Safeguard Your Code With GitHub Dependabot and IBM Cloud Toolchain
This blog talks about how one can smartly automate reporting vulnerabilities which in turn can help track these vulnerabilities so your code always stays healthy.
Join the DZone community and get the full member experience.
Join For FreeHave you ever wondered if people can take advantage of vulnerabilities present in your code and exploit it in different ways, like selling or sharing exploits, creating malware that can destroy your functionality, launching targeted attacks, or even engaging in cyber attacks? These mostly happen through known vulnerabilities which are present in the code, which are also known as CVEs, which stand for Common Vulnerabilities and Exposures.
In 2017, a malicious ransomware attack, WannaCry, wrought havoc by infiltrating over 300,000 computers in more than 150 nations. The assailants were able to utilize a flaw in the Microsoft Windows operating system, which had been designated a CVE identifier (CVE-2017–0144), to infect the computers with the ransomware. The ransomware encrypted users’ files and demanded a ransom payment in exchange for the decryption key, causing massive disruptions to businesses, hospitals, and government agencies. The attack’s total cost was estimated to have been in the billions of dollars.
When you have thousands of packages in use for a single functionality, it can be daunting to track every package utilized in your code and determine whether it is vulnerable. How do you ensure that your code is secure and cannot be abused in any way? What if you automatically get notified with a Slack alert — as soon as a new vulnerability is detected — in one of your many Git repositories. What if an issue automatically gets created, which can be used to monitor similar issues daily?
This is where Dependabot enters the picture. Dependabot can be integrated with various development tools and platforms such as GitHub, GitLab, Jenkins, and Travis CI, among others. It also supports a wide range of programming languages, and it can also be used with Docker to examine Docker images for outdated dependencies. As a result, it is a versatile tool for managing dependencies and keeping projects current with the most recent security patches and bug fixes.
To maintain the safety and security of your program dependencies, the use of Dependabot notifications is critical. Dependabot automates the process of scanning your code repositories for vulnerabilities and out-of-date dependencies. Dependabot alerts are notifications sent when a vulnerability is discovered in one of your dependencies. They are meant to keep you informed about any potential security risks that may emerge.
Dependabot Alerts can only be viewed by individuals with admin access to a repository or to users, and teams who are given access explicitly will have permission to view and manage Dependabot or secret scanning alerts. However, most people will not have access to Dependabot alerts for the component or microservice which they are working on. How can a developer learn about CVEs present in the code? How can they remediate vulnerabilities if they are unaware of them? In this scenario, we can use a combination of GitHub API, Webhooks, and Tekton pipelines to our advantage. You can leverage the IBM Cloud toolchain to create an automation that creates issues in the repository where the CVE was identified and can also close the issue once the CVE has been remedied. This way, developers can keep track of the vulnerabilities present in the code and have a clearer idea, which aids them in remaining compliant.

The Pipeline Implementation
GitHub has the ability to send POST requests to a webhook for a different set of events like repository vulnerability alerts (aka Dependabot Alerts) which will be useful for our case. Creating a webhook with this event selected will send POST requests whenever a new vulnerability is detected or remediated. The webhook can act as a pipeline trigger.

Before implementing the pipeline, it is important to understand the payload of the POST request and how it can be utilized. The payload contains an “action” key and an “alert” key. The “action” key indicates whether it is a remediation alert or a creation alert, while the “alert” key contains an array of important details such as the affected package name, range, severity, and suggested fix.
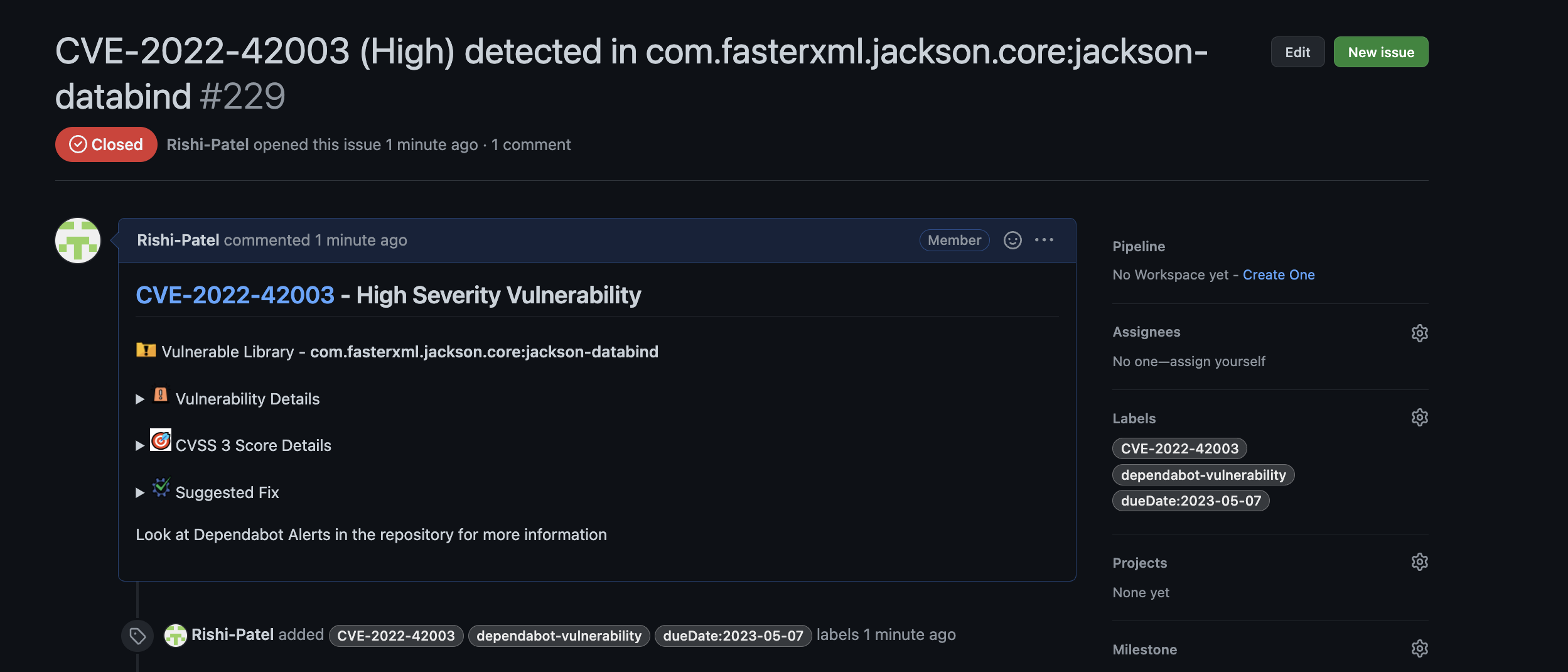
To utilize this information and alert the team, a pipeline can be created with a generic webhook trigger, which will trigger whenever there is a request sent to the webhook. The pipeline can extract the affected package from the payload and check if an issue for the CVE already exists in the repository. If not, it will create an issue with all the required details to identify the CVE and provide a suggested fix, if any. The pipeline can also add IBM-recommended due dates based on the severity.
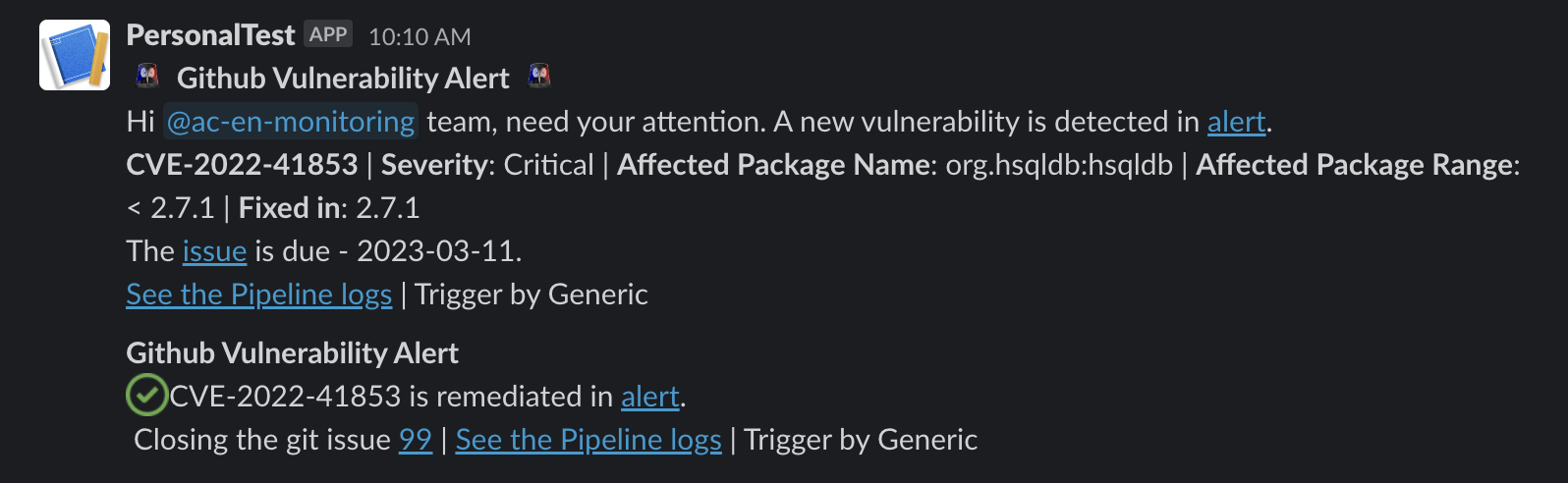
Once the developer works on remediation and the changes are reflected in the default branch, Dependabot will send a request to the webhook with the action being “resolve.” The pipeline can extract the affected package name from the payload and check if the issue is open in the repository. If yes, it will automatically close the issue and add a comment saying, “Vulnerability has been remediated, closing the issue.”
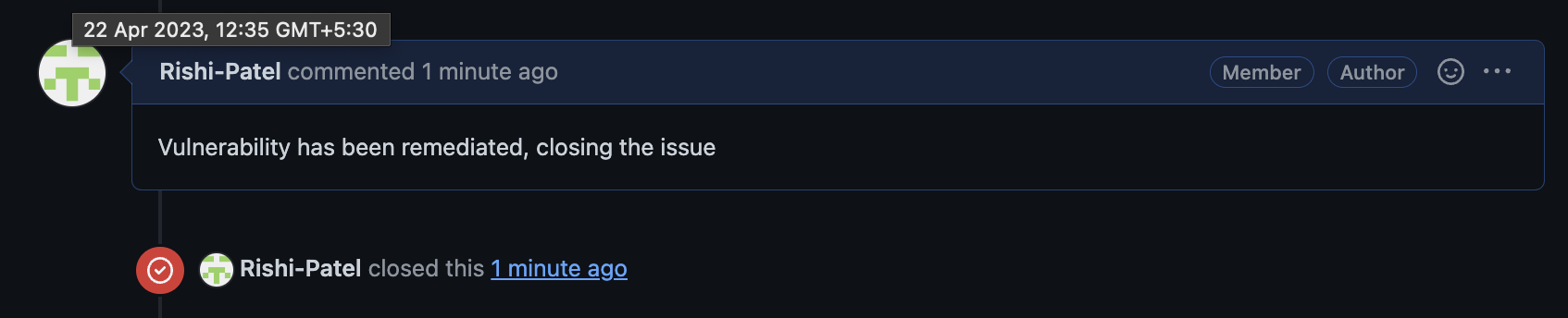
Additionally, the pipeline can be configured to send a Slack alert whenever an issue is created or resolved based on the team’s requirements. This pipeline can work at either the repository level or organization level, tracking all the repositories inside an organization if the webhook is integrated at an organization level.
Overall, implementing this pipeline can help developers stay compliant and ensure safety and security. However, it is important to follow best practices as a team to ensure the effectiveness of the pipeline. Don’t miss out on the next blog post about setting up the automation. Subscribe to my page and receive instant notifications as soon as I publish it, so you can stay ahead of the game and keep your skills sharp!
Opinions expressed by DZone contributors are their own.

Comments