Setting Up a VPN Connection Between Alibaba Cloud and GCP Using VPN Gateway
Take a look at this tutorial that gives you instructions on how to build a secure VPN connection with Alibaba Cloud and GCP.
Join the DZone community and get the full member experience.
Join For FreeA virtual private network (VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running across the VPN may, therefore, benefit from the functionality, security, and management of the private network.
This guide walks you through the process of configuring a VPN Gateway in Alibaba Cloud for integration with the Google Cloud VPN service.
This information is only provided as an example. If utilizing this guidance to configure your Alibaba Cloud VPN Gateway implementation, be sure to substitute the correct IP information for your environment.
Prerequisites
- An Alibaba Cloud Account. If you don't have an account yet, register here.
- A Google Cloud Account.
Topology
This guide will describe the VPN topology, a site-to-site route-based IPsec VPN tunnel configuration.
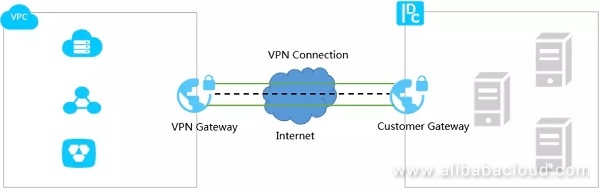
Overview
The configuration samples in this tutorial include numerous value substitutions provided for the purposes of example only. Any references to IP addresses, device IDs, shared secrets or keys, account information or project names should be replaced with the appropriate values for your environment when following this guide.
This guide is intended to assist in the creation of IPsec connectivity to the Google Cloud. The following is a high-level overview of the configuration process which will be covered:
- Configuring the VPN Gateway at Alibaba Cloud
- Configuring the Google Cloud Platform VPN
- Setting up the VPN Connection
- Connecting to GCP
- Testing the tunnel
The IPsec connectivity will utilize the pre-shared key set generated by you at Alibaba Cloud and GCP for authentication. We will be using ESP in Tunnel mode with authentication.
Getting Started
The first step is to establish the base networking environment in Alibaba Cloud. The basis of networking in Alibaba Cloud is the Virtual Private Cloud (VPC). Alibaba Cloud provides various documentation and guides for getting started with our networking products. The basic concepts to understand are:
- Virtual Private Cloud – Customer-defined private network space in Alibaba Cloud.
- VPN Gateway – The VPN concentrator on the Alibaba Cloud side of the VPN connection.
IPsec Parameters
For the IPsec configuration, the following details will be used to set up the VPN. Other parameters are assumed to take the default values.
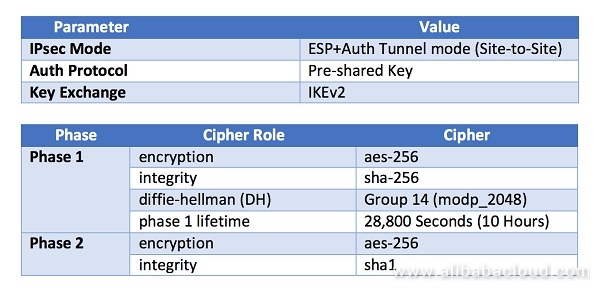
Configurations: Alibaba Cloud
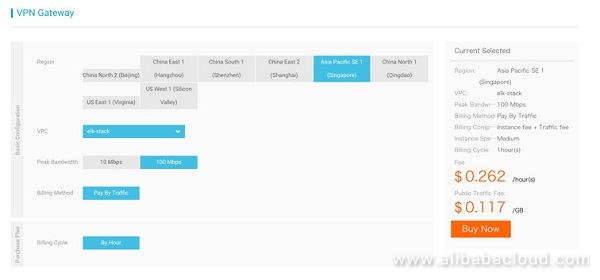
Set Up VPN Gateway
Purchase a new VPN Gateway. Click on Create VPN Gateway under the VPN Gateway. Select the bandwidth that makes sense for the use case. If you are not sure about the bandwidth, start with a smaller one so that I can be upgraded later. The VPC that will be used needs to be selected at this point.
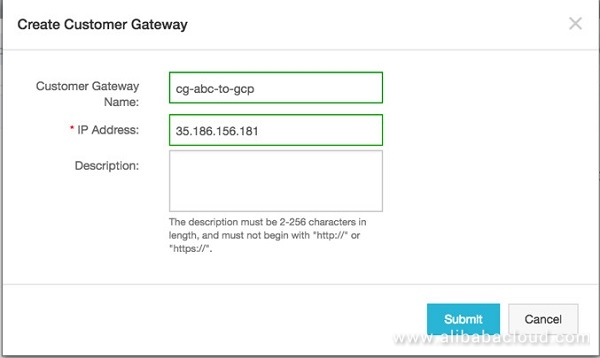
Set Up Customer Gateway
Once the VPN Gateway is set up, the next step is to set up the customer gateway that defines the public endpoint on the customer side. The GCP public IP will be used to set up the customer gateway.
Set Up VPN Tunnel
Once the VPN gateway and Customer gateway is done, set up the VPN connection with the parameters mentioned in IPSec Parameters. This setup will require the GCP side network details and set a Pre-Shared Key (PSK). Make sure the same settings are used when setting the VPN gateway at GCP side.
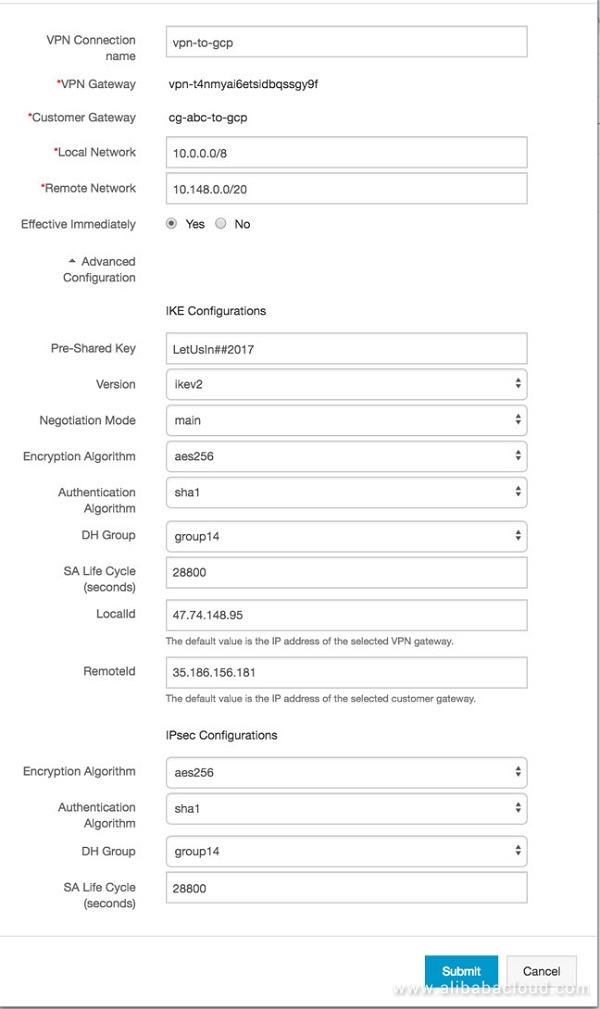
Configurations: GCP
In the Google Cloud Platform Developers Console, select the project into which the VPN will be deployed, or create a new project. To view the current network configuration for the project, select Networking from the main services menu in the Developer Console.
In GCP, all projects start with a single network named default at the time of creation. The default network is configured with a private IP space and a set of base firewall rules. The default network provides a sufficient starting point for creating a site-to-site IPsec VPN.
This section will configure the VPN endpoint on the Google Cloud side.
Select VPN from the Networking option
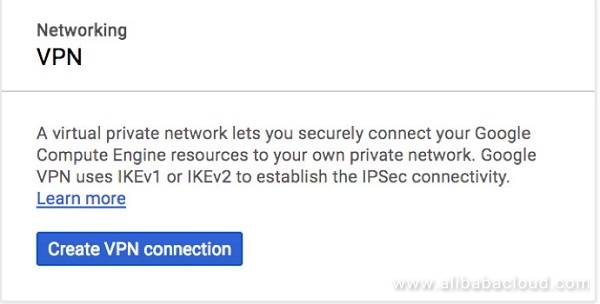
The VPN has several user configurable properties:
- Name: A representative name for the VPN connection (must be lowercase)
- Description: Free-form text describing the gateway (optional)
- Network: The network to which the VPN gateway will be attached
- Region: The region into which the VPN gateway will be deployed
- IP address: The static public IP address which will be assigned to the VPN gateway
Create a New Static IP
A Public IP is required for the VPN end from Alibaba Cloud to connect to GCP. This can be created by allocating a static IP at GCP side.
Create the VPN Gateway
The VPN gateway will launch a 99.9% available gateway that will be used to connect to the VPN gateway at Alibaba Cloud side. The Cloud VPN can be launched from the Networking section. This section will require us to input the public IP and the CIDR range of the network configured at Alibaba Cloud end. Also, ensure that the same PSK is input while configuring the gateway.
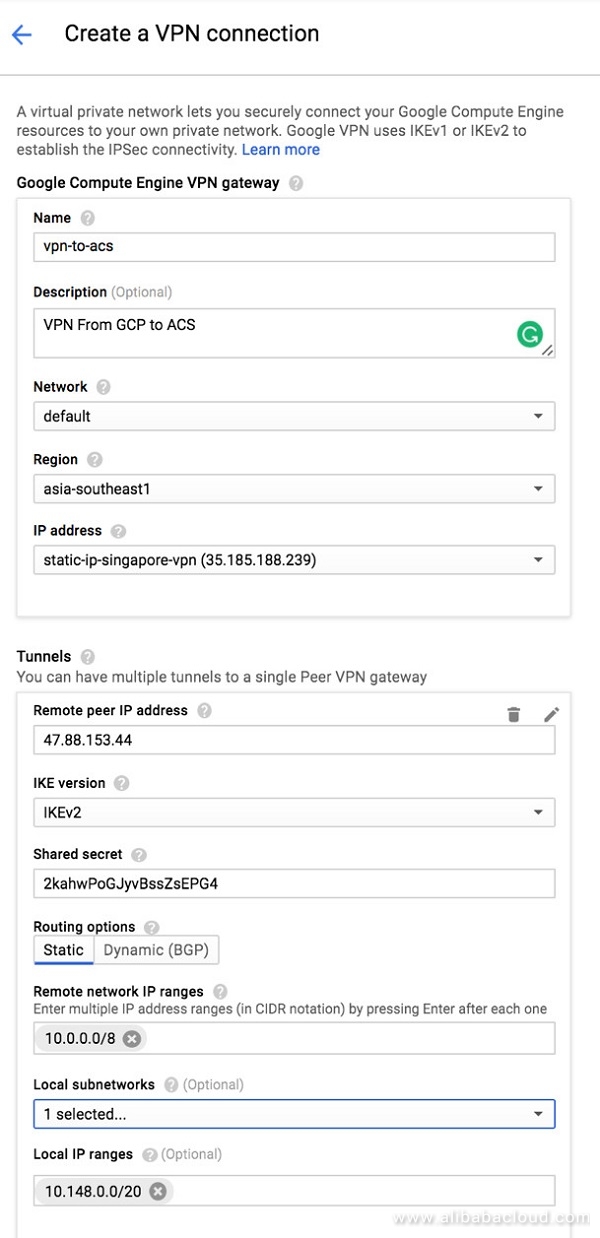
VPN Status
Once the VPN is setup, make sure that the VPN connects (ensuring that the strongswan endpoint at Alibaba Cloud is already started). Click on View under Logs to troubleshoot in case the VP status turns red.
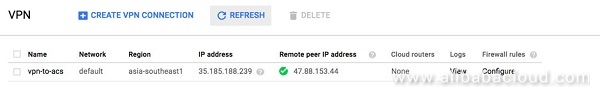
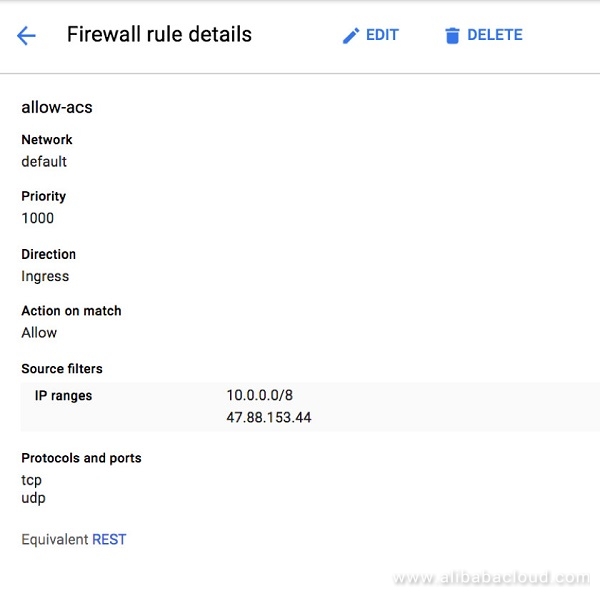
Firewall Rules
Setup the Firewall rules to allow network traffic if this was not prompted to be changed while the VPN was set. Ensure the CIDR range from the Alibaba Cloud VPC is mentioned here to be enabled.
Testing the Tunnel
With the site-to-site VPN online the tunnel is now ready for testing. To test, create virtual machines in both Alibaba Cloud and Google Compute Engine. Instructions for creating ECS virtual machines can be found on this guide. To learn how to create virtual machines in Google Compute Engine, visit GCP's Getting Started Guide.
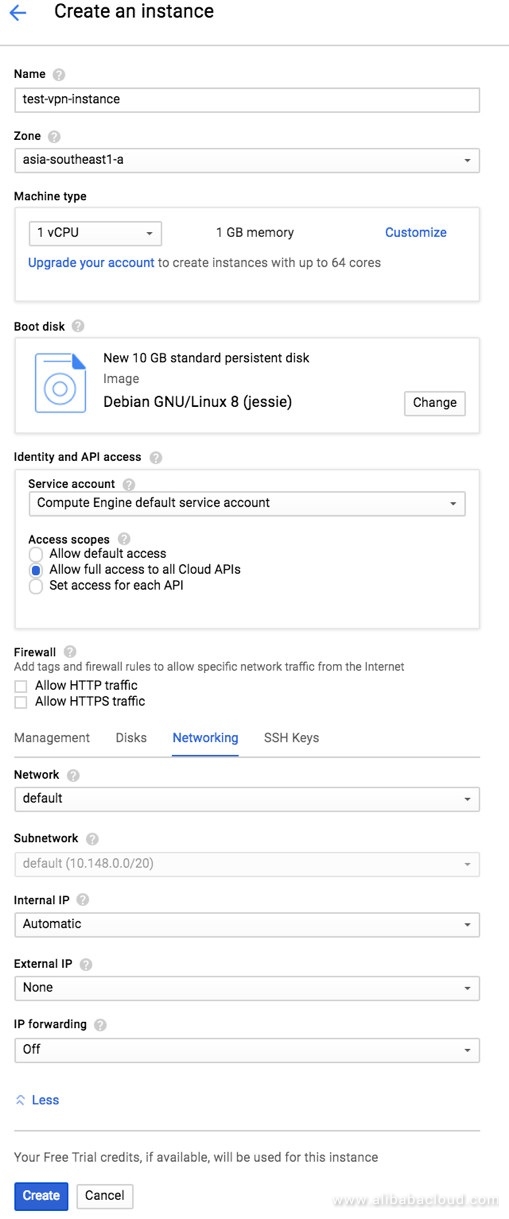
Create a Test Compute Engine
A compute engine at GCP side is required us to test the end to end networking. Make sure the launched instance does not have a public IP.
Check the VM Status
Make sure the ComputeEngine is up and running and correctly displays the internal IP.

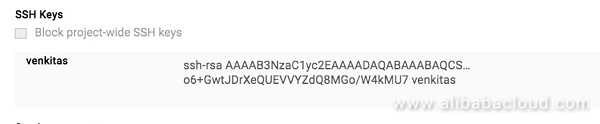
Create the SSH Keys
At the Alibaba Cloud side, create the SSH keys that can be used to login to the GCP Compute Engine. Note the username needs to be changed to fit the current setup. Do note that GCP doesn't support using root login unless configured manually to do so.
Create the Keys:
ssh-keygen -t rsa -f ~/.ssh/ssh-gcp-venkitas -C venkitasEnable Access
chmod 400 ~/.ssh/ssh-gcp-venkitasOutput the Key Contents
cat ~/.ssh/ssh-gcp-venkitas.pubSet the above SSH keys under the earlier created Compute Engine.
Once the key is set Ensure you can ping the Compute Engine at GCP Side.
ping https://www.linkedin.com/redir/invalid-link-page?url=10%2e148%2e0%2e2 #Private IP of GCPConnect to the GCP Compute Engine via the VPN Tunnel
ssh -i ~/.ssh/ssh-gcp-venkitas venkitas@10.148.0.2Conclusion
Setting up a VPN between the two major cloud providers allow the end user to have the best of both worlds. It is also one of the simplest ways for you to adopt a multi-cloud strategy for your enterprise.
With this setup, users can leverage the stronger China presence enjoyed by Alibaba Cloud while tapping into the big data functionalities provided by Google Cloud.
Further Reading
Alibaba Cloud ECS
GCP VPN
Published at DZone with permission of Leona Zhang. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments