Symmetric JCE Cryptography in Mule 4
In this post, we learn how to encrypt XML using the JCE cryptography module in Mule. Sounds daunting, but MuleSoft has made it simple. Let's get to it!
Join the DZone community and get the full member experience.
Join For FreeHere, we are going to validate changes/enhancements made to the security module in Mule 4.
Let's look at JCE Cryptography.
Below is the information and steps necessary to perform XML encryption and decryption in Mule 4 using the JCE cryptography module.
Step 1: Download the security module's plug-in from the exchange in Anypoint Studio. Once downloaded, we will able to search the security module's components in Anypoint Studio's Pallet.
Step 2: Based on the new release in the security module in Mule 4, encryption/decryption enhanced the secure key bases process, so now we need to generate a keystore file. Below is the command to generate a keystore file (jceks).
keytool.exe -genseckey -alias srccodes -keyalg AES -keystore aesKelltontech.jceks -keysize 128 -storeType JCEKSBelow are a few additional steps to generate a key.
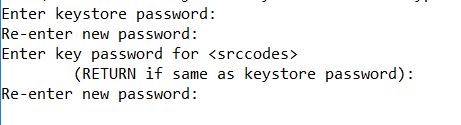
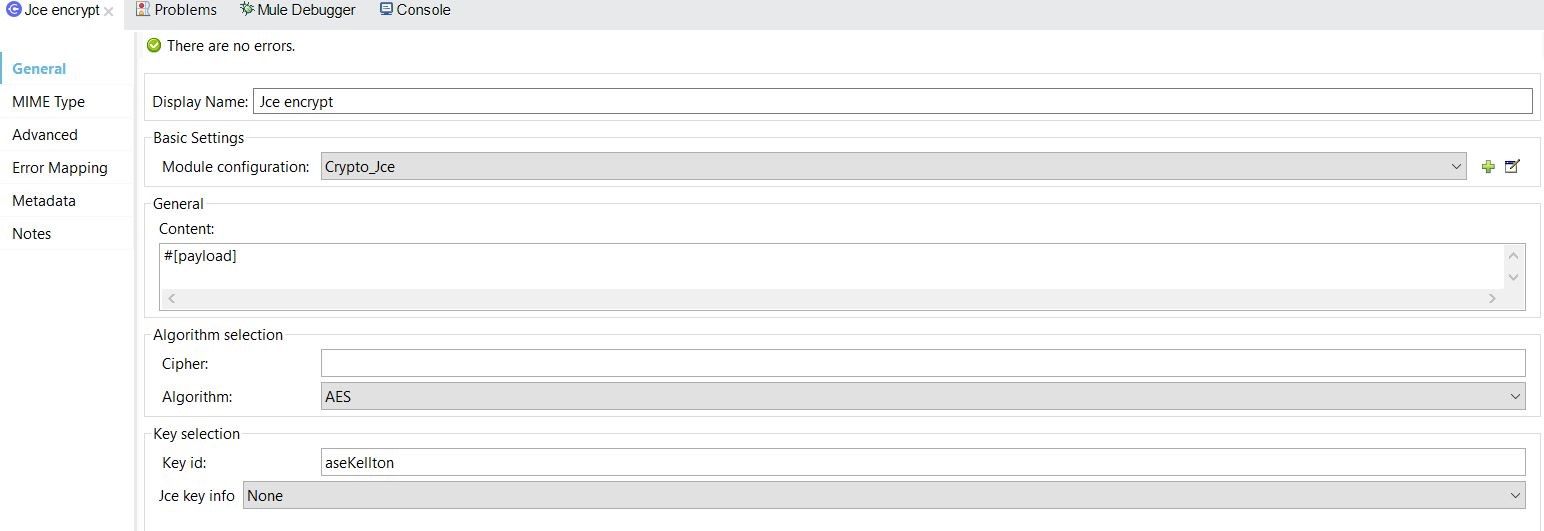
Step 3: Now, let's go to configure the "JCE encrypt" component to encrypt the data in flow with the below steps.
- Module configuration (global configuration): To use global configuration, we need to follow the below steps.
In the keystore file, "askKelltontech.jceks," which we have generated with the alias = 'srccodes' and password = '123456,' we can configure our app's global configuration.
