Property File Handling in Mule 4
Read this article in order to view a tutorial and see how the mechanism to handle property files has been modified in Mule 4.
Join the DZone community and get the full member experience.
Join For FreeIn this article, we are going to see how the mechanism to handle property files has been modified in Mule 4. Through this article I will mainly be covering:
The changes newly introduced, and how to handle these changes
Various mechanisms of hiding appliction properties in Mule 4
What Is Different
- mule-deploy.properties of Mule3 is replaced with mule-artifact.json. Whenever new Mule flow is created, mule-artifact.json will get updated automatically.
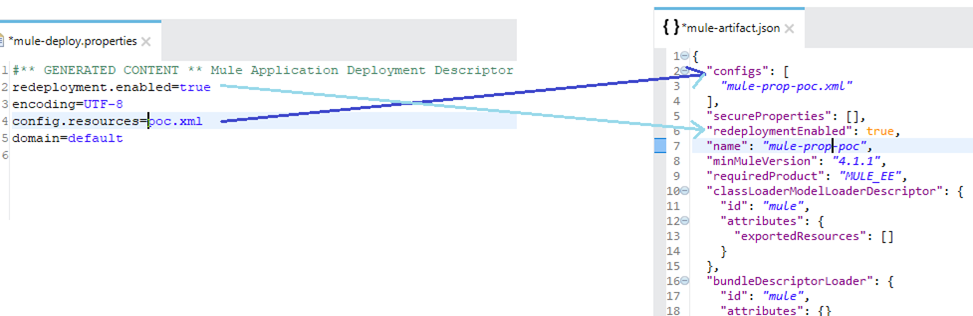
- Newly introduced descriptor to Mule application — mule-artificat.json file. This will manage all application and configuration specific settings, Mule version and configuration for class loader.
- mule-config.properties file of Mule 3 has been replaced with configuration.yaml file.
- Entries of mule-app.properties of Mule 3 has been migrated to Run Configuration -> Argument section in any point. Also these properties can be configured from the runtime manager console under Properties section on cloud hub.
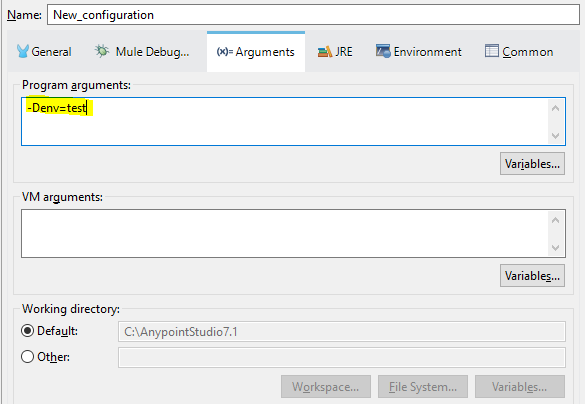 Adding properties Runtime manager console
Adding properties Runtime manager console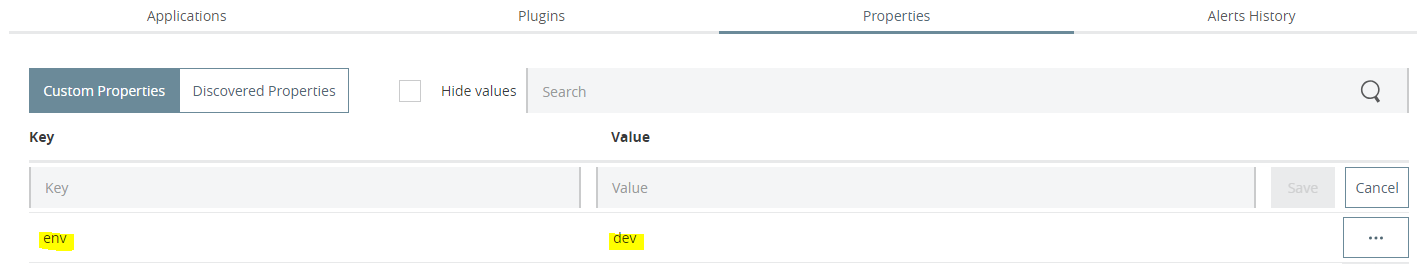
- Now developer will have to maintain only single file to maintain application, deployment and environment specific values that are not advisable to be part of code.
- More robust mechanism for securing configuration properties
- New feature for safely hiding application related properties
How to Configure Properties to Mule 4.X Platform?
