System Hardening Standards and Best Practices With Chef
Explore what system hardening is, why it's needed, its benefits, and how Chef enables DevSecOps teams to harden heterogeneous systems with speed and ease.
Join the DZone community and get the full member experience.
Join For FreeIf you have anything to do with IT infrastructure, operations management, or DevOps, you've certainly come across the term "system hardening." While system hardening seems like a regular everyday activity in large IT teams with diverse infrastructure, the use and benefits cover a wide range of functions that secure your systems.
This blog explores what system hardening is, why it's needed, its benefits, and how Chef enables DevSecOps teams to harden heterogeneous systems with speed and ease.
What Is System Hardening?
System hardening is a method of preventing cyberattacks by reducing vulnerabilities in servers, applications, firmware, and other network-exposed systems. System hardening is achieved with the help of infrastructure and security management tools that help audit all systems, detect potential attack vectors, and minimize the attack surface.
Given the impact of cybersecurity attacks on organizations, system hardening has become a strategic defense against bad actors by closing system loopholes that attackers frequently use to exploit systems and gain access to sensitive data.
Some critical activities associated with system hardening include:
Deleting or disabling systems that are no longer in use
Limiting permissions
Removing superfluous applications, ports, features, or user accounts
Monitoring vulnerabilities
Ideally, running vulnerability scans is a great place to start since they reveal missing patches, security updates, and open ports that can serve as entry points for an attack. System hardening also demands that default passwords of services and applications are changed, strict firewall rules are applied to restrict or control traffic, account lockout mechanisms are used and continuous compliance audits are performed. Since system hardening is a continuous dynamic process, it's best implemented with system hardening policies your teams identify long before spinning up systems.
Most organizations follow strict guidelines based on system-hardening standards such as CIS, NIST, ENISA, etc. To comply with popular industry security standards and prevent cyberattacks, organizations must consistently undergo system hardening processes. Sadly, it's never one-and-done. System hardening works with the principle of defense-in-depth that enables organizations to build multiple layers of security to reduce the attack surface without compromising the features and functionality of the applications and operating systems.
Broadly, system hardening is classified into the following types:
Server hardening: Protect the ports, functions, data, and permissions on a server. Techniques include regularly updating/patching server software and strong passwords.
Software hardening: Update security measures on all applications by editing/updating application code to prevent attacks.
Operating system hardening: Make OS running on all endpoints secure. Techniques include updating patches and limiting accounts with access to the OS.
Database hardening: Make the database and the DBMS secure. Techniques include limiting user privileges and access, disabling unnecessary services, and encrypting database information.
Network hardening: Make all communication channels in the network between servers and endpoints secure.
Importance of System Hardening
System hardening greatly minimized the risk of cyberattacks. One of the major causes of breaches that show in system-audit failures is configuration changes that result in compliance drift. Every time a new server or user is added or a new application is installed, it creates an opportunity for vulnerabilities to arise.
When organizations have numerous assets in the fleet with multiple configuration options, bringing every asset, old and new, in line with CIS benchmarks can take a long time with manual effort and, ironically, introduce newer errors. Since these events are inevitable within any IT ecosystem, great care should be taken to ensure secure configuration and continuous compliance of dynamic and ever-changing IT infrastructure. This can only be achieved by implementing automation tools that help harden systems by continuously monitoring and auditing your heterogeneous IT assets and remediating drifts when they arise.
System Hardening Standards and Best Practices
System hardening is an essential process, and organizations like the National Institute of Standards and Technology (NIST) and Center for Internet Security (CIS) maintain standards for system hardening best practices. They recommend establishing a thorough system-security plan, regularly patching and updating OSes, implementing encryption, and much more.
A comprehensive system hardening strategy must include:
A system hardening standard (CIS, NIST, ENISA, etc.)
