When considering a successful Kubernetes governance strategy, the first component is ensuring that good multi-cluster management and visibility are well in place. It is necessary to maintain control over how and where clusters are provisioned and configured, as well as which versions of software can be used. For visibility, ideally, you should be able to centrally view and manage clusters to better optimize resources and troubleshoot issues. Improved management practices and better visibility can also save you the headache of having to deal with a number of security risks and performance issues down the road.
Next, you need to have an authentication and access management system. Having centralized authentication and authorization is going to help your organization in a big way. Not only will it make the process of login easier, but it’ll also help track who is doing what, so you can ensure the right people are performing the right tasks at any given time.
Finally, for Kubernetes governance, you should optimize policy management. Think about how Kubernetes is going to impact your engineering culture and how to find the right balance for developers’ flexibility within it. Governance — with an appropriate level of flexibility — ensures that you can meet customer needs and deploy critical services in a uniform and consistent way.
The two governance dimensions consist of:
- Policy scope: where a specific rule should be applied, enforced, or verified
- Policy targets: what should be enforced and verified
When you think about policy targets for governance, there can be many aspects. Here, we are discussing security policies, network management, access management, and image management.
Limit User Access
In security policies for Kubernetes governance, it’s important to limit users' access on the pods in the clusters. Users of the cluster should have well-defined access depending on the privilege, which is based on their role. To achieve this, implement security policies in place that will have rules and conditions related to access and privileges. In these policies, define that the containers should have only read access to the file system and enforce allowPrivilegeEscalation=false in the policy so that the containers and child processes cannot be subject to privilege changes.
Network Policies
Network policies play a very important role in defining which service can talk to each other. Here, define which pod and service can communicate with each other and where the isolation must be established. This comes under the pod security in Kubernetes governance. These policies help you control the traffic inside the Kubernetes clusters. These network policies can be pod-based, namespace-based, or IP-based, depending on your requirement for governance. In these policies, you define entities such as spec, podSelector/namespaceSelector, policyTypes, ingress(rules defined for traffic), egress, etc.
Access Administration and Management
In access management, while configuring the RBAC (role-based access control) policy, admins need to take the responsibility to limit access to cluster resources. There are multiple Kubernetes objects such as Role, ClusterRole, RoleBinding, and ClusterRoleBinding, which helps you define access to the cluster resources in detail.
Image Management
Leveraging public Docker images can improve speed and agility when developing applications, however, there are a lot of vulnerable Docker images out there, and using them on the production cluster can be very risky.
Image management is also a part of Kubernetes governance. Any and all images to be used on the cluster must be audited first for any vulnerabilities. There are a number of approaches to vulnerability scanning — how and where you check will depend on your preferred workflows. However, it is recommended that images be tested and passed before deploying on the cluster.
Hacking activities have increased exponentially in recent years, and hackers keep on finding loopholes in the system to gain access for faulty intentions. So, be very vigilant when adopting best practices to ensure that you only use official, clean, and verified Docker images on the cluster.
These policies are a must for better Kubernetes governance. After these policies and rules are in place, verify that they are all enforced in the organization as a part of internal compliance rules and policies. Monitor teams and projects comprehensively to ensure that everyone in the organization follows the policies defined and does not bypass them.
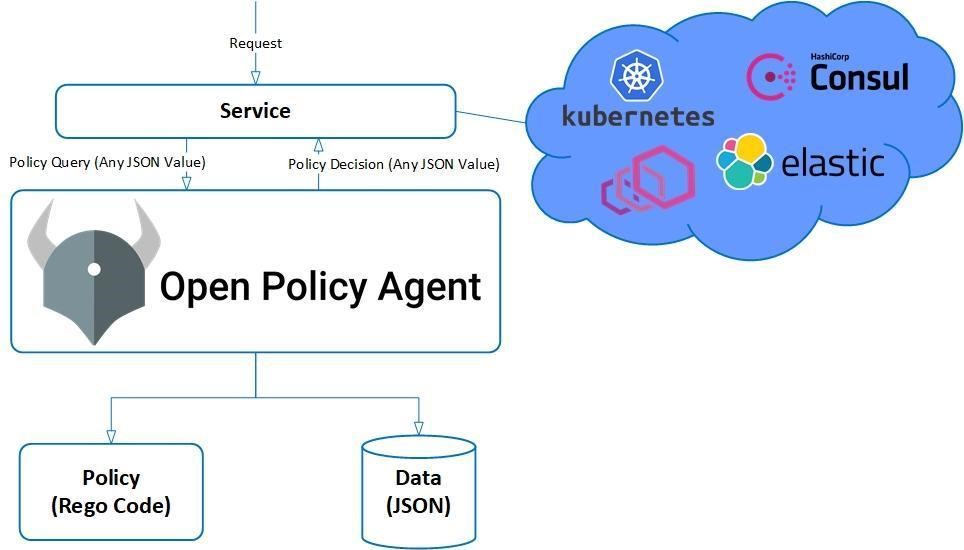
Open Policy Agent (OPA), a CNCF project, is an excellent way to create and enforce such policies across an enterprise at scale. As shown below, every request will go through the OPA, and the request decision will be based on the policies defined for the Kubernetes cluster. If the request is policy-compliant, it will be executed. If the request is violating the policies defined, it will be rejected by the OPA.