Okta + SAML + JBoss EAP 6.4.x + Picketlink
How to provide Okta authentication to your web app by using Okta + SAML + JBOSS EAP 6.4.x + Picketlink and JAVA as a backend.
Join the DZone community and get the full member experience.
Join For FreeIn this article, I explain how to provide Okta authentication to your web application hosted on a JBoss EAP 6.4.x server.
In this example, we provide authentication to internal users (who are logged in in the customer network) and external users (from the internet) who may be third-party collaborators such as carriers, partners, etc.
Architecture Diagram

Configure the Okta Account
In our case, the Okta account is managed by our customer. So, we had to provide them with the instructions for the setup.
The most relevant configuration parameters are:
![SAML Settings in OKTA: sso url, recipient url]() Single Sign-On URL
Single Sign-On URL
- This URL has to provide the logic to allow access to the application to all the users who are already logged in (in this example: internal users and external users who have already provided valid credentials before).
- Users who are not logged in to the system should be redirected to the Okta login page. We'll see later in this article how to leverage Picketlink in order to achieve this.
- Recipient URL
- This URL has to manage the SAML response and provide access to the landing page if the authentication with Okta was successful. Otherwise, it has to redirect the flow to the Okta login page.
Additionally, you may need to configure some additional security attributes which will be displayed on your web application, like user first name, last name, address, email, etc.
You do this in the ATTRIBUTE STATEMENTS section:

Picketlink Descriptor Setup (picketlink.xml)
Picketlink is a software library written in Java for abstracting the SAML protocol and allows authentication easily by configuring an xml descriptor and providing Java classes for parsing SAML attributes from the response. Integrate Picketlink into your web app.
Once the Okta account setup is ready, you need to configure the Picketlink descriptor in your web application.
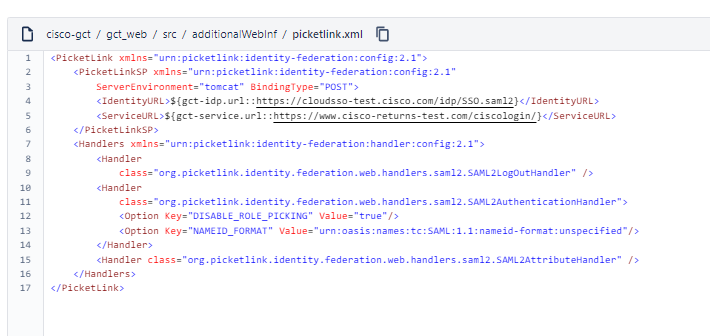 So, it's recommended to create 2 variables: one for the Identity URL and another one for the Service URL. In this example, we have created the variables gct-idp.url for the IdentityURL and gct-service.url for the service URL (we'll see later in this article how to configure your JBoss Server in order to have custom idp and service URLs for different environments like UAT, PRODUCTION, etc.)
So, it's recommended to create 2 variables: one for the Identity URL and another one for the Service URL. In this example, we have created the variables gct-idp.url for the IdentityURL and gct-service.url for the service URL (we'll see later in this article how to configure your JBoss Server in order to have custom idp and service URLs for different environments like UAT, PRODUCTION, etc.)
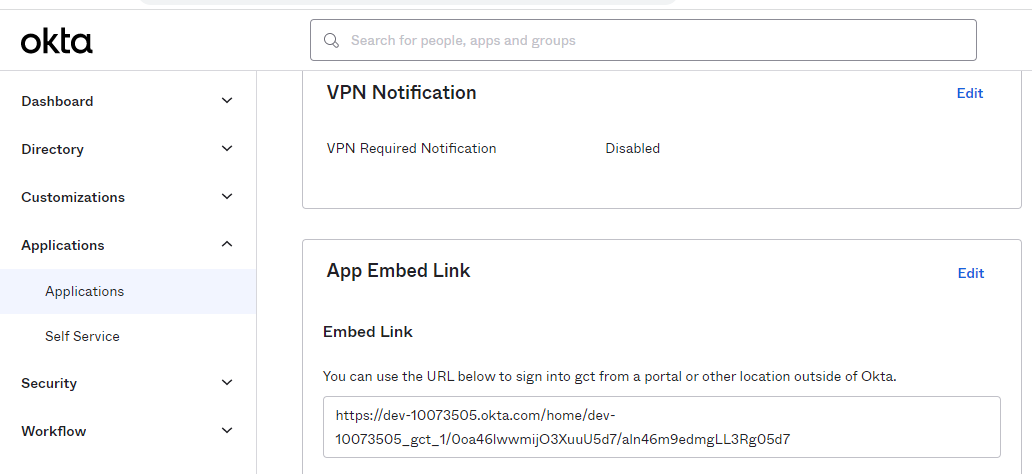
- The identity URL should be the one provided by your Okta account, and it allows the users to sign in (login page). Get it from the Embed Link section:
![OKTA identity url]()
- The service URL should be the endpoint provided by your web application which will handle the SAML response and authorize access to your app resources based on the SAML response attributes and if the SAML authentication was successful.
JBoss Configuration Descriptor (standalone.xml)
In your JBoss configuration descriptor, you need to set up the same variables defined on picketlink.xml. In this case: gct-idp.url and gct-service.url. This allows you to set up different environments for development, testing, and production.
SAML Response Attributes
Picketlink will do this for you. The session will have the attribute SESSION_ATTRIBUTE_MAP with all the SAML security attributes for the user authenticated.
Your Java class behind the Service URL has to retrieve this session attribute and get the value.
Opinions expressed by DZone contributors are their own.

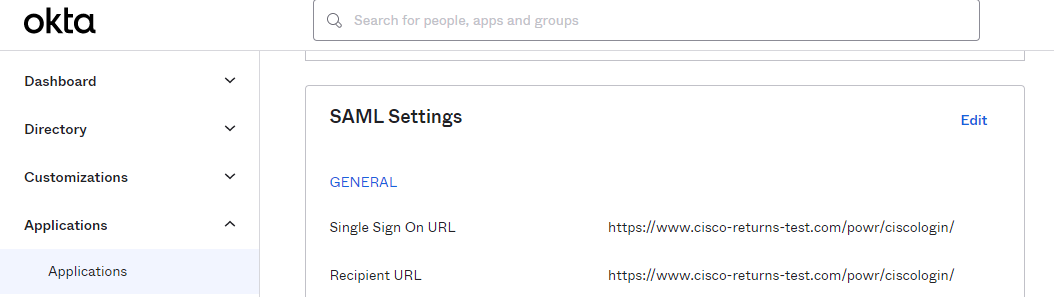 Single Sign-On URL
Single Sign-On URL
Comments