Terraform State File: Key Challenges and Solutions
Let's deep dive into the role of Terraform state files, their challenges like sensitive data and corruption, and effective solutions for secure infrastructure management.
Join the DZone community and get the full member experience.
Join For FreeIntroduction of Terraform State File
The Terraform state file serves as a crucial bridge between the declarative configuration in the Terraform code and the resources deployed in the infrastructure. It maintains a detailed record of all the resources managed by Terraform, including their attributes, dependencies, and metadata. This information enables Terraform to perform intelligent operations such as incremental updates and resource tracking across multiple executions.
When Terraform runs, it compares the desired state defined in the configuration files to the current state recorded in the state file. This comparison allows Terraform to determine which changes must be applied to align the infrastructure with the desired configuration.
The state file also plays a vital role in Terraform's ability to handle complex scenarios, such as managing resources with dependencies or dealing with resources that may have been modified outside Terraform. By storing sensitive information, such as resource IDs and connection strings, the state file facilitates Terraform's ability to manage these resources effectively over time, making it an indispensable component in maintaining infrastructure consistency and enabling seamless collaboration among team members working on the same infrastructure.
A Few Key Points About the Terraform State File
- By default, Terraform saves its state in a file called
terraform.tfstatein the same folder where you're working. - A recommendation for larger teams or production use is that instead of keeping the state file on a local computer, it's better to store it in a remote location.
- Here are some examples of remote storage options:
- Amazon S3 bucket
- Azure Blob Storage
- Terraform Cloud
Benefits of Remote Storage
- It enables team collaboration.
- It prevents potential issues that could arise from local storage.
Using the remote storage approach helps teams work together more effectively and reduces the risk of problems when managing infrastructure with Terraform.
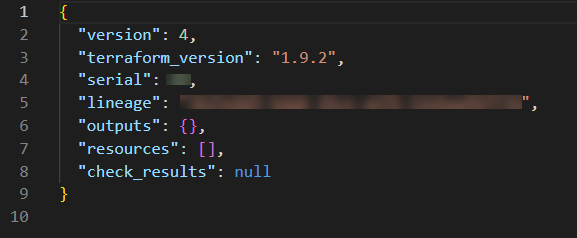
The Terraform state file looks like the following:
Tracking Infrastructure
Let's see how Terraform tracks its infrastructure.
Ever wondered why Terraform keeps track of resources this way? The state file keeps track of resources managed by Terraform and their current settings. It helps Terraform understand what already exists and what needs to be changed.
When you plan changes, Terraform compares the current state (from the file) with the desired state (from your configuration). When making changes, Terraform uses the state file to update the actual infrastructure, and then updates the file itself.
Please note that the state file is crucial for Terraform to work correctly and must be kept current. Making changes to the infrastructure outside of Terraform (e.g., manually) can cause problems because the state file won't reflect these changes.
Below is a sample of how the terraform.tfstate file content looks like.
Let's see a few challenges and possible solutions with terraform.tfstate file.
Problem 1: Sensitive Information Exposure
Sensitive information, like passwords and API keys, are frequently found in state files. It can pose a risk if the file is stored locally or shared incorrectly. It is crucial to secure the state file to prevent access and protect infrastructure information.
Solution
Consider employing a remote backend (e.g., AWS S3, Terraform Cloud) that supports encryption at rest and in transit as well. Additionally, secured vaults and other secret management solutions can also handle sensitive data more securely.
Problem 2: State File Corruption
The state file is meant to be managed by Terraform, and any manual changes to this file can cause potential issues and corrupt the state file, which can lead to inconsistent infrastructure states. A corrupt state file can further lead to errors during terraform plan and terraform apply commands, resulting in inconsistent deployments.
Solution
Avoid manual editing of state files. Use Terraform's built-in commands, such as terraform state, to manipulate state files safely. Taking regular backups of the state file and using remote backends will reduce the risk of file corruption.
The terraform import and terraform replace commands can be used to resolve some of the state file issues. The Terraform replace option, along with terraform apply, will force Terraform to replace an object. This approach is safer for infrastructure management because it reflects the change in the terraform plan. It is recommended to use terraform replace instead of using terraform taint by considering operational difficulties. Also, terraform taint is deprecated for the versions v0.15.2 and above.
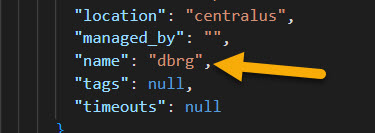
For example, the below state file has information on the creation of a Resource Group in Azure. I'm updating the name of the resource group in the state file for dbrg to dbrg1.
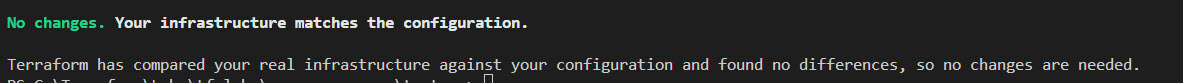
Now, I applied terraform plan. This shows that the infrastructure matches the configuration after the state file is compared with the existing configuration.
Now, let's do terraform apply and see what it says.
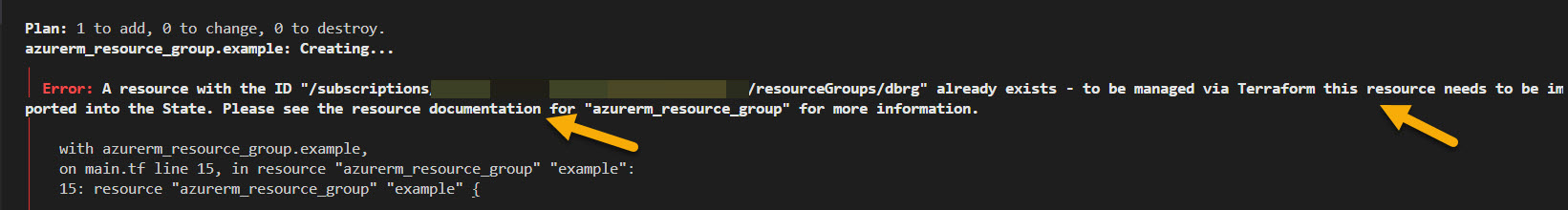
I used the below command to fix the issue:
terraform import azurerm_resource_group.example /subscriptions/<Subscription ID>/resourceGroups/dbrg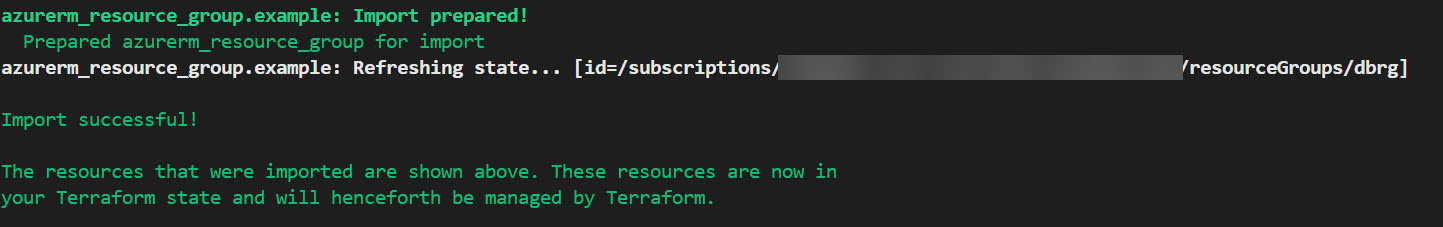
Problem 3: State Locking Issue
When working in a collaborative environment, state file locking ensures that only one user or process modifies the state at a time. However, issues can arise when the lock isn’t released or when Terraform crashes before releasing the lock. This can cause Terraform to become stuck in a locked state, preventing other users from applying changes.
Solution
If you are saving the state file remotely, check if the file is truly locked. From remote backends like Terraform Cloud, you can manually unlock the file. If using AWS S3 with DynamoDB, you can manually delete the lock entry from the DynamoDB table. From Azure blob storage, you can delete the lock container or object if required. After releasing the lock, re-run the terraform plan and terraform apply commands to access the state file and resume its operations.
Conclusion
A vital component of Terraform's infrastructure management is the state file, which monitors resources and helps properly maintain synchronization across them. Despite its significant usefulness, it typically has challenges, such as the elevated risk of revealing sensitive information, corrupted files, and issues with locks.
Efficiently storing the state file remotely, utilizing appropriate commands for management, and ensuring its security through encryption and adequate backups can help tremendously in preventing these complex issues. Ensuring correct state file management is key to maintaining smooth and reliable infrastructure operations with Terraform.
Opinions expressed by DZone contributors are their own.

Comments