System-hardening plans based on your organization's specific needs
The use of CIS benchmark-based security auditing tools to perform continuous audits and identify vulnerabilities in the systems
Quick vulnerability patching using an automation-based vulnerability scanning and patching tool to identify missing patches, security updates, and misconfigurations
Robust user permissions/access rules: Remove unnecessary accounts and privileges across the infrastructure
A CIS-certified compliance automation solution with compliance reporting and automatic drift remediation
![System Hardening infographic]()
System Hardening With Chef Compliance
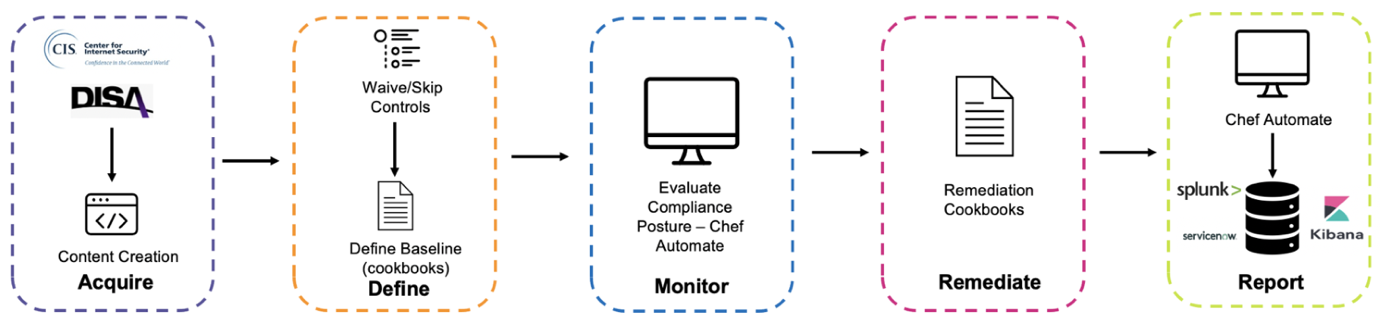
Chef Compliance is an automation solution that includes CIS and DISA STIG benchmarks to audit and remediate vulnerabilities in systems and help make IT ecosystems compliant and secure. With Chef Compliance, organizations use both Chef Infra (configuration management) and Chef InSpec (compliance) to:
Perform continuous audits that assess the current and ongoing state of configurations across heterogeneous estates
Correct misconfigurations based on recommended CIS and STIG benchmarks
Use exceptions and waivers in the audit process for specific controls
Customize existing remediation content to suit your organization's needs
Rollback changes to the last known trusted state if a benchmark is compromised
View the configuration status and compliance postures of all endpoints from a single dashboard
With Chef Compliance, enterprises can maintain security across hybrid and multi-cloud environments also improving the overall efficiency and speed of DevOps processes. Chef enables IT teams to perform system hardening with the help of continuous security audits and remediation that detects and fixes vulnerabilities in diverse IT fleets. The baselines are easily tuneable to organizational requirements, admins have total visibility, and the compliance profiles are easy to maintain – even for massively distributed hybrid and edge infrastructures.
![Acquire, Define, Monitor, Remediate, and Report]()
Benefits of System Hardening With Chef
While there are numerous benefits that come with system hardening from security and compliance perspectives, the primary benefits are:
Improved security postures: Continuous audits and remediation based on CIS and STIG standard profiles mean all vulnerabilities are detected and addressed, ensuring the reduced risk of data breaches, malware, and unauthorized access
Better auditability: Easy-to-read code that works across all platforms and operating systems. Chef's curated profiles make complex security audits easier, fast, and more transparent
Improved system functionality: With error-free automation, speed of processes, consistency of configurations, and fully secure infrastructure, Chef improves the overall efficiency of all systems in your fleet and the productivity of your DevOps teams.
Try Chef InSpec Scans To Check Your System Hardening
If you're looking for an automation solution for your system hardening to ensure compliance across heterogenous IT estates, download the freely available Chef Workstation and try running a couple of publicly available Chef InSpec profiles against Windows or Linux systems.
The following examples provide DevSec baselines to analyze Linux and Windows systems and don't require anything to be installed on your target nodes. The command pulls the content from GitHub, so there's no need to clone the repo. Provide either SSH or WinRM credentials to scan any system in your IT estate, on-prem, in the cloud, or on the edge:
Linux:
- DevSec Linux Baseline
$ inspec exec-t ssh://user@node -i ~/.ssh/id_rsa
Windows:
- windows-baseline
$ inspec exec-t winrm://user:password@node
These simple commands immediately report back passed and failed tests and highlight where you're vulnerable. Regardless of how your systems were initially configured, you'll see how hardened they are. Users of Chef Automate, the Chef ecosystem dashboard, can use Chef Compliance to schedule recurring scans and take advantage of hundreds of provided system-hardening profiles or your own custom profiles.
Published at DZone with permission of Anugraha Benjamin. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments