Enhance Terraform Final Plan Output in GitHub Actions
Follow these tips to easily identify and confirm the exact cloud resource changes for your GitHub pipeline approvals.
Join the DZone community and get the full member experience.
Join For FreeTerraform is an Infrastructure as Code (IaC) tool that allows the DevOps engineer to automate the provision and management of infrastructure resources. It uses configuration files written in HashiCorp Config Language (HCL) to define the desired state of the infrastructure and has various commands to configure and apply the infra resources.
GitHub Actions is a continuous integration and delivery platform (CI/CD) that allows developers to automate build, test, and deployment pipelines. During the deployment configuration, we need to define a step: a step is an individual action that GitHub Actions performs.
Current State
While deploying an infrastructure resource through Terraform in general, the Terraform plan output shows all the execution logs and displays the final plan output at last. If many infrastructure changes are going on at the same time, all changes will get dumped into a single plan output, and the reviewer needs to scroll down to see the final output. It may lead to distraction and the possibility of missing the final plan output clearly, which results in destroying the resources by accident after execution.
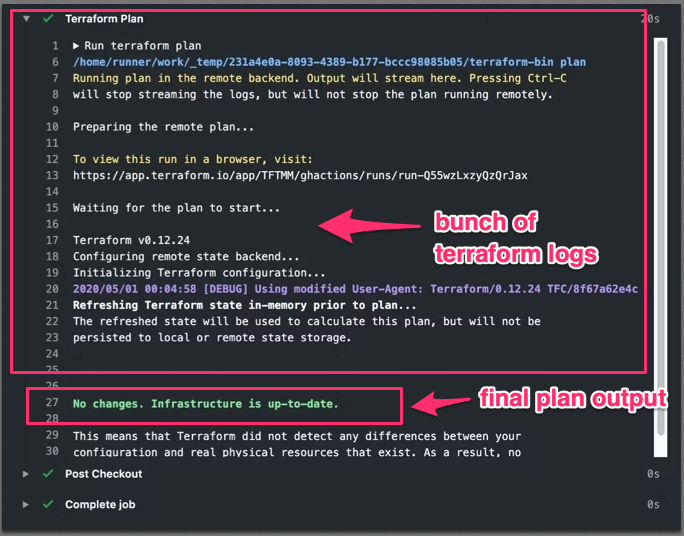
Proposed Solution
In this article, I have given a simpler solution to how to overcome the above problem in a simpler way. This will separate the Terraform output step into 3 steps.
Prerequisite
For this mock pipeline execution, I have used Google Cloud for the resource deployment. Before the code execution, set up the Google credentials as required (highlighted in the below code snippet).
Step 1
Introduce a new step in GitHub actions to collect all Terraform stdout log output.
Step 2
This output needs to be saved into a GitHub output variable.
Step 3
Use the output variable in the next steps, filter the plan output log alone to display in this step execution log, and provide the text contents and background color to gain attention during the pull request reviews.
#comment: introduce a new step to capture terraform stdout output and dump the logs into GitHub output variable
#comment: used google cloud for deployment and set up google credentials for this execution
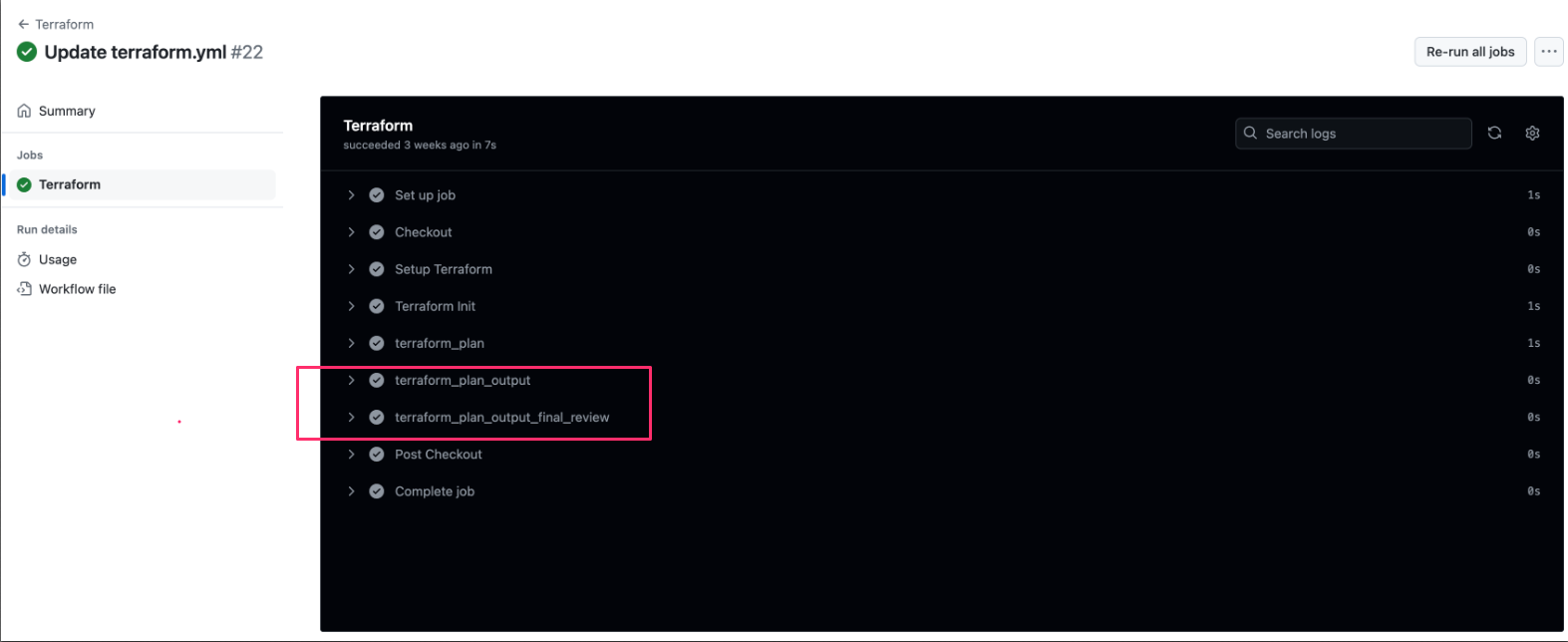
- name: terraform_plan_output
id: terraform_plan_output
run: |
{
echo 'tfplan_output<<EOF'
terraform plan -input=false 2>&1
echo EOF
} >> "$GITHUB_OUTPUT"
env:
GOOGLE_CREDENTIALS: ${{ secrets.GOOGLE_APPLICATION_CREDENTIALS }}
#comment: with the help of above step output variable, in this step, filter the logs and find only for final plan output line.
#comment: color code the line as needed with background shade to get reviewers attention before pull request approval
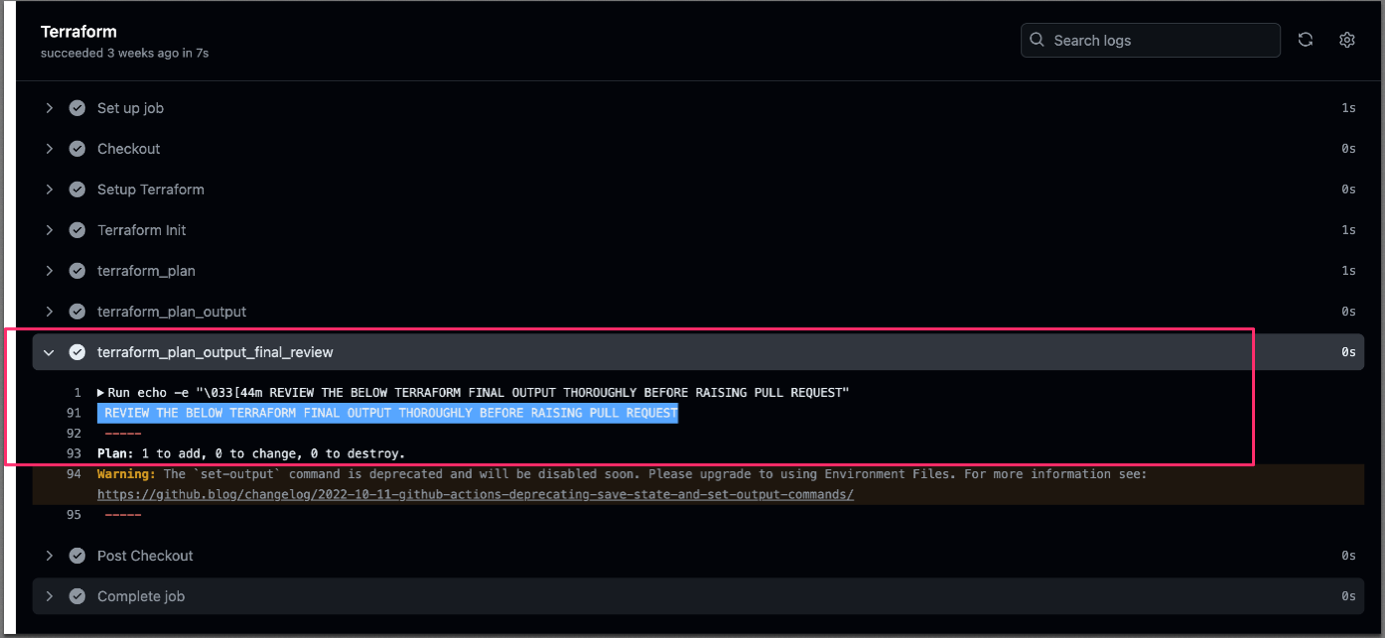
- name: terraform_plan_output_final_review
run: |
echo -e "\033[44m REVIEW THE BELOW TERRAFORM FINAL OUTPUT THOROUGHLY BEFORE RAISING PULL REQUEST"
echo -e "\033[31m -----"
echo "${{ steps.terraform_plan_output.outputs.tfplan_output }}" | grep 'Plan:'
echo -e "\033[31m -----"Mock Execution Screenshots
Introduce a separate step in the Terraform output plan:
Terraform final review plan with a comment:
Benefits
Separate out Terraform stdout logs and final plan output. This helps the GitHub reviewer to focus on the exclusive plan output step and see the infra changes clearly. Background color helps to get more attention during the review. Infra changes through Terraform, especially during update and delete, need more attention. This individual step may avoid environmental outages at later stages.
Conclusion
By following these tips, as a code reviewer or pull request approver, you are able to easily identify and confirm the exact cloud resource changes for your GitHub pipeline approvals.
For sample code, visit the repository on GitHub (maintainer: Karthigayan Devan).
Opinions expressed by DZone contributors are their own.

Comments