AWS VPC Sharing Model for Multiple Accounts
VPC sharing with multiple accounts is a simple way to design multi-account networking and avoid a complex hub-and-spoke model.
Join the DZone community and get the full member experience.
Join For FreeAs more organizations adopt cloud computing, managing multiple AWS accounts and virtual private clouds (VPCs) can become complex and challenging. When it comes to managing network resources in AWS, there are two main approaches: using a dedicated VPC or a shared VPC. Each approach has its own pros and cons, and choosing the right approach depends on your specific use case and requirements.
AWS VPC sharing is one approach that allows you to share VPC resources across multiple AWS accounts, simplifying network management and reducing costs. In this blog post, we'll explore VPC sharing, its benefits, use cases, and the shared VPC model.
What Is a Multi-Account Strategy?
A multi-account strategy is an approach to managing AWS resources using multiple AWS accounts, each with a specific purpose or function. A multi-account strategy can help you achieve several goals, such as:
- Improved security: By using separate AWS accounts for different workloads or departments, you can reduce the risk of unauthorized access and data breaches. You can also enforce security policies and compliance requirements more easily.
- Increased efficiency: By using separate AWS accounts for different environments, such as development, testing, and production, you can improve resource utilization and reduce costs. You can also manage resources more efficiently by centralizing administration and monitoring.
- Simplified billing: By using separate AWS accounts for different business units or customers, you can simplify billing and cost allocation. You can also use AWS Organizations to manage billing and payment methods across multiple AWS accounts.
Why VPC Sharing?
VPC sharing is a feature that allows you to share VPC resources, such as subnets, route tables, and security groups, with other AWS accounts. With VPC sharing, you can centralize your network resources and manage them more efficiently. You can also control access to your VPC resources and enforce security policies across multiple AWS accounts.
VPC sharing enables customers to share subnets with other AWS accounts within the same AWS Organization. This concept has many benefits, including:
- Separation of duties, as the VPC structure, routing, and IP address allocation can be centrally controlled.
- Application owners can still own their resources, accounts, and security groups.
- VPC-sharing participants can reference each other's security group IDs.
- Efficiency gains through higher subnet density and better use of VPNs and AWS Direct Connect.
- Simplified network architecture can help avoid hard limits, such as the 50 VIFs per AWS Direct Connect connection limit.
- Cost optimization through the reuse of NAT gateways, Transit gateway, Network Firewalls, VPC interface endpoints, and intra-Availability Zone traffic.
- VPC sharing allows for the decoupling of accounts and networks, enabling customers to have fewer, larger, centrally managed VPCs while maintaining highly interconnected applications.
Shared VPC Model
There are many ways to design shared VPC subnet configuration. When designing your shared VPC, there are several factors to consider, such as how to align subnets with VPC participants. It is common for individuals to create a dedicated set of subnets for each VPC participant, with one subnet for each Availability Zone in a three-AZ AWS Region.
This approach minimizes the impact of any issues that arise since each participant has their own set of subnets, reducing the risk of exhausting all available IPs and affecting other participants. Additionally, you can allocate a separate set of subnets for VPC infrastructure purposes.
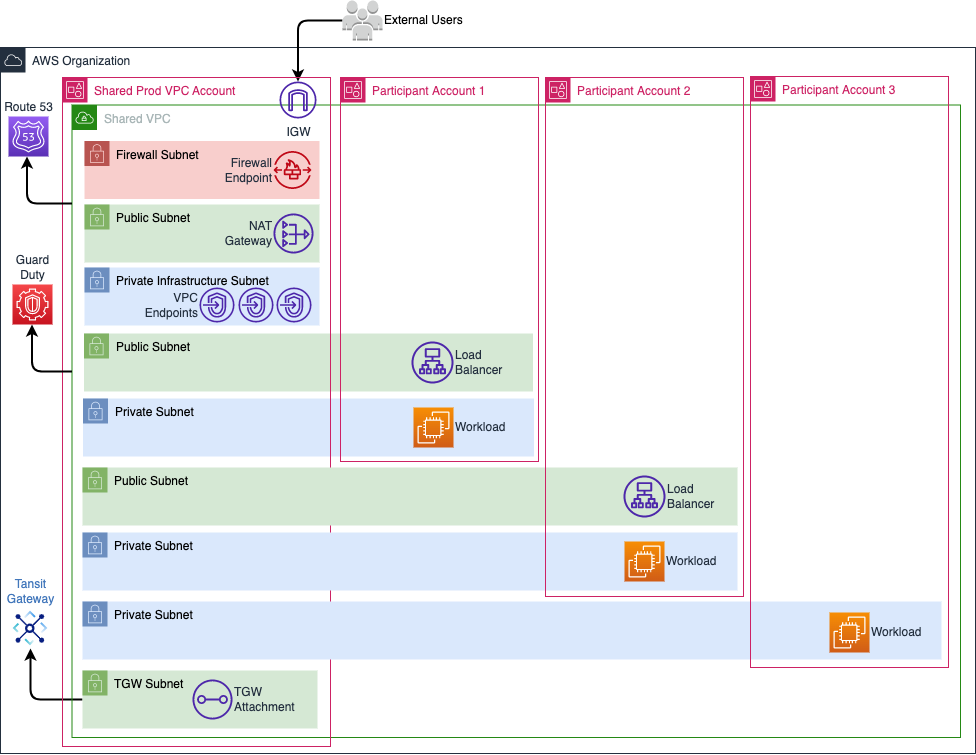
One of the most common models is to have multiple security zones within the same shared VPC.
- The VPC owner has centralized control over the Network ACLs and routing for all subnets.
- All participant accounts automatically utilize the transit gateway in the owner account to route traffic to on-premises resources.
- All participant accounts to access the internet through the NAT gateway configured in the owner account, and traffic is always inspected through the owner account's AWS Network Firewall.
- The VPC owner is responsible for managing VPC-related logs, such as Flow Logs and VPC DNS query logs.
- GuardDuty findings are only accessible to the AWS accounts that own the resources where malicious activity is detected.
- The owner VPC is responsible for managing DNS resolutions and forwarding rules, and there is no need for any additional configuration for participant VPCs to use this DNS.
- Participant VPCs can use the endpoints configured in the owner account's VPC subnets.
Use Cases for Multi-Account Strategies With VPC Sharing
Multi-account strategies with VPC sharing can be used in several scenarios, such as:
- Enterprise IT: If you're an enterprise IT organization, you can use multi-account strategies with VPC sharing to manage resources for different business units or departments. You can also use VPC sharing to control access to network resources and enforce security policies.
- Managed service providers: If you're a managed service provider, you can use multi-account strategies with VPC sharing to manage resources for multiple customers. You can also use VPC sharing to centralize network resources and improve efficiency.
- Software as a service (SaaS) providers: If you're a SaaS provider, you can use multi-account strategies with VPC sharing to manage resources for different tenants or customers. You can also use VPC sharing to control access to network resources and enforce security policies.
Conclusion
Multi-account strategies with VPC sharing provide a powerful approach to managing AWS resources across multiple AWS accounts. By using separate AWS accounts for different workloads or departments and sharing VPC resources, you can improve security, increase efficiency, and reduce costs. By following the best practices outlined in this blog post, you can set up multi-account strategies with VPC sharing and start reaping their benefits.
Opinions expressed by DZone contributors are their own.

Comments