PGP Encryption in Mule 4: How it Works
See how PGP encryption works in Mule 4.
Join the DZone community and get the full member experience.
Join For Free
Overview
The flow of information that runs through the average business every day is like a river. It’s massive and holds the potential for danger if you’re not careful. Scammers easily lift data from your payment systems if you let them and use it to steal your information. When working with clients, it's very common to receive and send sensitive information, such as server names, usernames, passwords, or even clients' internal information. Sharing this information via an email, text, files, or a 'chat' program is very insecure, unless you encrypt the information using a good encryption method.
Pretty Good Privacy (PGP) is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, E-mails, files, directories, and whole disk partitions to increase the security of e-mail communications. It was created by Phil Zimmermann in 1991.
Public and private keys play a vital role in PGP to encrypt and decrypt the data. Generally, a public key is used to encrypt the data, and it is always shared with end-users. The private key is used to decrypt the data.
How PGP Works
PGP encryption works by generating a key pair: a private key and a public key. The public key is the one you give to other people, who then use it to encrypt messages they want to send to you. When you receive a message encrypted with your public key, there is only one way to decrypt it: using your private key.
There's no way to decrypt the message with any other key (private or public) — that's the reason it's called "key pair." And just to be clear, there's no way to infer, guess, or obtain your private key from your public key.
Say you’ve got two keys and one box with a lock. The first key would be the only one you can use to lock the box. The second key would be the only one you can use to unlock it. You also might be interested to learn that PGP encryption can be used to secure text, emails, or files both in transit and at rest, while making them tamper-proof too.
PGP also supports applying digital signatures to messages, so that the receiver can be sure that a specific message came from a specific person.
Generate Public and Private Keys
There are many tools available to generate PGP private and public keys. In this article, we will use Git Bash to generate private and public keys.
Generate a Key
Go to Git Bash > Run > gpg --gen-key
At the prompt, specify the kind of key you want, or press Enter to accept the default RSA.
Enter the desired key size. We recommend a maximum key size of 4,096.
Enter the length of time the key should be valid. Press Enter to specify the default selection, indicating that the key doesn't expire.
Verify that your selections are correct.
Enter your user ID information.
Type a secure passphrase.
Use the
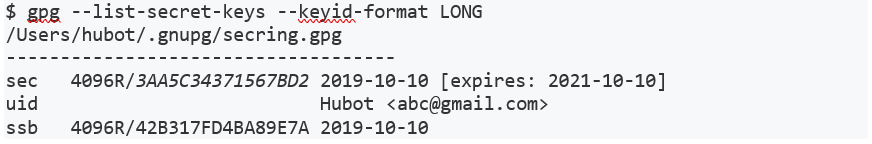
gpg --list-secret-keys --keyid-format LONGcommand to list GPG keys for which you have both a public and private key. A private key is required for signing commits or tags.
8. From the list of GPG keys, copy the GPG key ID you'd like to use. In this example, the GPG key ID is 3AA5C34371567BD2.
Exporting the Public Key
When using PGP encryption, the sender of the message must encrypt its content using the receiver’s public key. To export the public key select binary as the output format. This produces a key ring file.
gpg --output secring.gpg --export abc@gmail.com
Ensure that the key ring (.gpg) file is stored where the Mule app can access it during runtime.
Implementing PGP in Mule 4
Mule ESB provides PGP Security as part of its Enterprise Security. You can download Cryptography module, which provides cryptography capabilities to a Mule application.
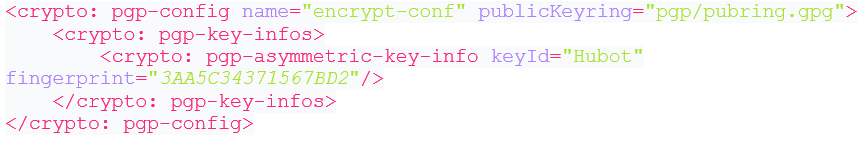
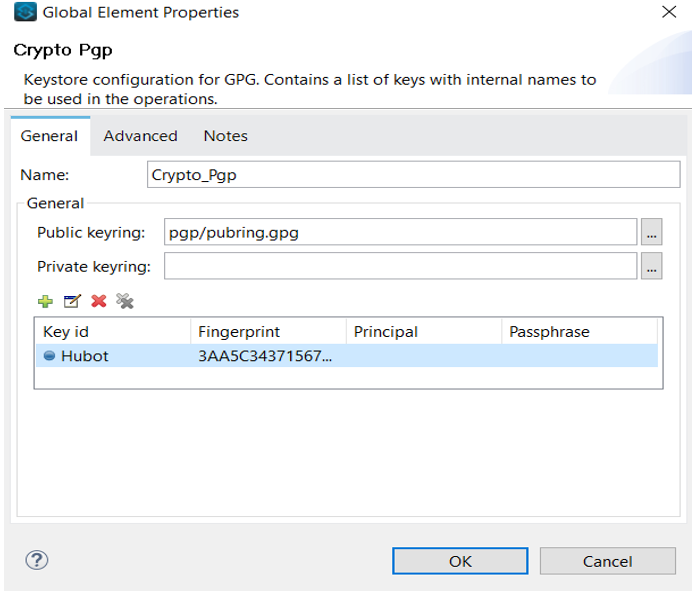
Once the Crypto module is downloaded, you can see various available PGP and JCE operations. Here, we are only looking for encryption operation, so all that's left is to configure the PGE encrypt connector. To do so, first, click on the plus sign to start connector configuration. Under the General tab, specify information for the public Keyring and add the Key ID and fingerprint details.
Example: PGP Configuration
Now, go to the PGP EncryptGeneral tab and specify the Key Id, as defined in the PGP configuration.
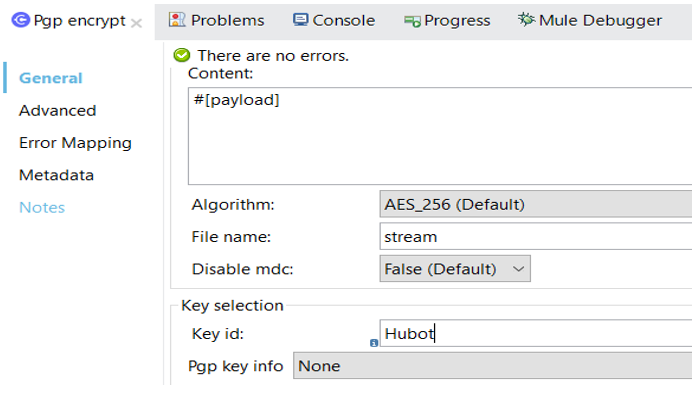
Make sure you have copied the public key in your application folder src/main/resources. Once setup is done, you can deploy and test the application.
