Integrate AWS Secrets Manager in Spring Boot Application
A guide for integration of AWS Secrets Manager in Spring Boot. This service will load the secrets at runtime and keep the sensitive information away from the code.
Join the DZone community and get the full member experience.
Join For FreeIntroduction
In this article, we will understand the integration of AWS Secrets Manager in the Spring Boot Application. This service will load the secrets at runtime and make sure to keep the sensitive information away from the code.
Context
When we work on a Spring Boot Application, we have an application.properties file based on the different profiles (environment). In these files, we keep all the information related to the configuration of the Spring Boot application. The file contains database credentials and other sensitive information like any credentials or ftp server's endpoint along with credentials. This sensitive information is not recommended to be put directly into the code for security concerns. To avoid such vulnerabilities in our application, we have to take several measures in order to ensure the security of sensitive information.
There are several ways to secure this information. We can define server arguments to load such details, and other ways are there too. As we are using AWS, there is a service available for the same. The service of AWS which we can use to store sensitive information and credentials is Secrets Manager. In this document, we will see how to integrate the AWS Secrets Manager and load all the secrets at the runtime and make our application secure.
What Is AWS Secrets Manager?
AWS Secrets Manager is an AWS service that makes it easier for you to manage secrets. Secrets can be database credentials, passwords, third-party API keys, and even arbitrary text. You can store and control access to these secrets centrally by using the Secrets Manager console, the Secrets Manager command-line interface (CLI), or the Secrets Manager API and SDKs.
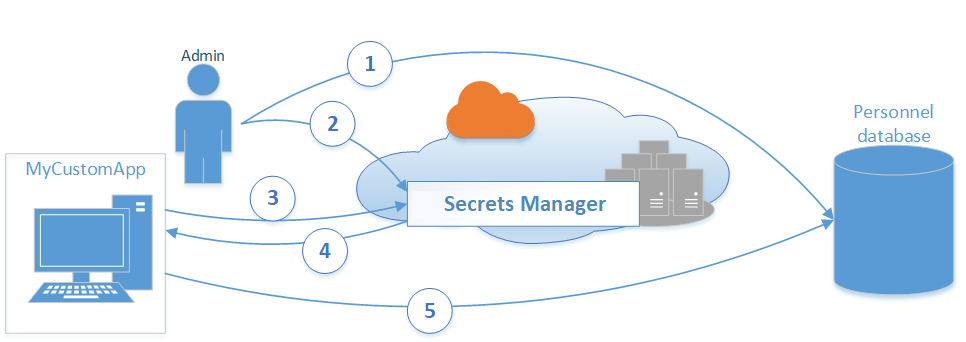
Let's create the secrets first.
In order to create the secrets, we need to log in to our AWS Console, and there, we have to search for the Secrets Manager in the service lists.
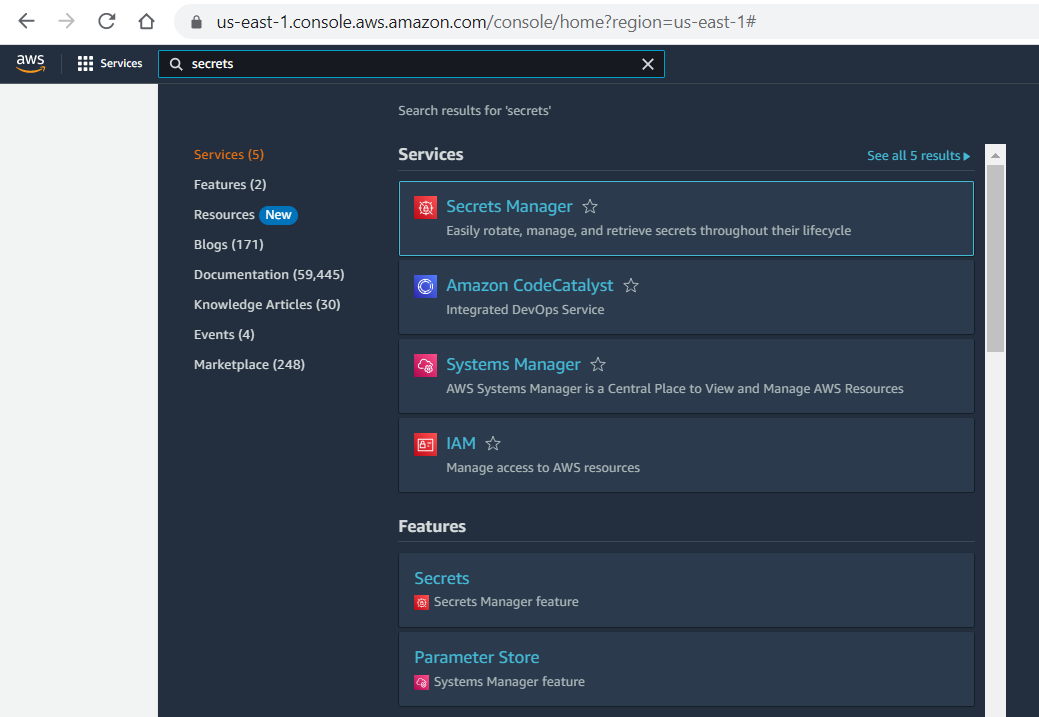
Now, we have to create new secrets by simply selecting the following type from the selection options, and we can create secrets there in the form of key and value. Here, we can add any number of secrets we want for our purpose.
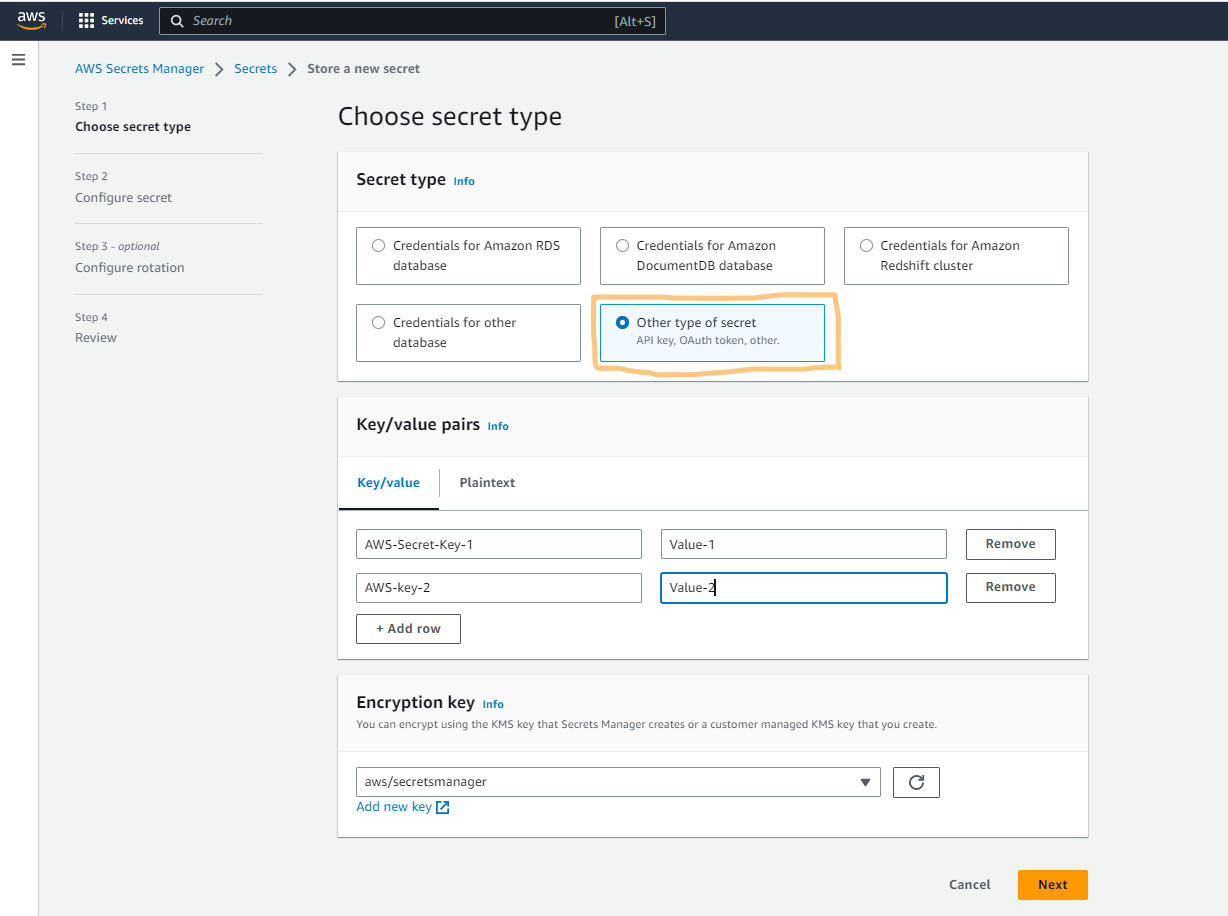
After creating all the secrets in the key-value pair, we have to click next, and we have to provide the name of the secret. By this name only, we can retrieve the values in our application.
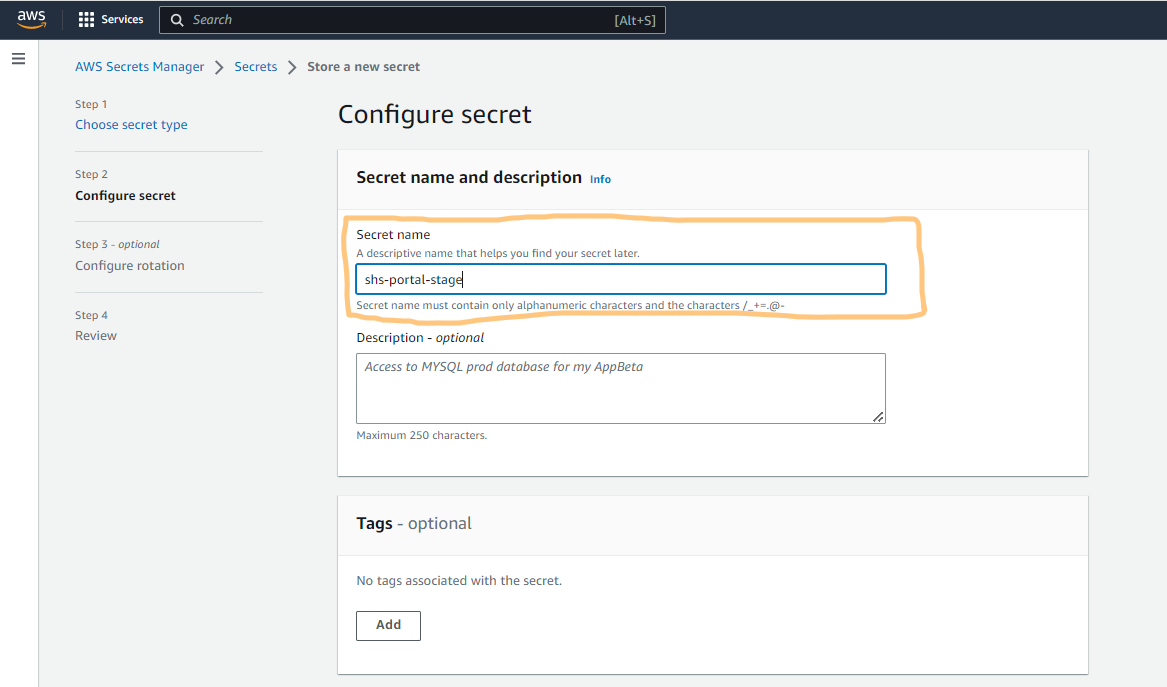
Once we complete this step, we will click on next, and there it will ask for a couple of configuration-related things which we have to select as per our requirement. If we want simple storage of secrets, we will let other configurations as it is and will move to the final screen of setting up the AWS secrets.
After successfully storing the secrets, we will now move to our Spring Boot application to retrieve the secrets there. In order to integrate the AWS Secrets Manager in our application, we need to add the Secrets Manager dependency in our pom.xml
In this article, we are using Spring Boot 2.7.3 version. Add the below dependency in the pom.xml as it is compatible with this version. You can change the version of dependency based on the version of your Spring Boot application.
<dependency>
<groupId>io.awspring.cloud</groupId>
<artifactId>spring-cloud-starter-aws-secrets-manager-config</artifactId>
<version>2.3.0</version>
</dependency>Note: The groupId for the secrets manager is changed. Earlier, it was org.springframework.cloud
Once you add the above dependency, now you have to import the secrets into our application. In this approach, we will be loading all the secrets at the bootstrap time of our application. The advantage of using this approach is that all the secrets will be available at the bootstrap time, and the information which is needed for the configuration in Spring Boot, such as database credentials and information needed in order to create beans, will be available. We need to add the below line in our application.properties file in order to import all the secrets.
spring.config.import= aws-secretsmanager: shs-portal-devIn this config, we are simply importing the secrets from AWS. The prefix aws-secretsmanager is needed in order to tell spring to load the config from AWS. In case the secrets are not available, we do not want our application to fail at the bootstrap, so we will add optional in the below manner to make the import optional.
spring.config.import= optional:aws-secretsmanager: shs-portal-devOnce this is done, we will start our Spring Boot application, and we will find the below line in the console. This line tells us that spring is loading the secrets from AWS Secrets Manager.
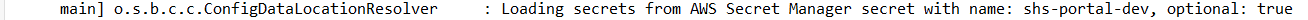
As we have seen, the following line in our logs ensures that secrets have been loaded successfully. In order to use them, we must use $ and {} to retrieve the value wherever needed.
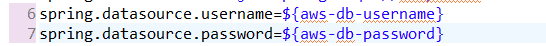
We can also retrieve the values in java code with the help of @Value annotation.
Note: If there is any error coming in regards to the bootstrap class in logs and the application fails to start, use the exclusion given below with the secrets manager dependency.
<dependency>
<groupId>io.awspring.cloud</groupId>
<artifactId>spring-cloud-starter-aws-secrets-manager-config</artifactId>
<version>2.3.0</version>
<exclusion>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-context</artifactId>
</exclusion>
</dependency>Opinions expressed by DZone contributors are their own.

Comments