Deploying Spring Boot to ECS — Part 1
Learn how to dockerize a Spring Boot microservice application and deploy it in an ECS cluster with a load balancer.
Join the DZone community and get the full member experience.
Join For FreeMicroservices are a common trend, and deploying them to the cloud is the prime factor of most projects nowadays. Important factors are zero downtime at peak hours, and how easily they can scale. We will be covering how to dockerize a Spring Boot application and deploy it in an ECS cluster in a private subnet with a load balancer in a public subnet.
- Setting Up a VPC network
- ECR
- ECS Concepts
- Create an ECS Cluster With Fargate
- Application Load Balancer
- Auto Scaling in ECS With Apache Benchmark
Setting Up a VPC Network
In this article, we will discuss setting up the VPC with two private and two public subnets in two distinct availability zones.
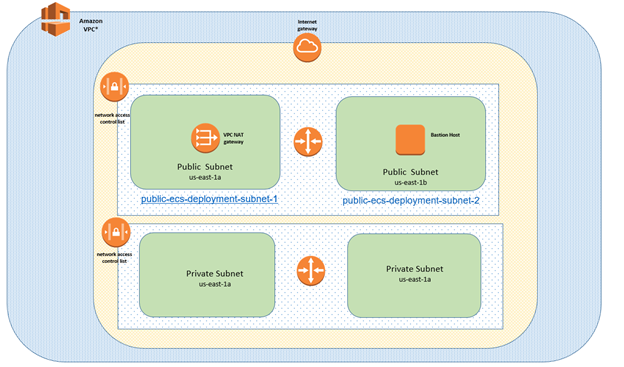
In the above design, the VPC will have a private subnet in two availability zones and the public subnets have to be in the same availability zone. Let’s go with definitions as per the diagram and then we will go on to how to set it up.
Amazon VPC: VPC is the Virtual Private Cloud which creates a networking layer for any services we spin up in AWS. It logically isolates the systems by creating a virtual network.
Internet Gateway: As the name suggests, it is a gateway to the Internet for all the resources within the VPC. If any resource within the VPC wants to call any services or fetch resources from th Internet, it needs to go via an Internet Gateway.
NACL: A network access control list (ACL) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets.
Subnet: A range of IP addresses allocated within the VPC network. AWS provides the option of creating public subnets, which are accessible from the internet, and private subnets, which are not. Any resources within a private subnet are secured and not accessible by outside sources. Hence, we will be spinning up all the containers and tasks of ECS in private subnet, whereas the load balancer will be in the public subnet. We will cover this more in the upcoming sections.
Router: A router, also known as a route table, is a set of rules that route traffic from one subnet to another. Each subnet should have one and only one route table that will specify where the traffic is routed.
NAT gateway: Network Address Translation is a gateway for resources launched inside a private subnet to be able to invoke services from the Internet. Basically, a NAT is a gateway to the Internet from private subnets. However, the reverse is not true; i.e., from the Internet, you cannot access private subnets.
Bastion Host: A bastion server or bastion host is created in a public subnet so that a proxy can be created to log into instances in the private subnet. This is a secure way of connecting to instances inside private subnets.
Setting Up the VPC
Create a VPC and provide the CIDR range as 10.0.0.0/16.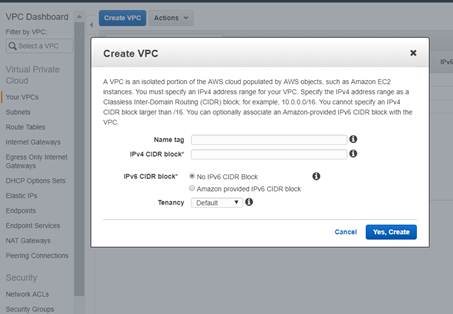
Create four subnets: two public (10.0.1.0/16 and 10.0.2.0/16) and two private (10.0.3.0/16 and 10.0.4.0/16). 10.0.1.0/16 and 10.0.3.0/16 should be in the same availability zone, and 10.0.2.0/16 and 10.0.4.0/16 should be in the same availability zone.
Create an Internet gateway and attach it to the VPC.
Create a NAT gateway with an Elastic IP associated with it.
Create two route tables, one for the public subnets and one for the private subnets. Associate the NAT gateway with the private route table and the internet gateway with the public route table.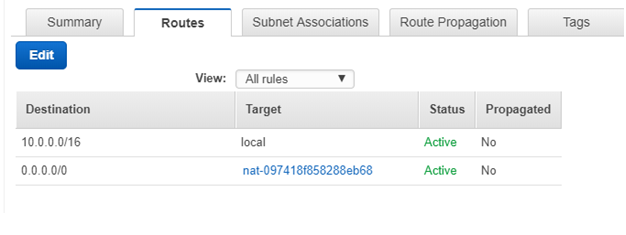
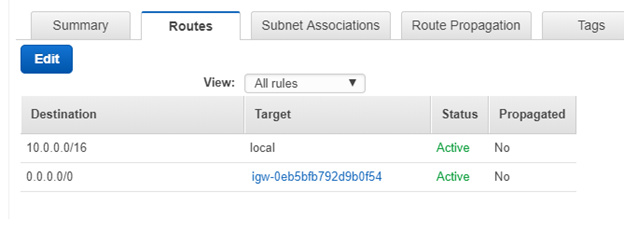
Create two Network ACLs, one private and one public.
The public one should have inbound rules like below:
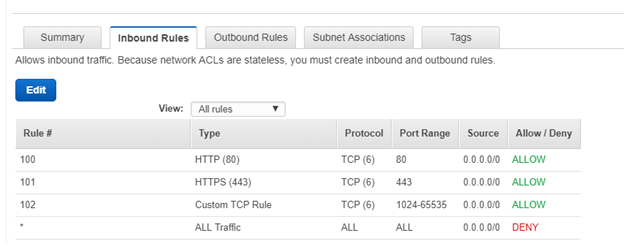
The private one should have inbound rules like below:
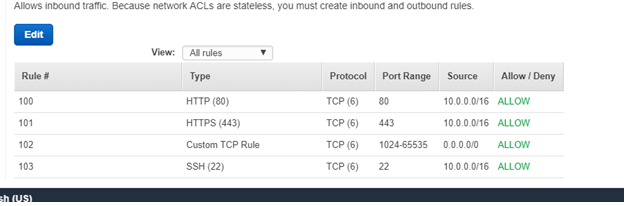
The VPC is all set now. Create a bastion host in the public subnet and associate it with the bastion security group. The bastion security group should have an SSH option enabled for port 22 and your own IP. Also, create an instance in the private subnet and a private security group which will allow only SSH with port 22 and the source as the bastion security group. This will make sure that the user can SSH to the private instance in this private subnet only via the bastion server.
In the next article, we will be deploying the ECS Fargate instance in this VPC with an ALB.
Published at DZone with permission of Joydip Kumar, DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments