A Comprehensive Guide to Access and Secrets Management: From Zero Trust to AI Integration — Innovations in Safeguarding Sensitive Information
By implementing effective secrets management, organizations can reduce risk, improve operational efficiency, and respond to incidents more quickly.
Join the DZone community and get the full member experience.
Join For FreeEditor's Note: The following is an article written for and published in DZone's 2024 Trend Report, Enterprise Security: Reinforcing Enterprise Application Defense.
Access and secrets management involves securing and managing sensitive information such as passwords, API keys, and certificates. In today's cybersecurity landscape, this practice is essential for protecting against breaches, ensuring compliance, and enhancing DevOps and cloud security. By implementing effective secrets management, organizations can reduce risk, improve operational efficiency, and respond to incidents more quickly. For developers, it provides a secure, convenient, and collaborative way to handle sensitive information, allowing them to focus on coding without worrying about the complexities of secure secrets handling.
This article explores the importance of access and secrets management, why organizations should care, and how it benefits developers.
Access and Secrets Management: Recent Industry Shifts
As we continue to embrace cloud-native patterns in our development environments, new terms surface. "Decentralized" is a newer term (at least to me) as there's growing traction for fast development cycles using a decentralized approach with the cloud. Decentralization improves scalability and security by isolating sensitive data and reducing the risk of large-scale breaches. Cloud security and identity management ensure that authentication and authorization processes are more robust and flexible, protecting user identities across a distributed environment.
An open-source tool example is Hyperledger Aries, part of the Hyperledger Foundation under the Linux Foundation. It provides the infrastructure for building, deploying, and using interoperable decentralized identity solutions.
- Aries provides the tools and libraries necessary for creating and managing decentralized identities based on verifiable credentials.
- Aries focuses on interoperability, ensuring that credentials issued by one party can be verified by another, regardless of the underlying system.
- Aries includes support for secure messaging and protocols to ensure that identity-related data is transmitted securely.
An excellent example of leveraging blockchain technology in AWS is the Managed Block Chain Identities. This service facilitates secure and efficient identity management, where identities are verified and managed through a decentralized network, ensuring robust security and transparency.
Let's look into another concept: zero-trust architecture.
Zero-Trust Architecture
Unlike traditional security models that rely on a well-defined perimeter, zero-trust architecture (ZTA) is a cybersecurity framework that assumes no user or device, inside or outside the network, can be trusted by default. This model requires strict verification for every user and device accessing resources on a private network. The core principle of zero trust is "never trust, always verify," ensuring continuous authentication and authorization.
Figure 1. Zero-trust architecture
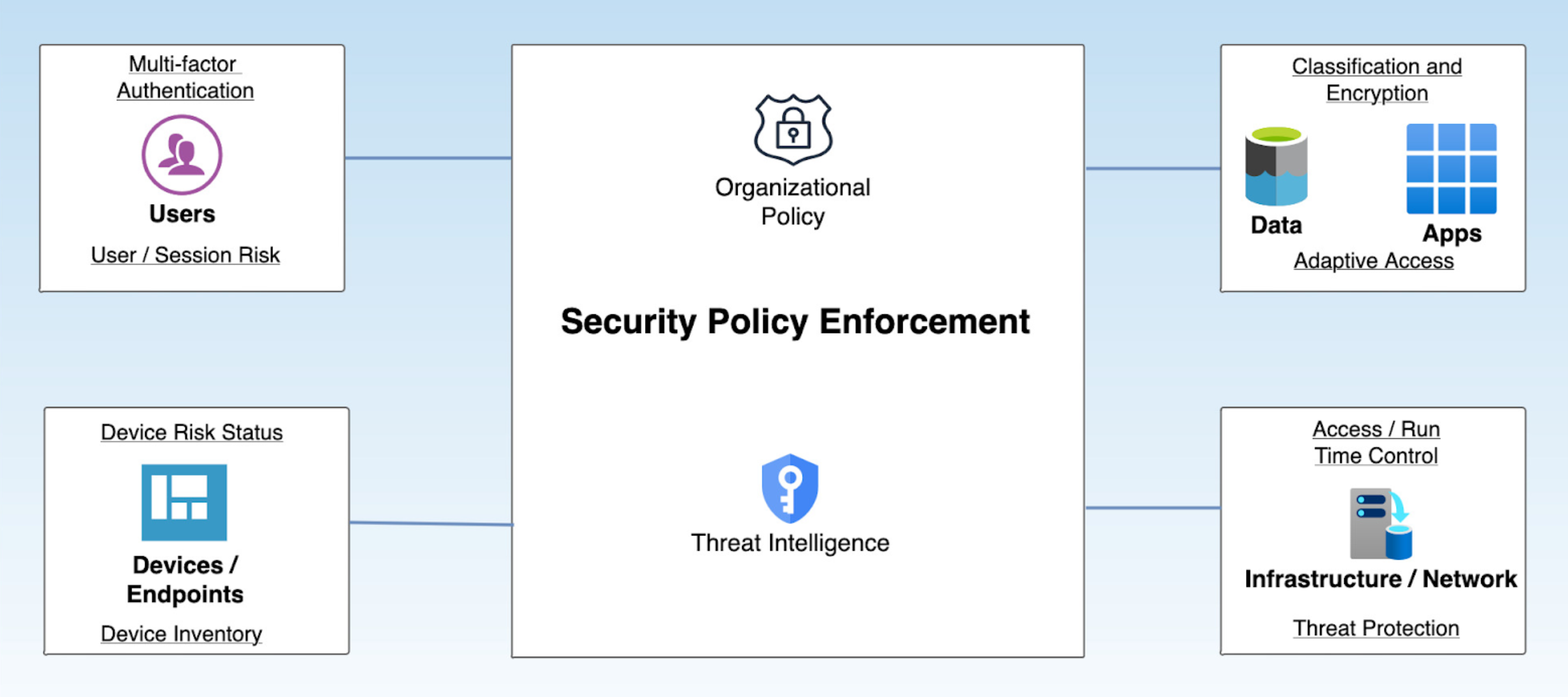
One of the key components of ZTA is micro-segmentation, which divides the network into smaller, more isolated segments to minimize the impact of potential breaches. This approach limits lateral movement within the network, therefore containing threats and reducing the attack surface. By implementing micro-segmentation, organizations can achieve finer-grained control over their network traffic, further supporting the principle of least privilege.
ZTA employs robust identity and access management (IAM) systems to enforce least-privilege access, ensuring users and devices only have the permissions necessary for their roles. By continuously verifying every access request and applying the least-privilege principle, ZTA can effectively identify and mitigate threats in real time. This proactive approach to security, grounded in micro-segmentation and least-privilege access, aligns with regulatory compliance requirements and enhances overall resilience against cyberattacks.
Another additional security feature is multi-factor authentication (MFA). Let's have a look at it.
MFA and Ways to Breach It
Advancements in MFA involve enhancing security by requiring multiple forms of verification before granting access to systems and data. These advancements make it harder for attackers to gain unauthorized access since they need multiple pieces of identification to authenticate.
However, MFA can be compromised with "MFA prompt bombing," a key concern for security. Imagine an attacker who has stolen a password and tries to log in, causing the user's device to receive multiple MFA prompts. They hope the user will either accept the prompt because they think it's legitimate or accept it out of frustration to stop the constant notifications.
Threat intelligence from ZDnet reveals how the hacking group, 0ktapus, uses this method. After phishing login credentials, they bombard users with endless MFA prompts until one is accepted. They might also use social engineering, like posing as Uber security on Slack, to trick users into accepting a push notification. Additionally, 0ktapus employs phone calls, SMS, and Telegram to impersonate IT staff and either harvests credentials directly or exploits MFA fatigue.
Behavioral Analytics With AI for Access Management
As cybersecurity threats grow more sophisticated, integrating AI and machine learning (ML) into access management systems is becoming crucial. AI technologies are continuously enhancing IAM by improving security, streamlining processes, and refining user experiences.
Key implementations include:
- User behavior analytics (UBA) – AI-driven UBA solutions analyze user behavior patterns to detect anomalous activities and potential security threats. For example, accessing sensitive data at unusual times or from unfamiliar locations might trigger alerts.
- Adaptive authentication – AI-powered systems use ML algorithms to assess real-time risks, adjusting authentication requirements based on user location, device type, and historical behavior. For example, suppose a user typically logs in from their home computer and suddenly tries to access their account from a new or unfamiliar device. In that case, the system might trigger additional verification steps.
- Identity governance and administration – AI technologies automate identity lifecycle management and improve access governance. They accurately classify user roles and permissions, enforce least privilege, and streamline access certification by identifying high-risk rights and recommending policy changes.
Core Use Cases of Access and Secrets Management
Effective access and secrets management are crucial for safeguarding sensitive data and ensuring secure access to resources. It encompasses various aspects, from IAM to authentication methods and secrets management. Typical use cases are listed below:
- IAM – Manage identity and access controls within an organization to ensure that users have appropriate access to resources. This includes automating user onboarding processes to assign roles and permissions based on user roles and departments and performing regular access reviews to adjust permissions and maintain compliance with security policies.
- Authentication and authorization – Implement and manage methods to confirm user identities and control their access to resources. This includes single sign-on (SSO) to allow users to access multiple applications with one set of login credentials and role-based access control to restrict access based on the user's role and responsibilities within the organization.
- Secrets management – Securely manage sensitive data such as API keys, passwords, and other credentials. This involves storing and rotating these secrets regularly to protect them from unauthorized access. Additionally, manage digital certificates to ensure secure communication channels and maintain data integrity across systems.
Secrets Management: Cloud Providers and On-Premises
Secrets management is a critical aspect of cybersecurity, focusing on the secure handling of sensitive information required to access systems, services, and applications. What constitutes a secret can vary but typically includes API keys, passwords, and digital certificates. These secrets are essential for authenticating and authorizing access to resources, making their protection paramount to prevent unauthorized access and data breaches.
Table 1
|
environment
|
overview
|
features
|
benefits
|
|---|---|---|---|
|
A cloud service for securely storing and accessing secrets |
Secure storage for API keys, passwords, and certificates; key management capabilities |
Centralized secrets management, integration with Azure services, robust security features |
|
|
Manages secrets and credentials in the cloud |
Rotation, management, and retrieval of database credentials, API keys, and other secrets |
Automated rotation, integration with AWS services, secure access control |
|
|
On-premises secrets management |
Managing and storing secrets within an organization's own infrastructure |
Secure vaults and hardware security modules for storing sensitive information; integration with existing IT infrastructure |
Complete control over secrets, compliance with specific regulatory requirements, enhanced data privacy |
|
Encrypted storage |
Uses encryption to protect secrets stored on-premises or in the cloud |
Secrets are stored in an unreadable format, accessible only with decryption keys |
Enhances security by preventing unauthorized access, versatile across storage solutions |
|
Open-source tool for securely accessing secrets and managing sensitive data |
Dynamic secrets, leasing and renewal, encryption as a service, and access control policies |
Strong community support, flexibility, and integration with various systems and platforms |
|
|
Open-source IAM solution |
Supports SSO, social login, and identity brokering |
Free to use, customizable, provides enterprise-level features without the cost |
Let's look at an example scenario of access and secrets management.
Use Case: Secured Banking Solution
This use case outlines a highly secured banking solution that leverages the Azure AI Document Intelligence service for document recognition, deployed on an Azure Kubernetes Service (AKS) cluster. The solution incorporates Azure Key Vault, HashiCorp Vault, and Keycloak for robust secrets management and IAM, all deployed within the AKS cluster. However, this use case is not limited to the listed tools.
Figure 2. Banking solutions architecture

The architecture consists of the following components:
- The application, accessible via web and mobile app, relies on Keycloak for user authentication and authorization. Keycloak handles secure authentication and SSO using methods like biometrics and MFA, which manage user sessions and roles effectively.
- For secrets management, Azure Key Vault plays a crucial role. It stores API keys, passwords, and certificates, which the banking app retrieves securely to interact with the Azure AI Document Intelligence service. This setup ensures that all secrets are encrypted and access controlled.
- Within the AKS cluster, HashiCorp Vault is deployed to manage dynamic secrets and encryption keys. It provides temporary credentials on demand and offers encryption as a service to ensure data privacy.
- The application utilizes the Azure AI Document Intelligence service for document recognition tasks. Access to this service is secured through Azure Key Vault, and documents are encrypted using keys managed by HashiCorp Vault.
Conclusion
Access and secrets management is crucial for safeguarding sensitive information like passwords and API keys in today's cybersecurity landscape. Effective management practices are vital for preventing breaches, ensuring compliance, and enhancing DevOps and cloud security. By adopting robust secrets management strategies, organizations can mitigate risks, streamline operations, and respond to security incidents swiftly.
Looking ahead, access and secrets management will become more advanced as cyber threats evolve. Expect increased use of AI for automated threat detection, broader adoption of decentralized identity systems, and development of solutions for managing secrets in complex multi-cloud environments. Organizations must stay proactive to protect sensitive information and ensure robust security.
This is an excerpt from DZone's 2024 Trend Report, Enterprise Security: Reinforcing Enterprise Application Defense.
Read the Free Report
Opinions expressed by DZone contributors are their own.

Comments