Vulnerability Management in DevSecOps
In this article, we discuss the importance of practicing an efficient vulnerability management approach in the DevSecOps ecosystem.
Join the DZone community and get the full member experience.
Join For FreeDevSecOps means including security in the DevOps delivery pipeline. This model integrates security tenets as early as possible and in all applicable phases of the software development lifecycle. The diagram below showcases the security aspect's integration in the later stage of DevOps but wherein DevSecOps security is integrated into all stages of the lifecycle.
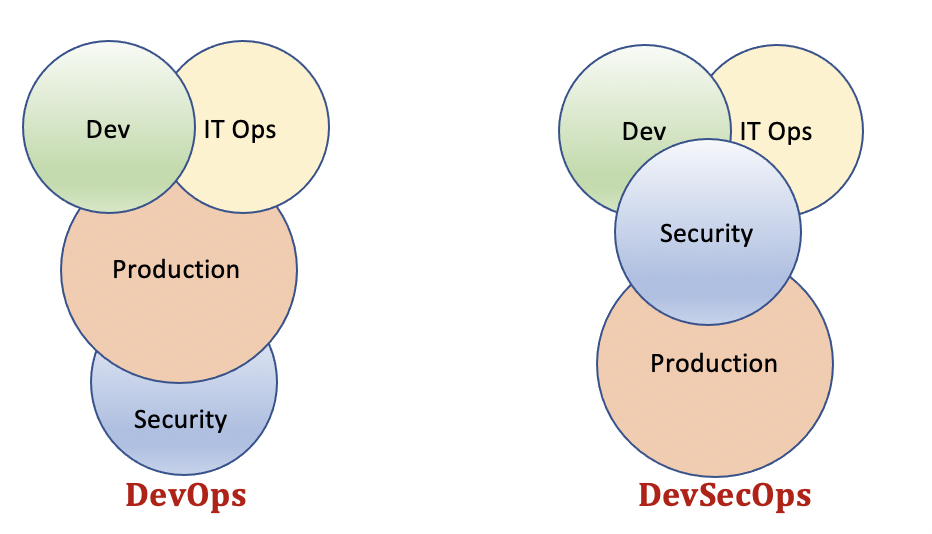
IT security leaders should adopt effective vulnerability management practices in their organizations to implement proper DevSecOps.
Vulnerability Management
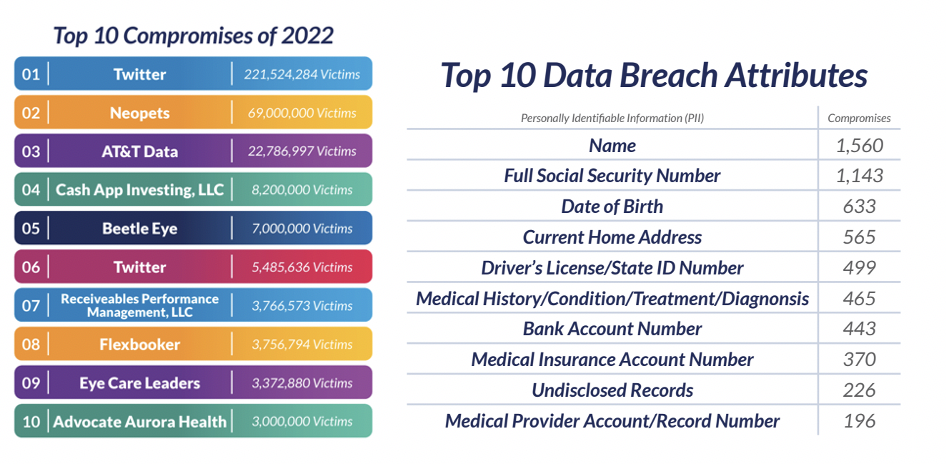
Vulnerability management is the practice that helps organizations identify, assess, prioritize, and fix vulnerabilities in their system. Ultimately, the goal of vulnerability management is to reduce the risks posed by vulnerabilities by using techniques such as patching, hardening, and configuration management. This helps to ensure security while limiting risks that could potentially be exploited by malicious users. IT Security's primary responsibility is to protect against vulnerabilities. We all know that security breaches can be very expensive; per the combined research conducted by Ponemon Institute and IBM, the average cost per data breach is USD 4.35M, while 85% of the organizations have at least one breach in 2022. Below are the top ten data compromises and top ten data breach attributes in recent years, per the 2022 Data Breach Report.
Vulnerabilities vs. Exploit vs. Threat
Understanding the definition and relationship between vulnerabilities, threats, and exploits is important.
Vulnerability is a flaw in the code or software leaving way for the attackers to gain unauthorized access to the system. At a high level, vulnerabilities can be of two types:
- Technical Vulnerabilities: Code-related bugs or errors, badly configured firewalls, Unpatched or outdated operating systems or Infrastructure, etc.
- Human Vulnerabilities: People making mistakes knowingly or unknowingly and gaining access to data, systems, or buildings by exploiting human psychology.
Exploit is the method hackers use to take advantage of the vulnerability. An exploit is some malicious code used to texploit a system's vulnerability. It can be stealing the information, slowing down/stopping the system from functioning, or being a parasite on the servers to create a problem in the future. For example, the Log4Shell vulnerability was a weakness in how the Log4j program allowed users to execute arbitrary code based on values that should have been printed in the logs. Many different exploits were subsequently implemented that attempted to use this vulnerability in different ways – some of them allowed you to plug in your own code. In contrast, others exposed the private environment variables of the software.
A threat is an actual event in which one or more exploits use a vulnerability to start an attack.
Vulnerability Management and DevSecOps Combination
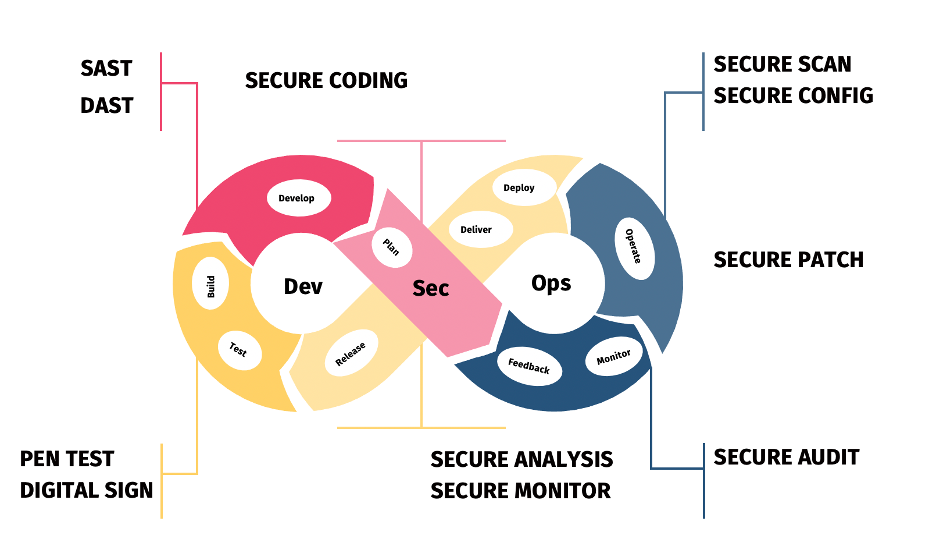
To have a good start with the DevSecOps project, integrate the security objectives early in the development of an application, ideally before starting to write the code. Security can integrate and can begin effective threat modeling during the initial phase of the project. Static analysis linter and policy engines can run anytime when a developer checks in the code to identify any issues before the code move ahead of the pipeline. This helps the developers to know about the security issues immediately, allowing them to take care of the ownership to fix the security issues. Once code is checked in the static application, security testing (SAST) can be performed using SAST tools to identify the vulnerabilities and perform the software composition analysis. SAST tools should be integrated into the post-commit processes to ensure that the new code introduced is proactively scanned for vulnerabilities. Hence, integrating SAST tools early in the software development life cycle reduces application vulnerability risk.
After the code builds, we can start to engage in security integration tests. Running the code in an isolated container sandbox allows automated testing of things like network calls, input validation, and authorization. These tests are part of Dynamic application scanning tools (DAST). These tests generate instant feedback enabling quick iteration for triaging the issues. If things like unexpected network calls or un-sanitized input occur, the test fails, and the pipeline generates actionable feedback in the form of notifications to relevant teams.
Access Management is the next important tenet that is required to be integrated with DevSecOps. We need to ensure the application writes relevant security and performance metrics. Role Engineering needs to be performed, defining roles and access associated with each role – standard birthright roles need to be defined.
Security scans and vulnerability management continues even after the product/project go into production. We need to ensure automated patching is applied to the latest version of the product via proper configuration management. Ensure the production is running the latest stable version of the software and its code.
