The Best Infrastructure as Code Tools for 2022
Know the best infrastructure as a Code tools for 2022.
Join the DZone community and get the full member experience.
Join For FreeCustomer: Can we exchange our systems?
System Admin: Why do you want to exchange your system?
Customer: Because the application behaves well on your system but throws tantrums on my system.
Sounds funny?! This is what millions of customers have been experiencing over the years. This blog talks about how infrastructure as code tools are bridging this gap.
The advent of cloud computing has revolutionized every IT segment. IT infrastructure is not excluded. Gone are the days when administrators had to manually provision resources and manage the data in large excel sheets. With today’s dynamically changing network requirements, the very thought of manual maintenance of IT infrastructure is terrifying. This is where Infrastructure as Code tools come to the rescue.
Simply put, IaC is about infrastructure automation using code. In an IaC environment, administrators write and deploy config files that are machine-readable for automatically provisioning IT infrastructure and maintaining the infrastructure always at the desired state. Using IaC config files, you can automate deployments of networks, virtual machines, servers, databases, etc.
The Need for Infrastructure as Code Tools
Initially, IT administrators manually placed servers, and configured and deployed applications on those servers. The configuration details were manually stored and managed by the network teams. This process was repetitive and time-consuming. Moreover, it required multiple people to manage this task. The biggest challenge was scalability as administrators struggle to set up new servers to match the speed and scale of changing business processes.
Managing the network team was an additional overhead. The cost to hire and manage this team was a costly affair as well. Another important concern was network visibility. Managing the ever-changing infrastructure from a central pane and identifying pain points was a challenge.
With multi-cloud and hybrid cloud deployments, organizations were able to overcome some of these challenges. However, the discrepancies that arose when multiple people handled the infrastructure management services were hard to manage. While they were able to automate certain tasks using scripts, managing the infrastructure at the desired state always was a challenge. With infrastructure as code tools, administrators are now able to write predefined configurations for each IT resource in the source code and automate IT infrastructure management.
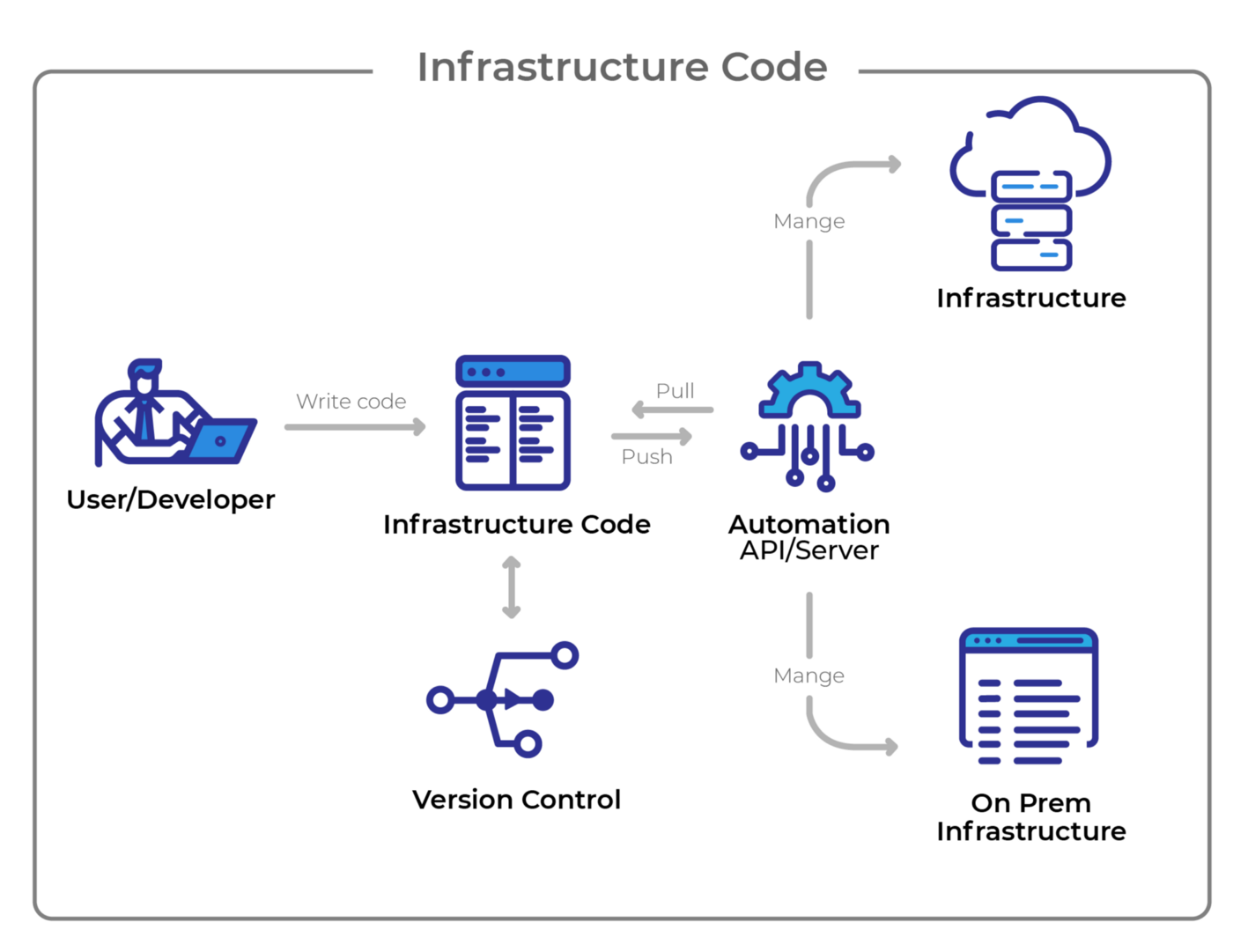
Benefits and Reasons To Implement IaC
Organizations that implement IaC gain significant benefits. An increase in operational efficiencies is one of the key benefits among them. As config files are used as a single source of truth, resources are deployed with the same configurations every time. So, it eliminates human errors or discrepancies arising from multiple configurations from multiple people.
Secondly, deploying code-based cloud infrastructure automation massively increases the speed of business operations. It allows you to scale higher and at your own pace. Right from development to testing and production, the entire product lifecycle can be automated, making it efficient and cost-effective.
Most importantly, IaC tools ensure that the infrastructure is always maintained at the desired state. Any deviations from the desired state are instantly notified to the concerned persons. As the entire operations are stored in config files, tracing and auditing processes are easy, resulting in compliance.
IaC allows developers to instantly deploy test environments to check out new features of apps while testers can run scripts on replicas of production environments. By eliminating administration, provisioning, and management tasks, organizations save a lot of money.
What Is Infrastructure as Code Security?
IaC is a part of the DevOps environment wherein security is also implemented across the CI/CD pipeline. However, as IaC environments operate on a single source of truth, a lack of powerful security controls can open up network vulnerabilities. For instance, an unpatched vulnerability or a misconfigured IaC template can enable hackers to gain access to sensitive resources.
Read DevOps Automation Tools for SaaS Companies, to know how to leverage the DevOps revolution entirely by choosing the right automation tools for the infrastructure.
IaC Templates
IaC templates are definition files that are machine-readable and hold the key to provisioning and managing agile deployments using code. When IaC templates use OS images from external sources, they unintentionally execute untrusted code, opening a way for hackers. Unsecure default configurations are another vulnerability with IaC templates that can be extended to cloud infrastructure on public networks. As such, you should check templates for these unsecured configurations and vulnerabilities in the initial phase.
Secret Storage
IaC code comprises sensitive information such as storage and configuration details of deploying infrastructure in the form of Secure Shell Keys (SSH), authentication tokens, passwords, etc. When this information is stored in a doc or text files or in the source code management systems, it can be accessed by hackers. So, storing secrets inside vaults and adding references to them within the configuration files is recommended.
Communication Channel Vulnerabilities
When IaC uses a master-node architecture, a single master manages and deploys configuration to all nodes. As such, a vulnerability in that master can affect the entire deployment infrastructure. So, securing the communication channel is the key.
Access Controls
When deployments are automated using IaC files, the code can make deployments without requiring root privileges on the target environment. It can be scary when the code is compromised. Ensuring that the least privilege principle is implemented is recommended.
What Are the Principles, and Best Practices of Infrastructure as Code?
To fully leverage IaC benefits, organizations should ensure that IaC's best practices are designed and implemented across the infrastructure.
Version Control System To Manage Code as a Single Source of Truth
To efficiently manage the infrastructure using code, you should treat infrastructure code as equivalent to the application code. So, add all your configuration code into the config files and make them a single source of truth by storing them in a version control system. It means you can seamlessly deploy code without signing into the server or documenting the procedures. The code handles everything. Moreover, every change is tracked and audited. Everyone across the pipeline can seamlessly collaborate wherever required.
Integrate IaC Into the CI/CD Pipeline
Once the infrastructure configuration turns into code, the same application code procedures apply to the infrastructure code too. So, integrate infrastructure as code tools into the CI/CD pipeline. In the test automation environment, when a change is made to the infrastructure, it will automatically trigger automated tests. With continuous testing and continuous monitoring, you can ensure that changes are automated and error-free.
Immutable Infrastructure Is the Key
Immutable infrastructure is a type of infrastructure management wherein IT resources such as servers, virtual machines, etc. cannot be modified after deployment. When an update is required, the existing instance will be replaced by a new instance. To fully leverage Docker containerization solutions, implement immutable infrastructure wherever possible. You can instantly create and deploy code and then kill those containers when you want to update or change the configuration and work with new ones. It brings consistency and security across the infrastructure.
Microservices Architecture Best Suits IaC
Similar to application code that leverages microservices, your IaC should also be broken into smaller, independent modular bits so that you can independently manage different parts of the infrastructure with customized and role-based access controls while comprehensively automating the entire infrastructure.
Infrastructure as Code Tools
As organizations are aggressively embracing the IaC revolution, the market is getting flooded with infrastructure as code tools. So, choosing the right cloud infrastructure automation tool for your organization is the key. Let’s review the IaC tools lists!
Terraform is a popular open-source tool for infrastructure as code orchestration offered by Hashicorp. It was written by Mitchell Hashimoto in the Go language and supports Windows, Linux, macOS, FreeBSD, Solaris, and OpenBSD platforms. A consistent CLI workflow enables you to manage various cloud services using declarative configuration files from cloud APIs.
Introduced in 2014, Terraform primarily focused on AWS but has evolved to support multi-service providers. The tool uses Hashicorp Configuration Language (HCL) that balances machine-readable code and human-friendly scripts. It also supports JSON.
Terraform offers an extensive set of built-in functions and string interpolations making it easier to code complex logic scenarios without needing another language. Modules can be reused again and can be stored and versioned in Git or Terraform Module Registry, allowing for seamless collaboration across teams.
The infrastructure state is written to a file and stored in S3, disk, or the source control. This means that you can play around with resources without tearing down the infrastructure. Configuration management is easy as well, using terraform plan wherein you can retrieve the actual state of the infrastructure every time you run that plan and compare it with the desired one and revert manual changes.
CloudFormation is a popular cloud infrastructure automation tool coming from the IaaS giant AWS. It enables organizations to easily create, deploy and manage the AWS resource stack using a template or a text file that acts as a single source of truth.
CloudFormation uses YAML or JSON. As it runs on the AWS infrastructure, you don’t have to worry about how it stores the infrastructure configuration. Templates are used to customize the AWS stack and replicate and deploy apps in multiple environments.
Change Sets is an important feature that enables you to check what changes before instantiating a template. Nested Stacks are another important feature that enables you to easily manage complex stacks by encapsulating functional logic, groups, databases, etc. in the template. It means you don’t have to compare and check old and new templates before making any changes.
Coming from Amazon AWS, CloudFormation enjoys certain benefits. AWS keeps updating its features and services and CloudFormation gets these updates as well. Moreover, AWS keeps improving CloudFormation which means users will get the latest features and best services.
Ansible is a configuration management tool that lets you automate the provisioning of infrastructure. In the early days of network infrastructure, Linux servers dominated the network landscape. Ansible began providing infrastructure automation solutions to Linux environments but now has evolved to support Windows, IBM Oss, virtualization platforms, containers, etc.
Ansible uses Python-based YAML syntax. It uses procedural style language to manage the infrastructure wherein step-by-step procedures for the desired state are coded. The tool stores the desired state configuration by mapping corresponding tasks with the defined group of hosts and stores them in ‘Play’. A list of ‘play’ is called a Playbook.
Ansible uses push mode to deliver change instructions to nodes in the network and deployments are instantly done. The agentless master architecture makes it simple to install and use. Ansible started with a CLI and now offers a UI. However, the UI can still be improved. When compared with Puppet and other CM tools, the Ansible community is smaller but offers good support. It best suits short-lived environments.
Puppet is an enterprise-ready configuration management tool that enables administrators to define the desired state of the infrastructure via code. It is more robust and popular among CM tools with powerful interfaces, modules, and available actions. It is written in Ruby. Puppet uses a Domain Specific Language (DSL) to manage code via a declarative programming method and manages Linux and Windows environments.
Puppet uses a Client-server model wherein the server software is installed on the server while each managed machine contains the node software installation. It is a model-driven architecture. Compared with Ansible, puppet installation takes some time and involves complex configuration settings. It offers high scalability and availability by replicating data of the master to another server that again involves complex settings. The tool uses Puppet Forge which stores around 6000 modules. It uses a pull deployment model where the agents initiate the pull mode and regularly check for updates from the master.
Puppet GUI is highly intuitive and enables users to seamlessly monitor and manage the entire infrastructure from a central pane in real-time. It offers customizable reporting tools. The tool enjoys a large and mature community that is supportive. Puppet offers dedicated support and extensive Kbs on its website. Puppet is offered in two versions; the Open-source edition and the Puppet Enterprise edition.
Pulumi is a new multi-language and multi-cloud development platform founded in 2017 and is quickly evolving to become one of the best Infrastructure as Code tools. Pulumi is more or less similar to Terraform, allowing you to create and deploy infrastructure as code to every type of cloud environment. It is open-source and free to use and is available on Github.
To express the desired state, you can use general-purpose languages such as Go, JavaScript, C#, TypeScript, Python, etc. As such, you don’t have to create new modules but simply use existing ones. It is quickly getting popular because it allows you to write applications in your desired language and manage the infrastructure by implementing DevOps best practices.
Pulumi supports all cloud providers such as AWS, Azure, and GCP as well as other cloud services and is highly flexible. The tool supports Windows, Linux, and OS X environments and comes with a powerful and feature-rich CLI. It uses a cloud-objective model to deliver a unified programming model. To manage the state and concurrency of the infrastructure, Pulumi offers its app.pulumi.com service. However, it is not easy to use but has a short learning curve. It offers deep support for Kubernetes. With reusable components and stacks, it makes your infrastructure management job simpler.
Docker is a popular name that no developer can ignore. Docker is not an IaC tool. It is a popular containerization tool that enables developers to create applications with all libraries, and dependencies as a package and deploys them in any environment. The Docker platform was introduced in 2011 by Solomon Hykes and Sebastian Pahl as a Linux container runtime and became popular in 2013 as a standard containerization tool across the globe. RedHat collaborated with Docker in 2013 followed by Microsoft, IBM, AWS, etc. in the following year. Docker support for non-Linux platforms was released in 2016. Microsoft Hyper-V came with Docker native support in the same year.
Docker enables developers to package an application along with its dependencies and libraries into a virtual container and deploy them in any target environment. It allows a single host to run multiple containers.
It contains 3 core components
- Daemon to build and run containers
- API to facilitate communication between the daemon and users
- CLI to manage the tool
Docker allows developers to focus on quality code without worrying about the target environment. Similarly, administrators enjoy the low overhead and smaller footprint of docker. So, organizations can focus on the product rather than the maintenance of the infrastructure.
Docker significantly improves the infrastructure as Code DevOps environments. You can spin up a container for every step in the CI/CD pipeline and kill the stateless container once the job is done. That way, you can manage an immutable infrastructure for security and consistency. With continuous testing and continuous monitoring, you can ensure that every change made to the infrastructure doesn’t affect the environment.
Docker ensures that apps deliver consistent and reliable performance regardless of the platform, OS, or services it works on. The ability to deploy faster facilitates faster time to market while reducing costs. Along with high availability, flexibility, and scalability, Docker brings mobility solutions, enabling you to run apps everywhere. With isolated app environments, maintenance is reduced. Repeatable automation makes infrastructure management easier. It is easy to roll back as well. Docker comes with huge community support.
| Infrastructure as Code tools | Terraform | CloudFormation | Pulumi |
| Language Support | Uses Hashicorp Configuration Language that is both machine-readable and human-readable | Both YAML and JSON | JavaScript, Go, Python, TypeScript, C# |
| Configuration support | Terraform configuration allows fetching and computing of data from data sources to be used elsewhere as well | 60 parameters. Values can be imported from SSM or another stack output | Config object allows you to retrieve the value using setters and getters and grep |
| Configuration Drift Detection | Yes | Yes | Yes |
| Command Line Interface | Single command-line app | Can develop and test resources | Single command-line app |
| State Management | A state can be saved in S3, Terraform cloud, locally, or DynamoDB | Using stacks | The state can be saved in S3, locally, or Pulumi service backend |
| Change Management | Using Terraform Plan | Using Change Sets | Using Pulumi Preview |
| Module Support | Reproducible infrastructure can be created | Allows cross-stack and nested stack references | Reproducible infrastructure can be created |
| Automatic Rollback | No automatic rollback | Automatic rollback | Not available. Have to use Open RFC |
| Multi-cloud support | Yes | No | Yes |
| License | Open-source | Free | Open-source |
| Support | Hashicorp support and a large community | AWS support and a large community | Pulumi support and a good community |
Infrastructure as Code Use Cases
Automate Deployments
IaC tools facilitate automatic provisioning of scalable infrastructure enabling organizations to automate deployments and reduce deployment cycles. Consider for instance an organization that requires infrastructure orchestration for multiple cloud platforms such as AWS, Azure, and GCP. The company operates multiple environments such as QA, Staging, production, etc. the infrastructure should be quickly set up while including database setups.
Using the cloud-agnostic Terraform tool, the organization can automate the provisioning of infrastructure using code. Similarly, when the infrastructure is killed, it automatically triggers data backup. By integrating the application deployment via a version control system such as Git or Bitbucket, you can automate app deployments as well. When manual configurations are automated, it increases efficiencies, and speed while reducing human errors.
Multi-cloud Deployments
Cloud computing has greatly evolved in recent times. Today, a single cloud is not enough to manage an organization’s changing business needs. As such, organizations are aggressively embracing multi-cloud and hybrid cloud environments. When you implement a hybrid cloud, you place certain resources on-premise, additional resources in a public cloud, and some are managed in private clouds. Configuring settings for different cloud deployments is time-consuming and challenging.
With IaC tools, you can write code in JSON or YAML and manage infrastructure using config files. So, with a single resource template or configuration file, you can manage multiple cloud deployments. Using repeatable configurations, you can automate deployments to Azure or AWS and efficiently manage them with ease.
Disposable Environments
When an organization works with multiple cloud environments for production, staging, QA, etc., managing and updating the infrastructure for all these tasks can be challenging. For instance, testing scripts presents the risk of damaging the underlying infrastructure if something goes wrong
To overcome this challenge, organizations can use a CI server along with Docker containerization solutions to instantly create QA, Dev, and UAT environments and automatically test scripts. When the test scripts pass all tests, you can successfully deploy them to production environments and tear down the test environments. By doing so, you can eliminate configuration drifts while ensuring that new employers are not damaging something.
Moreover, provisioning Virtual Cloud servers has become easy and cost-effective. As such, organizations can now afford to scale up environments while paying for the resources used.
Immutable Infrastructure
Immutable infrastructure can be defined as one that cannot be changed once deployed. Implementing immutable infrastructure is especially beneficial for enterprises that manage infrastructure at scale. As the organizations run applications in real-time, they can’t afford to pause them. The organization will simply codify the provisioning infrastructure and deploy it. When an update is required, you simply kill the old server, build a new one from the common image, and provision it while automatically documenting the timestamp, version, etc. The good thing is that you can roll back old servers if you require time.
Immutable infrastructure enables organizations to seamlessly replace problematic servers without disturbing the apps running on them. Moreover, the infrastructure is consistent and does not show configuration drift. With consistent deployment and auto-scaling across the organizations, infrastructure management becomes easy and effective.
The new 12-factor methodology that offers 12 best practices to develop apps as a service also mentions immutable infrastructure as one of them. Application processes should not be disrupted when a server is shut down intentionally or by error.
Security Automation
Security automation is another key requirement in the DevOps Infrastructure as a Code environment. Similar to integrating security into the CI/CD pipeline via DevSecOps, security policies and controls of the IaC are also integrated into the CI/CD pipeline. As such, every change made to the infrastructure goes through security testing, allowing organizations to check how the environment responds to every change.
When the infrastructure is managed as code, the code should be able to access app resources to build, test, and run them. Whether these secrets are in the source code of the app, configuration files, text files, or scripts, they should be secretly stored in a secure vault. Otherwise, hackers can gain access to this sensitive information.
Read our webinar blog about The Perfect DevOps Toolchain for Fintech to comply with the best security standards.
Disaster Recovery and Backups
Disaster recovery and backup hold the key to managing any type of IT infrastructure. There are multiple 3rd party tools that can help you easily recover from a disaster. However, recovering a virtual machine is not just enough. You need to provide a base infrastructure for the virtual machines to ensure that the applications are rightly recovered. The time to recover all the other areas of DR workflows is the key. This is where IaC tools such as Terraform come to the rescue.
Terraform leverages IaC, allowing you to automate all areas of disaster recovery workflows such as provisioning VPCs, Subnet, EC2 instances, security policies, etc. so that application recovery is automated and instant. In addition, Terraform also performs clean-ups so that DR failover costs are minimal.
Create Fully Automated Multi-tenant Environments
In today’s highly competitive business world, software providers are finding it challenging to cost-effectively deliver software solutions to multiple customers. Firstly, you need to create a separate application environment for each customer that will increase your AWS/Azure infrastructure costs. Managing multiple app environments will increase overhead as well as time to market. Another challenge is using multiple code repositories for each customer. A multi-tenant architecture will solve all these challenges.
By creating a multi-tenant architecture, you can use a single app environment for multiple customers. One codebase will serve as a single source of truth. It will deliver a faster time to market and reduce development costs.
Infrastructure as code tools such as Terraform, CloudFormation, or Pulumi allows you to seamlessly create multi-tenant environments.
Blue/Green Deployments
Continuous delivery is a key requirement in today’s software development landscape. In order to achieve a faster time to market, organizations are quickly building and deploying products to customers. However, a buggy release can result in downtime. So, it is important for developers to match the speed and scale of current software delivery while ensuring that deployments are safe. Blue/green Deployments are a popular method for achieving this.
In this method, two identical production environments (Blue and Green) are used wherein one environment will be live while the other one will serve as a staging one. Initially, the blue application will run on the blue environment and version 2 of the same application will be routed to the green environment. If it works fine, then the green environment will go live and the traffic from the blue environment will be routed to the green environment. In case of any discrepancy, the previous version can be rolled back. So, organizations can seamlessly deploy applications without downtime.
There are different steps involved in this process. You need to swap the application, route the DNS, update the DNS, clone stack, update orchestration services, etc. Infrastructure as Code tools enables organizations to efficiently manage blue/green deployments. For instance, Pulumi uses a create-before-release approach to blue/green deployments, eliminating the guesswork of updates.
Published at DZone with permission of Alfonso Valdes. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments