Generating Secure Properties in Mule 4
This blog will explore both traditional methods (using jar) and modern methods (using secure property generator) of generating secure properties in Mule 4.
Join the DZone community and get the full member experience.
Join For FreeSecure Property Placeholder is an essential standard for keeping sensitive data like User ID and Password secure (encrypted/cypher-text) in the Property file. Securing properties is one of the crucial elements in every Mule project. MuleSoft has introduced a Secure properties generator with a point and click environment that saves time and effort in specific scenarios.
This blog will explore both traditional methods — using jar — and modern methods — using secure property generator — of generating secure properties in Mule 4.
Method 1: Using Jar
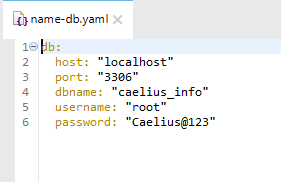
1. Create a simple Properties Config file that will be used as an input file.
File Name: name-db.yaml
2. We need to add the “Mule Secure Configuration” module now. It is not available in Anypoint studio by default. We need to add it from any point exchange. Click on the “Search in exchange” button in the Mule palette on the right side.
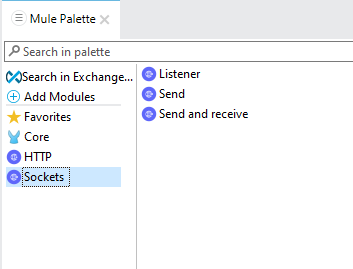
Then search for “Secure” and select the “Mule Secure Configuration” module.
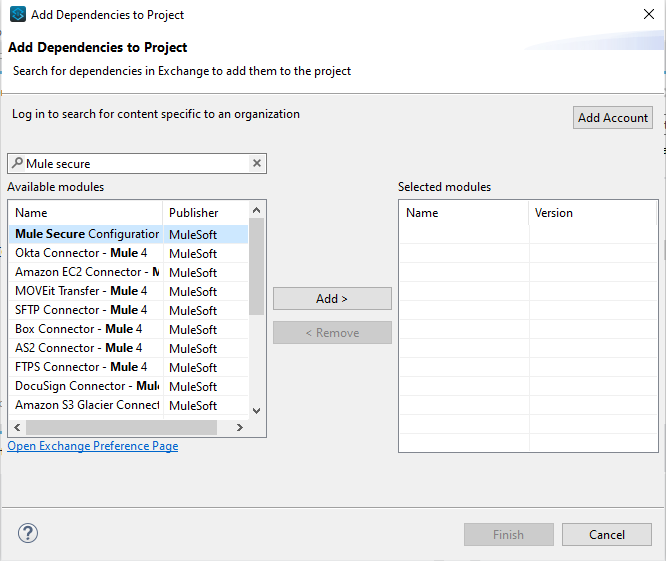
Click on “Add” to add this dependency to our project.
3. Now, Select the Global elements tab in your XML and click on “Create”. Then select “Secure properties Config” as shown below:
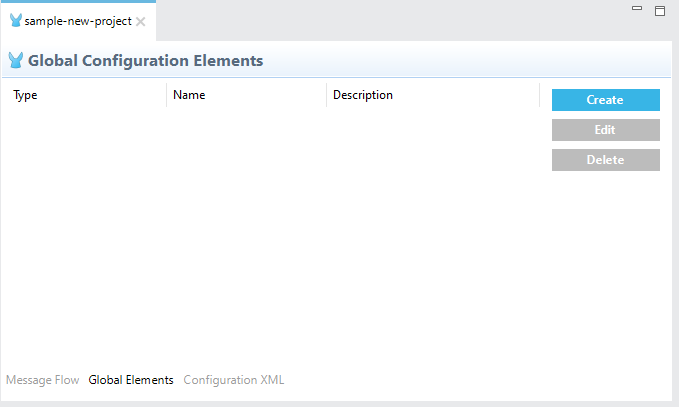
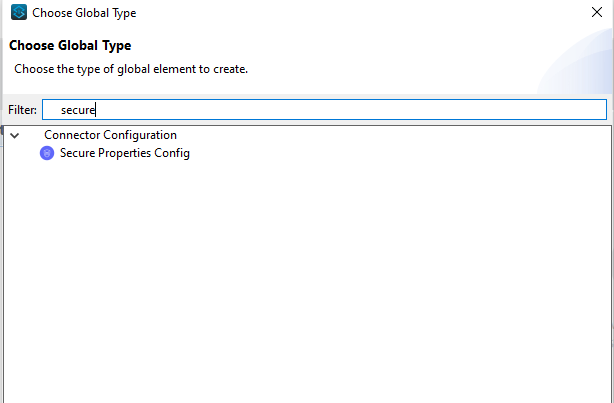
Now Configure Secure Properties Config as shown below:
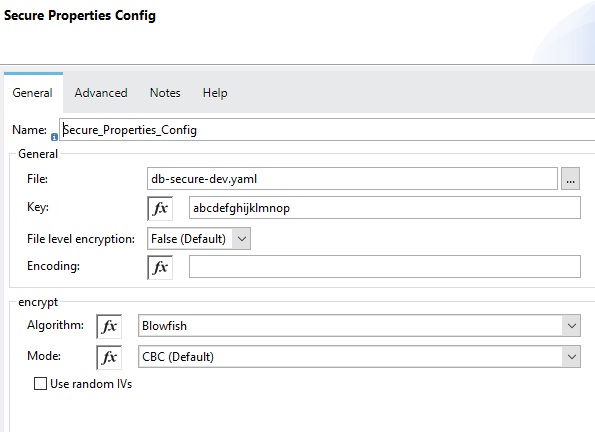
4. Now we have to generate a db-secure-dev.yaml file with encrypted property values using the jar file. This jar can be downloaded from the documentation page of MuleSoft.
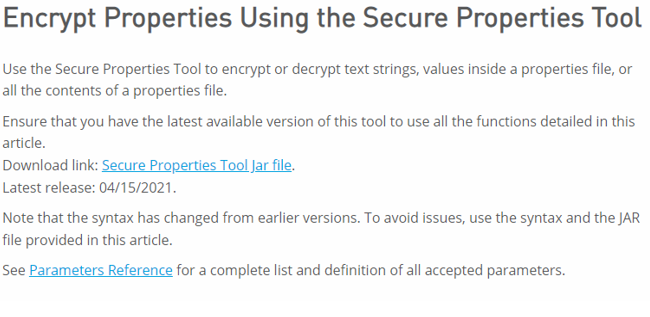
We can use the following command:
Open CMD and run these commands by adding the encryption and decryption information.
java -jar secure-properties-tool.jar file <encrypt|decrypt> <algorithm> <mode> <key> <input file> <output file>
java -jar secure-properties-tool.jar file encrypt Blowfish CBC abcdefghijklmnop db-dev.yaml + db-secure-dev.yamlYou can change the KEY according to your requirements.
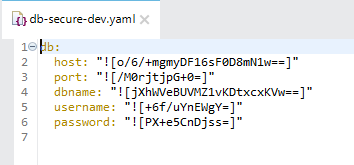
Copy the generated db-secure-dev.yaml into src/main/resources.
Now, edit the Database Config as shown below:
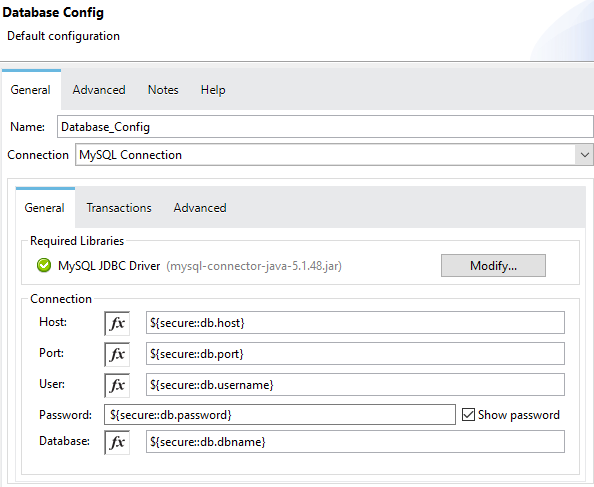
Run the application and observe if it still works the same.
<?xml version="1.0" encoding="UTF-8"?>
<mule xmlns:secure-properties="http://www.mulesoft.org/schema/mule/secure-properties" xmlns:ee="http://www.mulesoft.org/schema/mule/ee/core"
xmlns:db="http://www.mulesoft.org/schema/mule/db"
xmlns:http="http://www.mulesoft.org/schema/mule/http" xmlns="http://www.mulesoft.org/schema/mule/core" xmlns:doc="http://www.mulesoft.org/schema/mule/documentation" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.mulesoft.org/schema/mule/core http://www.mulesoft.org/schema/mule/core/current/mule.xsd
http://www.mulesoft.org/schema/mule/http http://www.mulesoft.org/schema/mule/http/current/mule-http.xsd
http://www.mulesoft.org/schema/mule/db http://www.mulesoft.org/schema/mule/db/current/mule-db.xsd
http://www.mulesoft.org/schema/mule/ee/core http://www.mulesoft.org/schema/mule/ee/core/current/mule-ee.xsd
http://www.mulesoft.org/schema/mule/secure-properties http://www.mulesoft.org/schema/mule/secure-properties/current/mule-secure-properties.xsd">
<configuration-properties doc:name="Configuration properties" doc:id="939739f1-02cc-4494-9174-e1bac975c70a" file="name-db.yaml" />
<db:config name="Database_Config" doc:name="Database Config" doc:id="7ca8be2a-b438-497f-9490-67180ca2b9c7" >
<db:my-sql-connection host="${secure::db.host}" port="${secure::db.port}" user="${secure::db.username}" database="${secure::db.dbname}" password="${secure::db.password}"/>
</db:config>
<secure-properties:config name="Secure_Properties_Config" doc:name="Secure Properties Config" doc:id="2de5364a-c147-4269-adfb-e3fa528c8e35" file="db-secure-dev.yaml" key="abcdefghijklmnop" >
<secure-properties:encrypt algorithm="Blowfish" />
</secure-properties:config>
</mule>Method 2: Securing Properties Using Secure Properties Generator
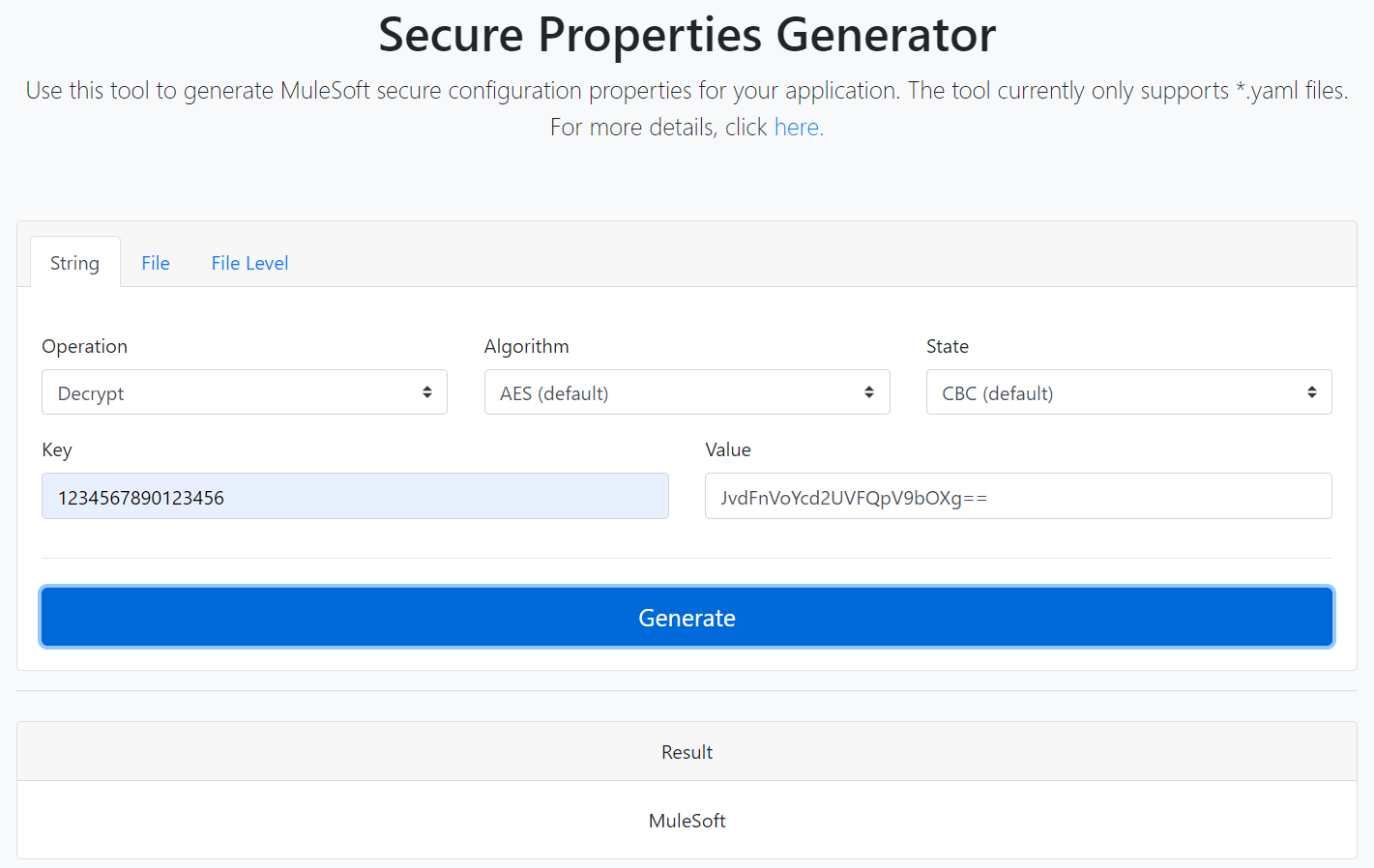
MuleSoft has optimized the complete process by providing an online secure properties generator that gives developers ease of securing properties. MuleSoft developers can now secure the properties in a point and click environment eliminating the command line interface.
The secure properties generator gives us an option of directly encrypting our values without creating an input file. However, we can secure our properties using input files as well.
1. Visit the MuleSoft secure properties generator.
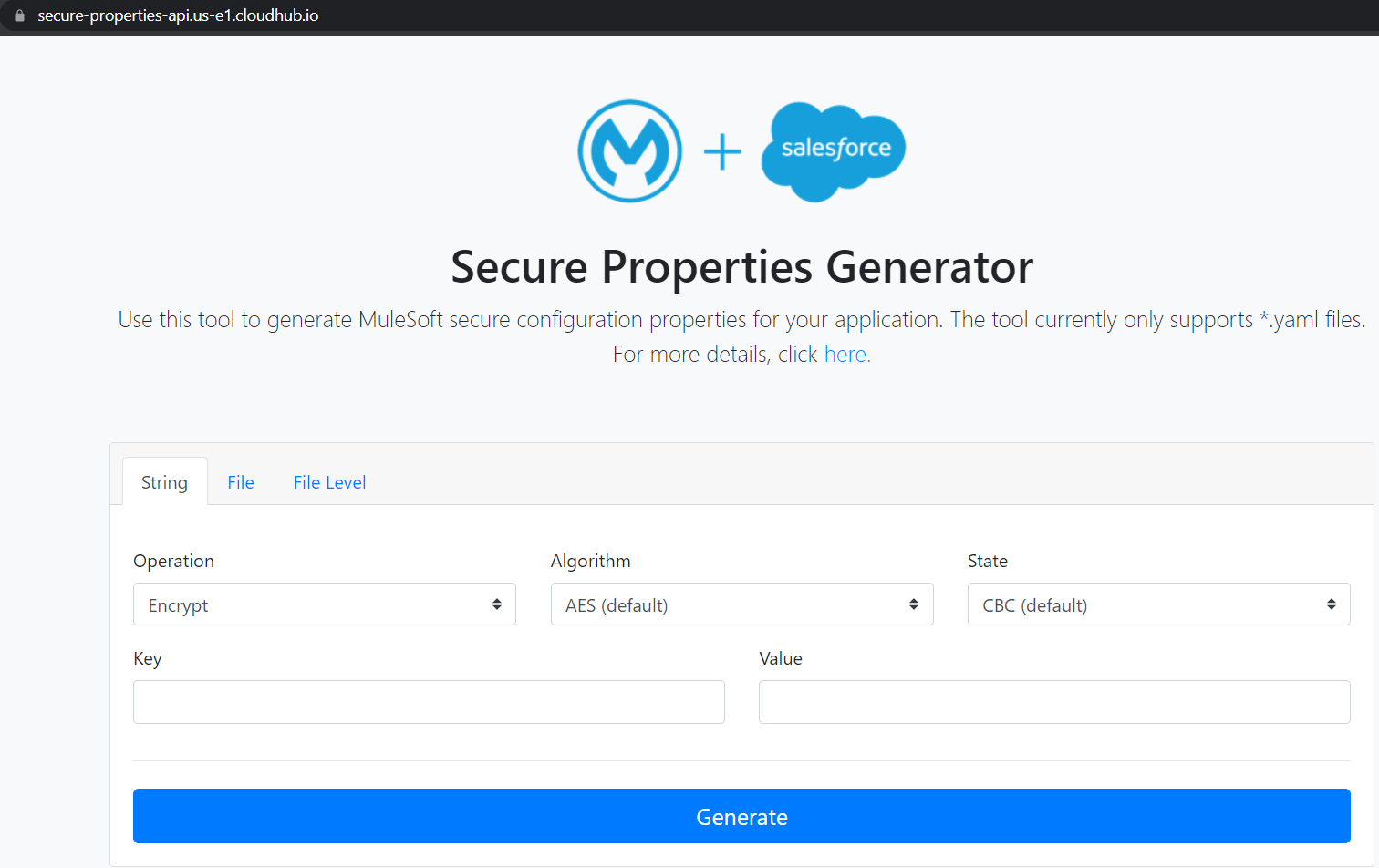
2. Provide the following configurations for operation, algorithm, state, and special key:
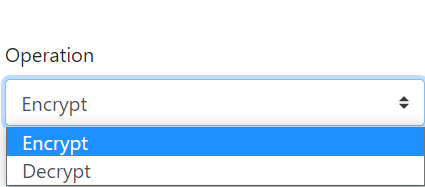
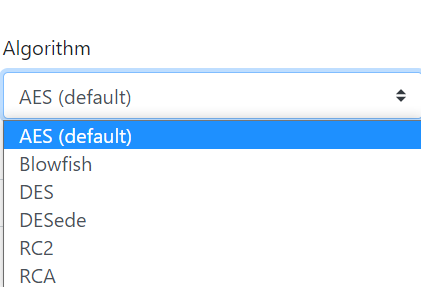
Reminders: While choosing the AES algorithm, you have to provide a key of length 16. While choosing the Blowfish algorithm, you have to provide a key of length 15.
3. Fill in the value you want to encrypt.
4. Click on Generate to get the required result.
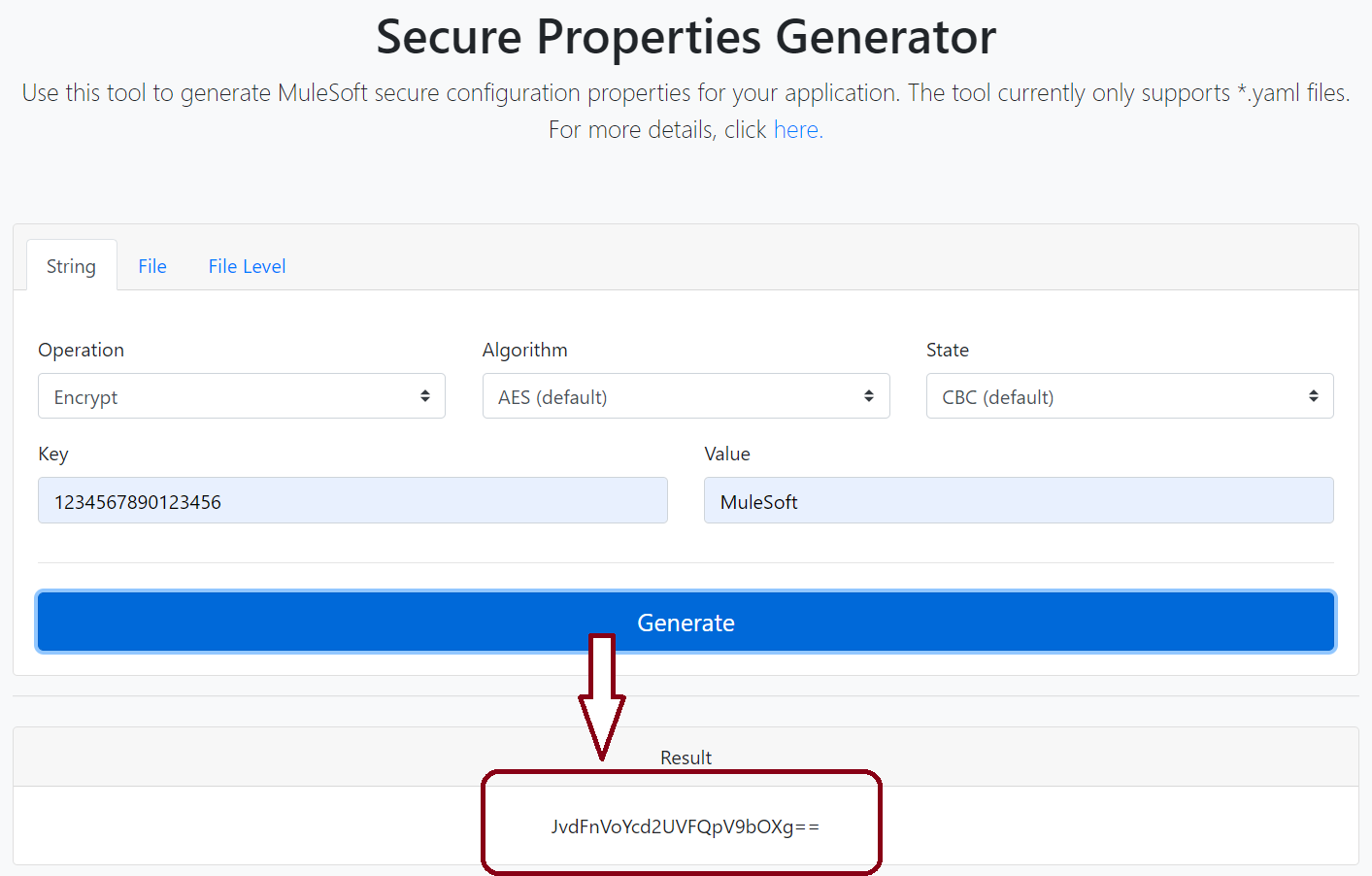
You can also provide the encrypted result along with the key (previously used for encryption) to get the original value.
Securing properties is one of the essential elements in every Mule project, and MuleSoft has made this process far easier for a developer by introducing Secure Properties Generator.
Published at DZone with permission of Achaleshwar Singh. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments