Restricting Access to EC2 Instances Based on Tags
Here's a refresher on the principle of least privilege and a code snippet that will help configure your EC2 instance security.
Join the DZone community and get the full member experience.
Join For FreeThe principle of least privilege is key when it comes to securing your infrastructure on AWS. For example, an engineer should only be able to control EC2 instances that are in scope for their day-to-day work. But how do you make sure an engineer is only allowed to …
- Start, stop, and terminate a specific instance?
- Create, attach, and delete specific volumes?
- Create, restore, and delete specific snapshots?
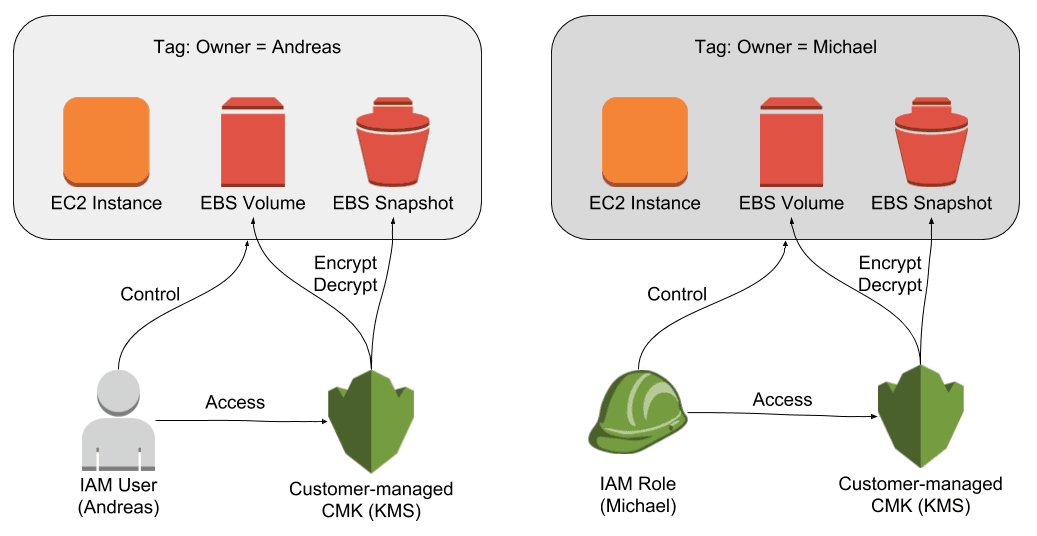
As illustrated in the following figure you can restrict access to EC2 instances, EBS volumes, and EBS snapshots by making use of …
- Tags attached to EC2 instances, EBS volumes, and EBS snapshots.
- An IAM role or user to authenticate an engineer.
- An IAM policy restricting access to the EC2 instances, EBS volumes, and EBS snapshots based on tags.
- A customer-managed CMK (KMS) to encrypt and decrypt data stored on EBS volumes and snapshots.
Attach the following IAM policy to a user or role to restrict access to instances, volumes, and snapshots based on a tag.
Replace <TAG_KEY> with the key you want to use for the tag (e.g. owner). Replace <TAG_VALUE> with an identifier of the user or role (e.g. andreas). Replace <KMS_KEY_ARN> with the ARN of the customer-managed CMK which only the user or role is allowed to use.
Note: I’ve added # comments to the IAM policy to explain the details. Please remove all # comments before making use of the policy. The JSON is not valid otherwise.
