SSO Login: Key Benefits and Implementation
Learn how to better protect your users and yourself by using Single Sign ON login to authenticate passwords and user IDs.
Join the DZone community and get the full member experience.
Join For FreeWhat Is SSO Login?
Single Sign On (SSO) login refers to when a user logs in to an application with a single set of credentials and is then automatically signed into multiple applications. With SSO login, a user gains access to multiple software systems without maintaining different login credentials such as usernames and passwords.
A very popular example of SSO login is Google's implementation for their software products. Once a user is logged in to Gmail, the user automatically gains access to YouTube, Google Drive, Google Photos, and other Google products.
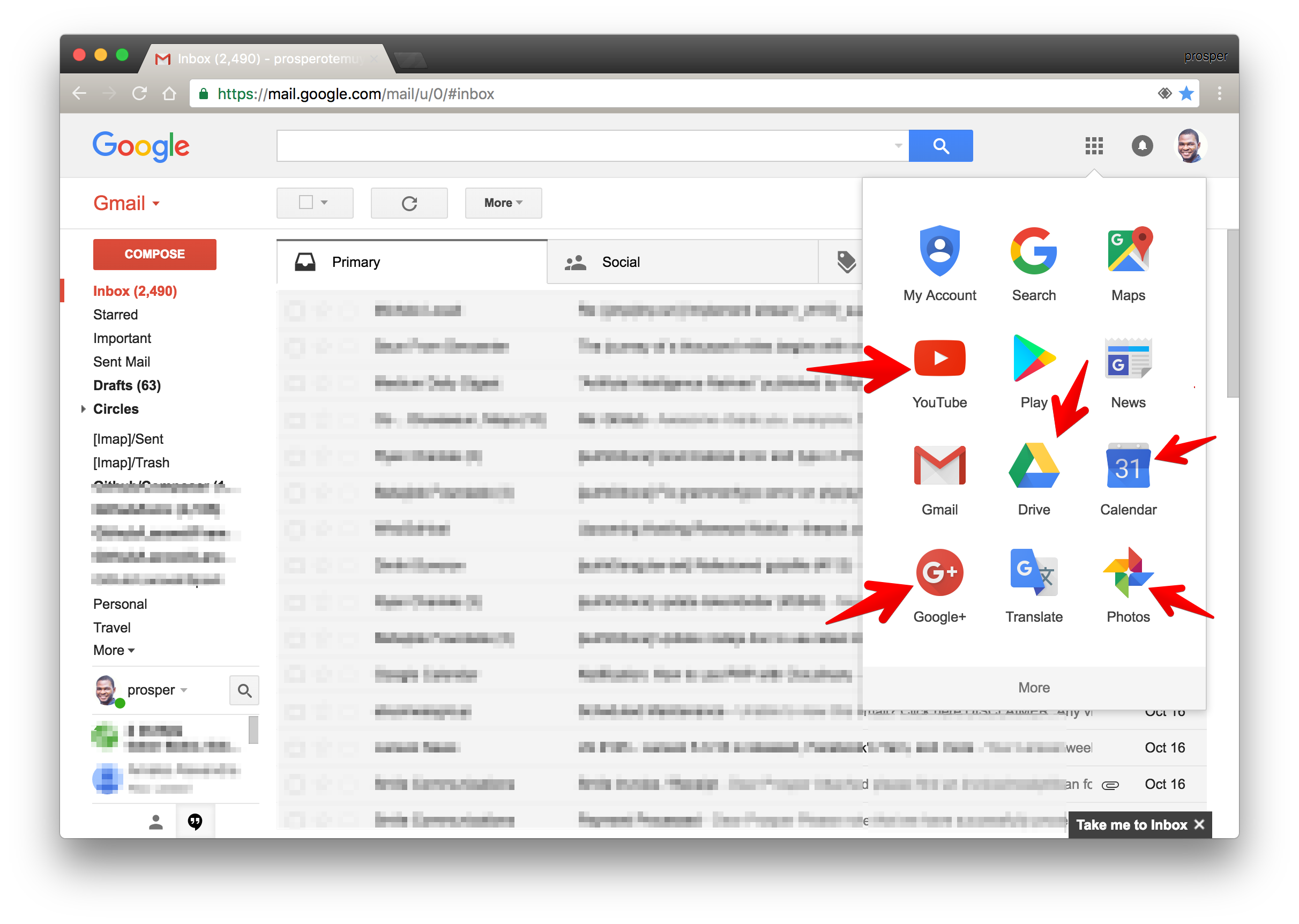 I signed into gmail and already have access to all those products around the red marker.
I signed into gmail and already have access to all those products around the red marker.
Key Benefits of SSO Login
Why should you implement SSO login? What are the benefits of SSO login? How does it increase your product's conversion rate? These are some of the benefits of SSO login:
- Eliminate the time spent re-entering user credentials, thus improving productivity for users and increasing conversion rates for product owners, which means your internal employees and your external users don't have to go through the hassle of maintaining and remembering yet another set of credentials.
- Eliminate password fatigue from having to store or remember different usernames and passwords.
- Reduce complaints about password problems, thus reducing the costs associated with setting up several helpdesk systems for password-reset issues, invalid credentials, etc.
- Minimize phishing, thus improving security.
- Streamlines the local, desktop, and remote application workflows, thus improving users' productive capacity.
How SSO Login Works
Let's look at an ideal scenario before going into the nitty-gritty of how SSO login works. Three apps have been developed separately: App FOO, App BAR, and App BAZ. They are also hosted on three different domains: foo.com, bar.com and baz.com, respectively.
Challenge: Users have to enter different usernames and passwords for the three different apps to gain access to certain resources.
Proposed solution: Eliminate the different login systems that are present. Users should be able to log in to foo.com and then be signed in to bar.com and baz.com automatically without having to re-enter their authentication credentials.
SSO login to the rescue: With SSO login, a central authentication server needs to exist. Let's call our central authentication server foobarbaz.com. This is how the process flow will look in this scenario:
- The user accesses foo.com.
- The user is redirected to foobarbaz.com, where an authentication-related cookie is generated.
- The user navigates to bar.com.
- The user is redirected to foobarbaz.com.
- foobarbaz.com checks whether the user already has an authentication-related cookie and redirects the user back to bar.com, providing access to its features and content.
- The same process applies to baz.com.
The simple take-away concept is that there is one central domain through which authentication is performed, and then the session is shared with other domains in some secure way e.g., a signed JSON Web Token (JWT).
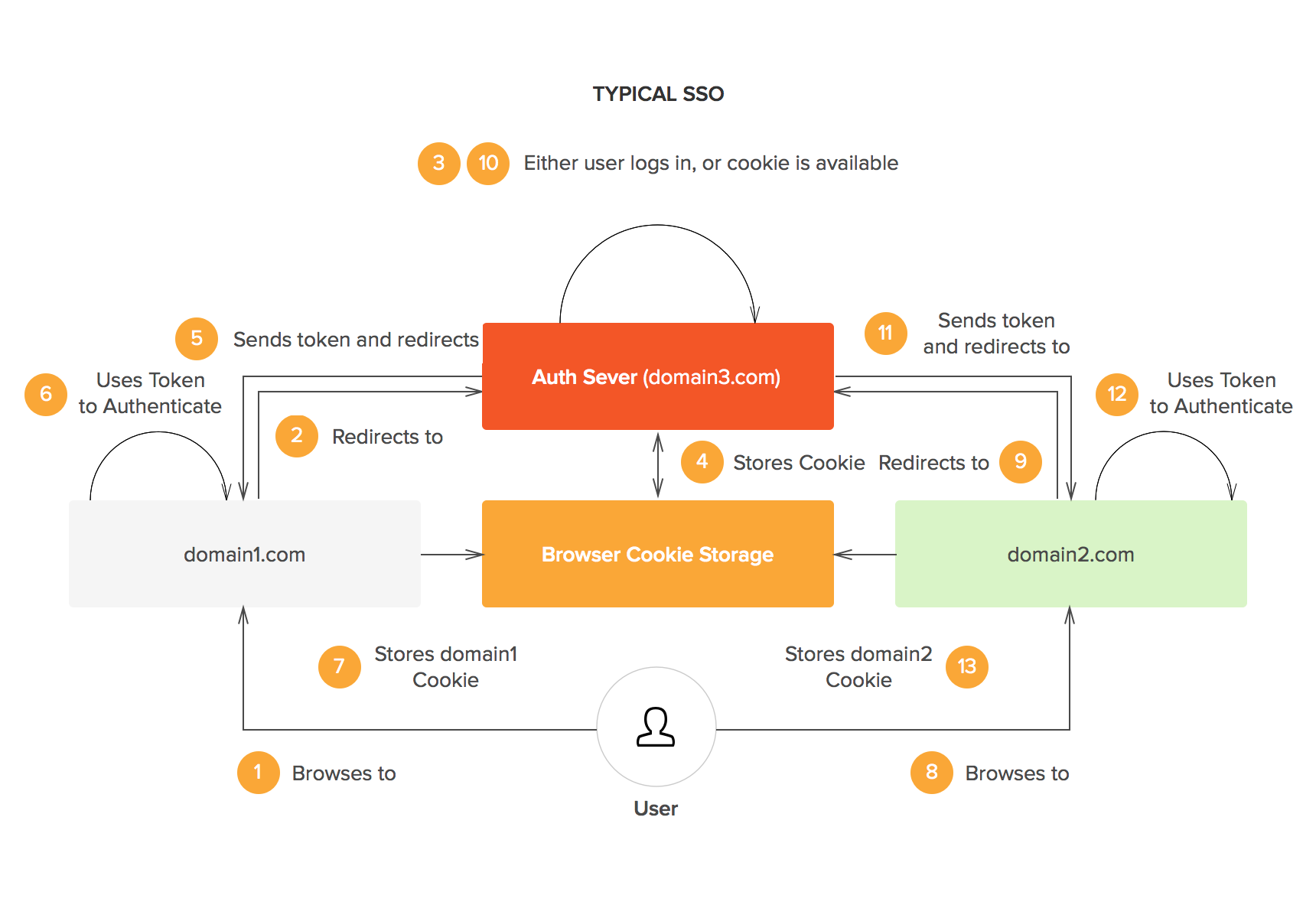 A typical graphical SSO example.
A typical graphical SSO example.
SSO Integrations
There are different SSO login integrations: these are external services you can use for Single Sign On logins. You can enable SSO login for your corporate applications, such as Salesforce, Dropbox, Microsoft Azure Active Directory, Slack, SharePoint, New Relic, Zendesk, and so on.
Conclusion
The benefits of using SSO login to manage a large ecosystem of applications and services are numerous. Modern application development supports distributed and decentralized systems. With an efficient SSO login in place, it's easier to add more applications to the existing suite of services without having to worry about authentication every time. If Google can implement SSO login and succeed, you can do it too!
Published at DZone with permission of Prosper Otemuyiwa, DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments