Learn How To Crack Passwords With Hashcat
This tutorial will guide you how to install Hashcat and also crack any password hashed in MD5, MD4, SHA1, SHA3 and other hash functioning techniques with examples and practice questions.
Join the DZone community and get the full member experience.
Join For Free
Hashcat claims to be the world’s fastest CPU and GPU password “recovery” tool. It is cross-platform, and available on Windows, macOS and Linux.
It supports a large variety of hashing algorithms, including LM Hash, NT hash, MD4, MD5, SHA-1, and 2 and many, many more. (Currently, it supports 237 different hash types)
The Basics
There are 4 arguments in the command used to crack the password. Below is the breakdown of the command.
.\hashcat -m 0 -a 0 .\crackme.txt .\rockyou.txt
-m(or --hash-type)
- For example, MD5, SHA1, etc.
- In the example, we will use “-m 0” which is for MD5.
- -a(or –attack-mode)
- Tells hash cat how to crack passwords.
- For example, using a dictionary of words, or brute-force, or the famous combination attack.
- In the example, we will use “-a 0” to use a dictionary attack.
- [filename]
- Specifies the location of the file containing the hash(es) you intend to crack
- In the example I have used “.\crackme.txt.
- [dictionary | mask | directory]
- Specifies the dictionary(wordlist), mask, or directory to be used.
- In the example, we will use “.\rockyou.txt”
Installation and Setup
Visit the website- https://hashcat.net/hashcat/
Download the binary version of the two given zip files and extract them.
Run cmd and cd to the directory where the hashcat is extracted. To copy the path just refer to the pic below.
When you are in the correct directory type the command to execute the hashcat.exe file. You will see the boilerplate of the command which is used as mentioned below.
Create a new text document inside the hashcat folder where your hashed passwords will be stored in my case its .\crackme.txt. Below is the list of test hashes that you can copy.
6c569aabbf7775ef8fc570e228c16b98
e10adc3949ba59abbe56e057f20f883e
25f9e794323b453885f5181f1b624d0
5f4dcc3b5aa765d61d8327deb882cf9
d8578edf8458ce06fbc5bb76a58c5ca4
fcea920f7412b5da7be0cf42b8c93759
96e79218965eb72c92a549dd5a330112
25d55ad283aa400af464c76d713c07ad
e99a18c428cb38d5f260853678922e03
7c6a180b36896a0a8c02787eeafb0e4c
3f230640b78d7e71ac5514e57935eb69
f6a0cb102c62879d397b12b62c092c06
NOTE: Add at least 5 hashes to test with at a time. If not done, Hashcat ignores them and gives you a message that it is exhausted.
You can also generate your own hashes here: https://passwordsgenerator.net/md5-hash-generator/
Now a create a dictionary file. Hashcat gives a pre-made dictionary called example(DICT file) either use that or create your own dictionary files.
You can find one here: https://www.scrapmaker.com/data/wordlists/dictionaries/rockyou.txt
The Final Command
Open cmd and make sure you are in the correct directory.
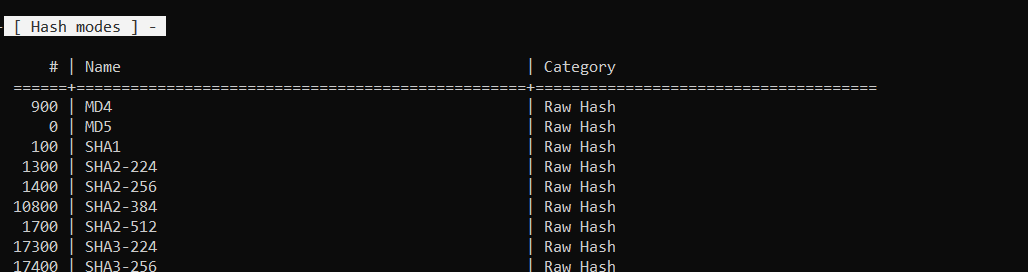
For different attack modes and hashing algorithms supported by Hashcat, type the following command and it will give you list of information.
Here we are using dictionary attack (-a 0) on MD5 hash(-m 0).
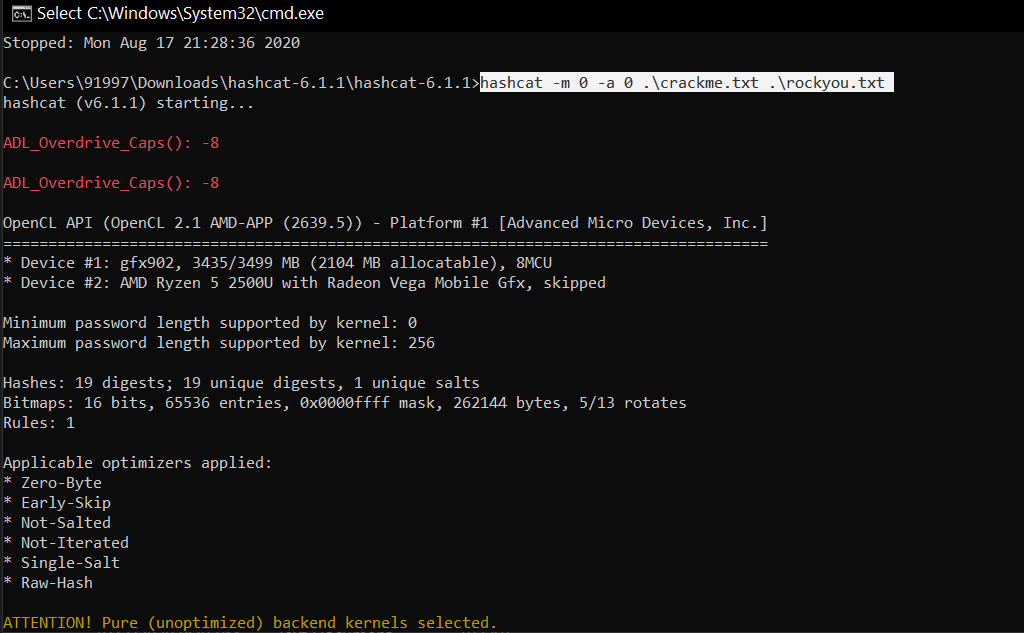
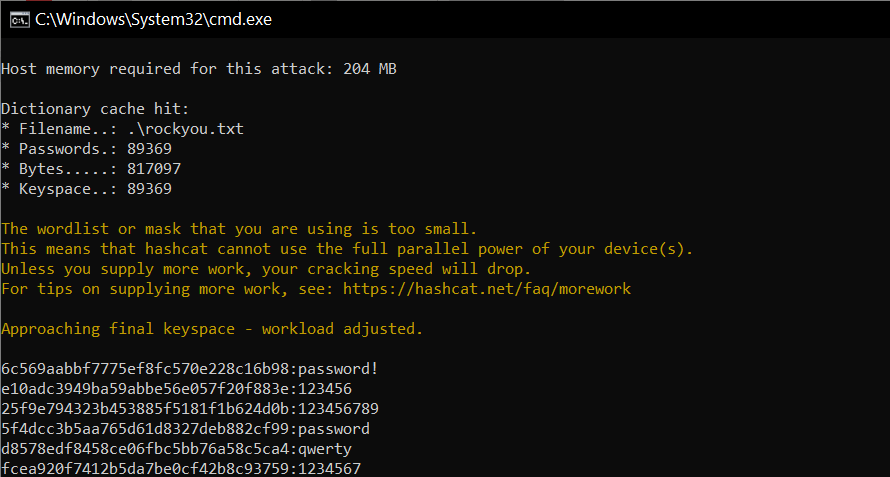
Now a brilliant in-built feature of Hashcat appends all the cracked passwords in a potfile which you can see in the directory.
Comment the actual passwords of the remaining used in the test example.
If you want more tutorials with combinator attacks and brute-force attacks let me know in the comments.
Opinions expressed by DZone contributors are their own.

Comments