What Is Segmentation in Operating System?
Read this article to learn how segmentation creates segments for the user program, and see an example of how it can reduce CPU overhead.
Join the DZone community and get the full member experience.
Join For FreeThe idea of segmentation In OS is similar in function to paging, which is used to manage memory. Segmentation is a way to divide the user program and data into segments. Segmentation and paging are two different things. Each page in paging has a fixed size, while segments have a variable size.
Segmentation maps the user's view onto actual physical memory. We will briefly discuss segmentation and its workflow in the next section. We will also discuss segmentation using an example and conclude the discussion with some advantages and disadvantages.
What Is Segmentation in OS?
Segmentation is used to manage memory. The user's view is plotted onto physical memory. Segmentation is where the user program is broken down into the number of segments that each segment is of variable size.
Segmentation can be described as dynamic partitioning where the segments that are being divided are of variable sizes. These segments do not need to be in the same memory. Segmentation doesn't cause internal fragmentation, but it can create external fragmentation.
A program can be divided into segments according to the user's perspective. The main method has a set of objects, methods, arrays, and procedures. It also includes templates, global variables, and other items. These modules or data elements refer to the segments that the user refers to by their name. They are indifferent as to what address the modules or elements are stored in their memory. The user doesn't have to worry about the order in which the data elements or modules are stored in memory.
Each segment in the user program is variable in length. The purpose of each segment is what determines its length. In logical addressing, elements within a segment are identified using their offset value, which starts at the beginning of the segment. Two entities know the logical address for a segment: segment name and the offset. Each segment created by a user program is numbered as the segment number instead of the segment name. Now, the logical address is composed of two tuples.
Segmentation Implementation
Let's now look at the implementation of segmentation. Segmentation is a way to divide a user program into a number of segments. A segment can be identified by two components: a segment name and a segment offset.
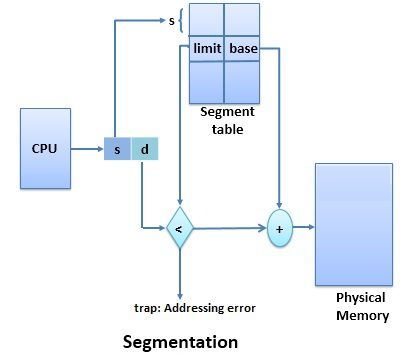
This section will show you how the two-dimensional address is mapped onto one-dimensional physical memories. As we have a page table for paging, we also have a segment table for segmentation.
Segmentation Table
The segmentation table contains two entries: the segment base address and segment limit. The segment base address denotes the address at which the segment is stored in memory. The segment limit denotes the length and width of the segment.
As you can see in the above figure, the CPU calls for a segment and provides a two-dimensional address. The segment number (or segment name) and its offset are "d".
The segment number will allow you to get two additional details about the segment number in the segment table: segments base address and its limit. The offset provided by the CPU is checked to see if it's between 0 and the limit for called segments. If yes, then the offset is added to the base address of called segments to retrieve the physical address. If the offset does not verify the condition, the operating system will throw an addressing error. The logical address attempts to extend the segment limit.
Advantages and Disadvantages of Segmentation
Segmentation has many advantages:
- Segmentation is closer to the programmer’s view of physical memories.
- Segmentation is a way to prevent internal fragmentation.
- Segmentation reduces CPU overhead because it contains an entire module at once.
Segmentation's disadvantages:
- External fragmentation can be caused by segmentation.
The Key Takeaways
- Segmentation is used to manage memory.
- Segmentation is very similar to how the user views physical memory.
- Segmentation is a method of dividing a user program into segments with variable lengths. The purpose of each segment will determine its length.
Segmentation is an array that contains the base address and the limits. The base address denotes where a particular segment is located in the physical memory, while the limit denotes how long it is.
External fragmentation can be caused by segmentation.
Opinions expressed by DZone contributors are their own.

Comments