Now, let's take a look at some key core practices of identity and access management.
Credential and Identity Hygiene
As a fundamental block of a cybersecurity strategy, credential and identity hygiene plays a pivotal role in identity security:
- Prevents dormant and orphaned accounts, users, identities, roles, permissions, and groups
- Addresses vulnerable identities, weak passwords, identity sprawl, and permission creep
- Guarantees that access is aligned with each identity's changing roles and responsibilities, minimizing the potential for overprovisioning and unauthorized access
Lacking a well-designed credential and identity hygiene policy can dramatically increase the attack surface for unauthorized access, so it's critical for security teams to regularly perform a comprehensive audit of existing identities, access privileges, and credentials.
Legacy Authentication Protocols
Legacy authentication protocols have inherent weaknesses that attackers can exploit by employing tactics — such as brute-force attacks, password spraying, and man-in-the-middle attacks — in order to gain unauthorized access. Examples of such legacy and insecure authentication protocols include NTLM, basic authentication (username and password), and any IAM solution that uses insecure cipher suites and algorithms, or lacks support for MFA and interactive sign-ins. It is highly recommended to disable all legacy authentication protocols, enable security defaults, and apply conditional access policies, as described next.
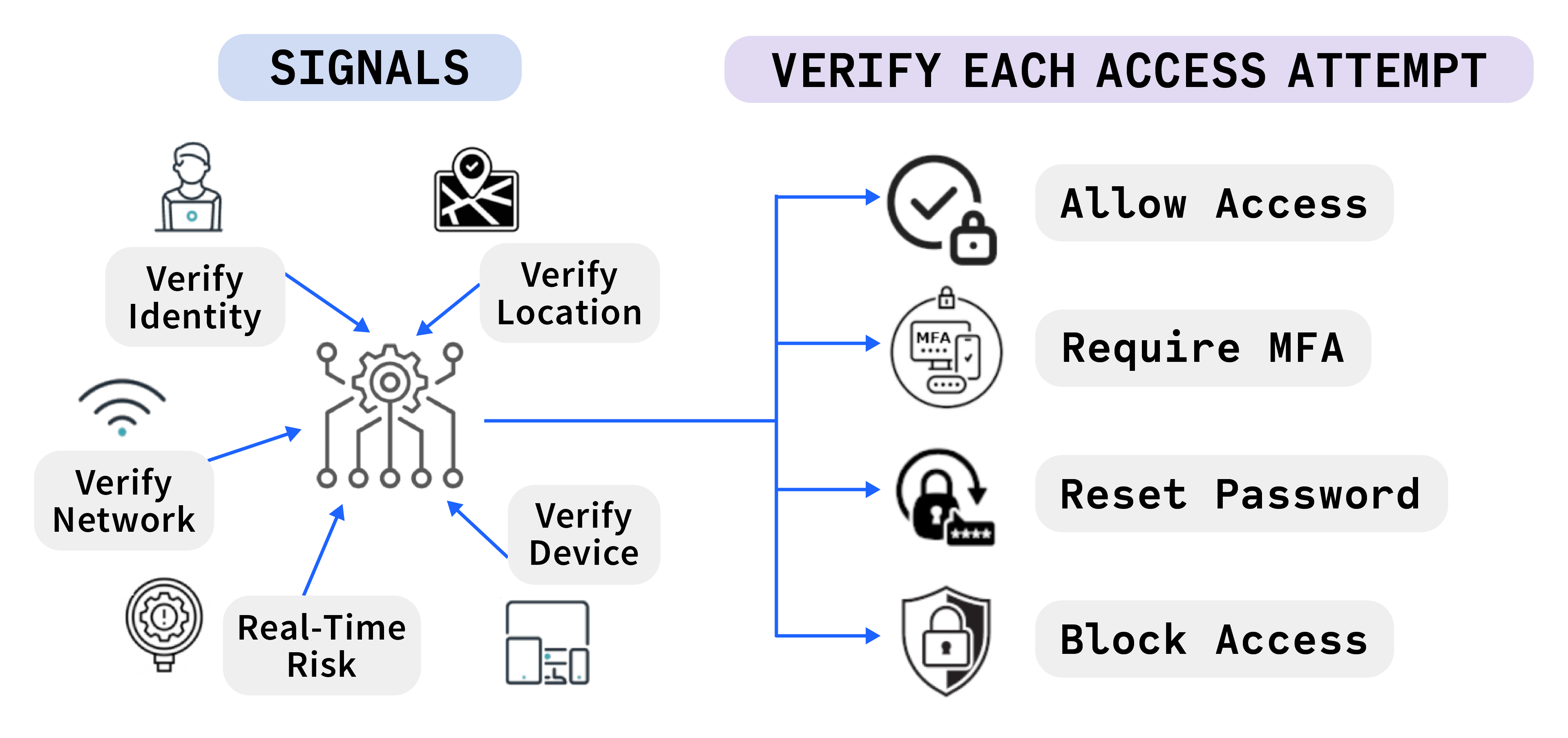
Conditional Access
Conditional access extends an organization's first-factor authentication by combining real-time identity signals in order to grant or deny access based on predefined conditions. By implementing conditional access, organizations can enforce context-aware access controls, taking into account factors such as user location, device health, roles, risky sign-in behaviors, resources accessed, etc.
Conditional access helps organizations align their IAM strategy with the guiding principles of zero trust by allowing them to define access policies according to the business' risk levels, needs, and compliance requirements, ensuring that the right users access the right resources under the appropriate circumstances.
Figure 2: How conditional access works
Just-in-Time Access
Just-in-time (JIT) access is another critical cybersecurity process that aligns with the zero-trust security model. JIT provides users, applications, or systems privileged access to a resource only for a limited period of time and on an as-needed basis. This way, JIT:
- Reduces the attack surface by minimizing the number of standing credentials and privileges
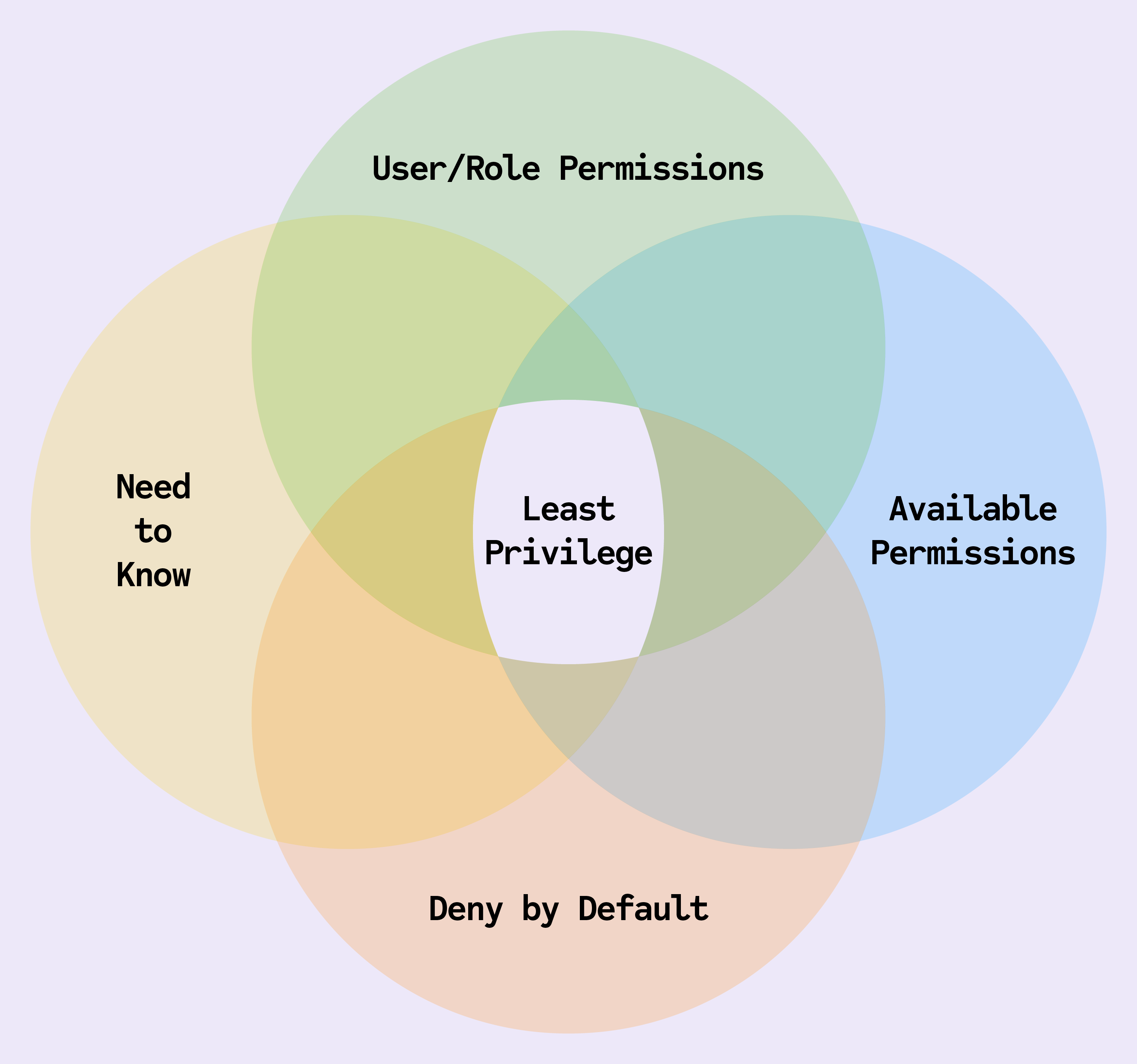
- Enforces the principle of least privilege by granting only the minimal level of access required for a specific task
- Improves the auditability and accountability of access requests and actions by logging and monitoring them
Using JIT, the need for standing (long-term) credentials is removed; thus, the risk of credential theft or misuse is significantly reduced.
Multi-Factor Authentication
Multi-factor authentication is a simple best practice that adds extra forms (factors) of authentication on top of the first form of authentication, which is typically the combination of a username and password. When enabled, MFA requires at least one of three types of additional information:
- Something you know, such as a password, a PIN, or an answer to a security question. This is typically the first factor of authentication.
- Something you have, such as a one-time token generated by a smartphone app or a hardware token.
- Something you are, such as biometric data like fingerprint scans or facial recognition.
MFA can be enabled to verify the MFA token during the sign-in process; before privileged actions, including password changes or financial transactions; or as a response to any unusual user activity.
Passwordless Authentication
Traditional authentication using passwords is susceptible to several security issues, including brute forcing, dictionary attacks, credential stuffing, and credential theft through phishing attacks and data breaches. Even if eight-character passwords use combinations of letters, numbers, and symbols, they can be cracked in less than 60 minutes. Password managers can also be compromised, exposing credential and personal details to malicious actors, as was the case of the recent LastPass security incident that allowed unauthorized access to cloud backups.
Passwordless authentication is the future of authentication, and all tech giants recently announced that they would support FIDO2 to enable passwordless authentication across devices. By eliminating the reliance on passwords and adopting advanced methods like biometrics, hardware tokens, or push notifications on mobile apps, passwordless authentication establishes a more secure user authentication process.
Role-Based Access Control
Role-based access control (RBAC) is an authorization strategy that organizes privileges according to specific roles, providing access rights and permissions associated with those roles. RBAC allows permissions to be grouped for collective assignment and revocation. Altering role permissions can quickly modify permissions for a group of users rather than tens or hundreds of individual users, simplifying administration efforts.
Every RBAC implementation requires careful planning by the IAM engineering team, which should define the roles and perform periodic reviews to validate assigned permissions, helping maintain the least privilege and avoid separation of duties conflicts.
Below is pseudocode illustrating a basic implementation of an RBAC authorization check:
Single Sign-on
Single sign-on (SSO) is an important feature that enhances IAM security by simplifying user access to multiple applications with a single set of credentials without having to log in to each app separately. Once a user authenticates using SSO, a digitally signed certificate or token is generated, serving as a security key for accessing other apps. This approach allows administrators to centrally control IAM requirements like credential hygiene and MFA, significantly reducing the chances of weak passwords or password reuse. SSO also streamlines user provisioning and deprovisioning and enhances the overall user log-in experience as it eliminates the problem of credential entry fatigue.
Privileged Identity and Access Management
Privileged access management (PAM) and privileged identity management (PIM) are integral to IAM. Even though they share similarities, they offer complementary roles in organizational security:
- PIM centralizes the management of privileged identities, ensuring time-bound access to sensitive resources enforced through granular role-based authorization. It encompasses privileged account discovery, centralized provisioning, strong password policies, temporary privileges, monitoring, and auditing, ensuring strict security and efficient control over elevated access.
- PAM broadens its scope with detection and access controls for privileged identities, encompassing privileged identity discovery, baseline establishment, policy-based privilege adjustments, and real-time monitoring for privilege misuse and policy changes.
The terms PIM and PAM are oftentimes used interchangeably due to overlapping functionalities offered by various vendors.
Customer Identity and Access Management
While identity and access management focuses on internal users like employees and contractors, customer identity and access management (CIAM) platforms are designed to manage external user identities, such as customers, partners, and suppliers. More specifically, CIAM's main use cases are business-to-business (B2B), business-to-consumer (B2C), business-to-business-to-consumer (B2B2C), business-to-business-to-employee (B2B2E), and machine-to-machine (M2M) authentication and authorization.
CIAM is often regarded to be at the forefront of digital transformation. Modern CIAM platforms are built upon five fundamental pillars: personalized customer experience, frictionless developer experience, security and future-proof authentication, privacy and compliance, and scalability and high availability.
Personalized Customer Experience
Customer experience is a top concern in CIAM. CIAM platforms streamline user onboarding and registration processes, offering features like self-service account management, SSO, and social login options. Social login is a critical component of the customer experience in CIAM that enables customers to use their existing digital identities, also known as bring your own identity, such as those from Facebook, Microsoft, and Google. Another important component of the overall customer experience is the full customization and personalization of the user interfaces, the login pages, the user journeys, emails, and the authentication workflows. This ensures alignment with each customer’s branding across all devices (mobile, tablet, desktop).
Frictionless Developer Experience
To facilitate seamless integration, CIAM platforms provide tools such as quick-start application wizards, software development kits (SDKs), and low-code interfaces that simplify complex workflows. This developer-friendly approach enables efficient incorporation of authentication and user management features into applications without requiring deep identity management expertise. Additionally, CIAM platforms provide a set of APIs enabling seamless integration with various enterprise applications and services and providing a unified view of customer data across the organization. Using off-the-shelf integrations, developers can seamlessly embed identity management into content management systems, marketing automation tools, customer relationship management platforms, enterprise resource planning systems, and business analytics.
Security and Future-Proof Authentication
Customer identity and data security is of critical importance in CIAM. Modern CIAM solutions prioritize robust security controls, including MFA, adaptive access control, passwordless authentication, rate limiting, password compliance, breach detection, fraud detection, and identity verification and proofing. Single-tenant architectures further enhance security by isolating customer data, thereby minimizing the risk of cross-tenant data breaches.
Privacy and Compliance
CIAM manages customer identity data, protection of which is heavily regulated, and adherence to global privacy regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), is a critical aspect of CIAM platforms. CIAM platforms incorporate consent management services that empower users with granular control over how their personal data is processed and shared, ensuring compliance and user trust.
Scalability and High Availability
Modern CIAM platforms are designed to handle millions of users, ensuring high availability and low latency for seamless login experiences, even during peak traffic times. To achieve this, they employ distributed architectures that eliminate single points of failure, ensuring redundancy and disaster recovery capabilities. CIAM solutions should offer transparent total cost of ownership with clear and predictable pricing models that scale with user needs, avoiding hidden fees and restrictive licensing.
Data Perimeters
A data perimeter consists of preventive measures that ensure trusted identities, such as IAM roles and users, access resources from expected networks. These guardrails establish a protective boundary across accounts and resources, and enhance security by enforcing security standards, preventing unauthorized access and improving data loss prevention strategies. Data perimeters establish controls through resource-based, identity-based, and network access policies. They ensure IAM users, roles, and resources adhere to defined security standards, reducing the risks of privilege escalation and insider attacks. Additionally, data perimeters prevent external sharing of resources, mitigating data loss risks effectively.
IAM Configuration Verification
In large environments with a large number of users, roles, permissions, microservices, cloud services, and APIs, IAM configurations can become very complex and prone to human errors. As the number of IAM objects and their scopes grow, the risk of misconfigurations also rises. Automated checks enforce IAM best practices using policy as code and static IAM configuration scans at build time. Cloud providers also offer native tools for enhanced permissions management, generating fine-grained policies and verifying permissions while identifying and removing unused access permissions for more secure IAM configurations.
Centralized and Decentralized Identity Management
Centralized identity management enables access to multiple applications with the same credentials by storing user identity data in a single, central identity store. This strategy enhances user convenience, simplifies administration, improves security monitoring, and streamlines access (often with SSO), reducing friction and fatigue. However, centralized identity management can introduce a single point of failure and poses risks if the identity store is compromised.
In contrast, decentralized identity management distributes access across various environments. Users store identity data in a digital wallet on their devices, using unique public and private keys to share only necessary transaction information. Decentralized models emphasize unidirectional trust relationships, ensuring user data control and privacy through advanced cryptographic techniques like self-sovereign identity and verifiable credentials.