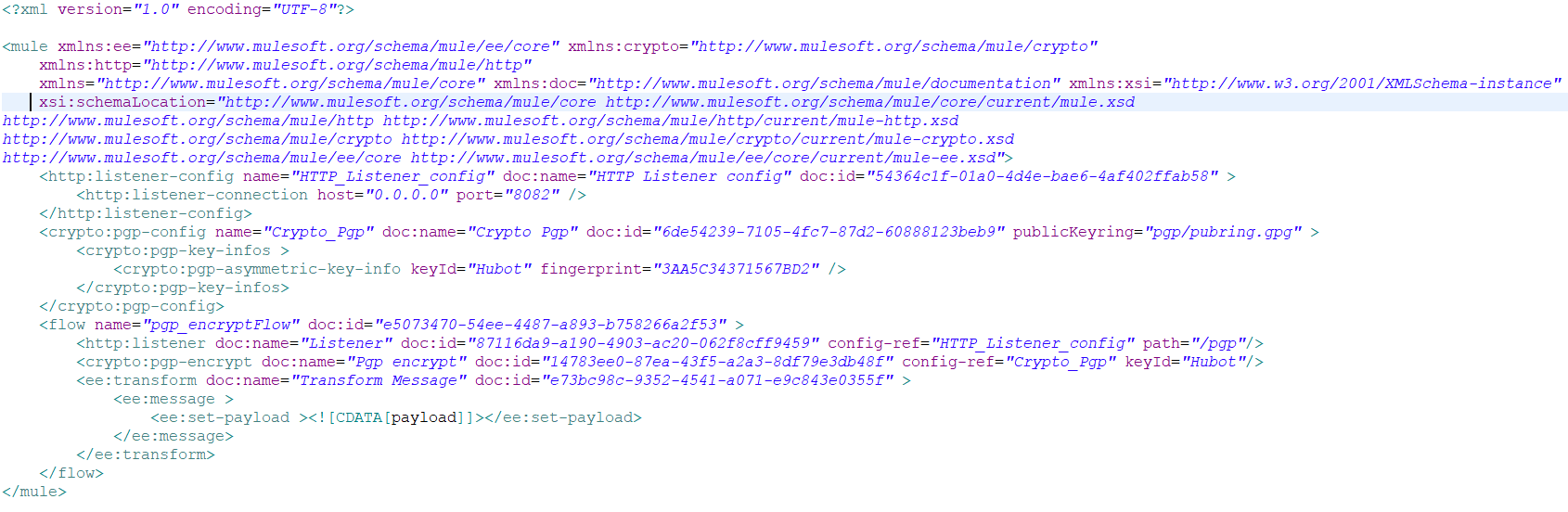
Now, we can test our application
Request:

Response
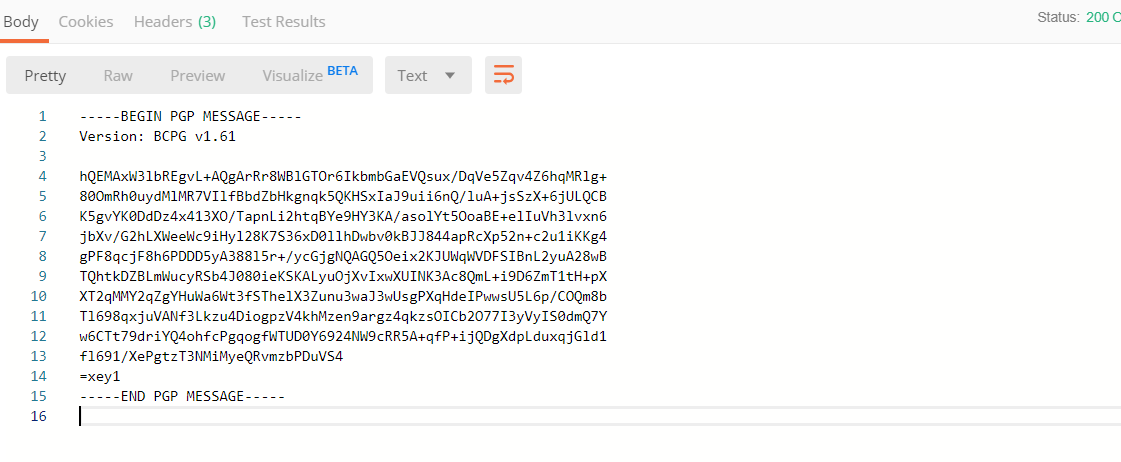
Conclusion
PGP Encryption secures data transmission in emails, documents, and files and only the person with whom you have shared the keys is able to decrypt the data and use it. This protects your data so that it cannot be misused, even if someone has the file. Without keys, no one can decrypt the file and access the data. It can also be used for decrypting and signing messages and files.
Further Reading
Opinions expressed by DZone contributors are their own.

Comments