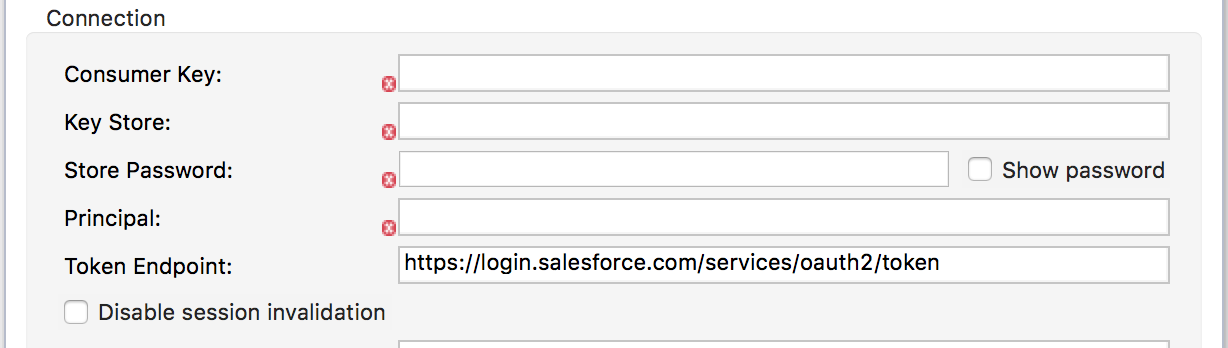
- Add salesforce connected app
- Consumer Key - The consumer key for the Salesforce connected app
- Generate keystore
- Keystore File - The generated keystore file
- Store Password - The Keystore password
- Principal - The Salesforce username account you are using.
Add salesforce connected app
- Login to salesforce using your account
- Click Setup, from the left menu, select Build->Create->Apps find the Connected Apps section and click new.
![Image title]()
- Follow these steps to created a new connected app:
Enter the following information in the appropriate fields:
- A name for the connected app.
- The API name.
- Contact email.
- Under API (Enable OAuth Settings), select Enable OAuth Settings.
- Enter the Callback URL.
- Add the Full access (full) and Perform requests on your behalf at any time (refresh_token, offline_access)OAuth scopes to Selected OAuth Scopes.
- Click Save, and then click Continue.
![Image title]()
- Configure the Authorization settings for the app:
- Click Manage, and then click Edit.
- Under the OAuth Policies section, expand the Permitted Users drop-down, and select All users may self-authorize.
- Click Save.
- Copy the consumer key found in Build->Create->Apps then click the app name.
![Image title]()
Generate Keystore
- Click Setup, from the left menu, select Administer->Security Controls->Certificate and Key Management.
- Input values of Label and Unique Name. Click Save.
- Download the certificate. I suggest you to rename it to salesforce-cert.crt but is not required.
- Go back to the list of certificates, then click Export To Keystore.

- Enter desired keystore password then click export. The keystore will be downloaded to you. I suggest you to rename it to salesforce-keystore.jks but is not required.
- Go back to Setup->Build->Create->Apps find the connected app then click edit.
- Click use digital signature then upload the certificate file (salesforce-cert.crt) you created. Click Save then Continue.
- Copy both the key store (salesforce-keystore.jks) and the public key (salesforce-cert.crt) files in your workspace.
Authorize the connected application
- Run this in your browser or you could use curl, replacing <consumer_key> with the consumer key of your connected app. https://login.salesforce.com/services/oauth2/authorize?client_id=<consumer_key>&redirect_uri=https://www.getpostman.com/oauth2/callback&response_type=code
- Click Allow to grant access, disregard the response as long as the request is successful. You will know if it's successful if the code is provided in the callback URL.
![Image title]()
Create Mule Application
- Create a simple flow same as what we did in Part I.

- Select salesforce configuration with OAuth 2.0 JWT Bearer and fill out the required parameters we gathered in the early steps.

- After successful validation of the configuration, proceed to test the application by invoking the HTTP endpoint using postman or any client you're used to, like soapui or plain browsers.

Now we have successfully integrated MuleSoft and salesforce using OAuth 2.0 JWT Bearer Flow.
Opinions expressed by DZone contributors are their own.





Comments