{
"Version": "2012-10-17",
"Statement": [
{
# Allow all actions we don't want to or cannot restrict by a tag.
"Effect": "Allow",
"Action": [
"ec2:AcceptReservedInstancesExchangeQuote",
"ec2:AcceptVpcEndpointConnections",
"ec2:AcceptVpcPeeringConnection",
"ec2:AllocateAddress",
"ec2:AllocateHosts",
"ec2:AssignIpv6Addresses",
"ec2:AssignPrivateIpAddresses",
"ec2:AssociateAddress",
"ec2:AssociateDhcpOptions",
"ec2:AssociateIamInstanceProfile",
"ec2:AssociateRouteTable",
"ec2:AssociateSubnetCidrBlock",
"ec2:AssociateVpcCidrBlock",
"ec2:AttachClassicLinkVpc",
"ec2:AttachInternetGateway",
"ec2:AttachNetworkInterface",
"ec2:AttachVpnGateway",
"ec2:AuthorizeSecurityGroupEgress",
"ec2:AuthorizeSecurityGroupIngress",
"ec2:BundleInstance",
"ec2:CancelBundleTask",
"ec2:CancelConversionTask",
"ec2:CancelExportTask",
"ec2:CancelImportTask",
"ec2:CancelReservedInstancesListing",
"ec2:CancelSpotFleetRequests",
"ec2:CancelSpotInstanceRequests",
"ec2:ConfirmProductInstance",
"ec2:CopyFpgaImage",
"ec2:CopyImage",
"ec2:CopySnapshot",
"ec2:CreateCustomerGateway",
"ec2:CreateDefaultSubnet",
"ec2:CreateDefaultVpc",
"ec2:CreateDhcpOptions",
"ec2:CreateEgressOnlyInternetGateway",
"ec2:CreateFlowLogs",
"ec2:CreateFpgaImage",
"ec2:CreateImage",
"ec2:CreateInstanceExportTask",
"ec2:CreateInternetGateway",
"ec2:CreateKeyPair",
"ec2:CreateLaunchTemplate",
"ec2:CreateLaunchTemplateVersion",
"ec2:CreateNatGateway",
"ec2:CreateNetworkAcl",
"ec2:CreateNetworkAclEntry",
"ec2:CreateNetworkInterface",
"ec2:CreateNetworkInterfacePermission",
"ec2:CreatePlacementGroup",
"ec2:CreateReservedInstancesListing",
"ec2:CreateRoute",
"ec2:CreateRouteTable",
"ec2:CreateSecurityGroup",
"ec2:CreateSpotDatafeedSubscription",
"ec2:CreateSubnet",
"ec2:CreateVpc",
"ec2:CreateVpcEndpoint",
"ec2:CreateVpcEndpointConnectionNotification",
"ec2:CreateVpcEndpointServiceConfiguration",
"ec2:CreateVpcPeeringConnection",
"ec2:CreateVpnConnection",
"ec2:CreateVpnConnectionRoute",
"ec2:CreateVpnGateway",
"ec2:DeleteCustomerGateway",
"ec2:DeleteDhcpOptions",
"ec2:DeleteEgressOnlyInternetGateway",
"ec2:DeleteFlowLogs",
"ec2:DeleteFpgaImage",
"ec2:DeleteInternetGateway",
"ec2:DeleteKeyPair",
"ec2:DeleteLaunchTemplate",
"ec2:DeleteLaunchTemplateVersions",
"ec2:DeleteNatGateway",
"ec2:DeleteNetworkAcl",
"ec2:DeleteNetworkAclEntry",
"ec2:DeleteNetworkInterface",
"ec2:DeleteNetworkInterfacePermission",
"ec2:DeletePlacementGroup",
"ec2:DeleteRoute",
"ec2:DeleteRouteTable",
"ec2:DeleteSecurityGroup",
"ec2:DeleteSpotDatafeedSubscription",
"ec2:DeleteSubnet",
"ec2:DeleteVpc",
"ec2:DeleteVpcEndpointConnectionNotifications",
"ec2:DeleteVpcEndpointServiceConfigurations",
"ec2:DeleteVpcEndpoints",
"ec2:DeleteVpcPeeringConnection",
"ec2:DeleteVpnConnection",
"ec2:DeleteVpnConnectionRoute",
"ec2:DeleteVpnGateway",
"ec2:DeregisterImage",
"ec2:DescribeAccountAttributes",
"ec2:DescribeAddresses",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeBundleTasks",
"ec2:DescribeClassicLinkInstances",
"ec2:DescribeConversionTasks",
"ec2:DescribeCustomerGateways",
"ec2:DescribeDhcpOptions",
"ec2:DescribeEgressOnlyInternetGateways",
"ec2:DescribeElasticGpus",
"ec2:DescribeExportTasks",
"ec2:DescribeFlowLogs",
"ec2:DescribeFpgaImageAttribute",
"ec2:DescribeFpgaImages",
"ec2:DescribeHostReservationOfferings",
"ec2:DescribeHostReservations",
"ec2:DescribeHosts",
"ec2:DescribeIamInstanceProfileAssociations",
"ec2:DescribeIdFormat",
"ec2:DescribeIdentityIdFormat",
"ec2:DescribeImageAttribute",
"ec2:DescribeImages",
"ec2:DescribeImportImageTasks",
"ec2:DescribeImportSnapshotTasks",
"ec2:DescribeInstanceAttribute",
"ec2:DescribeInstanceCreditSpecifications",
"ec2:DescribeInstanceStatus",
"ec2:DescribeInstances",
"ec2:DescribeInternetGateways",
"ec2:DescribeKeyPairs",
"ec2:DescribeLaunchTemplateVersions",
"ec2:DescribeLaunchTemplates",
"ec2:DescribeMovingAddresses",
"ec2:DescribeNatGateways",
"ec2:DescribeNetworkAcls",
"ec2:DescribeNetworkInterfaceAttribute",