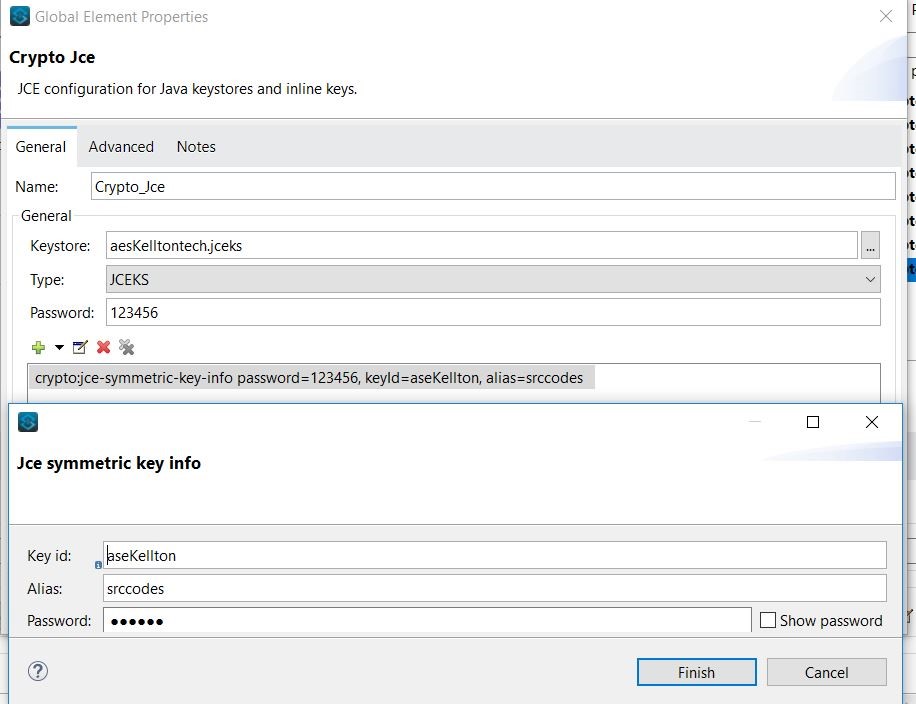
Refer to the global configuration in JCE encrypt component, as shown below.
The above are the steps to configure JCE encryption. The below is the final flow.
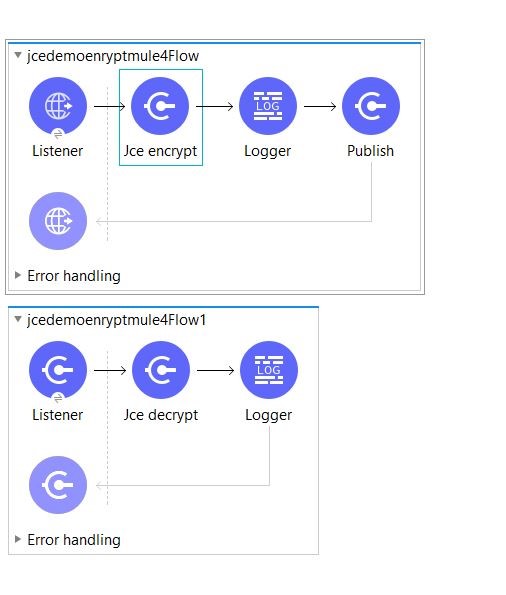
The above is a graphical flow. Below I've given the XML syntax of the flow.
<mule xmlns:vm="http://www.mulesoft.org/schema/mule/vm" xmlns:crypto="http://www.mulesoft.org/schema/mule/crypto" xmlns:http="http://www.mulesoft.org/schema/mule/http" xmlns="http://www.mulesoft.org/schema/mule/core" xmlns:doc="http://www.mulesoft.org/schema/mule/documentation" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.mulesoft.org/schema/mule/core http://www.mulesoft.org/schema/mule/core/current/mule.xsd http://www.mulesoft.org/schema/mule/http http://www.mulesoft.org/schema/mule/http/current/mule-http.xsd http://www.mulesoft.org/schema/mule/crypto http://www.mulesoft.org/schema/mule/crypto/current/mule-crypto.xsd http://www.mulesoft.org/schema/mule/vm http://www.mulesoft.org/schema/mule/vm/current/mule-vm.xsd"> <http:listener-config name="HTTP_Listener_config" doc:name="HTTP Listener config" doc:id="6a1d4faf-8a26-4748-8332-5216f9b9dd60"> <http:listener-connection host="0.0.0.0" port="8081" /> </http:listener-config> <crypto:jce-config name="Crypto_Jce" doc:name="Crypto Jce" doc:id="2f5a799b-bb60-4515-b2c0-c210050e6b59" keystore="aesKelltontech.jceks" password="123456" type="JCEKS"> <crypto:jce-key-infos> <crypto:jce-symmetric-key-info keyId="aseKellton" alias="srccodes" password="123456" /> </crypto:jce-key-infos> </crypto:jce-config> <vm:config name="VM_Config" doc:name="VM Config" doc:id="4ddf74ef-b002-47cd-9968-4d00b32d8186"> <vm:queues> <vm:queue queueName="jceQueue" /> </vm:queues> </vm:config> <flow name="jcedemoenryptmule4Flow" doc:id="643c7feb-0e37-4efa-8b51-f0b34f8b997d"> <http:listener doc:name="Listener" doc:id="027793d6-6012-4ce8-871d-3779fda90590" config-ref="HTTP_Listener_config" path="/postJce" /> <crypto:jce-encrypt doc:name="Jce encrypt" doc:id="6e9502dd-f16c-4895-abfc-3e4ff4af5b70" config-ref="Crypto_Jce" keyId="aseKellton" algorithm="AES" /> <logger level="INFO" doc:name="Logger" doc:id="fac262ce-feb7-40e7-b6d8-74269162b902" message="======================== > This is Main Flow logs : ---#[payload]" /> <vm:publish doc:name="Publish" doc:id="7b8731b8-92ca-4530-b35d-e887825c8af7" config-ref="VM_Config" queueName="jceQueue" /> </flow> <flow name="jcedemoenryptmule4Flow1" doc:id="3f8e2fcf-44c1-404f-8714-cf1dcaf6cb18"> <vm:listener doc:name="Listener" doc:id="fddfa348-54bc-4171-abb6-b66d6fb8db2f" config-ref="VM_Config" queueName="jceQueue" /> <crypto:jce-decrypt doc:name="Jce decrypt" doc:id="95a95020-d540-4f97-b6aa-01a20e6afa9f" config-ref="Crypto_Jce" algorithm="AES" keyId="aseKellton" /> <logger level="INFO" doc:name="Logger" doc:id="d2e77328-ce06-4189-bc64-531af3e5eb49" message="======================== > This is final logs : ---#[payload]" /> </flow></mule>Now start the application. The below logs show that the application configured and deployed successfully.
Mule is up and kicking (every 5000ms) INFO 20180512 09:00:52,330 [WrapperListener_start_runner] org.eclipse.jetty.server.AbstractConnector: Started ServerConnector@238b76c5{HTTP1.1,[http1.1]}{0.0.0.0:50525}INFO 20180512 09:00:52,332 [WrapperListener_start_runner] org.mule.runtime.module.deployment.internal.StartupSummaryDeploymentListener: DOMAIN STATUS default DEPLOYED APPLICATION DOMAIN STATUS jcedemoenryptmule4 default DEPLOYED We're all set to go and test the flow. Below are the steps to follow to run the test.
In the logs, we can find encrypted data and decrypted data as expected.
INFO 20180512 09:04:09,117 [[MuleRuntime].cpuLight.12: [jcedemoenryptmule4].jcedemoenryptmule4Flow.CPU_LITE @3e5b04fe] [event: 0535927c0559511e8b0df34f64bf39778] org.mule.runtime.core.internal.processor.LoggerMessageProcessor: > This is Main Flow logs : V0]oWFLYytk8f$INFO 20180512 09:04:09,184 [[MuleRuntime].cpuLight.12: [jcedemoenryptmule4].jcedemoenryptmule4Flow1.CPU_LITE @6770e5eb] [event: 0535927c0559511e8b0df34f64bf39778] org.mule.runtime.core.internal.processor.LoggerMessageProcessor: > This is final logs : {"name" : "Sadik Ali"}Happy MuleSoft!
Opinions expressed by DZone contributors are their own.

Comments