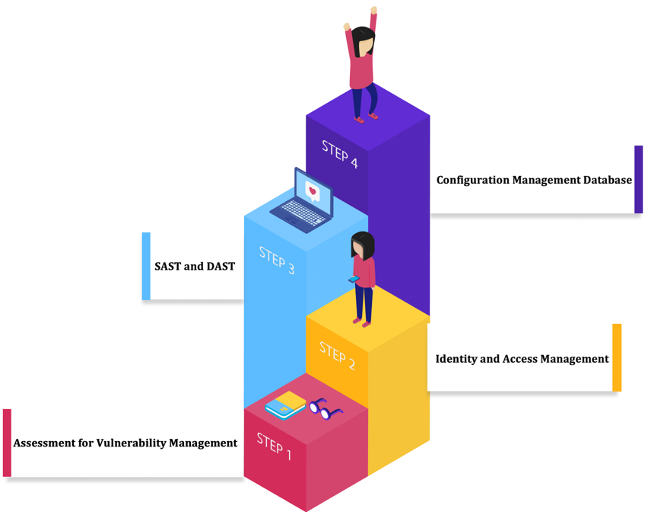
Setting up a Vulnerability Management as a Program To Support DevSecOps
Being discussed about the DevSecOps and the importance of Security inclusion in the DevOps models, it's very important we set up efficient vulnerability management practices. This can be achieved by setting up a vulnerability management as a program.
We can get started with a Vulnerability management assessment for the IT organization. The frequently asked question can be why we need an assessment as we already have some remediation mechanism set up in place. But it's extremely important to have these kinds of assessments to keep up to date with the industry standard on security and vulnerability remediation. Below is one of the reasons why we need to have a vulnerability management assessment and be up to date with the industry security standards.
We will only have top of 20%-25% of the custom code in the projects we use for our software development in a typical IT organization. We will use all of our tools for different types of code scans and ensure we remediate the vulnerabilities. However, the rest of the code will be from open-source modules and libraries. The frameworks and libraries we check out will inherit more frameworks and libraries underneath, which we may not be aware of the fact about how clean that code can be. This code has not been written in-house, and we are unaware of some of the calls it makes to function successfully; on the other hand, we have containers that contain packages and metadata. Infrastructure as a code can open up several avenues for vulnerabilities if it's not configured in the right way.
Hence DevSecOps, properly implemented, can mitigate the vulnerabilities in the first place, while proper vulnerability management can remediate the open vulnerabilities.
Steps for efficient Application Security via Vulnerability Management practice set up until it's operationally matured:
1. Assessment for Vulnerability Management
An assessment is significantly important to understand the landscape of the IT organization. This will allow us to prioritize the vulnerability types avoiding the risk - Analyze vulnerability risk and focus on what's urgent. We can define, identify and monitor the endpoints for known or emerging vulnerabilities.
2. Identity and Access Management
Efficient IAM is required to proactively prevent the opening of vulnerabilities. IAM is the gateway between internal and external networks in an organization when the sheet of security layer needs to be placed. Leverage appropriate way of authentication techniques like Multifactor Authentication (MFA), Sigle Sign-On (SSO), and Risk-based authentication (RBA).
A few Advantages of the IAM are:
- Secure data confidentiality
- Data Security
- Stop Malware attacks
- Limit the organization portals to only required parties.
3. SAST and DAST Scans
- SAST: Static application security testing analyzes program source code to identify security vulnerabilities. The SAST methodology guides developers to begin testing their application at early development stages without executing a functional component. This approach discovers application source code security flaws early and avoids leaving security issues to later development phases. This decreases development time and enhances overall program security.
- DAST: Dynamic application security testing scans software applications in real time against leading vulnerability sources to find security flaws or open vulnerabilities. DAST tests the running application and has no access to its source code. DAST is a form of closed-box testing that stimulates an outside attacker's perspective. It assumes the tester does not know the application's inner functions. It can detect security vulnerabilities that SAST cannot, such as those that appear only during the program runtime.
Because DAST tests require a complete working application, reserve them for a later phase in your application development process. Testers need to interact with the application: provide inputs, check outputs, and simulate other actions typical of user interactions.
4. Effective Configuration Management Database (CMDB)
CMDB being up to date is the most important aspect of a successful vulnerability program. It is key to understand the organization's software asset and configuration management process. Configure discovery tools for the transparent discovery of software configurations. Update CMDB and Map configuration items to services and applications.
Conclusion
I will conclude that the implementation of effective vulnerability management in organizations having a high-paced environment with development and IT operations teams with automated pipelines is very important. Considering the current situation in the industry, prevention of security breaches and cyber-attacks is extremely important, and it's like breath. This can be achieved by bringing on the security aspect early and all phases of the software development life cycle and timely remediating the vulnerabilities.
Opinions expressed by DZone contributors are their own.

Comments