"ec2:DescribeNetworkInterfacePermissions",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribePlacementGroups",
"ec2:DescribePrefixLists",
"ec2:DescribeRegions",
"ec2:DescribeReservedInstances",
"ec2:DescribeReservedInstancesListings",
"ec2:DescribeReservedInstancesModifications",
"ec2:DescribeReservedInstancesOfferings",
"ec2:DescribeRouteTables",
"ec2:DescribeScheduledInstanceAvailability",
"ec2:DescribeScheduledInstances",
"ec2:DescribeSecurityGroupReferences",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSnapshotAttribute",
"ec2:DescribeSnapshots",
"ec2:DescribeSpotDatafeedSubscription",
"ec2:DescribeSpotFleetInstances",
"ec2:DescribeSpotFleetRequestHistory",
"ec2:DescribeSpotFleetRequests",
"ec2:DescribeSpotInstanceRequests",
"ec2:DescribeSpotPriceHistory",
"ec2:DescribeStaleSecurityGroups",
"ec2:DescribeSubnets",
"ec2:DescribeTags",
"ec2:DescribeVolumeAttribute",
"ec2:DescribeVolumeStatus",
"ec2:DescribeVolumes",
"ec2:DescribeVolumesModifications",
"ec2:DescribeVpcAttribute",
"ec2:DescribeVpcClassicLink",
"ec2:DescribeVpcClassicLinkDnsSupport",
"ec2:DescribeVpcEndpointConnectionNotifications",
"ec2:DescribeVpcEndpointConnections",
"ec2:DescribeVpcEndpointServiceConfigurations",
"ec2:DescribeVpcEndpointServicePermissions",
"ec2:DescribeVpcEndpointServices",
"ec2:DescribeVpcEndpoints",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:DescribeVpnConnections",
"ec2:DescribeVpnGateways",
"ec2:DetachClassicLinkVpc",
"ec2:DetachInternetGateway",
"ec2:DetachNetworkInterface",
"ec2:DetachVpnGateway",
"ec2:DisableVgwRoutePropagation",
"ec2:DisableVpcClassicLink",
"ec2:DisableVpcClassicLinkDnsSupport",
"ec2:DisassociateAddress",
"ec2:DisassociateIamInstanceProfile",
"ec2:DisassociateRouteTable",
"ec2:DisassociateSubnetCidrBlock",
"ec2:DisassociateVpcCidrBlock",
"ec2:EnableVgwRoutePropagation",
"ec2:EnableVolumeIO",
"ec2:EnableVpcClassicLink",
"ec2:EnableVpcClassicLinkDnsSupport",
"ec2:GetConsoleOutput",
"ec2:GetConsoleScreenshot",
"ec2:GetHostReservationPurchasePreview",
"ec2:GetLaunchTemplateData",
"ec2:GetPasswordData",
"ec2:GetReservedInstancesExchangeQuote",
"ec2:ImportImage",
"ec2:ImportInstance",
"ec2:ImportKeyPair",
"ec2:ImportSnapshot",
"ec2:ImportVolume",
"ec2:ModifyFpgaImageAttribute",
"ec2:ModifyHosts",
"ec2:ModifyIdFormat",
"ec2:ModifyIdentityIdFormat",
"ec2:ModifyImageAttribute",
"ec2:ModifyInstanceAttribute",
"ec2:ModifyInstanceCreditSpecification",
"ec2:ModifyInstancePlacement",
"ec2:ModifyLaunchTemplate",
"ec2:ModifyNetworkInterfaceAttribute",
"ec2:ModifyReservedInstances",
"ec2:ModifySnapshotAttribute",
"ec2:ModifySpotFleetRequest",
"ec2:ModifySubnetAttribute",
"ec2:ModifyVolume",
"ec2:ModifyVolumeAttribute",
"ec2:ModifyVpcAttribute",
"ec2:ModifyVpcEndpoint",
"ec2:ModifyVpcEndpointConnectionNotification",
"ec2:ModifyVpcEndpointServiceConfiguration",
"ec2:ModifyVpcEndpointServicePermissions",
"ec2:ModifyVpcPeeringConnectionOptions",
"ec2:ModifyVpcTenancy",
"ec2:MonitorInstances",
"ec2:MoveAddressToVpc",
"ec2:PurchaseHostReservation",
"ec2:PurchaseReservedInstancesOffering",
"ec2:PurchaseScheduledInstances",
"ec2:RegisterImage",
"ec2:RejectVpcEndpointConnections",
"ec2:RejectVpcPeeringConnection",
"ec2:ReleaseAddress",
"ec2:ReleaseHosts",
"ec2:ReplaceIamInstanceProfileAssociation",
"ec2:ReplaceNetworkAclAssociation",
"ec2:ReplaceNetworkAclEntry",
"ec2:ReplaceRoute",
"ec2:ReplaceRouteTableAssociation",
"ec2:ReportInstanceStatus",
"ec2:RequestSpotFleet",
"ec2:RequestSpotInstances",
"ec2:ResetFpgaImageAttribute",
"ec2:ResetImageAttribute",
"ec2:ResetInstanceAttribute",
"ec2:ResetNetworkInterfaceAttribute",
"ec2:ResetSnapshotAttribute",
"ec2:RestoreAddressToClassic",
"ec2:RevokeSecurityGroupEgress",
"ec2:RevokeSecurityGroupIngress",
"ec2:RunScheduledInstances",
"ec2:UnassignIpv6Addresses",
"ec2:UnassignPrivateIpAddresses",
"ec2:UnmonitorInstances",
"ec2:UpdateSecurityGroupRuleDescriptionsEgress",
"ec2:UpdateSecurityGroupRuleDescriptionsIngress"
],
"Resource": "*"
},
{
# Allow launching an instance, but only if the tag is set.
"Effect": "Allow",
"Action": "ec2:RunInstances",
"Resource": [
"arn:aws:ec2:*:*:volume/*",
"arn:aws:ec2:*:*:instance/*"
],
"Condition": {
"StringEquals": {
"aws:RequestTag/<TAG_KEY>": "<TAG_VALUE>"
}
}
},
{
# Allow actions we can't restrict by using tags.
"Effect": "Allow",
"Action": "ec2:RunInstances",
"NotResource": [
"arn:aws:ec2:*:*:volume/*",
"arn:aws:ec2:*:*:instance/*"
]
},
{
# Allow creating a volume, but only if the tag is set.
"Effect": "Allow",
"Action": "ec2:CreateVolume",
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:RequestTag/<TAG_KEY>": "<TAG_VALUE>"
}
}
},
{
# Allow creating tags only when creating a volume, launching an instance, or creating a snapshot.
"Effect": "Allow",
"Action": [
"ec2:CreateTags"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"ec2:CreateAction": [
"CreateVolume",
"RunInstances",
"CreateSnapshot"
]
}
}
},
{
# Allow actions when the resource is tagged.
"Effect": "Allow",
"Action": [
"ec2:StartInstances",
"ec2:StopInstances",
"ec2:RebootInstances",
"ec2:TerminateInstances",
"ec2:CreateTags",
"ec2:DeleteTags",
"ec2:AttachVolume",
"ec2:DetachVolume",
"ec2:DeleteVolume",
"ec2:DeleteSnapshot"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"ec2:ResourceTag/Owner": "<TAG_VALUE>"
}
}
},
{
# Allow creating a snapshot, but only if the tag is set.
"Effect": "Allow",
"Action": "ec2:CreateSnapshot",
"Resource": [
"arn:aws:ec2:*:*:snapshot/*"
],
"Condition": {
"StringEquals": {
"aws:RequestTag/<TAG_KEY>": "<TAG_VALUE>"
}
}
},
{
# Allow creating a snapshot, but only if volume matches the tag.
"Effect": "Allow",
"Action": "ec2:CreateSnapshot",
"Resource": [
"arn:aws:ec2:*:*:volume/*"
],
"Condition": {
"StringEquals": {
"ec2:ResourceTag/Owner": "<TAG_VALUE>"
}
}
},
{
# Grant access to the customer-managed CMK.
"Effect": "Allow",
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "<KMS_KEY_ARN>"
}
]
}As the IAM policy references a tag and a customer-managed CMK, it is necessary to use a separate policy per user or role.
Why do we need to use a customer-managed CMK? Because it is not possible to restrict who can restore an EBS snapshot by using tags. Therefore, any engineer could access the data stored on any snapshot. Encrypting all volumes and snapshots with a customer-managed CMK (KMS) is a workaround allowing you to control very fine-granular which engineers can access data stored on volumes and snapshots.
It is also important to note, that it is not all action support conditions by tags. For example, it is not possible to restrict engineers from attaching a networking interface (ec2:AttachNetworkInterface) to any of the instances. If you want to be able to isolate your resources without any limitations, choose a multi-account strategy instead.
For details about IAM policies for EC2 go to the official AWS Documentation or our Complete IAM Reference.
Published at DZone with permission of Andreas Wittig. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments