Understanding the Chained Microservice Design Pattern
Understanding the chained microservice design pattern, its key characteristics, advantages and disadvantages, problem context, and solution.
Join the DZone community and get the full member experience.
Join For FreeThe chained microservice design pattern is a common architectural approach that results in a single, consolidated response to a client request. Though it is widely used, many developers may employ it without fully realizing its implications.
In this pattern, the request from the client is first handled by Service A, which then communicates with Service B, and subsequently, Service B may interact with Service C. Typically, this pattern relies on synchronous HTTP request-response communication between the services.
Key Characteristics of the Chained Microservice Pattern
One of the critical aspects of this design is that the client remains blocked until the entire chain of requests and responses is completed. This means that the process flows in a series of synchronous steps:
- Service A requests information from Service B.
- Service B, in turn, requests information from Service C.
- Once Service C responds, the data is passed back through Service B, and ultimately to Service A, which sends the final response back to the client.
It’s important to note that the request from Service B to Service C may be structured quite differently from the request from Service A to Service B. Similarly, the response formats can vary across each service in the chain, with the data flowing back in a format that may differ at each stage.
The diagram below illustrates a simple example of how the chained microservice pattern operates:
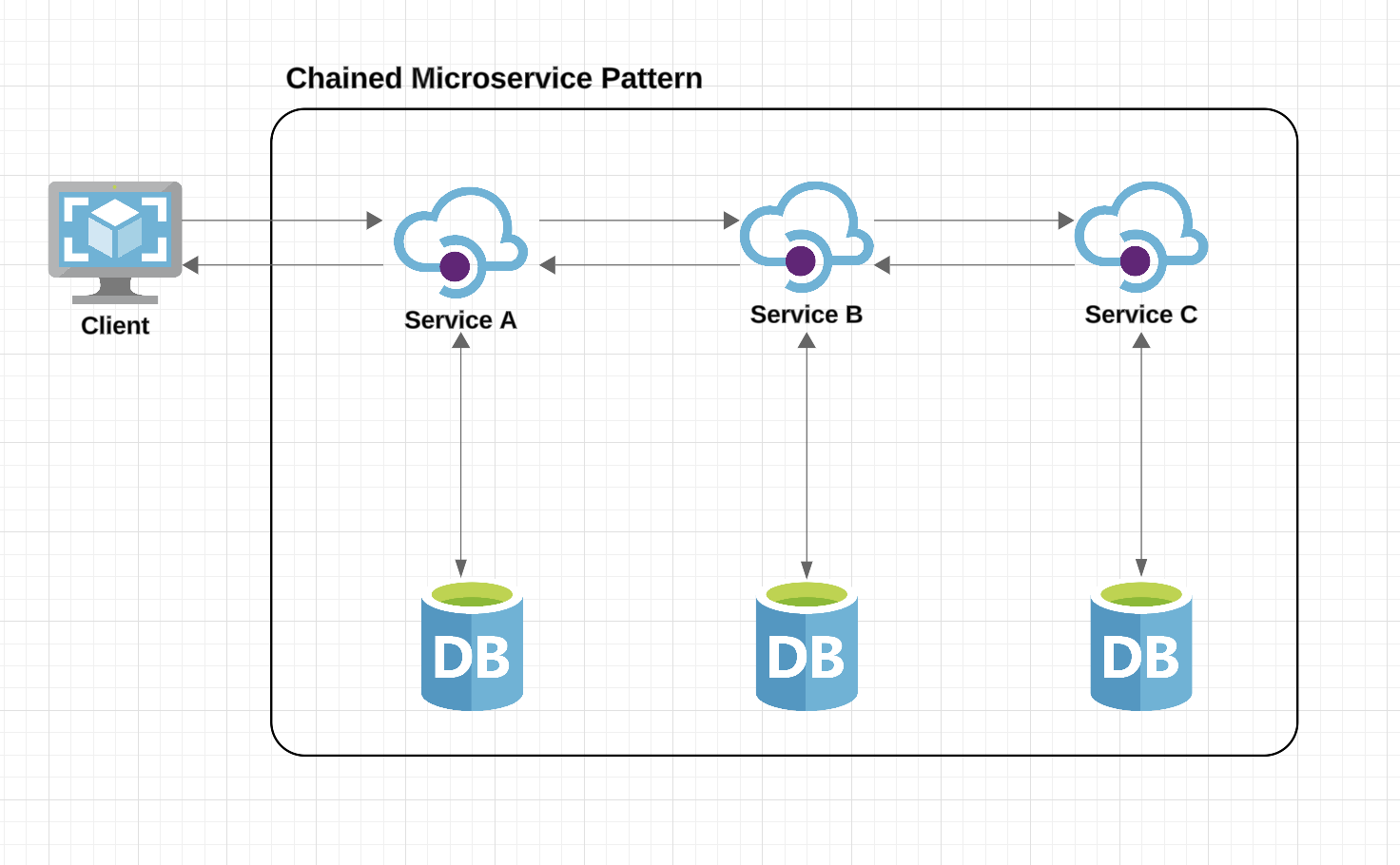
The Chained Microservice Design Pattern: Characteristics, Advantages, and Disadvantages
The chained microservice design pattern is a widely used architectural approach where a client request is passed through a series of microservices to generate a consolidated response. Each microservice in the chain performs its part of the business logic before passing the data to the next service. Below, we’ll explore the key characteristics, advantages, and disadvantages of this pattern.