- Create a folder with the name config under /src/main/resources project directory.
- Create a configuration file with the name configuration.yaml inside the newly created config folder.
- Below screen will detailed out what and how Mule4 has changed the approach for property placeholders.
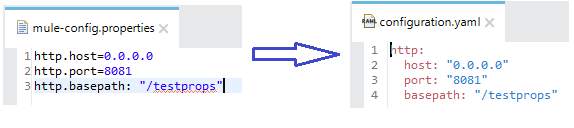 Configuring Mule Flow to Read yaml.
Configuring Mule Flow to Read yaml.
In Mule flow, select ”Global Element,” click on Create button, and select the configuration.yaml file create in step-2.
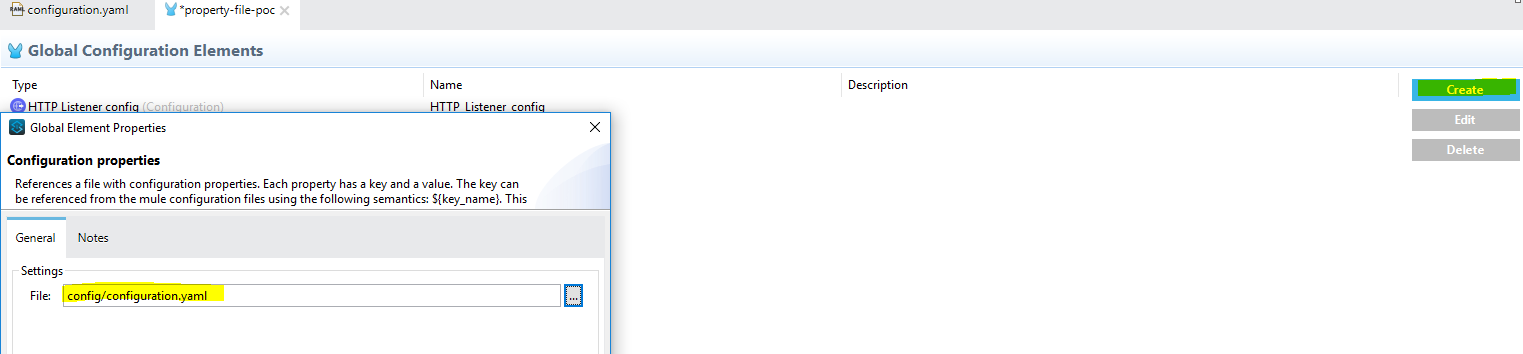 - Configuration XML for Property placed holder should look like..
- Configuration XML for Property placed holder should look like..
<configuration-properties doc:name="Configuration properties" doc:id="84048bfe-e690-4b64-9760-76afeb6c7860" file="config/configuration.yaml" />- Configuration XML for Global HTTP Listener configuration for Mule4 in Studio 7 should look like below
<http:listener-config name="HTTP_Listener_config" doc:name="HTTP Listener config" doc:id="161c3bc6-555e-4842-87ae-596bdd92eed9" >
<http:listener-connection host="${http.host}" port="${http.port}" />
</http:listener-config>- To verify develop a simple flow with HTTP listener which has above entries. Put the logger that prints the values on console.
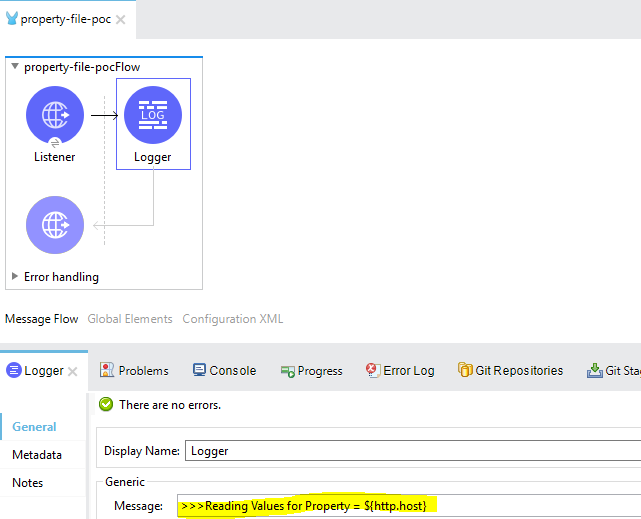
- After running application you will see value of http.host will get picked from yaml file and getting print on the console
org.mule.runtime.core.internal.processor.LoggerMessageProcessor: >>>Reading Values for Property = 0.0.0.0
Hiding Application Properties
- Mule4 has introduced a new provision of hiding the value for property file from Runtime manager. CloudHub supports safely hiding application properties, where name of a property is visible in the console, but the value is not displayed or retrievable by any user.
- Hiddng Appilication Properties through Runtime manager console
- Login into Rumtime manager console
- For deployed application, click on Manage Application and Go to Properties Tab as shown in screen below
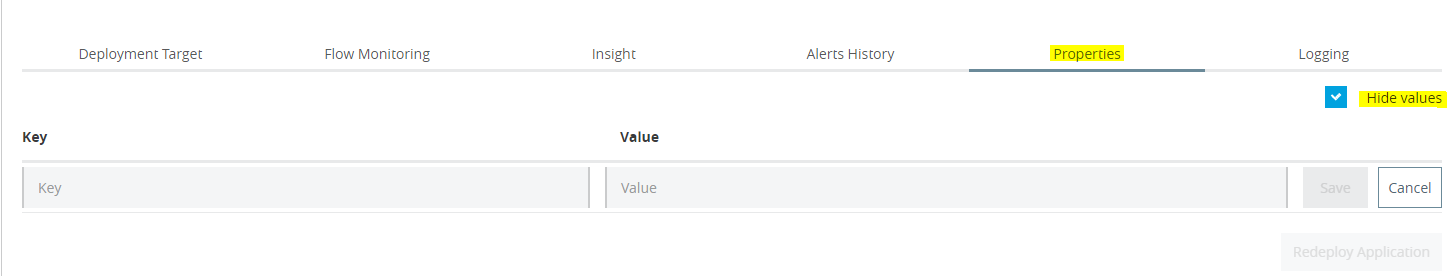
- To hide out the property value, check on Hide values button as highlighted. Enter key and value and click on save.
- For example if Key =loginid and value =myloginid then after clicking on Hide Values, Mule will hide out value defined for Key.
- Before Hiding Values.
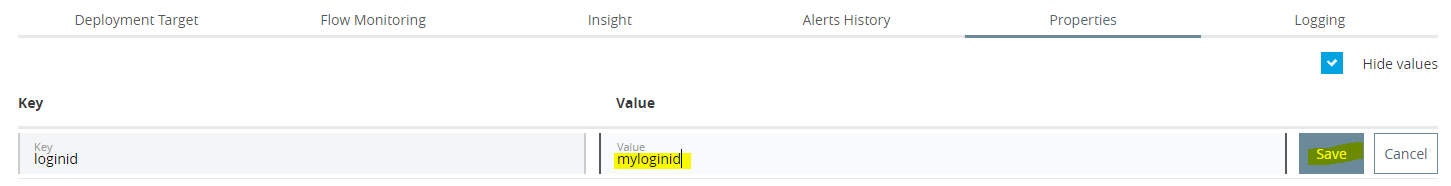
- After Hiding Values.
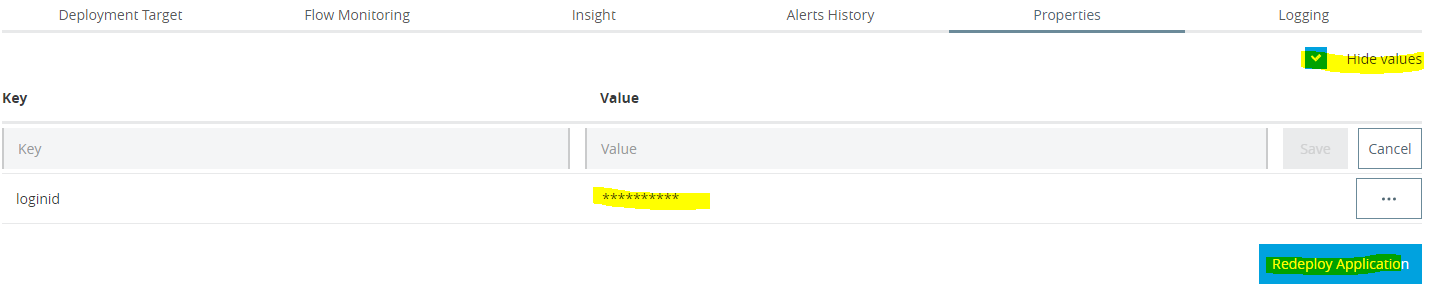
- After adding application from the console, ensure to Redeploy Application.
- Once property values are added as hidden from console, their values are neither visible in the console nor passed between the console and the CloudHub server.
- Hiddng Appilication Properties through Runtime manager console
- Hidding Application Properties through Application configuration
- Safely hidden application properties are a feature that is currently only available for setting via the Runtime Manager UI for applications deployed to CloudHub workers. For applications that you deploy through any other deployment strategy, you need to use secure property placeholder files bundled with your application zip file
- To hide out application properties from within the application configuration
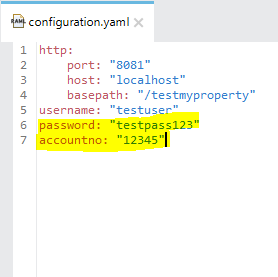
- Identify the property that needs to be hidden when application is deployed onto CloudHub. For an example from configuration.yaml file (shown below), I want to hide password and accountno when my application gets deployed on to the CloudHub.
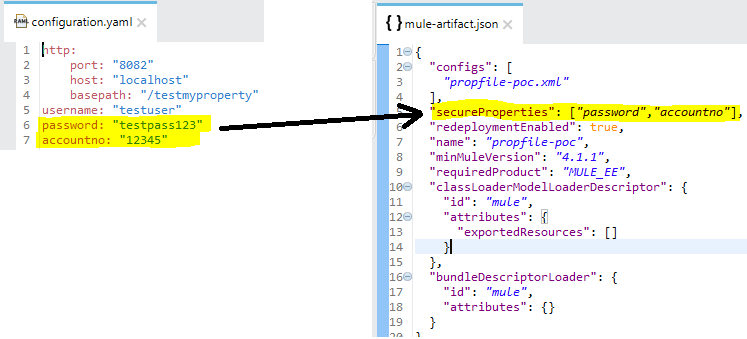
- Identified property names would be listed as comma separated array as value of the secureProperties key inside the Mule application’s mule-artifacto.json file.
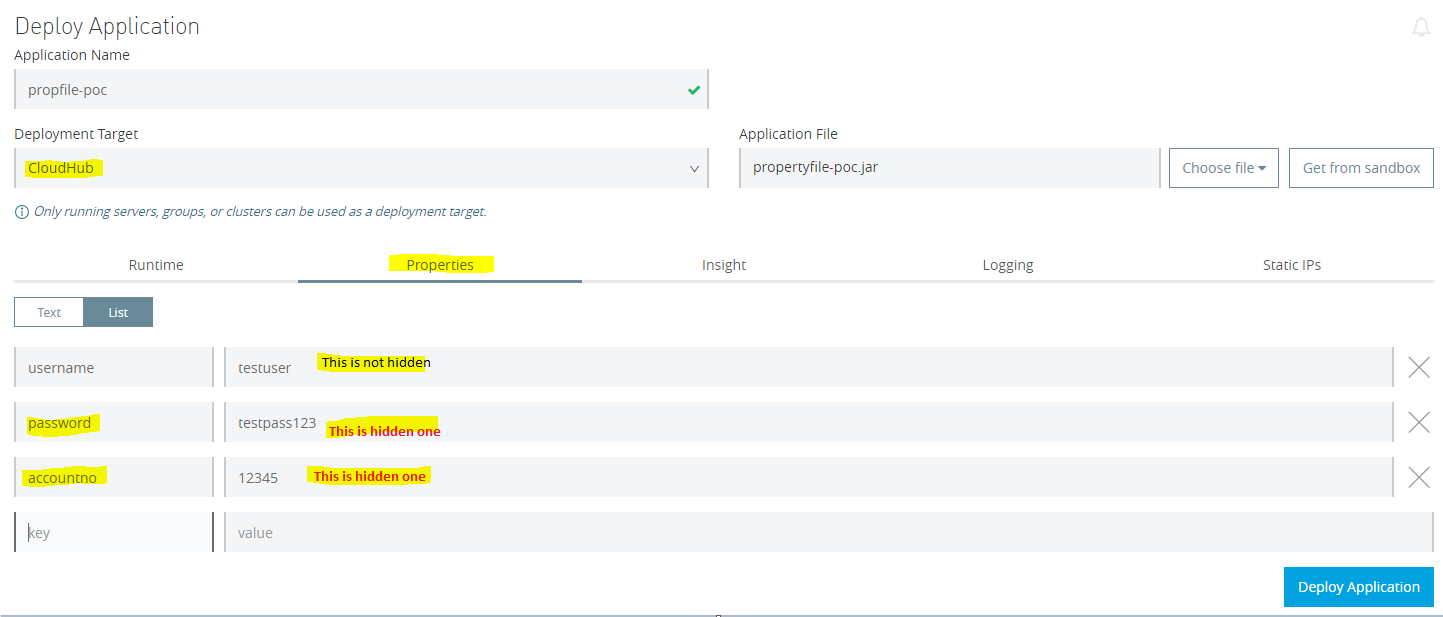
- Deploy application onto CloudHub. While deploying, enter application properties as shown in screen below
- Click on deploy application
- Now remember, since we made two properties viz. password and accountno hidden under mule-artifact.json, these properties should not be visible once application is deployed on the CloudHub.
- Once after application is deployed, go to manage application -> properties. All properties, which were listed under secureProperties array will not get display.
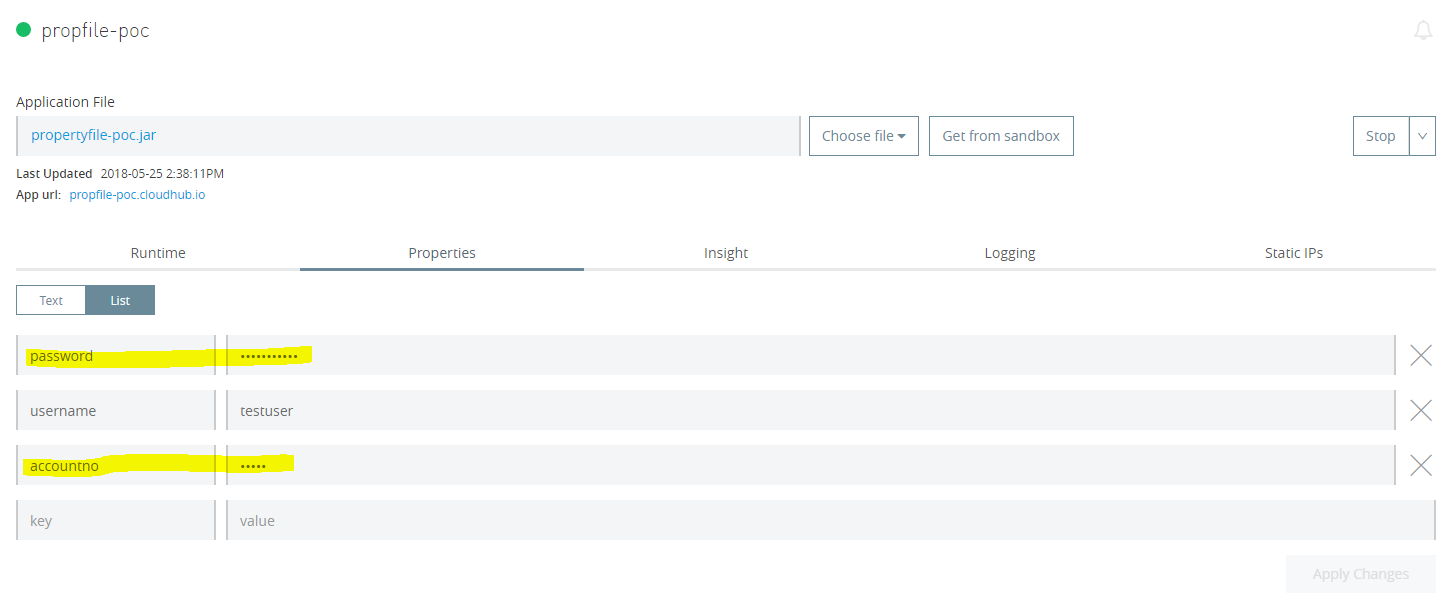
- Identify the property that needs to be hidden when application is deployed onto CloudHub. For an example from configuration.yaml file (shown below), I want to hide password and accountno when my application gets deployed on to the CloudHub.
- It is important to note that
- Once the values are committed and the application is uploaded, the safely hidden properties are never displayed on the console, nor sent and received between the console and the CloudHub server. There is no way to retrieve the property, once set. It can, however, be overwritten with a new value. So, if you need to update a value, type a new value into the field, as shown below.
- Copying Safely Hidden Application Properties between Sandboxes When moving applications between sandboxes, safely hidden application property values will not be copied to the new environment. For all safely hidden application properties, the name of the property will be copied, but the value will be left blank.
Opinions expressed by DZone contributors are their own.

Comments