Stay Safe on GitHub: Security Practices to Follow
Here are eight security practices that GitHub users can follow to stay safe and protect their code! Read on!
Join the DZone community and get the full member experience.
Join For FreeGitHub is undoubtedly the largest and most popular social development platform in the world. According to its 2019 State of the Octoverse Report, GitHub is home to over 40 million, and the community keeps expanding every day.
As developers in this deeply interconnected community use open source code to build software, Github security should be a top priority. This is because extensive code re-use increases the risk of distributing vulnerabilities from one dependency or repository to another. As such, every contributor should focus on creating a secure development environment.
Here are eight security practices that GitHub users can follow to stay safe and protect their code:
Strengthen Access Controls
Implementing proper access control is one of the best practices for enhancing security, not only on GitHub but in every other environment where code security is imperative.
GitHub offers several options that users can employ to reduce the risk of improper exposure. But to start with, it is important to employ the least privilege model where users are only granted necessary permissions.
Here are some basic access control guidelines that you should follow:
- Restrict the creation of repositories to prevent users from exposing organization information in public repositories.
- Enable branch protection and status checks to ensure users can merge commits or manipulate branches safely.
- Allow or disallow forking private repositories to ensure users do not expose or share organizational code with unauthorized parties.
- Revoke access for all inactive users who are no longer part of the contributors.
- Review access rights to your GitHub projects periodically.
- Ensure users do not share GitHub accounts or passwords.
- Ensure every contributor uses two-factor authentication on their account.
- Rotate personal access tokens and SSH keys
Never Store Credentials in Your GitHub Files
Leaking secrets to your GitHub repositories, either through code, configuration files, or commit messages, provides a gateway for attacks.
To prevent adding sensitive data into your repository, consider using secret management tools like git-secrets or vault. These tools scan your codebase and break builds whenever sensitive information is detected in your code or configuration files.
In case you realize sensitive information has leaked in your GitHub repository, you should remove it immediately. However, GitHub keeps a history of all commits in your repo, so deleting the data is not enough. You will need to purge the files from your GitHub repository history.
For enhanced security, an important step would be invalidating all secrets (passwords and tokens) that were leaked to the public.
Enable Security Alerts for Vulnerable Dependencies
As GitHub users work on more projects, it becomes hard to secure the increasing number of dependencies. Luckily, GitHub provides automatic security alerts for vulnerable dependencies detected in your repository.
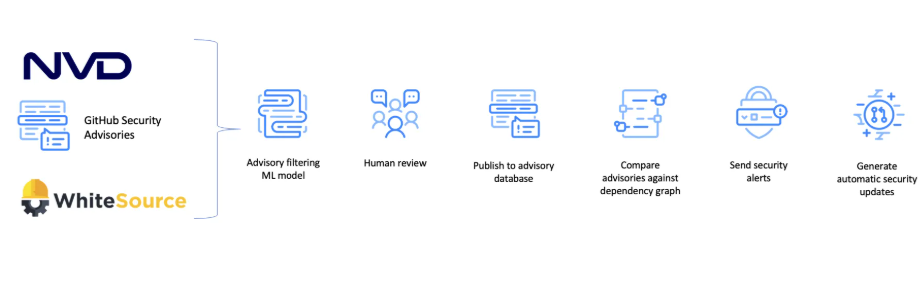
As illustrated above, GitHub security alerts are powered by the National Vulnerability Database (NVD), GitHub Security Advisories, and the WhiteSource Vulnerability Database - which provides vulnerability data for over 200 languages.
With real-time security alerts on GitHub, it will be easier to use open source libraries in a safe manner.
Validate GitHub Applications
The GitHub marketplace contains hundreds of applications written by third-party developers and organizations. It is therefore important to carefully validate every application you add to your GitHub repositories. Make it a norm to do the following when installing GitHub apps:
- Enforce the principle of least privilege. Never grant applications greater access rights than they require.
- Always question the access rights or permissions an application requests. Consider the kind of damage it can cause when given that level of access.
- Perform a background check to ensure the organization or developer behind an application is legitimate and credible enough before granting them access to your GitHub.
- Validate how robust is the application’s security posture. In case they suffer a breach, you might also be a victim of the attack
An application is only as secure as its weakest link. The same applies to GitHub repositories. So, before giving an application access to your repositories, ensure you trust it and that its worthy of the access levels it requests.
Audit All Code Imports Into GitHub
It is common for developers to import external code into GitHub. Every time you import a project, consider performing a full audit of the source code. While this may seem like a trivial exercise, especially for smaller projects, there are chances that you might introduce security vulnerabilities into your repositories.
Another risk inherent in imported code is that it may contain sensitive information such as credentials, which, if stored in GitHub files, pose another security risk. Auditing code before pushing it into GitHub can help reveal these security loopholes.
Do not just assume that the imported code is safe since it was in a closed environment; it might end up causing harm once it reaches your GitHub codebase.
Use Automatic Static Source Code Analysis for Your Repos
There are several third-party tools that you can use to analyze your repository for security vulnerabilities. One such tool is WhiteSource Bolt, a tool that’s freely available in the GitHub marketplace.
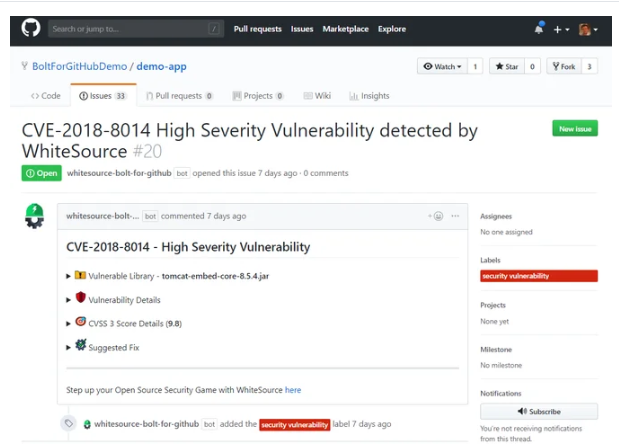
WhiteSource Bolt scans your repos to detects vulnerabilities in all open source components. It also provides detailed vulnerability information and suggests fixes for immediate remediation.
Using these open source analysis tools goes a long way to keeping your GitHub repositories secure.
Pick the Right GitHub Offering for Your Organizational Needs
Most organizations have regulations that restrict their development teams from using social development platforms such as GitHub, where other parties can access their source code. This is particularly common in government departments and financial institutions.
If you operate in such a tightly regulated environment, consider using GitHub Enterprise that allows in-premise hosting of GitHub repositories. The enterprise package is more secure as it allows internal development teams to access all projects without worrying about other users on GitHub.
Embrace an All-Round Security Policy for Your Projects
Security is a collective responsibility. If you’re working as a team, it is vital to implement a security policy that all stakeholders should follow. Ideally, you should bring the security and development teams together right from the planning stages to ensure they work together in sync. This way, it will be easier to enforce security controls during development.
If a team member becomes sloppy with sensitive information such as passwords, they might compromise the entire repository. With a security policy that applies to all repositories within the organization, developers will have a secure mindset in every project.
Additionally, document a clear process that team members can follow to report and resolve security issues within your repositories.
Conclusion
Every developer should focus on protecting their code and staying safe on GitHub to contribute to a secure development platform. By following the above practices, it’s achievable.
You only need to implement proper authentication and access controls while taking advantage of GitHub’s native security features. Additionally, integrate additional tools that strengthen your security in your development workflow.
You can also check the GitHub business security and GitHub security documentation sections of their platform for additional information on how to stay safe and protect your code on GitHub.
Opinions expressed by DZone contributors are their own.

Comments