Characteristics of the Chained Microservice Pattern
1. Single Entry Point
The system typically has a single entry point, which serves as the starting point for the client request. All other services depend on this entry point to begin the chain of communication.
2. Service Dependency
Each service in the chain calls the next service to perform a task. The services are linked in a sequential order, as shown in the diagram below, with each service passing data to the next.
3. Chain Length
Due to the synchronous nature of the pattern, it is crucial that the chain is not too long. A long chain can introduce delays and block the client for extended periods.
4. Singleton Chain
A chain consisting of a single microservice is often referred to as a singleton chain. This can be expanded in the future by adding more services, depending on the system’s needs.
Advantages of the Chained Microservice Pattern
1. Enhanced Security
With only one entry point into the system, security can be more easily managed. For example, a highly secure service can be placed at the end of the chain, reducing its exposure and accessibility.
2. Clear Business Logic Implementation
This pattern allows for a practical, step-by-step implementation of business logic. Each microservice handles a specific part of the process, making the overall business flow easier to follow and manage.
3. Increased Business Dynamism
The chained approach adds flexibility and dynamism, allowing each service to perform specialized tasks while interacting with others to achieve a broader goal.
4. Independent Scalability
Each service in the chain can be scaled independently based on its workload, providing better performance and resource utilization.
5. Encapsulation
The pattern encapsulates access to each microservice, simplifying the internal interactions and improving the modularity of the system.
Disadvantages of the Chained Microservice Pattern
1. Client Blocking
Since each service waits for a response from the previous one, the client remains blocked until the entire process is completed. To mitigate this, it is highly recommended to keep the chain as short as possible.
2. Single Point of Failure
If one service in the chain fails, the entire chain fails, which can cause disruptions in the system. Ensuring proper error handling and service redundancy is crucial.
3. Slower Processing
Because each request passes through multiple services, processing times can increase, especially when the chain becomes longer.
4. Potential Latency
The more services in the chain, the higher the likelihood of introducing latency points. This can impact overall system performance, particularly in real-time applications.
5. Complexity in Data Ownership
Tracking and understanding data ownership can become challenging when data is passed through multiple services, especially if the services operate on different formats or systems.
6. Debugging Complexity
Debugging can become more difficult as the request moves through various services, making it harder to pinpoint issues in the chain.
Problem and Context: When to Use the Chained Microservice Pattern
Imagine you are building an application with a set of microservices that need to contribute data to a final response by executing business logic within each individual service. Each service in the chain must wait for a response from the previous service before continuing. This means that after a client sends a request, it expects a response from the first service in the chain, and each subsequent service must wait for the previous one to complete before proceeding. The chained microservice pattern is ideal for such scenarios, where the tasks must be completed sequentially, and each service contributes a piece to the final output.
Solution: Real-World Example of the Chained Microservice Pattern
Let’s consider an example where you are building a payment processing system for a bank. One unavoidable process in such systems is reconciliation — a critical task that happens every day to ensure that the bank’s records match the merchant's records.
The reconciliation process generally involves several steps:
- Retrieve documents from the bank and the merchant.
- Compare the documents with database records.
- Handle any discrepancies that arise.
Each of these steps must be performed in sequence: retrieving the documents, verifying them, and then addressing any issues. In this case, a chained microservice pattern is ideal, as it ensures that each task is completed step by step before moving on to the next.
The following diagram illustrates this process:
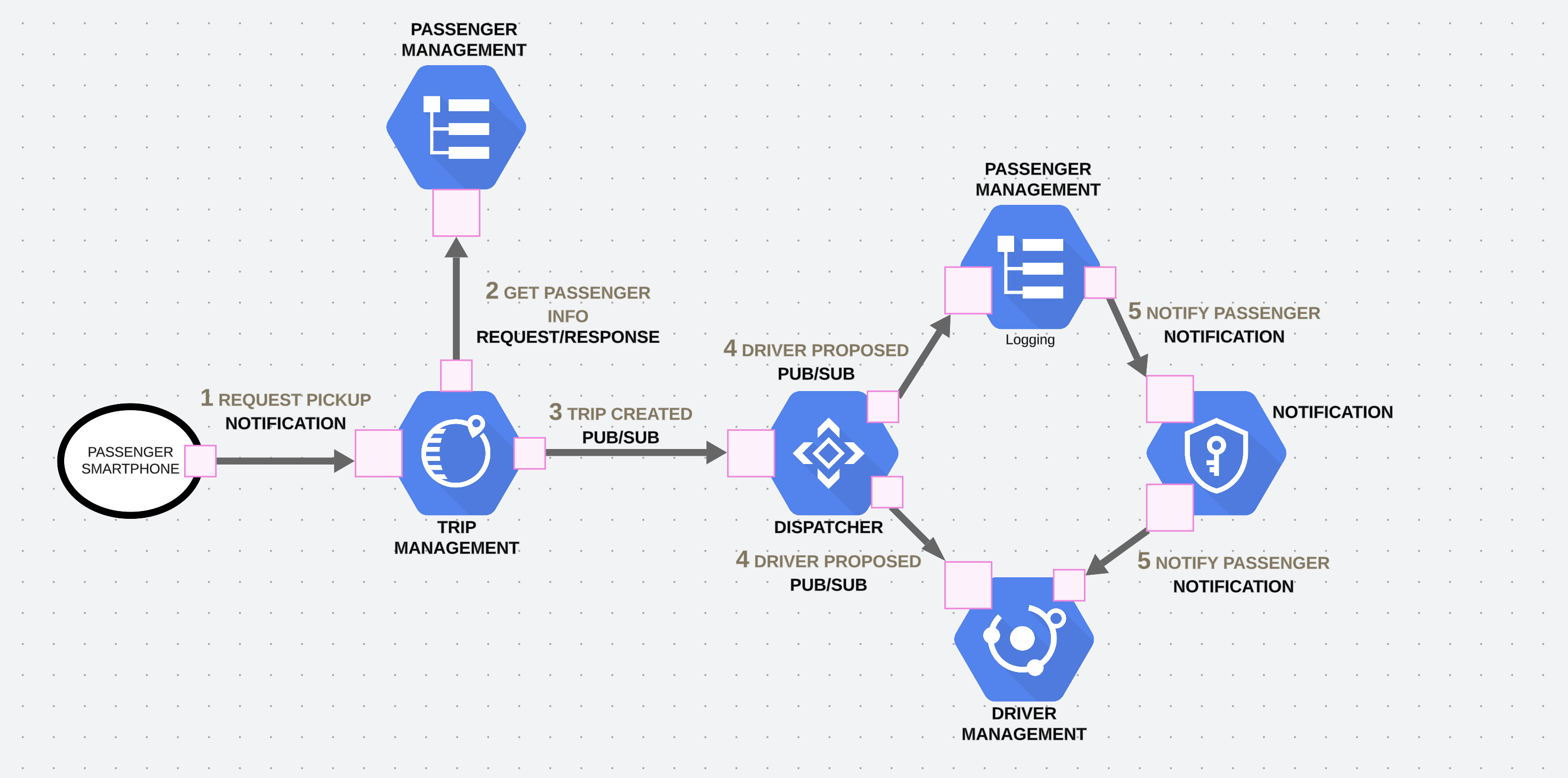
Tips for Implementing the Chained Microservice Pattern
The chained microservice design pattern is relatively simple to implement, especially when using familiar tools like the HTTP protocol. However, while the pattern can be effective for orchestrating a sequence of services, it can become complex and difficult to maintain over time. The primary challenge arises from the potential issues caused by direct communication between microservices, which can lead to problems that are difficult to resolve as the system scales.
When dealing with complex communication patterns, such as the chained microservice pattern, it's essential to have proper monitoring and logging in place to identify anomalies and diagnose problems. This is where the use of consistent and centralized logs becomes critical. However, achieving this in distributed systems can be difficult, as logs may be scattered across multiple services, making it challenging to trace the flow of requests.
Best Practices for Monitoring and Debugging
To effectively trace and debug the communication flow between multiple microservices, one useful approach is to implement a correlation ID. A correlation ID provides a unique identifier for each request or transaction as it flows through various services, allowing you to follow the path of that request across different parts of the system.
A simple way to implement a correlation ID is by generating a UUID (Universally Unique Identifier) and sending it in the HTTP request header. Each service that handles the request can then log this UUID, allowing you to trace the request as it passes through the system. By associating logs with the same correlation ID, you can easily identify where errors occur and follow the request's journey across services.
Real-World Example: Money Withdrawal at ATMs
To illustrate how the chained microservice pattern works in practice, let’s consider a hypothetical example of an ATM withdrawal.
In this scenario:
- Service A: The customer inserts their card into the ATM.
- Service B: The ATM interacts with the bank’s server to authenticate the user and check account details.
- Service N: The bank’s server may call additional services for tasks like balance verification, transaction validation, and fraud checks.
Based on the combined results from these microservices, the ATM determines whether to approve or decline the transaction. Each step in this process relies on successful communication between the services in the chain. If any one service fails or returns an unexpected result, the entire chain can break, preventing the transaction from being completed.
Conclusion
This simple ATM withdrawal example highlights how the chained microservice pattern works in a real-world setting, with multiple services handling discrete parts of the transaction process. By using correlation IDs and structured logging, developers can ensure that they can trace and debug each step in the process, even when the services are spread across a distributed system.
Published at DZone with permission of Sharad Jain. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments