How to Generate a Keystore and CSR Using the Keytool Command
Want to learn more about using the Java keytool command?
Join the DZone community and get the full member experience.
Join For FreeWhat Is a Keytool
A keytool is a key and certificate management JDK utility that helps manage a keystore of private/public keys and associated certificates. It allows users to administer their own public/private key pairs and associated certificates for use in self-authentication (where the user authenticates themselves to other users/services) or data integrity and authentication services using digital signatures. It also allows users to cache the public keys (in the form of certificates) of their communicating peers.
Java keytool stores the keys and certificates in what is called a keystore. The Java keystore is implemented as a file by default. It protects private keys with a password.
Keytool also enables users to administer secret keys used in symmetric encryption/decryption (e.g. RSA, DES).
A Keytool keystore contains the private key and any certificates necessary to complete a chain of trust and establish the trustworthiness of the primary certificate.
All certificates in a Java keystore are associated with a unique alias, which will be used as a pointer to later perform any of the keytool operations to import, export, delete, and/or change certificates and keys.
Keytool Options
The various keytool options are listed below:
| KEYTOOL OPTIONS | DESCRIPTION |
| -delete | Deletes an entry from the Keystore |
| -exportcert | Exports a certificate from a Keystore |
| -genkeypair | Generates a key pair |
| -genseckey | Generates a secret key pair |
| -gencert | Generates a certificate from a certificate request |
| -importcert | Import a certificate or a certificate chain to keystore |
| -importpass | Imports a password |
| -importkeystore | Imports one or all entries from another keystore to a keystore |
| -keypasswd | Changes the key password of an entry in keystore |
| -list | Lists entries in a keystore |
| -printcert | Prints the content of a certificate |
| -printcertreq | Prints the content of a certificate request |
| -printcrl | Prints the content of a CRL file |
| -storepasswd | Changes the store password of a keystore |
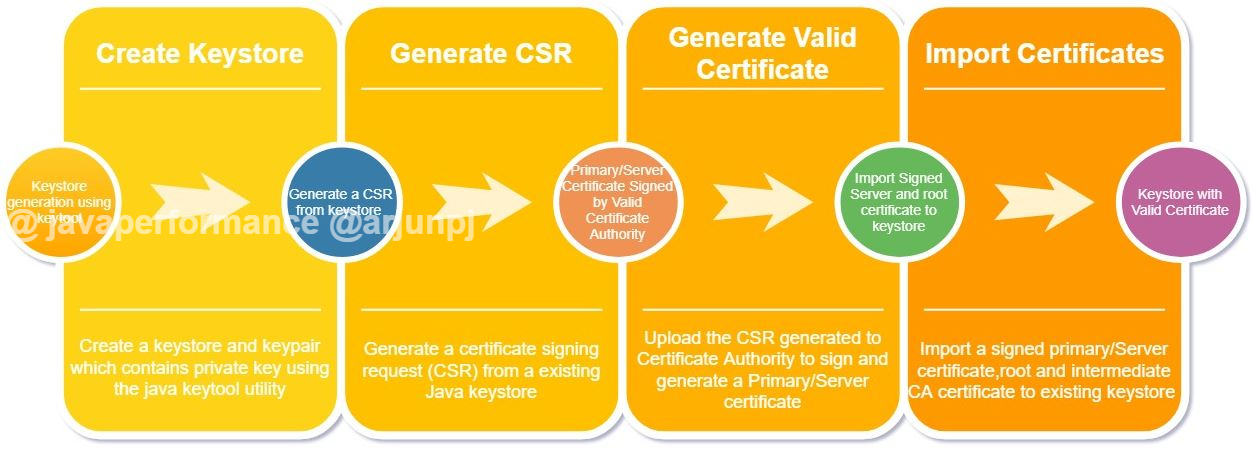
How to Process the Keystore, CSR, and the Signed Certificate

- Create a keystore that contains a private key
- Generate a CSR (Certificate Signing Request) from keystore
- Generate a signed primary/server certificate from the Certificate Authority
- Import the primary/server certificate, root, and intermediate CA certificates to keystore.
- Share the certificate or root certificates to the system that uses the SSL to communicate to your system/application.
Step 1. Create a Keystore Using the Keytool
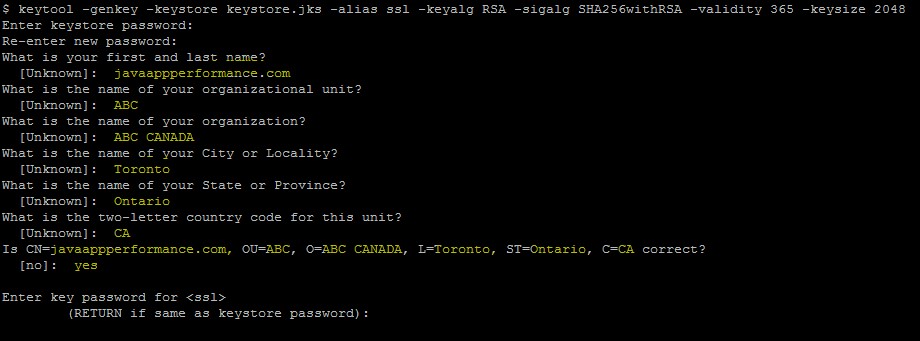
While we create a Java keystore, we will first create the .jks file that will initially only contain the private key using the keytool utility.
keytool -genkey -keystore keystore.jks -alias ssl -keyalg RSA -sigalg SHA256withRSA -validity 365 -keysize 2048-
-aliasis an option to mention an Alias Name for your key entry -
-keyalgspecifies the algorithm to be used to generate the key pair -
-keysizespecifies the size of each key to be generated -
-sigalgspecifies the algorithm that should be used to sign the self-signed certificate; this algorithm must be compatible withkeyalg. -
-validityspecifies the validity of the keystore that you want to create.
When you execute the command, we will be prompted with a question we need to answer to add the key details, such as common name (website/application dns name), organization, country, state, province, country code, etc. These are user-defined values. Also, it will prompt you to enter keystore and key password, which should be used in the future to read/write/modify the keystore.
As the keystore name is mentioned, keystore.jks, while creating the keystore.jks file, will be created in the current folder.
Use the command below to list the entries in keystore to view the content. We will be able to see the entered values reflected on the private key entries on the keystore.jks file.
keytool -list -v -keystore keystore.jks 
Step 2. Generate a CSR (Certificate Signing Request) From the Keystore
The next step is to create a Certificate Signing Request (CSR) from the created keystore to share with the Certificate Authority (CA) to sign and generate the primary/server certificate.
keytool -certreq -alias ssl -keystore keystore.jks -file javaappperfomance.csrWe need to pass the correct alias name and password, which we mentioned during the creation of the keystore to extract the certificate request.


Step 3. Generate a Signed Primary/Server Certificate From the Certificate Authority
Submit the generated CSR to any of the CA, which is supported by the SSL community to get the signed the Primary/Server certificate. The CA will be selected based on the organizations or your personnel selection.
Here is a list of the top ten Certificate Authorities in the world (according to Wikipedia):
| Rank | Issuer |
| 1 | Comodo |
| 2 | IdenTrust |
| 3 | Symantec |
| 4 | GoDaddy |
| 5 | GlobalSign |
| 6 | DigiCert |
| 7 | Certum |
| 8 | Entrust |
| 9 | Secom |
| 10 | Actalis |
Step 4. Import the Primary/Server Certificate, Root, and Intermediate CA Certificates to Keystore
Once the CA signed the certificate and share it with us, we need to import the certificate to the keystore for the private key entry we created.
The following keytool commands can be used to import the signed certificate to keystore; we should use the alias name that is the same as the alias name on the private key entry.
keytool -import -alias ssl -keystore keystore.jks -file javaappperfomance.crt keytool -import -trustcacerts -alias ssl -file javaappperfomance.crt -keystore keystore.jksThe second one is optional using -trustcacerts.
If the -trustcacerts option has been specified, additional certificates are considered for the chain of trust, namely the certificates in a file named "cacerts."
If the alias does not point to a key entry, then keytool assumes you are adding a trusted certificate entry. In this case, the alias should not already exist in the keystore. If the alias does already exist, then keytool outputs an error since there is already a trusted certificate for that alias and does not import the certificate.
If the alias points to a key entry, then keytool assumes you are importing a certificate reply.
The old chain can only be replaced if it is a valid keypass, the password used to protect the private key of the entry is supplied. If no password is provided, and the private key password is different from the keystore password, the user will be prompted for it.
Step 5. Import a Root or Intermediate CA Certificate to an Existing Java Keystore
keytool -import -trustcacerts -alias root -file entrust.cer -keystore keystore.jksEntrust(CA) is used as an example, File will be different and supplied by the Certificate Authority(CA) based on your CA.

To View/List the certificate we have added below command can be used
keytool -list -v -keystore keystore.jks Step 6. Share the Certificate or Root Certificates to the System
Next, you need to share the certificate or root certificates to system which use the SSL to communicate to your system/application.
As you have created a new private/public key for your DNS name, we need to share the certificate with any of the interfacing applications (Not Browser as it will be having CA root/intermediate on its list).
Important Commands for keytool
These commands can be used while we create, import, export, delete, and/or change certificate in a keystore.
First, generate a Java keystore and key pair:
keytool -genkey -alias aliasname -keyalg RSA -keystore keystore.jks -keysize 2048Then, generate a certificate signing request (CSR) for an existing Java keystore:
keytool -certreq -alias aliasname -keystore keystore.jks -file domainname.csrNext, generate a keystore and self-signed certificate:
keytool -genkey -keyalg RSA -alias selfsigned -keystore keystore.jks -storepass password -validity 360 -keysize 2048You can view or list the certificate; the command below can be used:
keytool -list -v -keystore keystore.jks Import a root or intermediate CA certificate to an existing Java keystore:
keytool -import -trustcacerts -alias root -file domainname.crt -keystore keystore.jksDelete a certificate from a Java keytool keystore:
keytool -delete -alias aliasname -keystore keystore.jksNext, change a Java keystore password:
keytool -storepasswd -new new_storepass -keystore keystore.jksLastly, export a certificate from a keystore:
keytool -export -alias aliasname -file filename.crt -keystore keystore.jksConclusion
The keytool utility is provided with any standard JDK/JRE distribution. The command keytool comes with several options to manage public/private security keys and certificates and store in a KeyStore file (<filename>.jks). A certificate is a digitally signed statement primarily used to verify to other users or services that the data has its integrity intact (not tampered) and comes from an authentic source that claims to have created and (digitally) signed it. The utility can also be used to administer secret keys and passphrase used in symmetric encryption/decryption. The article provided a step-by-step tutorial on how to generate KeyStore and CSR using the keytool utility command.
That's all for now. Hope you learned more about using the Java keytool command.
Published at DZone with permission of Arjun P Jathindramohan. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments