Managing Secrets for Automation Using Ansible Vault and Tower
Managing secrets is essential for all businesses. In this tutorial, let's go into how to encrypt your secrets or sensitive data using the Ansible Vault tool.
Join the DZone community and get the full member experience.
Join For FreeIn today's advanced technology, Managing secrets is essential for all businesses. Failing to manage the secrets under a tightly controlled security environment, may lead to worst consequences. In this tutorial, I am explaining how to encrypt your secrets or sensitive data using the Ansible Vault tool which is very useful for Automation.
Ansible Vault
Ansible is a configuration management tool from Redhat, which is a simple and powerful tool for infrastructure automation. During automation, it is important to hide sensitive data like API key, DB credentials, and server login credentials, etc, and exposing them is a threat to attack. Vault tool from Redhat Ansible provides the flexibility to encrypt these secrets in a very easy way.
Encrypt secrets using Ansible Vault
The following example will help you to understand how to encrypt secrets via ansible vault during automation. Let's create a role called manage-secret inside roles folder using ansible-galaxy command as below:
x
(ansible-venv) [test-user@linux-node dzone-ansible-secret]$ ls
inventory playbook-httpd-install.yml roles
(ansible-venv) [test-user@linux-node roles]$ ansible-galaxy init manage-secret
- Role manage-secret was created successfully
(ansible-venv) [test-user@linux-node dzone-ansible-secret]$ tree roles/manage-secret/
.
├── defaults
│ └── main.yml
├── files
├── handlers
│ └── main.yml
├── meta
│ └── main.yml
├── README.md
├── tasks
│ └── main.yml
├── templates
├── tests
│ ├── inventory
│ └── test.yml
└── vars
└── main.yml
8 directories, 8 files
create secret.yml inside defaults directory, with secret data that you want to encrypt. You can use any editor or directly use ansible-vault create secret.yml command.
x
secret
api_token"abc34ff-09fedf-oac5fc-ufh0ed-90defa"
licence_key"EERST36ENO43MOUNSL0SF24IUR"
To encrypt the secret, use encrypt key word along with ansible-vault command as shown below
x
(ansible-venv) [test-user@linux-node defaults]$ ansible-vault encrypt secret.yml
New Vault password:
Confirm New Vault password:
Encryption successful
now the content of the secret.yml file is in an encrypted format and difficult for readability.
xxxxxxxxxx
(ansible-venv) [test-user@linux-node defaults]$ cat secret.yml
$ANSIBLE_VAULT;1.1;AES256
64366334656464366234396134613266316239353236616164643661313938306164383935333832
6564653932383864363938386465663666323237343533650a643534376263363061343062303565
39643133336466333539663130303261343138323036656233613035313630383764343037643136
3366333462613861390a353065313931353330663765323639353936376433643266363933373163
37623663653432346564646532663566386632623432376431373037653063373434643931396339
38666132303236353531326632363733363530653263393434636531313131653633363932376337
65663736303838343239333631356538366334396535396466346461653534383432643539386337
32396466313366386162346264366435373135376139303031313463663762373536393437666436
65633837373966666637383435396663333337636331346232616434666531386266333364373431
35626235346639353331653134636265646662623038663364336232326563633039376163376232
323361376464643630373931343331633833
use below ansible-vault edit command, to update or modify the secrets by providing a decryption key in the command prompt.
x
(ansible-env) [test-user@linux-node defaults]$ ansible-vault edit secret.yml
Vault password:
ansible-vault view command is used to view the contents of the secret file.
Read Secrets in Ansible Playbook
To read the secrets, let's edit main.yml under tasks directory as below. Read parameters of secret.yml file in task using module include_vars: "defaults/secret.yml"
xxxxxxxxxx
---
# tasks file for manage-secret
nameRead secret file
include_vars"defaults/secret.yml"
namedisplay API Token
debug
msg"{{ secret.api_token }}"
namedisplay LICENCE Key"
debug
msg"{{ secret.licence_key }}"
Execute playbook as below and provide decryption key while prompts
x
(ansible-venv) [test-user@linux-node dzone-ansible-secret]$ ansible-playbook playbook-manage-secret.yml --ask-vault-pass
Vault password:
[WARNING]: No inventory was parsed, only implicit localhost is available
[WARNING]: provided hosts list is empty, only localhost is available. Note that the implicit localhost does not match 'all'
PLAY [DZone ansible-vault demo] *********************************************************************************
TASK [Gathering Facts] *********************************************************************************
ok: [localhost]
TASK [manage-secret : Read secret file] *********************************************************************************
ok: [localhost]
TASK [manage-secret : display API Token] *********************************************************************************
ok: [localhost] => {
"msg": "abc34ff-09fedf-oac5fc-ufh0ed-90defa"
}
TASK [manage-secret : display LICENCE Key] *********************************************************************************
ok: [localhost] => {
"msg": "EERST36ENO43MOUNSL0SF24IUR"
}
PLAY RECAP *********************************************************************************
localhost : ok=5 changed=0 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
But providing a password via terminal with a prompt is difficult while using automation and user may not be able to intervene to provide decryption key in command-line. Hence the alternate option for automation is, the decryption key can be read from the file. The below example shows, how the encryption key is read via file.
xxxxxxxxxx
(ansible-venv) [test-user@linux-node dzone-ansible-secret]$ ansible-playbook playbook-manage-secret.yml --vault-password-file /home/test-user/decrypt_key.txt
[WARNING]: No inventory was parsed, only implicit localhost is available
[WARNING]: provided hosts list is empty, only localhost is available. Note that the implicit localhost does not match 'all'
PLAY [DZone ansible-vault demo] *********************************************************************************
TASK [Gathering Facts] *********************************************************************************
ok: [localhost]
TASK [manage-secret : Read secret file] *********************************************************************************
ok: [localhost]
TASK [manage-secret : display API Token] *********************************************************************************
ok: [localhost] => {
"msg": "abc34ff-09fedf-oac5fc-ufh0ed-90defa"
}
TASK [manage-secret : display LICENCE Key] *********************************************************************************
ok: [localhost] => {
"msg": "EERST36ENO43MOUNSL0SF24IUR"
}
PLAY RECAP *********************************************************************************
localhost : ok=5 changed=0 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
But storing the decryption key in file is dangerous and vulnerable for the attack as anyone can read and can't be stored on git or any repository level. So the best way to overcome this problem is to use Ansible Tower.
Ansible Tower
Tower tool from Ansible Redhat provides a web-based user interface with enhanced features for efficient automation. Let's see how to create a vault credential to decrypt the secrets.
Decrypt Secret Using Ansible Tower Vault Credential
