Static Code Analysis for Embedded Development Projects Using C-STAT Tool (IAR-Embedded Workbench)
Identify deviations from code rules using the C-STAT static analysis tool.
Join the DZone community and get the full member experience.
Join For FreeC-STAT is a static analysis tool that is used to identify the deviations from certain coding rules by doing one or a lot of checks for the rule.
The checks are grouped into packages. The various packages are listed below:
STDCHECKS
These checks contain rules that come from CWE (Common Weakness Enumeration), as well as checks specific to C-STAT.
CERT
These checks contain rules that come from CERT (Computer Emergency Response Team). In addition, few CERT rules and suggestions are verified by checks for other standardized rules.
SECURITY
These checks contain rules from SANS Top25, OWASP (Open Web Application Security Project) and CWE.
MISRA C:2004
These are checks for selected rules of the MISRA C:2004 standard (Motor Industry Software Reliability Association), and this standard identifies unsafe code constructs in the C89 standard.
MISRA C++:2008
This will contain checks for selected rules of the MISRA C++:2008 standard, and this standard identifies unsafe code constructs in the 1998 C++ standard.
MISRA C:2012
This will contain checks for selected rules of the MISRA C:2012 standard and this standard identifies unsafe code constructs in both C99 and C89 standards.
Every MISRA C rule is either necessary, required, or informatory. The checks for the necessary and needed rules are, by default, on, whereas the checks for the informatory rules are by default off. Each rule specifies an unsafe code construct.
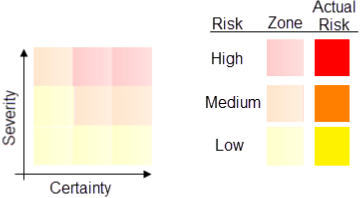
A below grid shows the severity of the problems that code that does not conform to the rule (non-conformant code) can cause and the level of certainty that the message reflects a true error in the source code.
The grid is split into three zones, which are indicated with pale colors, that show the risks based on the severity and certainty. The actual risk for a particular check is indicated with a grid cell in study color.
Getting Started Analyzing Using C-STAT
1. Before you perform static analysis, confirm your project builds successfully without any errors.
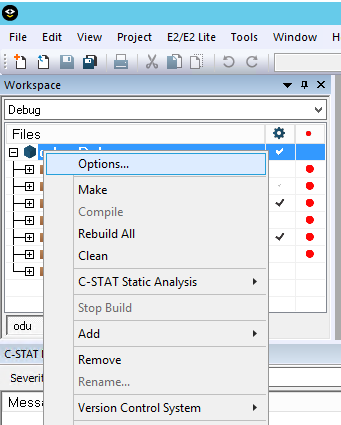
2. Choose the project in IAR, right-click the Project->Options, and select the C-STATStatic Analysis category. On the C-STAT Static Analysis page, click choose C-STAT Checks.
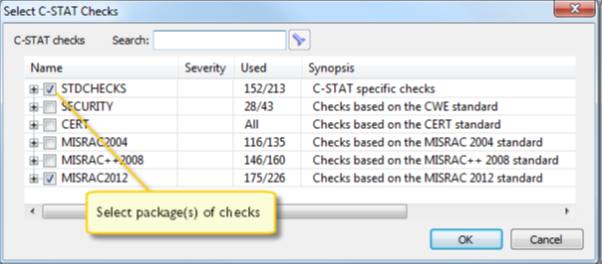
3. Next, in the Select C-STAT Checks dialog window, choose the packages of checks you wish to use.
For example, STDCHECKS.
4. For every package, choose available groups of checks or individual checks:
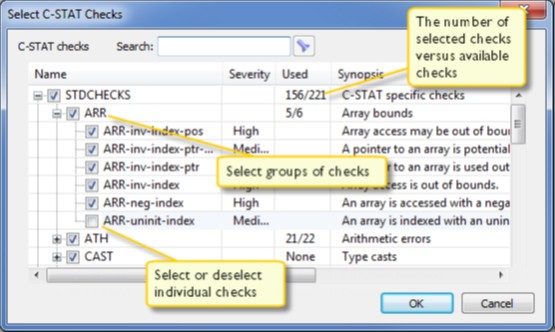
For detailed information about a particular check, select it and press F1 to open the context-sensitive online guide system.
When you have created your settings, click OK.
5. To run the analysis, confirm the project is active and execute one of these below steps:
To analyze your project, choose the project in your Workspace window and click Project>C-STAT Static Analysis>Analyze Project.
To analyze one or more individual files, select the file(s) in the Workspace window and choose Project>C-STAT Static Analysis>Analyze File(s).
Note: The next time you run the analysis and if you have done any changes to your source code since the previous analysis, we should first clean the database file to avoid issues, due to the mixing of old and new data in the database. To do that, Choose Project>C-STAT Static Analysis>Clear Analysis Results.
6. The results of the performed analysis are listed within the C-STAT Messages window.
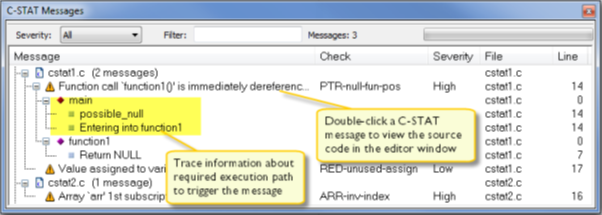
For information about a particular check, select it and press F1 to open the context-sensitive online guide system.
Note: If there are any issues once analyzing, the Build Log window displays detailed information.
7. Double-click a C-STAT message to look at the corresponding source code within the editor window:
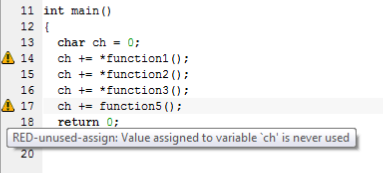
Point at a message with the mouse pointer to induce tooltip info regarding that to determine which check caused the message.
8. Correct the error and click on the successive message within the C-STAT Messages window. Continue until all messages have been processed.
Generating an Analysis Report
Here's what you need to do to generate a report:
Within the IDE, select Project>C-STAT Static Analysis and opt for either Generate HTML outline or Generate Full HTML Report based on which type of report you wish to generate.
This is an example of a summary report:
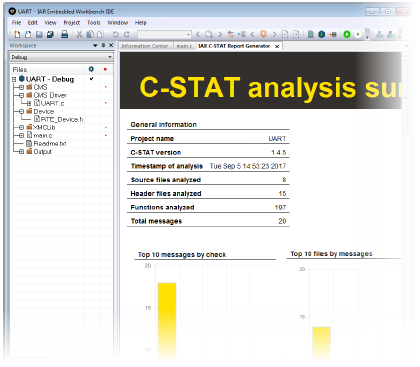
Advantages
- Fully integrated within the IAR-Embedded Workbench and easy to execute on a single file or your whole project
- Easy configuration and possibility to reuse the same setup on other projects.
- Database file of a list of messages available in case of certification
- C-STAT helps to maintain general code quality and portability by enforcing coding standards like MISRA C:2012 and others
Conclusion
In embedded development projects, we definitely need to follow certain coding rules and standard for each industry. C-STAT helps us to analyze each and every line of your code and digs out the deviations and coding standard issues present in it based on the checks we perform.
Opinions expressed by DZone contributors are their own.

Comments