Click Credentials on the left navigation panel to create a new credential. Select Vault in credential type and enter your decryption key in Vault Password and save it.
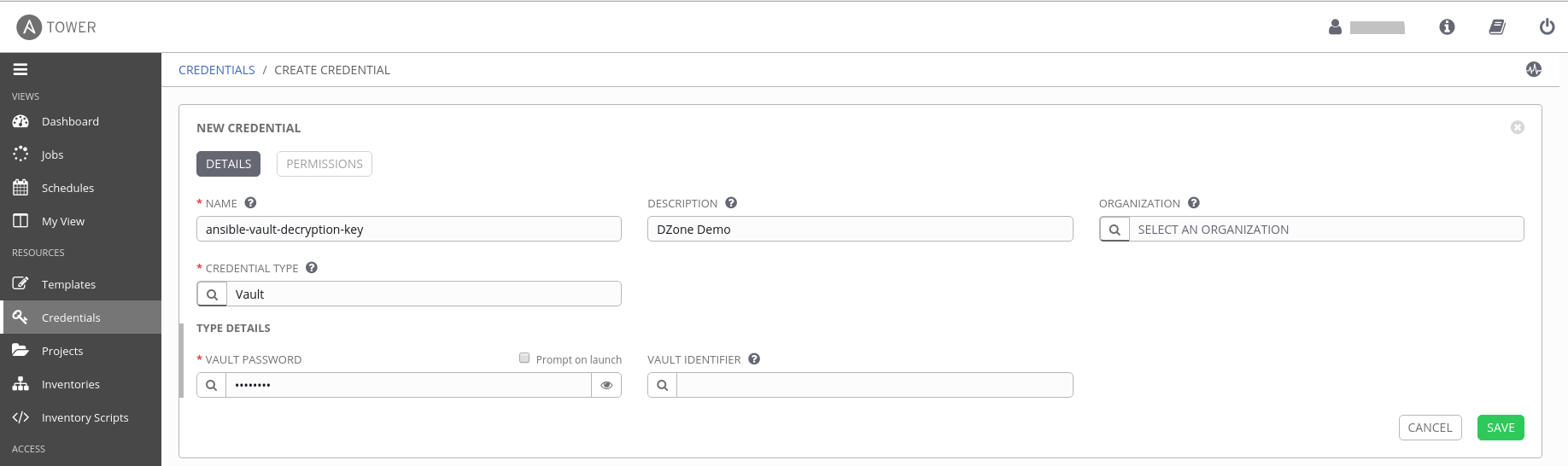
Now map this ansible-vault-decryption-key vault credential in Ansible Tower template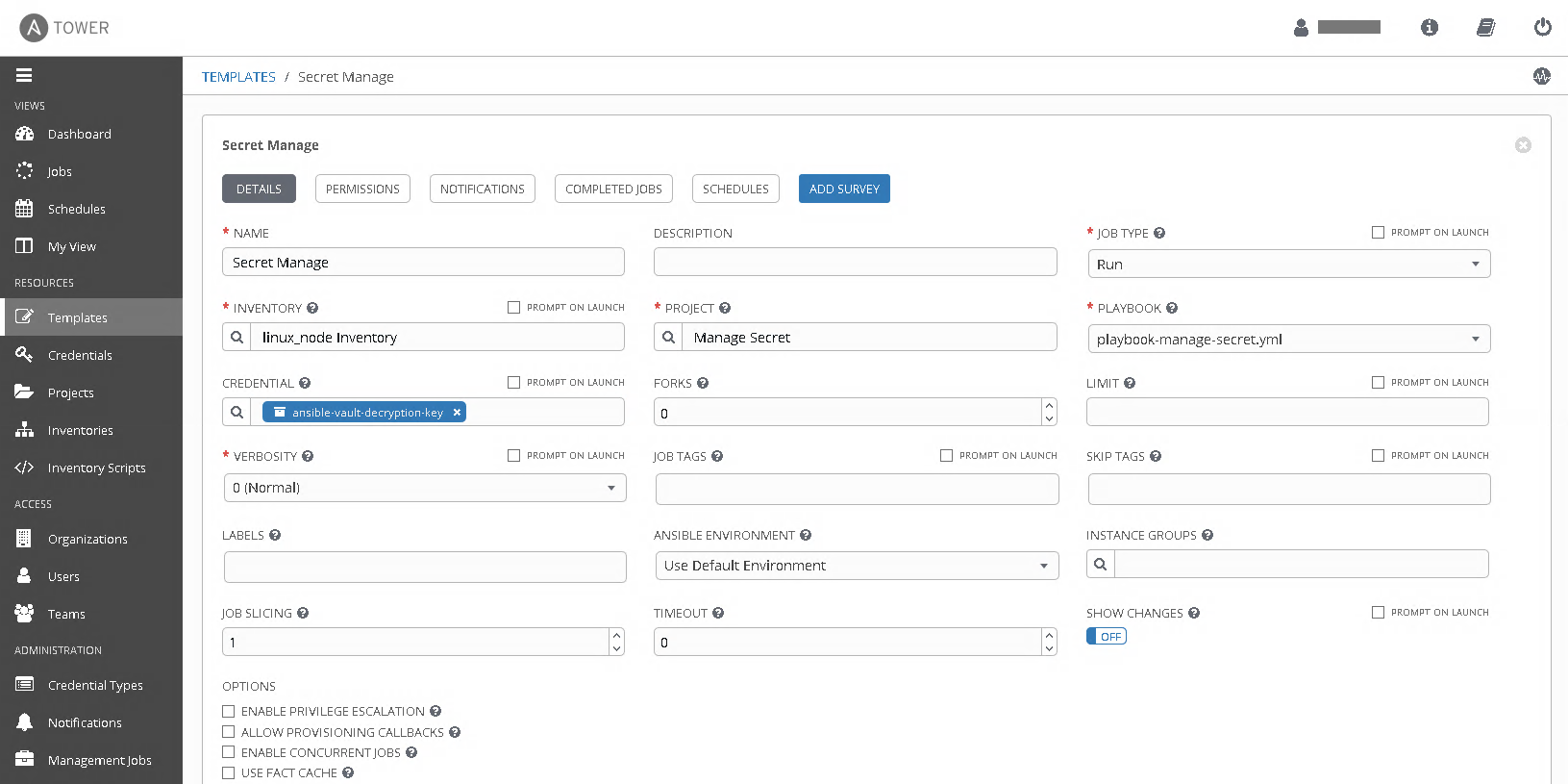
You will be able to see the decrypted information in Tower Job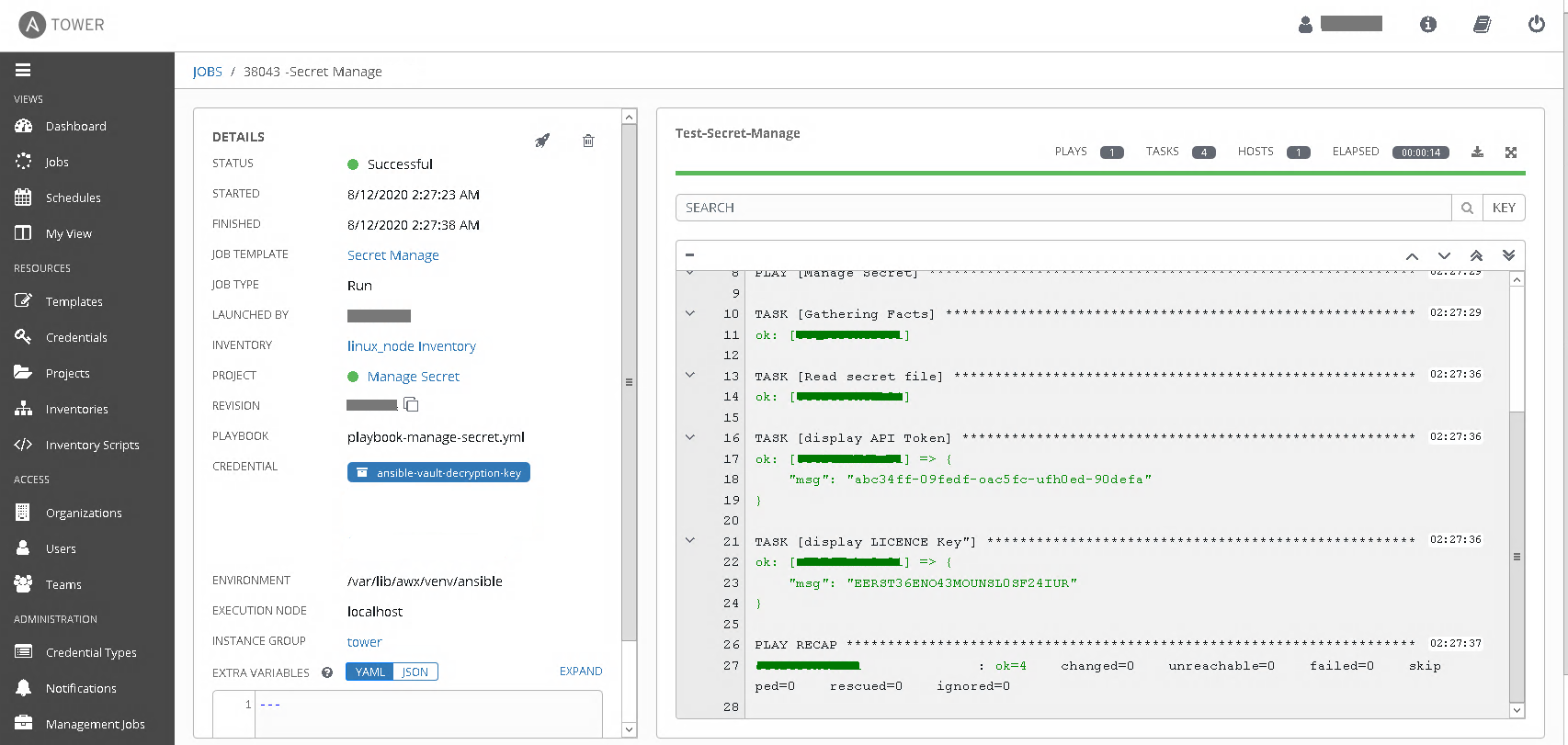
Summary
Ansible from Redhat is widely used as a configuration management tool for infrastructure automation such as provisioning servers, middleware deployment, and configurations, etc. While using the automated deployment and configuration process, it is important, not to expose the secret information outside. Ansible vault provides a more easy and simple way to encrypt secrets. In this tutorial, I have explained how we can manage these secrets using Ansible Vault and Tower.
Opinions expressed by DZone contributors are their own.

Comments